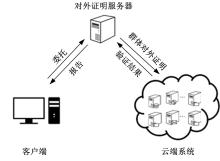
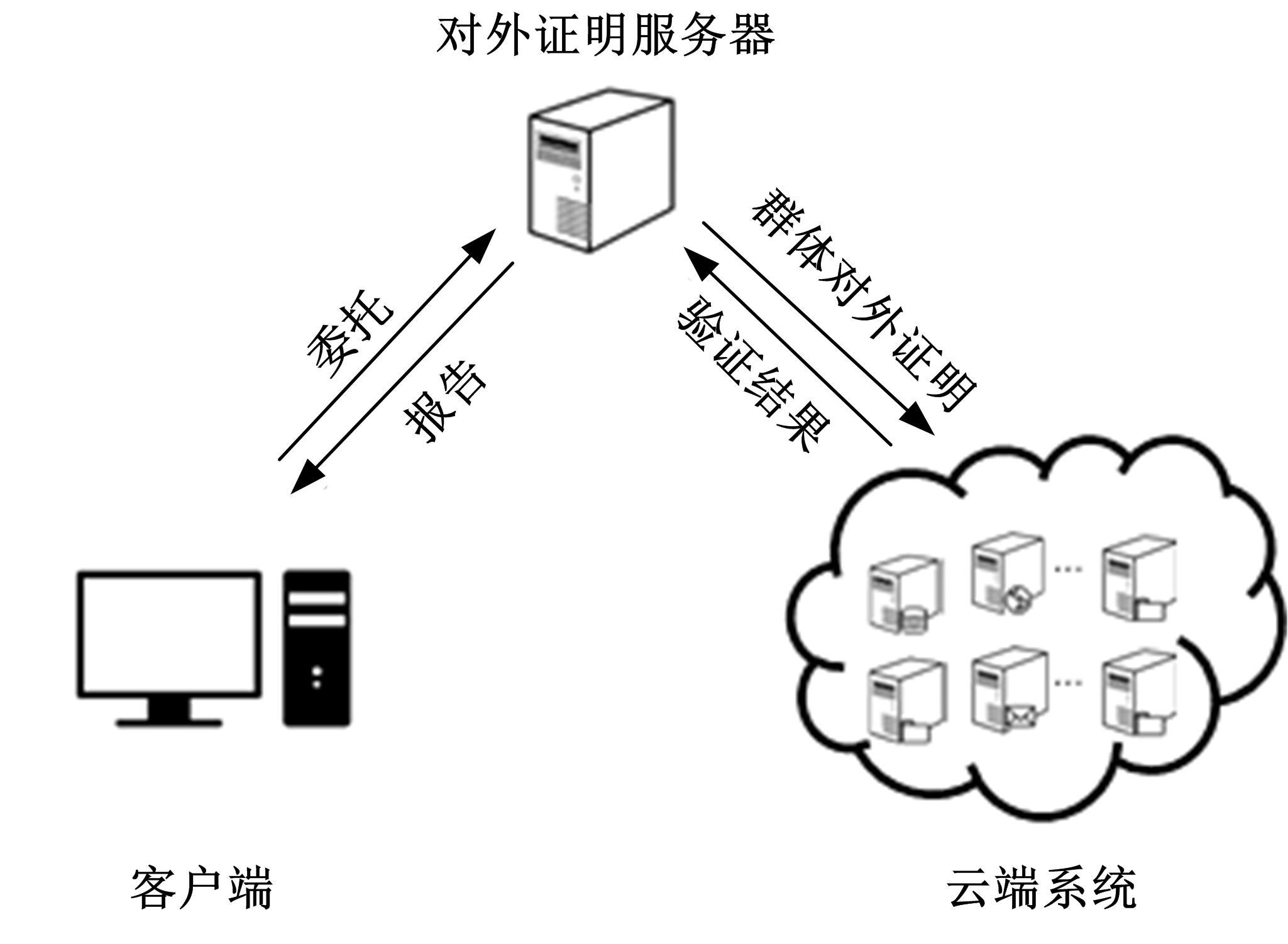
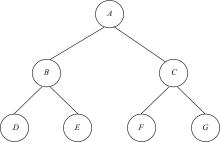
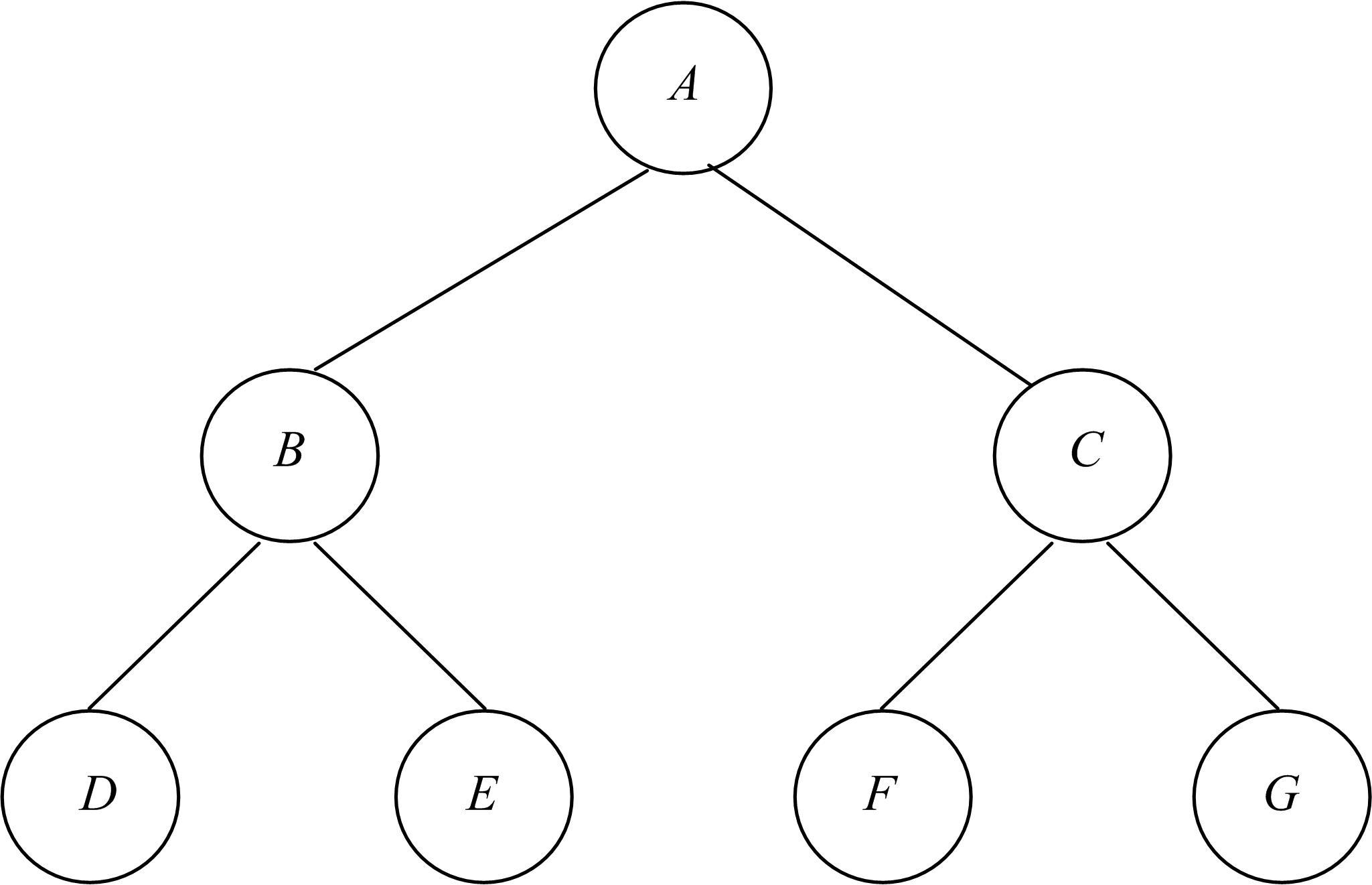
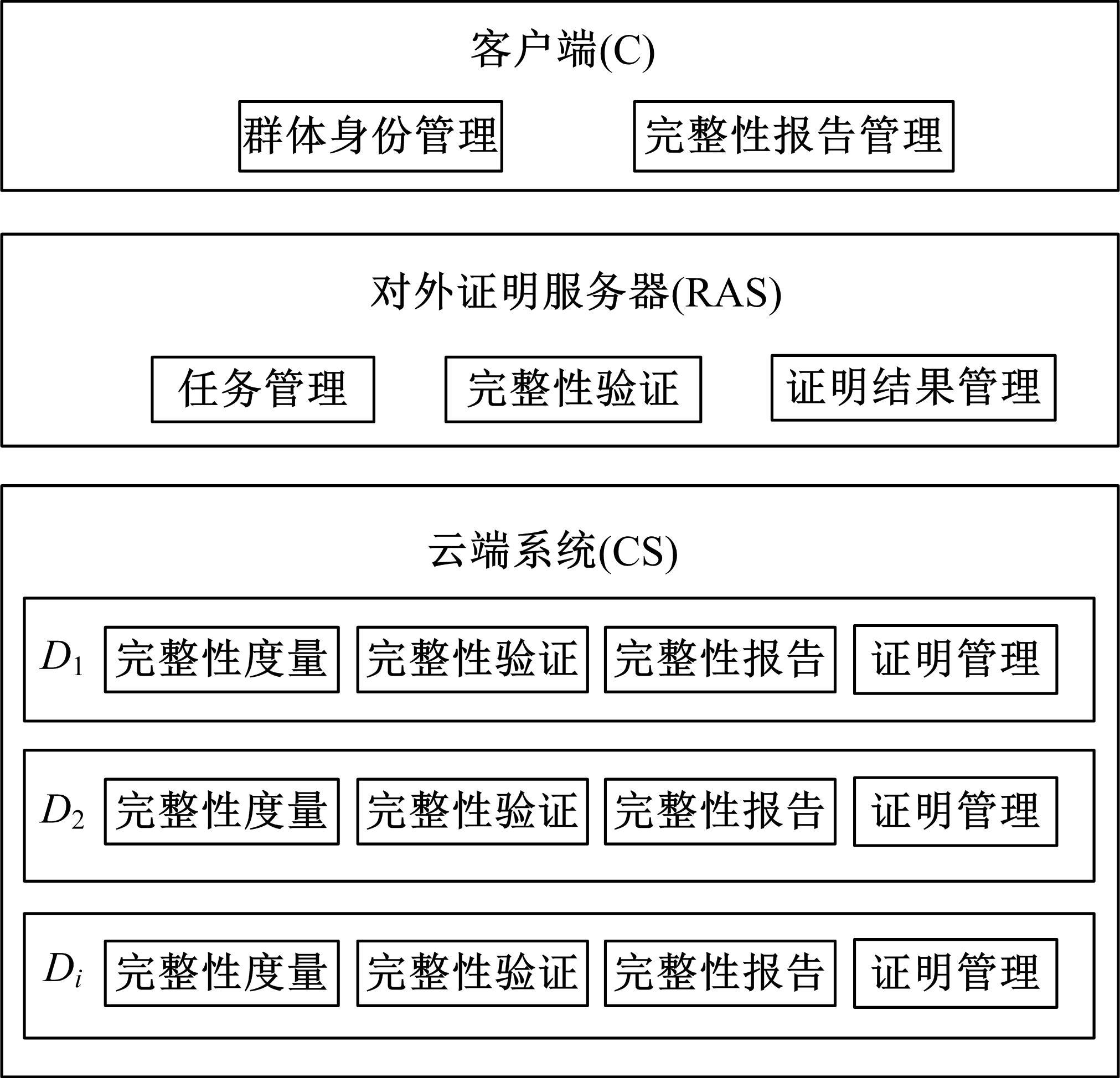
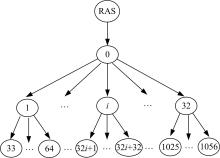
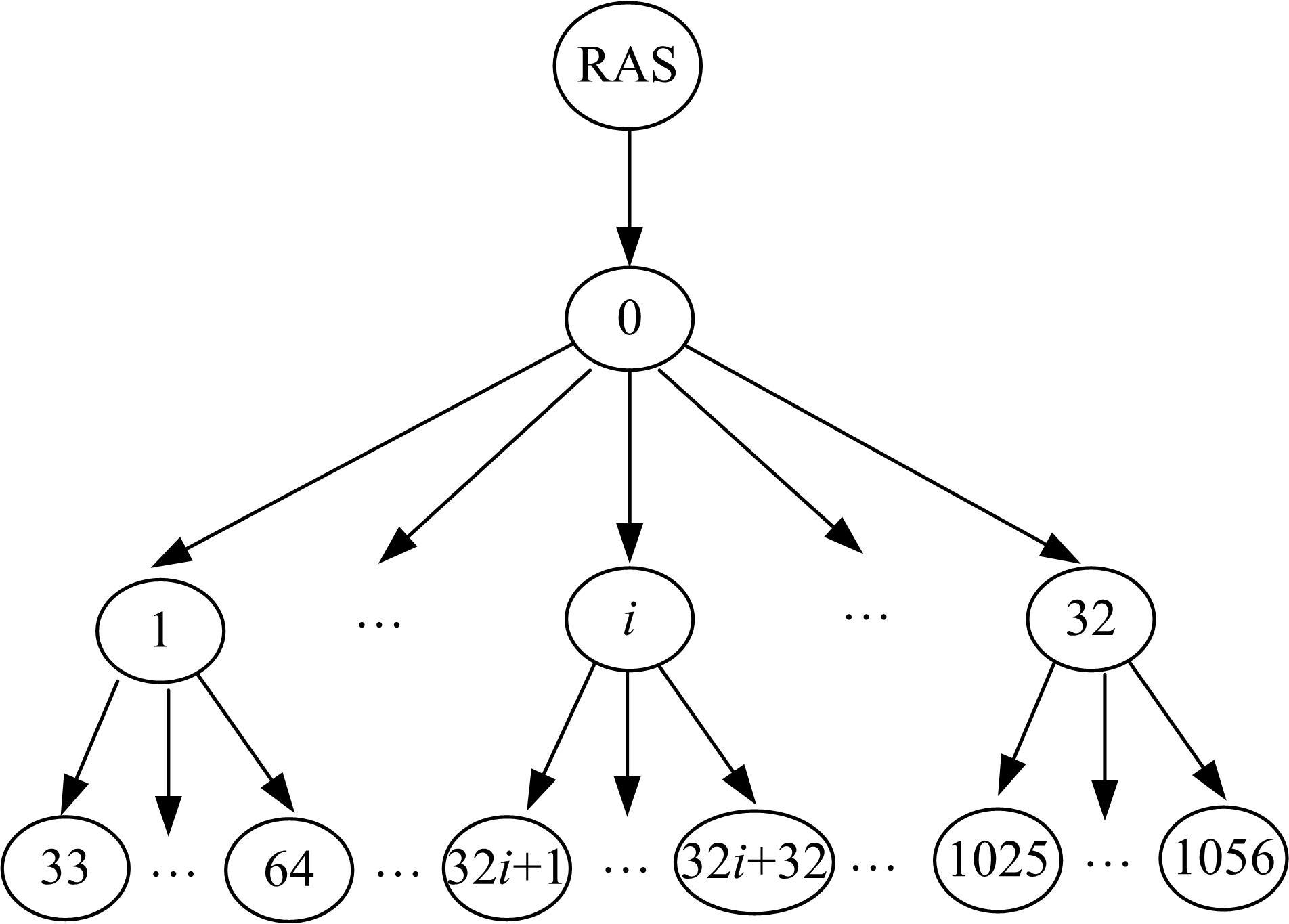
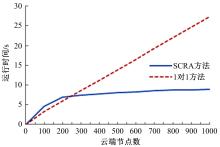
Journal of Jilin University(Engineering and Technology Edition) ›› 2021, Vol. 51 ›› Issue (6): 2198-2206.doi: 10.13229/j.cnki.jdxbgxb20210475
Scalable collective remote attestation towards cloud system
He-qing SONG1( ),Li-qiang YOU1,Yuan SONG2,Zhang-ye WANG3(
),Li-qiang YOU1,Yuan SONG2,Zhang-ye WANG3( )
)
- 1.Hangzhou College of Commerce,Zhejiang Gongshang University,Hangzhou 311500,China
2.School of Information,Renmin University,Beijing 100872,China
3.College of Computer Science and Technology,Zhejiang University,Hangzhou 310013,China
CLC Number:
- TP399
| 1 | Common vulnerabilities and exposures. CVE-ID: CVE-2021-31929[DB/OL].[2021-04-30]. |
| 2 | Common vulnerabilities and exposures. CVE-ID: CVE-2020-8933[DB/OL].[2020-02-12]. |
| 3 | Gao Xing, Steenkamer B, Gu Zhong-shu, et al. A study on the security implications of information leakages in container clouds[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(1): 174-191. |
| 4 | Patel S, Persiano G, Yeo K, et al. Mitigating leakage in secure cloud-hosted data structures: volume-hiding for multi-maps via hashing[C]∥Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019:79-93. |
