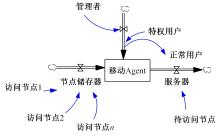
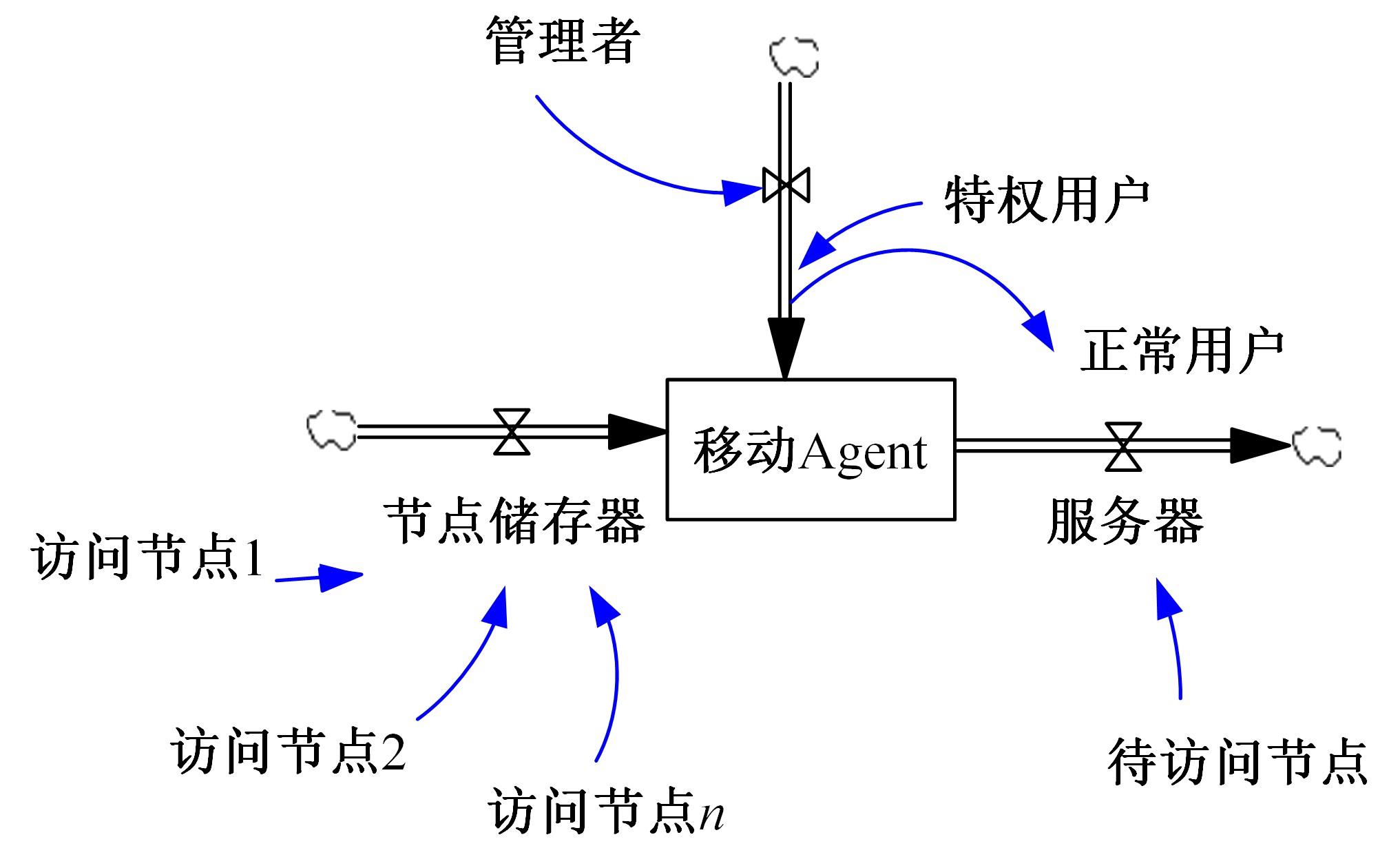
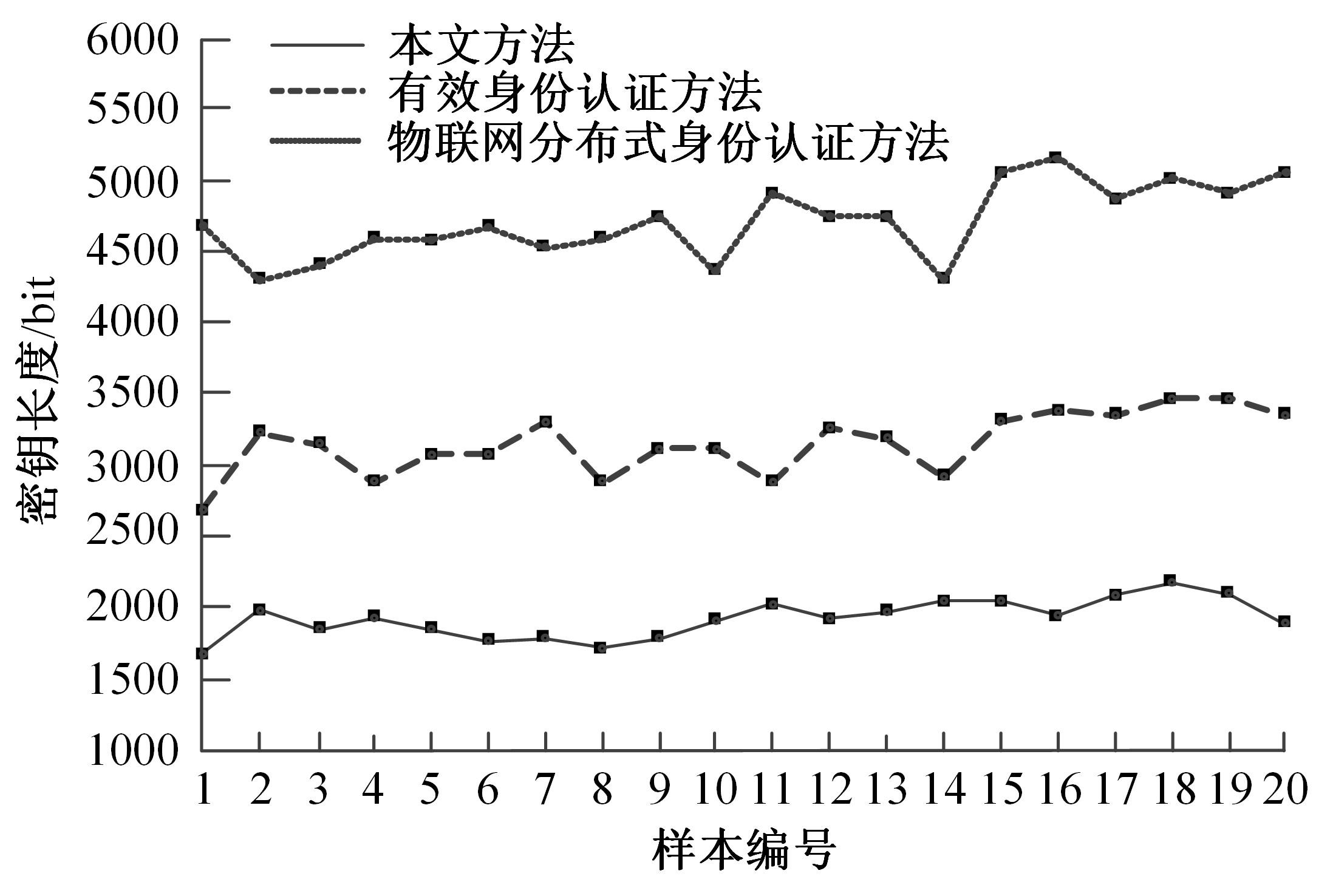
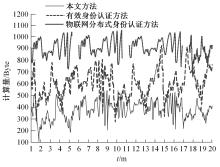
Journal of Jilin University(Engineering and Technology Edition) ›› 2024, Vol. 54 ›› Issue (3): 815-820.doi: 10.13229/j.cnki.jdxbgxb.20221524
Identity authentication of wireless power mobile terminal based on mobile Agent
Li ZHENG1,2( ),Guang-hui YAN1(
),Guang-hui YAN1( ),Tian-feng YAN1,2
),Tian-feng YAN1,2
- 1.School of Electronic and Information Engineering,Lanzhou Jiaotong University,Lanzhou 730070,China
2.Gansu Radio Monitoring and Positioning Industry Technology Center,Lanzhou Jiaotong University,Lanzhou 730070,China
CLC Number:
- TP393
| 1 | 胡畔, 聂祺昕, 刘晓强, 等. 基于离散域采样数据模型的电力移动终端边缘节点数据采集系统设计[J]. 中国测试, 2022, 48(8): 144-149. |
| Hu Pan, Nie Qi-xin, Liu Xiao-qiang, et al. Design of edge node data acquisition system of power mobile terminal based on discrete domain sampling data model[J]. China Measurement & Test, 2022,48(8): 144-149. | |
| 2 | 侯世玺, 付士利, 储云迪. 基于情感神经网络的有源电力滤波器智能终端滑模控制[J]. 控制与决策, 2022, 37(8): 2067-2076. |
| Hou Shi-xi, Fu Shi-li, Chu Yun-di. Emotional neural networks based intelligent terminal sliding mode control for active power filter[J]. Control and Decision, 2022, 37(8): 2067-2076. | |
| 3 | 刘那仁格日乐, 王郝日钦. 基于PKI技术的用户身份数据转发认证算法仿真[J]. 计算机仿真, 2020, 37(9): 373-376, 403. |
