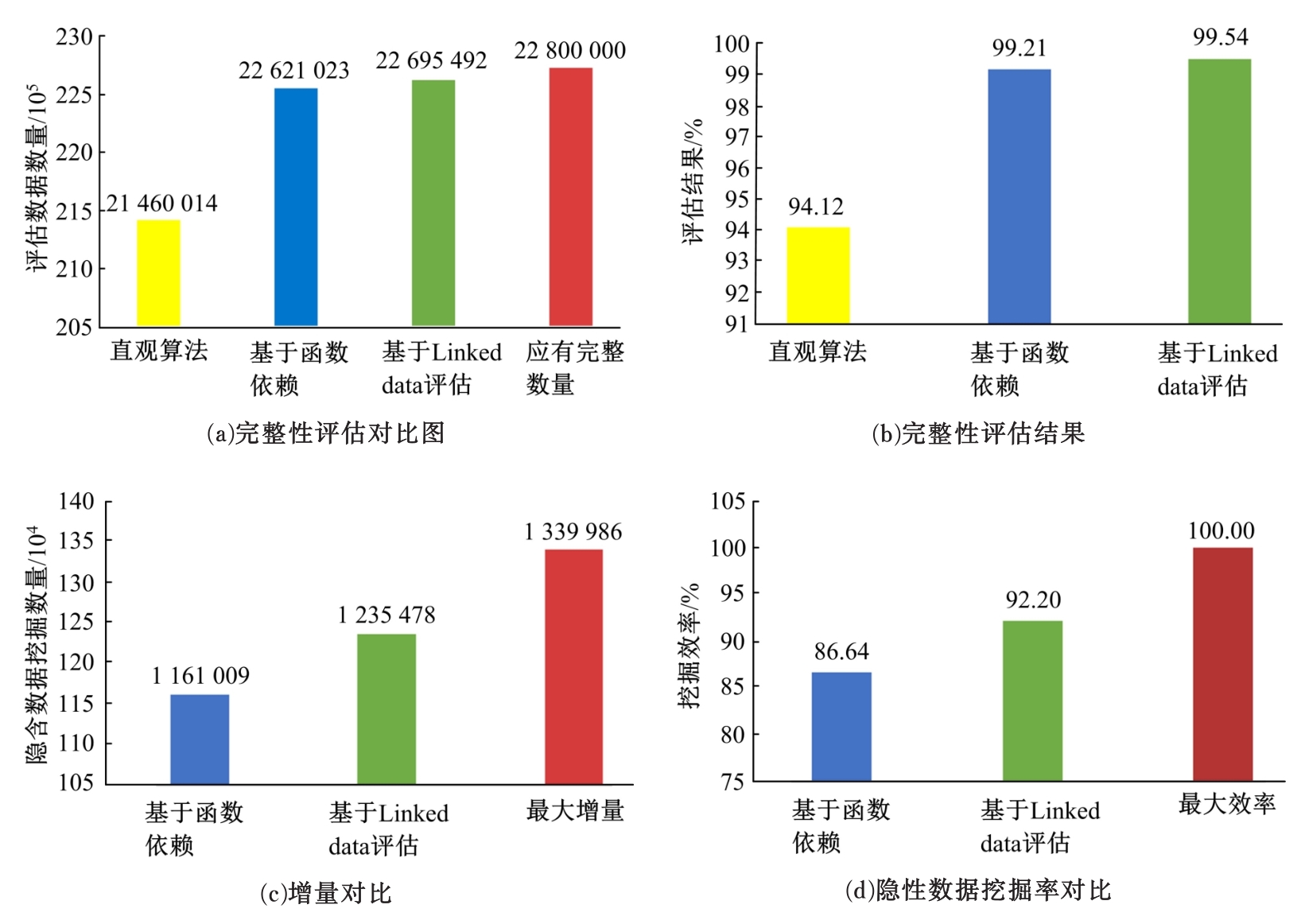
Journal of Jilin University(Engineering and Technology Edition) ›› 2020, Vol. 50 ›› Issue (5): 1826-1831.doi: 10.13229/j.cnki.jdxbgxb20190546
A new method for data integrity assessment based on Linked data
Man YUAN( ),Chao HU,Ting-ting QIU
),Chao HU,Ting-ting QIU
- School of Computer and Information Technology, Northeast Petroleum University, Daqing 163318, China
CLC Number:
- TP391
| 1 | 比特网. 大数据时代下的大数据到底有多大?[EB/OL]. (2014-03-06) [2019-03-18] |
| 2 | 白猫. 英特尔预测2020年全球数据量达44 ZB:中国占据五分之一[EB/OL]. (2017-9-19). [2019-03-19]. |
| 3 | Reza V, Mehran M, Jafar H. Measuring data quality with weighted metrics[J]. Total Quality Management & Business Excellence, 2019, 30(5/6): 708-720. |
| 4 | Redman T C. Seizing opportunity in data quality[J]. MIT Sloan Management Review, 2019, 60(2): 9-12. |
| 5 | Wang R Y, Reddy M P, Kon H B. Toward quality data: an attribute-based approach[J]. Decision Support Systems, 1995, 13(3/4): 349-372. |
| 6 | 刘永楠, 邹兆年, 李建中, 等. 数据完整性的评估方法[J]. 计算机研究与发展, 2013, 50(): 230-238. |
| Liu Yong-nan, Zou Zhao-nian, Li Jian-zhong, et al. Evaluation of data completeness[J]. Journal of Computer Research and Development, 2013, 50(Sup.1): 230-238. | |
| 7 | McDowall R D. Data integrity focus, part 1: understanding the scope of data integrity[J]. LC-GC North America, 2019, 37(1): 44-51. |
| 8 | Libkin L. Incomplete information and certain answers in general data models[C]∥Thirtieth ACM Sigmod-sigact-sigart Symposium on Principles of Database Systems, ACM, 2011: 59-70. |
| 9 | Arenas M, Pérez, J, Reutter J. Data exchange beyond complete data[J]. Journal of the ACM, 2013, 60(4): 83-94. |
| 10 | Fan W, Geerts F. Relative information completeness[J]. ACM Transactions on Database Systems, 2010, 35(4): 97-106. |
| 11 | Deng T, Fan W, Geerts F. Capturing missing tuples and missing values[J]. ACM Transactions on Database Systems, 2016, 41(2): 1-47. |
| 12 | Razniewski S, Nutt W. Completeness of queries over incomplete databases[J]. Proceedings of the Vldb Endowment, 2011, 4(11): 749-760. |
| 13 | Biswas J, Naumann F, Qiu Q. Assessing the completeness of sensor data[C]∥Database Systems for Advanced Applications, Singapore, 2006: 717-732. |
| 14 | Naumann F, Freytag J C, Leser U. Completeness of integrated information sources[J]. Information Systems, 2004, 29(7): 583-615. |
| 15 | Pfeiffer M. Data intergrity[J]. Die Pharmazeutiseche Industrie(Pharmind), 2017, 79(5): 736-741. |