| 5 | Bacis E, Paraboschi S, Foresti S, et al. Securing resources in decentralized cloud storage[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 286-298. |
| 6 | Cojocar L, Kim J, Patel M, et al. Are we susceptible to rowhammer? An end-to-end methodology for cloud providers[C]∥2020 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 2020: 712-728. |
| 7 | Ali T, Ismail R, Musa S, et al. Design and implementation of an attestation protocol for measured dynamic behavior[J]. The Journal of Supercomputing, 2018, 74(11): 5746-5773. |
| 8 | Weng Chu-liang, Liu Qian, Li Ken-li, et al. CloudMon: monitoring virtual machines in clouds[J]. IEEE Transactions on Computers, 2016, 65(12): 3787-3793. |
| 9 | Stephen A, Benedict S, Kumar R P A, et al. Monitoring IaaS using various cloud monitors[J]. Cluster Computing, 2019, 22(1): 12459-12471. |
| 10 | 何欣枫, 田俊峰, 刘凡鸣. 可信云平台技术综述[J]. 通信学报, 2019, 40(2): 154-163. |
| He Xin-feng, Tian Jun-feng, Liu Fan-ming. Survey on trusted cloud platform technology[J]. Journal on Communications, 2019, 40(2): 154-163. | |
| 11 | 冯登国, 刘敬彬, 秦宇, 等. 创新发展中的可信计算理论与技术[J].中国科学: 信息科学, 2020, 50(8): 1127-1147. |
| Feng Deng-guo, Liu Jing-bin, Qin Yu, et al. Trusted computing theory and technology in innovation-driven development[J]. Scientia Sinica(Informationis), 2020, 50(8): 1127-1147. | |
