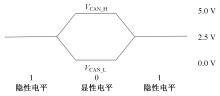
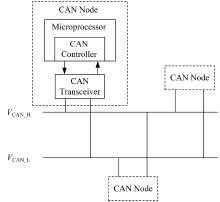
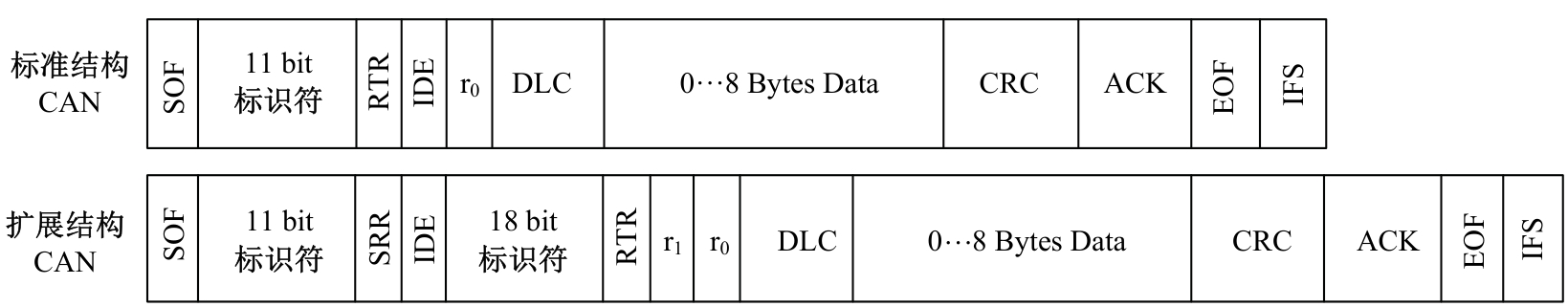
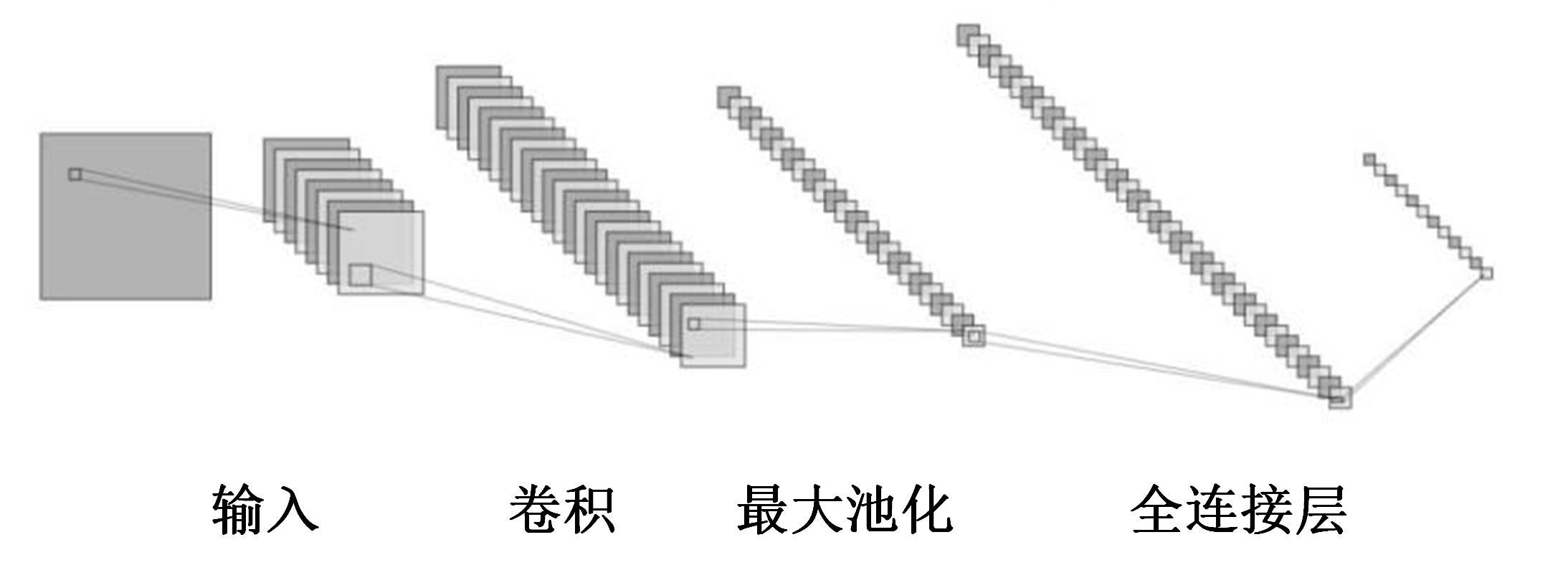
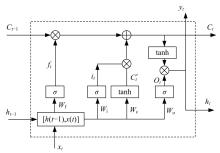
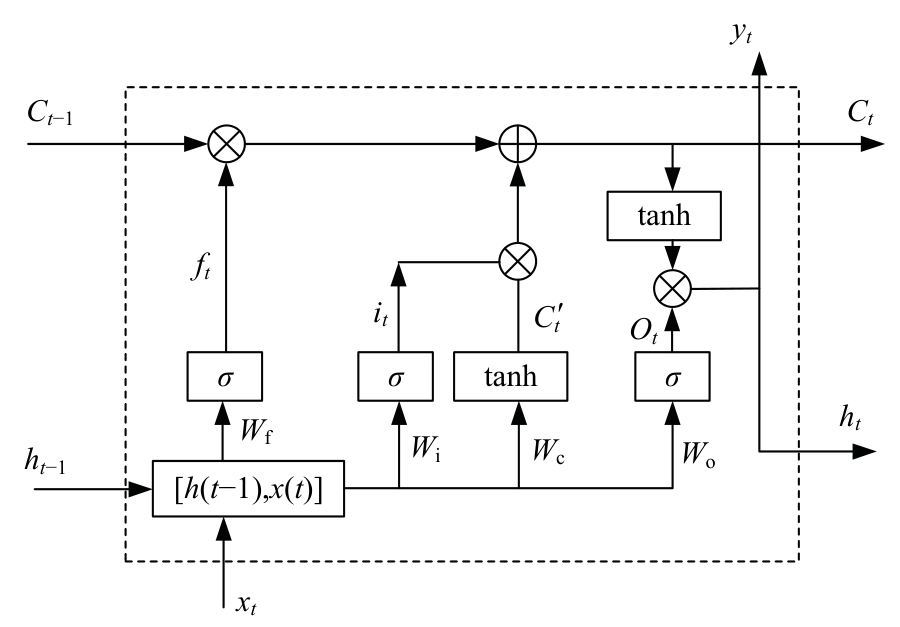
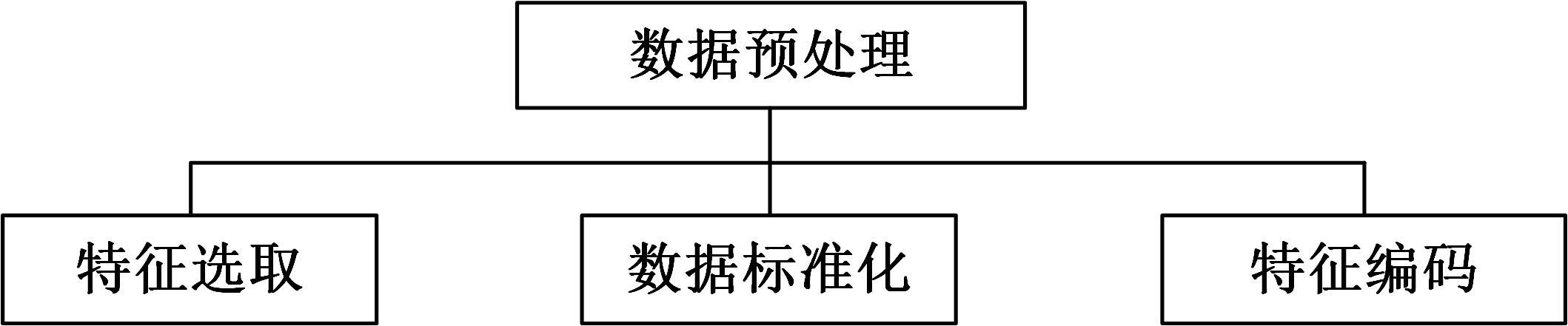
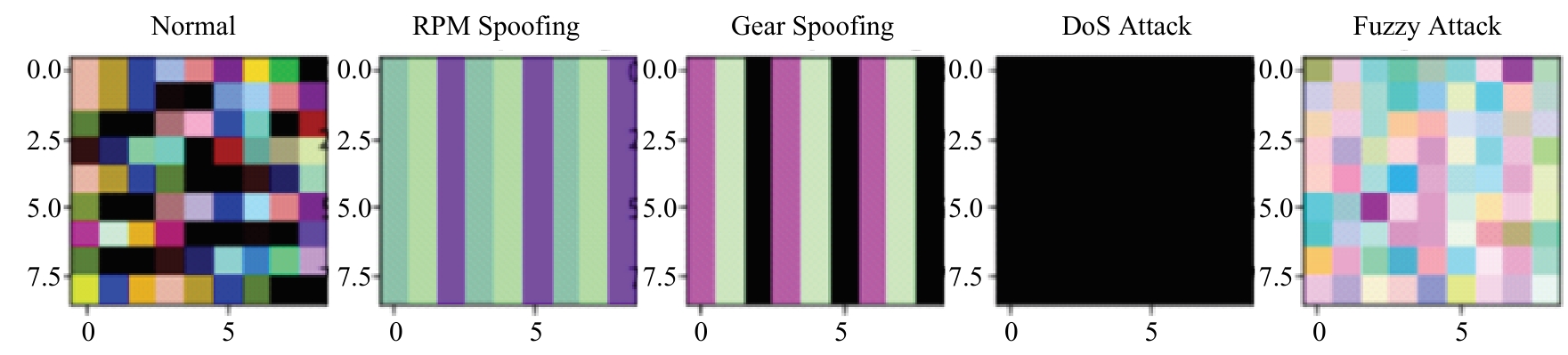
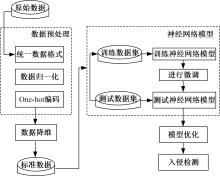
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (3): 857-865.doi: 10.13229/j.cnki.jdxbgxb.20240044
Previous Articles Next Articles
In⁃vehicle network intrusion detection system based on CAN bus data
Yin-fei DAI( ),Xiu-zhen ZHOU,Yu-bao LIU(
),Xiu-zhen ZHOU,Yu-bao LIU( ),Zhi-yuan LIU
),Zhi-yuan LIU
- School of Computer Science and Technology,Changchun University,Changchun 130022,China
CLC Number:
- TP393
| 1 | Miller C, Valasek C. Remote exploitation of an unaltered passenger vehicle[J]. Black Hat USA, 2015, 2015(S91): 1-91. |
| 2 | Javed A R, Ur Rehman S, Khan M U, et al. CANintelliIDS: detecting in-vehicle intrusion attacks on a controller area network using CNN and attention-based GRU[J]. IEEE Transactions on Network Science and Engineering, 2021, 8(2): 1456-1466. |
| 3 | Kim S H, Seo S H, Kim J H, et al. A gateway system for an automotive system: LIN, CAN, and FlexRay[C]∥6th IEEE International Conference on Industrial Informatics, Foshan, China, 2008: 967-972. |
| 4 | Farsi M, Ratcliff K, Barbosa M. An overview of controller area network[J]. Computing & Control Engineering Journal, 1999, 10(3): 113-120. |
| 5 | 朱鹏程, 涂江健, 招志才, 等. 车联网威胁分析和入侵检测关键技术[J]. 自动化博览, 2022,39(1):88-93. |
| Zhu Peng-cheng, Tu Jiang-jian, Zhao Zhi-cai, et al. Key technologies for threat analysis and intrusion detection in telematics[J]. Automation Expo, 2022, 39(1): 88-93. | |
| 6 | Checkoway S, McCoy D, Kantor B, et al. Comprehensive experimental analyses of automotive attack surfaces[C]∥20th USENIX Security Symposium,San Francisco,USA, 2011: 99-114. |
