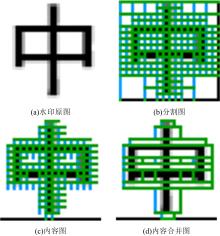
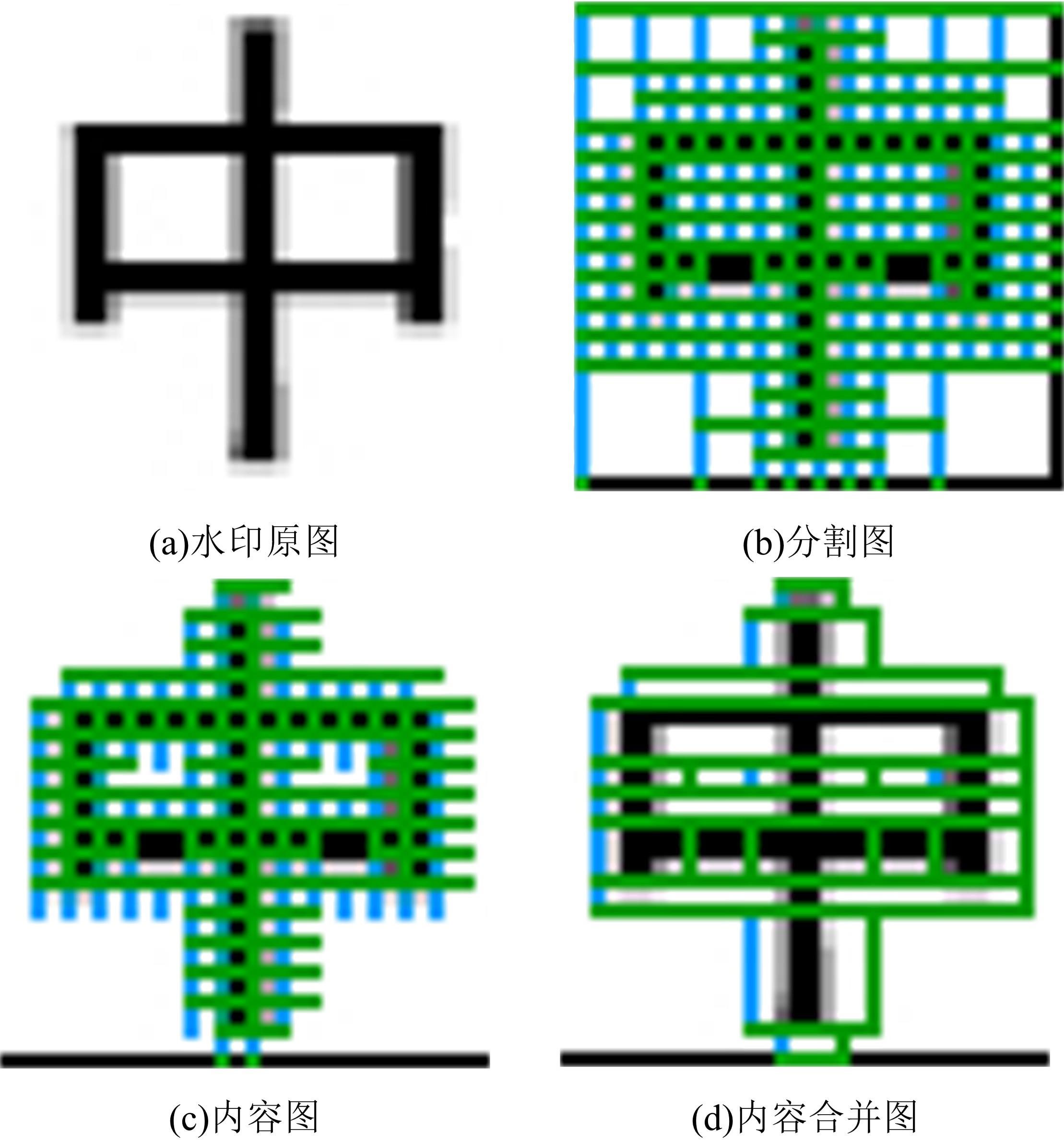
Journal of Jilin University(Engineering and Technology Edition) ›› 2022, Vol. 52 ›› Issue (1): 174-179.doi: 10.13229/j.cnki.jdxbgxb20200681
High-capacity and robust image watermarking algorithm
Xi-yan LI1,2( ),Xia-bing ZHOU3(
),Xia-bing ZHOU3( ),Zheng LIU1,4
),Zheng LIU1,4
- 1.State Key Laboratory of Mathematical Engineering and Advanced Computing,PLA Information Engineering University,Zhengzhou 450001,China
2.School of Information Science and Technology,Hainan Normal University,Haikou 571158,China
3.School of Computer Science and Technology,Soochow University,Suzhou 215006,China
4.School of Information on Engineering,Henan University of Animal Husbandry and Economy,Zhengzhou 450001,China
CLC Number:
- TP309
| 1 | Ernawan F, Kabir M N, Fadli M, et al. Block-based tchebichef image watermarking scheme using psychovisual threshold[C]∥International Conference on Science and Technology Computer (ICST), Yogyakarta, Indonesia, 2016. |
| 2 | Kumar S, Jain N, Fernandes S L. Rough set based effective technique of image watermarking[J]. Journal of Computational Science, 2017,19:121-137. |
| 3 | Su Po-chyi, Tien-ying Kuo,Li Meng-Huan. A practical design of digital watermarking for video streaming services[J]. Journal of Visual Communication and Image Representation, 2017,42:161-172. |
| 4 | Shao Zhu-hong, Shang Yuan-yuan, Zeng Rui, et al. Robust watermarking scheme for color image based on quaternion-type moment invariants and visual cryptography[J]. Signal Processing: Image Communication, 2016,48:12-21. |
| 5 | Quadry Khaza Mizbahuddin,Govardhan A,Mohammed Misbahuddin. A novel approach of Kurtosis based watermarking by using wavelet transformation[J]. International Journal of Image, Graphics and Signal Processing, 2018, 10(7):42-50. |
| 6 | 徐江峰,张守强. 基于QR码的DWT-DCT数字水印算法[J].计算机应用研究,2018,35(5):1540-1544. |
| Xu Jiang-feng, Zhang Shou-qiang. Algorithm of DWT-DCT digital watermarking based on QR code[J]. Application Research of Computers,2018,35(5):1540-1544. | |
| 7 | 顾宇鑫, 马小虎. 采用稀疏变换和拉普拉斯金字塔的数字水印算法[J].计算机辅助设计与图形学学报,2018,30(5):901-910. |