| 16 | Strobin L, Niewiadomski A. Integration of multiple graph datasets and their linguistic summaries: an application to linked data[C]∥15th International Conference, Zakopane, Poland, 2016: 333-343. |
| 17 | Böckerman P, Ilmakunnas P. Do good working conditions make you work longer? Analyzing retirement decisions using linked survey and register data[J]. The Journal of the Economics of Ageing, 2019,49(5): 1-26. |
| 18 | 李楠, 张学福. 基于关联数据的知识发现模型研究[J]. 图书馆学研究, 2013(1): 73-77, 67. |
| Li Nan, Zhang Xue-fu. Research on knowledge discovery model based on linked data[J]. Researches in Library Science, 2013(1): 73-77, 67. | |
| 19 | Alessandreia O, Gabriel T, Gleiph G, et al. An efficient similarity-based approach for comparing XML documents[J]. Information Systems, 2018, 78: 40-57. |
| 20 | Eddamiri S, Zemmouri E M, Benghabrit A. An improved RDF data clustering algorithm[J]. Procedia Computer Science, 2019, 148: 208-217. |
| 21 | 徐光伟, 白艳珂, 燕彩蓉, 等. 大数据存储中数据完整性验证结果的检测算法[J]. 计算机研究与发展, 2017, 54(11): 2487-2496. |
| Xu Guang-wei, Bai Yan-ke, Yan Cai-rong, et al. Check algorithm of data integrity verification results in big data storage[J]. Journal of Computer Research and Development, 2017, 54(11): 2487-2496. | |
| 22 | Mao J, Cui J, Zhang Y, et al. Collaborative outsourced data integrity checking in multi-cloud environment[C]∥International Conference on Wireless Algorithms, Bozeman, USA, 2016: 511-523. |
| 23 | 谭霜, 何力, 陈志坤, 等. 云存储中一种基于格的数据完整性验证方法[J].计算机研究与发展, 2015, 52(8): 1862-1872. |
| Tan Shuang, He Li, Chen Zhi-kun, et al. A method of provable data integrity based on lattice in cloud storage[J]. Journal of Computer Research and Development, 2015, 52(8): 1862-1872. | |
| 24 | 杜岳峰, 申德荣, 聂铁铮, 等. 基于关联数据的一致性和时效性清洗方法[J]. 计算机学报, 2017, 40(1): 92-106. |
| Du Yue-feng, Shen De-rong, Nie Tie-zheng, et al. A cleaning method for consistency and currency in related data[J]. Chinese Journal of Computers, 2017, 40(1): 92-106. | |
| 25 | 陈龙, 李俊中. 支持不同粒度运算的远程数据完整性验证[J]. 吉林大学学报: 工学版, 2012, 42(): 295-299. |
| Chen Long, Li Jun-zhong. Verifiable method for remote data integrity supporting different granular operation[J]. Journal of Jilin University(Enhineering and Technology Edition), 2012, 42(Sup.1): 295-299. | |
| 26 | 陈晓慧, 张伟. 基于混沌的协同商务数据完整性验证方法[J]. 吉林大学学报: 工学版, 2009, 39(4): 1080-1084. |
| Chen Xiao-hui, Zhang Wei. Data integrality validation of collaborative business based on chaos[J]. Journal of Jilin University(Enhineering and Technology Edition), 2009, 39(4): 1080-1084. |