| 7 | Xu Z, Wang Z. Feature selection-based intrusion detection system for internet of vehicles[J]. IEEE Transactions on Intelligent Transportation Systems,2021,22(1): 1-11. |
| 8 | Song Y, Du J, Chen X, et al. Anomaly detection algorithm based on improved one-class support vector machine[J]. Journal of Ambient Intelligence and Humanized Computing,2019, 10(1): 219-228. |
| 9 | Wu S, Xu J, Wang Y,et al. Anomaly detection algorithm based on improved spectral clustering[J]. Journal of Ambient Intelligence and Humanized Computing,2022, 13(1): 513-521. |
| 10 | 丁宝星. 基于人工智能的网络入侵检测与防御研究[J]. 中国信息化, 2023(11): 76-78. |
| Ding Bao-xing. Research on network intrusion detection and defense based on artificial intelligence[J]. China Informatization, 2023(11):76-78. | |
| 11 | 陈力, 王海江, 吴凯. 基于卷积神经网络的车载网络入侵检测方法[J].浙江科技学院学报, 2021, 33(1):59-66, 84. |
| Chen Li, Wang Hai-jiang, Wu Kai. Intrusion detection method for in-vehicle networks based on convolutional neural networks[J]. Journal of Zhejiang Institute of Science and Technology, 2021, 33(1):59-66, 84. | |
| 12 | Zhang J, Wu Z C, Li F, et al. A deep learning framework for driving behavior identification on in-vehicle CAN-BUS sensor data[J]. Sensors, 2019, 19(6): 1356. |
| 13 | Chung J, Gulcehre C, Cho K H, et al. Empirical evaluation of gated recurrent neural networks on sequence modeling[J/OL]. [2024-01-05]. |
| 14 | 关宇昕, 冀浩杰, 崔哲, 等. 智能网联汽车车载CAN网络入侵检测方法综述[J]. 汽车工程, 2023,45(6): 922-935. |
| Guan Yu-xin, Ji Hao-jie, Cui Zhe, et al. A review of intrusion detection methods for in-vehicle CAN networks in smart connected vehicles[J]. Automotive Engineering,2023, 45(6): 922-935. | |
| 15 | Sun H, Chen M, Weng J, et al. Anomaly detection for in-vehicle network using CNN-LSTM with attention mechanism[J]. IEEE Transactions on Vehicular Technology, 2021, 70(10): 10880-10893. |