| Gu Yu-xin, Ma Xiao-hu. Digital watermarking algorithm using sparse transform and Laplace pyramid[J]. Journal of Computer-aided Design & Computer Graphics,2018,30(5):901-910. | |
| 8 | Ernawan Ferda, Muhammad Nomani Kabir. A robust image watermarking technique with an optimal DCT-psychovisual threshold[J]. IEEE Access, 2018, 6:20464-20480. |
| 9 | Lai Chih-chin. An improved SVD-based watermarking scheme using human visual characteristics[J]. Optics Communications,2011,284(4):938-944. |
| 10 | Anoop Kumar Chaturvedi,Piyush Kumar Shukla. Data hiding and watermarking techniques: a survey[J]. International Journal of Computer Applications,2018,179(32):28-36. |
| 11 | Amit Kumar Singh, Dave Mayank, Mohan Anand. Hybrid technique for robust and imperceptible image watermarking in DWT–DCT–SVD domain[J]. National Academy Science Letters,2014,37(4):351-358. |
| 12 | Kavitha C, Sakthivel S. An effective mechanism for medical images authentication using quick response code[J]. Cluster Computing,2019,22:4375-4382. |
| 13 | 张元钦.基于DWT-DCT的图像数字水印技术的研究[D].北京:北京邮电大学计算机学院,2013. |
| Zhang Yuan-qin. Research of the image digital watermarking technique based on DWT-DCT algorithm[D]. Beijing:Beijing University of Posts and Telecommunications, College of Computer,2013. | |
| 14 | Kang Qing-bo, Li Ke, Yang Ji-chun. A digital watermarking approach based on DCT domain combining QR code and chaotic theory[C]∥IEEE and IFIP International Conference on Wireless and Optical communications Networks,Vijayawada, India,2014:127-137. |
| 15 | Seyyed Hossein Soleymania, Amir Hossein Taherinia. High capacity image data hiding of scanned text documents using improved quadtree[DB/OL].[2018-03-29]. . |
| 16 | 王小超,胡坤,胡建平. 结合BEMD与Hilbert曲线的重复嵌入图像水印算法[J]. 计算机辅助设计与图形学学报,2020,32(2):287-296. |
| Wang Xiao-chao,Hu Kun,Hu Jian-ping. Repeated embedding algorithm for image watermarking based on BEMD and Hilbert curve[J]. Journal of Computer-Aided Design & Computer Graphics,2020,32(2):287-296. | |
| 17 | Liu L, Chen W, Zheng W, et al. Structure-aware error diffusion approach using entropy-constrained threshold modulation[J]. The Visual Computer, 2014,30(10):1145-1156. |