| 12 | Santos N, Gummadi K P, Rodrigues R, et al. Towards trusted cloud computing[C]∥IEEE International Conference on Cloud Computing Technology and Science, San Diego, CA, USA, 2009: 1-5. |
| 13 | Sen P, Saha P, Khatua S. A distributed approach towards trusted cloud computing platform[C]∥2015 Applications and Innovations in Mobile Computing (AIMoC), Kolkata, India, 2015: 146-151. |
| 14 | Asokan N, Brasser F, Ibrahim A, et al. SEDA: scalable embedded device attestation[C]∥Computer and Communications Security, Denver, USA, 2015: 964-975. |
| 15 | Sailer R, Zhang X L, Jaeger T, et al. Design and implementation of a TCG-based integrity measurement architecture[J/OL].[2021-04-27]. |
| 16 | Xing Bin, Han Zhen, Chang Xiao-lin, et al. OB-IMA: out-of-the-box integrity measurement approach for guest virtual machines[J]. Concurrency and Computation: Practice and Experience, 2015, 27(5): 1092-1109. |
| 17 | Zheng Wei, Wu Ying, Wu Xiao-xue, et al. A survey of intel SGX and its applications[J]. Frontiers of Computer Science, 2021, 15(3): 186-200. |
| 18 | Hua Zhi-chao, Gu Jin-yu, Xia Yu-bin, et al. vTZ: virtualizing ARM trustZone[C]∥The Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 2017: 541-556. |
| 19 | Wang Juan, Hong Zhi, Zhang Yu-han, et al. Enabling security-enhanced attestation with intel sgx for remote terminal and IoT[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2018, 37(1): 88-96. |