| 16 | Seo E, Song H M, Kim H K. GIDS: GAN based intrusion detection system for in-vehicle network[C]∥16th Annual Conference on Privacy, Security and Trust (PST),Waterloo, Canada,2018: 1-6. |
| 17 | Ergen T, Kozat S S. Unsupervised anomaly detection with LSTM neural networks[J]. IEEE transactions on Neural Networks and Learning Systems, 2019, 31(8): 3127-3141. |
| 18 | Song H M, Kim H K. Can network intrusion datasets[EB/OL].[2024-01-06]. |
| [1] | Hua-zhen FANG,Li LIU,Qing GU,Xiao-feng XIAO,Yu MENG. Driving intention recognition based on trajectory prediction and extreme gradient boosting [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(2): 623-630. |
| [2] | Xiao-dong CAI,Qing-song ZHOU,Yan-yan ZHANG,Yun XUE. Social recommendation based on global capture of dynamic, static and relational features [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(2): 700-708. |
| [3] | Hao WANG,Bin ZHAO,Guo-hua LIU. Temporal and motion enhancement for video action recognition [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(1): 339-346. |
| [4] | Lei ZHANG,Jing JIAO,Bo-xin LI,Yan-jie ZHOU. Large capacity semi structured data extraction algorithm combining machine learning and deep learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(9): 2631-2637. |
| [5] | Ping YU,Kang ZHAO,Jie CAO. Rolling bearing fault diagnosis based on optimized A-BiLSTM [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(8): 2156-2166. |
| [6] | Cheng CHEN,Pei-xin SHI,Peng-jiao JIA,Man-man DONG. Correlation analysis of shield driving parameters and structural deformation prediction based on MK-LSTM algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(6): 1624-1633. |
| [7] | Qiu-zhan ZHOU,Ze-yu JI,Cong WANG,Jing RONG. Non-intrusive load monitoring via online compression and reconstruction [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(6): 1796-1806. |