| Liu Na-rengerile, Wang Hao-riqin. Simulation of user identity data forwarding authentication algorithm based on PKI technology[J]. Computer Simulation, 2020, 37(9): 373-376, 403. | |
| 4 | 张翼英, 周保先, 庞浩渊, 等. 面向能源互联的电力物联网安全架构及技术[J]. 电信科学, 2021, 37(2): 115-124. |
| Zhang Yi-ying, Zhou Bao-xian, Pang Hao-yuan, et al. Electric internet of things security framework and technologies for energy interconnection[J]. Telecommunications Science, 2021, 37(2): 115-124. | |
| 5 | 刘浩然, 李帮俊, 王如竹. 基于FLUENT/MATLAB联合优化的移动终端功耗预算分配方法[J]. 工程热物理学报, 2022, 43(1): 233-239. |
| Liu Hao-ran, Li Bang-jun, Wang Ru-zhu. Power Budget allocation optimization of mobile devices via MATLAB/FLUENT Co-optimization[J]. Journal of Engineering Thermophysics, 2022,43(1): 233-239. | |
| 6 | 杜心雨, 王化群. LTE-A网络中基于动态组的有效的身份认证和密钥协商方案[J]. 计算机应用, 2021, 41(6): 1715-1722. |
| Du Xin-yu, Wang Hua-qun. Dynamic group based effective identity authentication and key agreement scheme in LTE-A networks[J]. Journal of Computer Applications, 2021,41(6): 1715-1722. | |
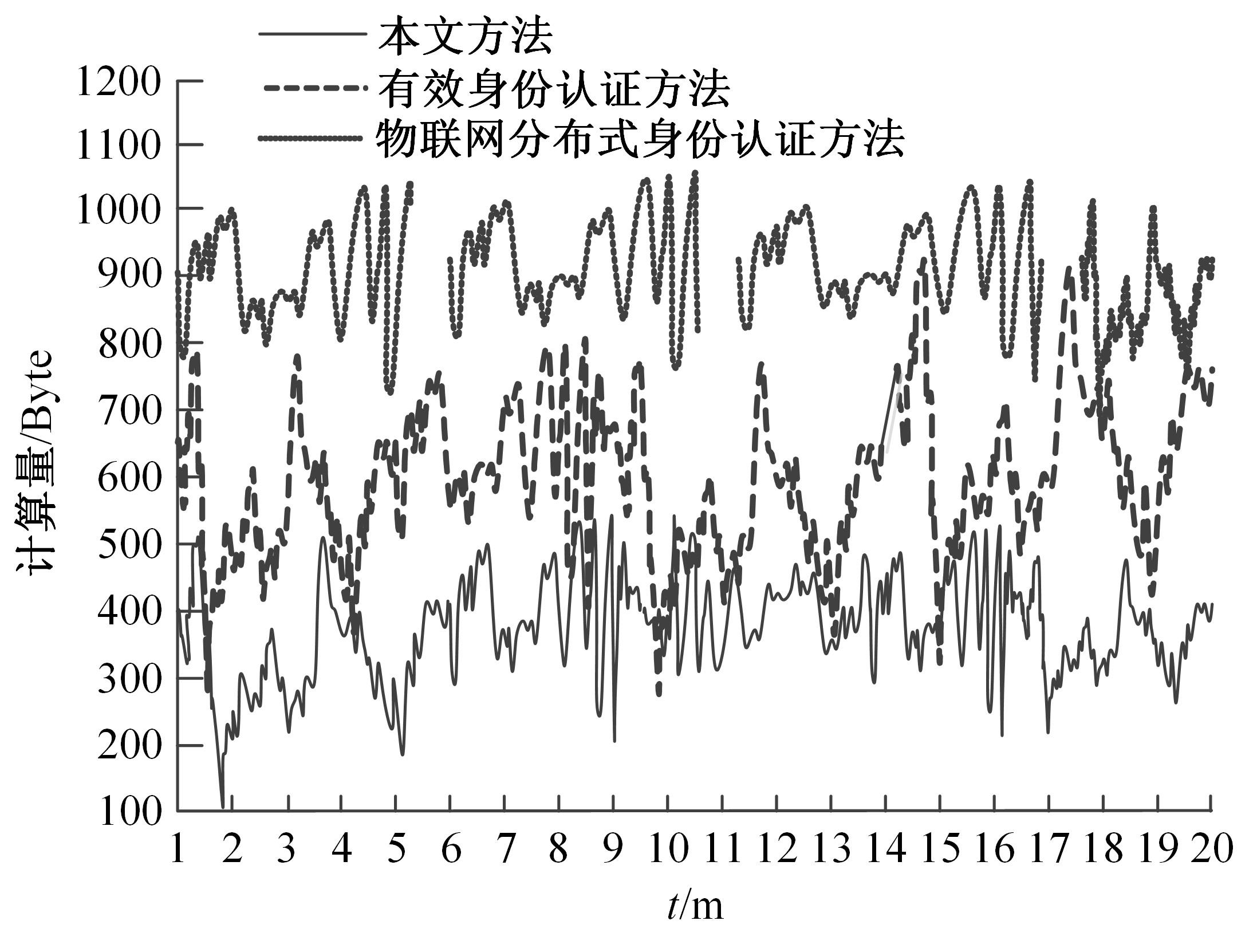
| 7 | 袁刚, 温圣军, 唐琦, 等. 基于共有区块链的物联网分布式身份验证方法[J]. 计算机工程与设计, 2021, 42(7): 1859-1866. |
| Yuan Gang, Wen Sheng-jun, Tang Qi, et al. Distributed authentication method of internet of things based on public blockchain[J]. Computer Engineering and Design, 2021,42(7): 1859-1866. | |