| 20 | Arnautov S, Trach B, Gregor F, et al. Scone: secure linux containers with intel SGX[C]∥The 12th USENIX Symposium on Operating Systems Design and Implementation, Savannah, GA, USA, 2016: 689-703. |
| 21 | Baumann A, Peinado M, Hunt G C. Shielding applications from an untrusted cloud with haven[J]. ACM Transactions on Computer Systems, 2015, 33(3): 1-26. |
| 22 | 陈璐, 柯文彬, 张立强, 等. 云计算环境下基于系统依赖图的远程证明方案[J]. 武汉大学学报:理学版, 2020, 66(4): 401-408. |
| Chen Lu, Ke Wen-bin, Zhang Li-qiang, et al. A remote attestation scheme based on system dependence graph in cloud computing environment[J]. Journal of Wuhan University(Natural Science Edition), 2020, 66(4): 401-408. | |
| 23 | 荣星, 沈昌祥, 江荣, 等. 基于双层非平衡散列树的云平台远程验证方案[J]. 通信学报, 2017, 38(9): 31-38. |
| Rong Xing, Shen Chang-xiang, Jiang Rong, et al. Remote attestation scheme for cloud platform based on double-layer unbalanced hash tree[J]. Journal on Communications, 2017, 38(9): 31-38. | |
| 24 | Ruan An-bang, Martin A. Repcloud: attesting to cloud service dependency[J]. IEEE Transactions on Services Computing, 2016, 10(5): 675-688. |
| 25 | Shim K. An ID-based aggregate signature scheme with constant pairing computations[J]. Journal of Systems and Software, 2010, 83(10): 1873-1880. |
| [1] | Yan-hua DONG,Jing-wei LIU,Jing-hua ZHAO,Liang LI,Fang-xi XIE. Real-time torque tracking control based on BPNN online learning prediction model [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1405-1413. |