| [8] | Ling HUANG,Zuan CUI,Feng YOU,Pei-xin HONG,Hao-chuan ZHONG,Yi-xuan ZENG. Vehicle trajectory prediction model for multi-vehicle interaction scenario [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(5): 1188-1195. |
| [9] | Shi-feng NIU,Shi-jie YU,Yan-jun LIU,Chong MA. Real-time detection method of angry driving behavior based on bracelet data [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(12): 3505-3512. |
| [10] | Li-zhao DAI,Chong WANG,Ping YUAN,Lei WANG. Prediction model for shear capacity of corroded RC beams based on interpretable machine learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(11): 3231-3243. |
| [11] | Xian-feng REN,Wen-wen YUAN,Xue-qiang WU,Yan-ru SHI,Meng-meng YAO,Kai-xuan ZHANG,Rui-xin YANG,Yue PAN. Multi-dimensional aging diagnosis of lithium-ion battery with a long short-term memory neural network [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(11): 3135-3147. |
| [12] | Zhong-liang FU,Xiao-qing CHEN,Wei REN,Yu YAO. Random K-nearest neighbor algorithm with learning process [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(1): 209-220. |
| [13] | Qing-tian GENG,Zhi LIU,Qing-liang LI,Fan-hua YU,Xiao-ning LI. Prediction of soil moisture based on a deep learning model [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(8): 2430-2436. |
| [14] | Shuang LI,Zi-rui LIN,Song YE,Xu LIU,Ji-song ZHAO. Orbital capability evaluation and trajectory reconstruction for launch vehicle with thrust decline [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(8): 2245-2253. |
| [15] | Rong-han YAO,Wen-tao XU,Wei-wei GUO. Drivers' takeover behavior and intention recognition based on factor and long short⁃term memory [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(3): 758-771. |
|
||