| 8 | 王凯, 宋礼鹏, 郑家杰. 融合击键内容和击键行为的持续身份认证[J]. 计算机工程与设计, 2020, 41(6): 1562-1567. |
| Wang Kai, Song Li-peng, Zheng Jia-jie. Continuous authentication fusing keystroke behavior and keystroke content[J]. Computer Engineering and Design, 2020, 41(6): 1562-1567. | |
| 9 | 翟峰, 杨挺, 曹永峰, 等. 基于区块链与K-means算法的智能电表密钥管理方法[J]. 电力自动化设备, 2020, 40(8): 38-46. |
| Zhai Feng, Yang Ting, Cao Yong-feng, et al. Key management method of smart meter based on blockchain and K-means algorithm[J]. Power Automation Equipment, 2020, 40(8): 38-46. | |
| 10 | 晏勇. 一种高效的物联网移动Agent路由规划算法[J]. 西南师范大学学报: 自然科学版, 2020, 45(11): 73-79. |
| Yan Yong. An efficient routing planning algorithm for mobile Agent in the IoT[J]. Journal of Southwest Normal University (Natural Science Edition), 2020, 45(11): 73-79. | |
| 11 | 蒋伟进, 吕斯健. 移动agent系统安全问题的动态信任计算模型[J]. 控制与决策, 2022, 37(2): 499-505. |
| Jiang Wei-jin, Lv Si-jian. Mobile internet mobile agent system dynamic trust model for cloudcomputing[J]. Control and Decision, 2022,37(2): 499-505. | |
| 12 | 金飞飞, 刘金培, 陈华友, 等. 基于信任关系和信息测度的概率语义社会网络群决策模型[J].中国管理科学, 2021, 29(10): 178-190. |
| Jin Fei-fei, Liu Jin-pei, Chen Hua-you, et al. Social network group decision-making model based on trust relationship and information measures with probabilistic linguistic information[J]. Chinese Journal of Management Science, 2021,29(10): 178-190. | |