| [2] | Xiao-hui WEI,Fang-yu TANG,Hong-liang LI. Cost-efficient resource allocation algorithm for scientific workflow accross geo-distributed data centers [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1349-1357. |
| [3] | Xiao-hui WEI,Chang-bao ZHOU,Xiao-xian SHEN,Yuan-yuan LIU,Qun-chao TONG. Accelerating CALYPSO structure prediction with machine learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 667-676. |
| [4] | Man CHEN,Yong ZHONG,Zhen-dong LI. Multi-focus image fusion based on latent low⁃rank representation combining low⁃rank representation [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 297-305. |
| [5] | Xiao-dong ZHANG,Xiao-jun XIA,Hai-feng LYU,Xu-chao GONG,Meng-jia LIAN. Dynamic load balancing of physiological data flow in big data network parallel computing environment [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 247-254. |
| [6] | ZHAO Hong-wei, LIU Yu-qi, DONG Li-yan, WANG Yu, LIU Pei. Dynamic route optimization algorithm based on hybrid in ITS [J]. 吉林大学学报(工学版), 2018, 48(4): 1214-1223. |
| [7] | ZHANG Hao, ZHAN Meng-ping, GUO Liu-xiang, LI Zhi, LIU Yuan-ning, ZHANG Chun-he, CHANG Hao-wu, WANG Zhi-qiang. Human exogenous plant miRNA cross-kingdom regulatory modeling based on high-throughout data [J]. 吉林大学学报(工学版), 2018, 48(4): 1206-1213. |
