Journal of Jilin University(Engineering and Technology Edition) ›› 2021, Vol. 51 ›› Issue (6): 2253-2258.doi: 10.13229/j.cnki.jdxbgxb20200814
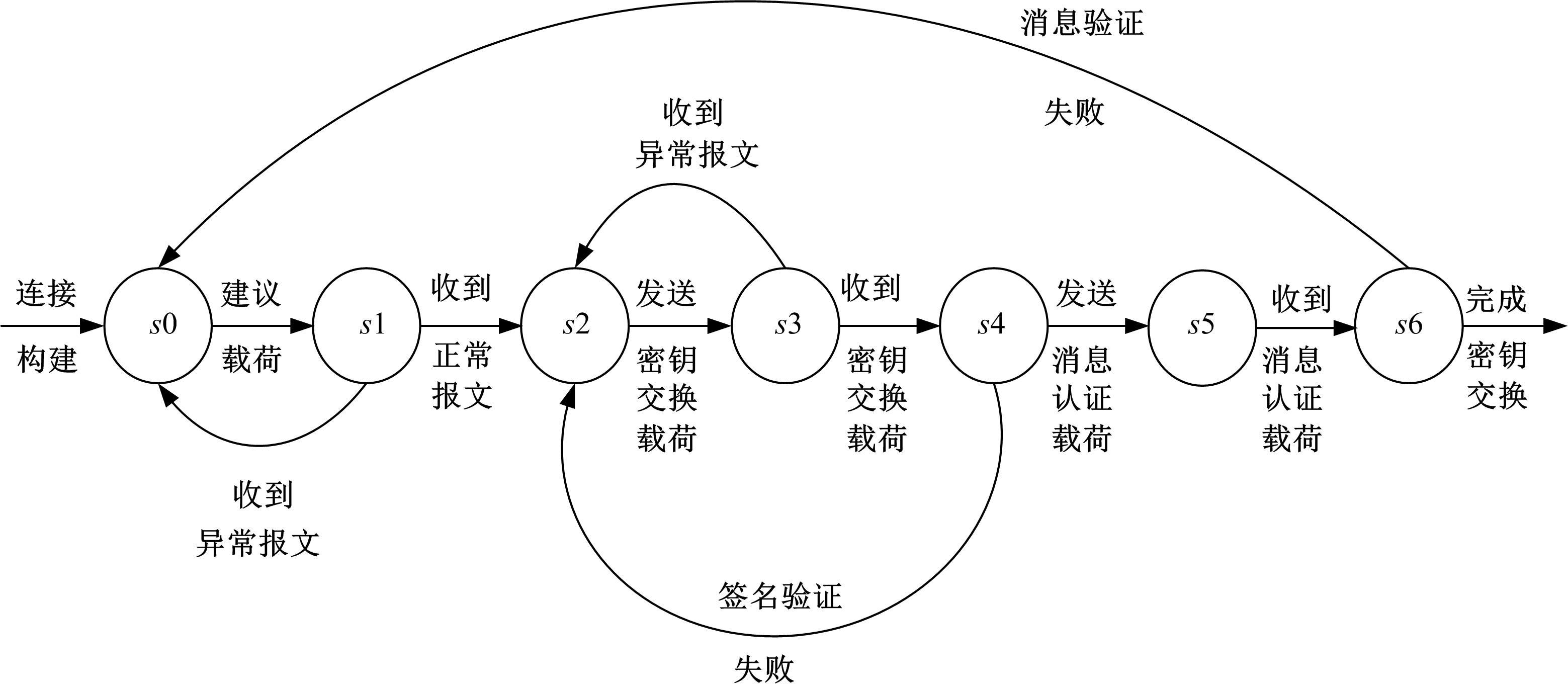
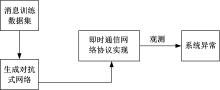
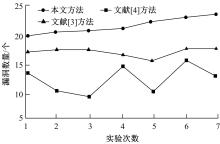
Vulnerability detection of instant messaging network protocol based on passive clustering algorithm
Jie ZHANG1( ),Wen JING1,Fu CHEN2
),Wen JING1,Fu CHEN2
- 1.School of Computer and Network Engineering,Shanxi Datong University,Datong 037009,China
2.School of Mathematics and Statistics,Shanxi Datong University,Datong 037009,China.