| [1] | Lei LIU,Jie WENG,De-gui GUO. Static input determination method in partial evaluation for compiler test [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 262-267. |
| [2] | MA Jian, FAN Jian-ping, LIU Feng, LI Hong-hui. The evolution model of objective-oriented software system [J]. 吉林大学学报(工学版), 2018, 48(2): 545-550. |
| [3] | LUO Yang-xia, GUO Ye. Software recognition based on features of data dependency [J]. 吉林大学学报(工学版), 2017, 47(6): 1894-1902. |
| [4] | YING Huan, WANG Dong-hui, WU Cheng-gang, WANG Zhe, TANG Bo-wen, LI Jian-jun. Efficient deterministic replay technique on commodity system environment [J]. 吉林大学学报(工学版), 2017, 47(1): 208-217. |
| [5] | LI Yong, HUANG Zhi-qiu, WANG Yong, FANG Bing-wu. New approach of cross-project defect prediction based on multi-source data [J]. 吉林大学学报(工学版), 2016, 46(6): 2034-2041. |
| [6] | WANG Nian-bin, ZHU Guan-wen, ZHOU Lian-ke, WANG Hong-wei. Novel dataspace index for efficient processing of path query [J]. 吉林大学学报(工学版), 2016, 46(3): 911-916. |
| [7] | CHEN Peng-fei, TIAN Di, YANG Guang. Design and implementation of LIBS software based on MVC architecture [J]. 吉林大学学报(工学版), 2016, 46(1): 242-245. |
| [8] | TE Ri-gen, JIANG Sheng, LI Xiong-fei, LI Jun. Document compression scheme based on integer data [J]. 吉林大学学报(工学版), 2016, 46(1): 228-234. |
| [9] | FENG Xiao-ning, WANG Zhuo, ZHANG Xu. Formal method for routing protocol of WSN based on L-π calculus [J]. 吉林大学学报(工学版), 2015, 45(5): 1565-1571. |
| [10] | LIU Lei, WANG Yan-yan, SHEN Chun, LI Yu-xiang, LIU Lei. Performance portable GPU parallel optimization technique on Bellman-Ford algorithm [J]. 吉林大学学报(工学版), 2015, 45(5): 1559-1564. |
| [11] | LI Ming-zhe, WANG Jin-lin, CHEN Xiao, CHEN Jun. Architecture model of streaming media applications on network processors(VPL) [J]. 吉林大学学报(工学版), 2015, 45(5): 1572-1580. |
| [12] | WANG Ke-chao, WANG Tian-tian, SU Xiao-hong, MA Pei-jun. Plagiarism detection in student programs based on frequent closed sequence mining [J]. 吉林大学学报(工学版), 2015, 45(4): 1260-1265. |
| [13] | HUANG Hong-tao,WANG Jing,YE Hai-zhi,HUANG Shao-bin. Lazy slicing based method for verifying linear temporal logic property [J]. 吉林大学学报(工学版), 2015, 45(1): 245-251. |
| [14] | HE Qin-lu, LI Zhan-huai, WANG Le-xiao, WANG Rui. Testing technology for aggregate bandwidth of cloud storage system [J]. 吉林大学学报(工学版), 2014, 44(4): 1104-1111. |
| [15] | FAN Da-juan, HUANG Zhi-qiu, XIAO Fang-xiong, ZHU Yi, WANG Jin. Compatibility analysis and adaptor generation for multi-service interaction [J]. 吉林大学学报(工学版), 2014, 44(4): 1094-1103. |
|
||