| [8] | CAO Jing-hua, KONG Fan-sen, RAN Yan-zhong. QoS-aware listwise collaborative ranking algorithm for service recommendation [J]. 吉林大学学报(工学版), 2018, 48(1): 274-280. |
| [9] | LIANG Shi-li, CHAI Zong-qian, ZHANG Ling, WU Yan-sheng, CAO Chun-lei. Image encryption method based on partial X type cellular automaton [J]. 吉林大学学报(工学版), 2017, 47(5): 1653-1660. |
| [10] | LIN Dong-mei, ZHANG Ai-hua, SHEN Rong, WANG Ping, YANG Li-ming, CHEN Xiao-lei. Dual-camera synchronous acquisition method for binocular vision pulse measurement system [J]. 吉林大学学报(工学版), 2015, 45(6): 1999-2006. |
| [11] | KANG Bing, LIU Fu, WEI Qi-wei. Palmprint fine line feature extraction based on spectral fusion [J]. 吉林大学学报(工学版), 2015, 45(4): 1274-1280. |
| [12] | LIU Fu,ZHANG Xiao,HOU Tao,LIU Yun. Attributes reduction of gene signal based on rough set [J]. 吉林大学学报(工学版), 2015, 45(2): 624-629. |
| [13] | LIU Yuan-ning, AI Lu-lu,DUAN Yun-na,LI Zhi,TIAN Ming-yao,ZHANG Hao. RNA pseudoknot prediction based on local structure interaction [J]. 吉林大学学报(工学版), 2015, 45(2): 613-618. |
| [14] | LIU Yuan-ning, XU Bao-lin, ZHANG Hao, CHEN Jing-bo, HAN Ye, YU Jian-long. Selecting highly effective siRNAs by thermodynamics of siRNA-mRNA binding [J]. 吉林大学学报(工学版), 2014, 44(01): 191-195. |
| [15] | WU Jia-nan, ZHOU Chun-guang, XIA Xue-fei, LIU Gui-xia, SHEN Wei, ZHOU You. Using simple statistical model to identify differentially expressed genes in microarray experiments [J]. 吉林大学学报(工学版), 2013, 43(04): 1059-1063. |
|
||