| 13 | 邹萌, 张敏, 陈仪香. 面向安全属性的软件组件可信依赖关系度量模型[J]. 空间控制技术与应用, 2021, 47(2): 49-54. |
| Zou Meng, Zhang Min, Chen Yi-xiang. A novel trustworthiness measure model of trustworthy dependence relation between software components for security attributes[J]. Aerospace Control and Application, 2021,47(2): 49-54. | |
| 14 | 徐昭, 周昕, 白星, 等. 基于深度学习的相位截断傅里叶变换非对称加密系统攻击方法[J]. 物理学报, 2021, 70(14): 226-232. |
| Xu Zhao, Zhou Xin, Bai Xing, et al. Attacking asymmetric cryptosystem based on phase truncated Fourier fransform by deep learning[J]. Acta Physica Sinica, 2021, 70(14): 226-232. | |
| 15 | 石振国, 孙景玉. 无线可充能传感器网络的锚点算法与移动设备调度研究[J]. 计算机应用研究, 2021, 38(5): 1520-1523, 1528. |
| Shi Zhen-guo, Sun Jing-yu. Research of point tracing algorithm and mobile device scheduling in WRSN[J]. Application Research of Computers, 2021, 38(5): 1520-1523, 1528. | |
| 16 | 卢爱芬. 基于遍历异或运算的RFID移动认证协议[J]. 控制工程, 2021, 28(7): 1423-1429. |
| Lu Ai-fen. An RFID mobile authentication protocol based on ergodic XOR operation[J]. Control Engineering of China, 2021,28(7): 1423-1429. | |
| 17 | 张人上, 邱久睿. 基于混沌系统的扩频通信多源异构数据加密算法[J]. 火力与指挥控制, 2021, 46(8): 162-166, 176. |
| Zhang Ren-shang, Qiu Jiu-rui. Multi-source heterogeneous data encryption algorithm for spread spectrum communication based on chaotic system[J]. Fire Control & Command Control, 2021, 46(8): 162-166, 176. | |