| 18 | Li X. Edge-directed error diffusion halftoning[J]. IEEE Signal Processing Letters, 2006,13(11):688-690. |
| 19 | Singh Y K. Generalized error diffusion method for halftoning[C]∥IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore,India,2015:1-6. |
| 20 | Zhou Z, Arce G R, di Crescenzo G. Halftone visual cryptography[J]. IEEE Transactions on Image Processing,2006, 15(8):2441-2453. |
| 21 | Alasseur C, Constantinides A G, Husson L. Colour quantisation through dithering techniques[C]∥IEEE International Conference on Image Processing,Barcelona,Spain,2003:No.1-469-72. |
| [1] | WANG Ding-cheng, TIAN Cui-cui, CHEN Bei-jing, TIAN Yu-hang. Dual watermarking for color images based on 4D quaternion frequency domain [J]. 吉林大学学报(工学版), 2015, 45(4): 1336-1346. |
| [2] | WEN Quan,WANG Yu-fei,ZHANG Xin-peng. Buyer-seller watermarking protocol for unbinding problem [J]. 吉林大学学报(工学版), 2014, 44(5): 1447-1452. |
| [3] | WANG Dan, LI Yang, NIAN Gui-jun, WANG Ke. An inhomogeneity mask for spatial watermarking [J]. 吉林大学学报(工学版), 2013, 43(03): 771-775. |
| [4] | NIAN Gui-jun, LIU Hong-shi, WANG Dan, WANG Nai-dan. Analysis and realization of watermaking hiding in color picture [J]. 吉林大学学报(工学版), 2011, 41(增刊1): 339-343. |
| [5] | XU Wen-Li, WANG Ming-Yu, WANG Yu-Min. High capacity and robust digital watermarking scheme based on CDMA [J]. 吉林大学学报(工学版), 2011, 41(02): 547-0552. |
| [6] | NIAN Gui-jun, LIU Hong-shi,CHE Xiao-lei, SUN Xiao-ying. Prediction error filter applied in blind additive watermarking algorithm [J]. 吉林大学学报(工学版), 2011, 41(01): 249-0253. |
| [7] | Zheng Hai-hong,Zeng Ping,Wang Yi-feng . Robust watermarking algorithm based on polarity modulation [J]. 吉林大学学报(工学版), 2007, 37(03): 681-0685. |
| [8] | Zheng Hai-hong,Wang Yi-feng,Zeng Ping,Kong Yue-ping,Xu Pei-pei . Watermarking algorithm for halftone images based on human visual system [J]. 吉林大学学报(工学版), 2006, 36(05): 782-0786. |
| [9] | ZHANG Guannan, WANG Shuxun, WEN Quan. Watermarking algorithm for halftone images by stochastic error diffusion [J]. 吉林大学学报(工学版), 2004, (4): 639-643. |
| [10] | ZHU Xiao-dong, YUAN Sen-miao, LIU Jing, QI Li-feng. Spatial domain digital watermarking algorithm [J]. 吉林大学学报(工学版), 2003, (2): 56-59. |
|
||