| 18 | 车小亮, 周昊楠, 周潭平, 等. 基于NTRU的多密钥同态加密方案解密结构[J]. 计算机应用, 2020, 40(7): 1959-1964. |
| Che Xiao-liang, Zhou Hao-nan, Zhou Tan-ping, et al. Decryption structure of multi-key homomorphic encryption scheme based on NTRU[J]. Journal of Computer Applications, 2020, 40(7): 1959-1964. | |
| 19 | 薛建彬, 白子梅. 边缘计算中移动终端安全高效认证协议[J]. 北京邮电大学学报, 2021, 44(1): 110-116. |
| Xue Jian-bin, Bai Zi-mei. Security and efficient authentication scheme for mobile edge computing[J]. Journal of Beijing University of Posts and Telecommunications, 2021, 44(1): 110-116. |
| [1] | WU Jie-hong, ZHANG Lei, ZHANG Po, SHI Xiang-bin. Research of mobile agent active protection based on homomorphism encryption technology [J]. 吉林大学学报(工学版), 2013, 43(增刊1): 221-224. |
| [2] | CHEN Mian-shu, WANG Shi-peng, CHEN He-xin, SHENG Kai-ping, LI Pei-peng. Improved trust model based on recommendation evidence for P2P networks [J]. 吉林大学学报(工学版), 2013, 43(06): 1666-1674. |
| [3] | DU Jun, LI Wei-hua. Security trust model for multi-hop wireless ad hoc networks [J]. 吉林大学学报(工学版), 2011, 41(05): 1421-1425. |
| [4] | Bai Yan,Liu Da-you,Liu Jie . Ontologybased information alignment method in mobile Agent communication [J]. 吉林大学学报(工学版), 2007, 37(05): 1132-1136. |
| [5] | Bai Yan,Liu Da-you,Jiang Li . Multi-agent based open ontology services [J]. 吉林大学学报(工学版), 2007, 37(03): 587-0590. |
|
||