CLC Number:
- TP357
| 1 | 冯文博, 洪征, 吴礼发,等. 网络协议识别技术综述[J]. 计算机应用, 2019, 39(12):3604-3614. |
| Feng Wen-bo, Hong Zheng, Wu Li-fa, et al. Overview of network protocol identification technology [J]. Computer Applications, 2019, 39 (12): 3604-3614. | |
| 2 | Atilgan C, Nasibov E N. A space efficient minimum spanning tree approach to the fuzzy Joint points clustering algorithm[J]. IEEE Transactions on Fuzzy Systems, 2019, 27(6):1317-1322. |
| 3 | 邓兆琨, 陆余良, 黄钊, 等. 基于程序建模的网络程序漏洞检测技术[J]. 北京航空航天大学学报, 2019, 45(4):796-803. |
| Deng Zhao-kun, Lu Yu-liang, Huang Zhao, et al. Network program vulnerability detection technology based on program modeling[J]. Journal of Beijing University of Aeronautics and Astronautics, 2019, 45(4):796-803. | |
| 4 | 李佳莉, 陈永乐, 李志, 等. 基于协议状态图遍历的RTSP协议漏洞挖掘[J]. 计算机科学, 2018, 45(9):178-183. |
| Li Jia-li, Chen Yong-le, Li Zhi, et al. RTSP protocol vulnerability mining based on traversal of protocol state graph [J]. Computer Science, 2018, 45 (9): 178-183. | |
| 5 | Huang C, Molisch A F, Geng Y A, et al. Trajectory-Joint clustering algorithm for time-varying channel modeling[J]. IEEE Transactions on Vehicular Technology, 2020, 69(1):1041-1045. |
| 6 | 丁旭, 黄成, 吴晓蓓,等. 基于压缩感知的传感器网络中概率负载均衡的数据路由协议[J]. 控制与决策, 2018, 33(06):1041-1047. |
| Ding Xu, Huang Cheng, Wu Xiao-bei, et al. Data routing protocol for probabilistic load balancing in sensor networks based on compressed sensing [J]. Control and Decision, 2018, 33 (06): 1041-1047 | |
| 7 | Tan B, Elnaggar R, Fung J M, et al. Towards hardware-based IP vulnerability detection and post-deployment patching in systems-on-chip[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2020, PP(99):1-1. |
| 8 | 夏之阳, 易平, 杨涛. 基于神经网络与代码相似性的静态漏洞检测[J]. 计算机工程, 2019, 45(12):141-146. |
| Xia Zhi-yang, Yi Ping, Yang Tao. Static vulnerability detection based on neural network and code similarity [J]. Computer Engineering, 2019, 45 (12): 141-146. | |
| 9 | Nancy P, Muthurajkumar S, Ganapathy S, et al. Intrusion detection using dynamic feature selection and fuzzy temporal decision tree classification for wireless sensor networks[J]. IET Communications, 2020, 14(5):888-895. |
| 10 | 苏彬, 马丽梅, 崔宝江. 适用于传感器采集网络的轻量级安全通信协议[J]. 计算机工程与设计, 2018, 39(5): 1262-1268. |
| Su Bin, Ma Li-mei, Cui Bao-jiang. Lightweight secure communication protocol for sensor acquisition networks [J]. Computer engineering and design, 2018, 39 (5): 1262-1268. | |
| 11 | Zhao Z N, Wang J, Guo H W. Analysis of vulnerability propagation for the all-optical network based on Bio-PEPA[J]. Wireless Networks, 2019, 25(6):3513-3529. |
| 12 | Nunes P, Medeiros I, Fonseca J, et al. An empirical study on combining diverse static analysis tools for web security vulnerabilities based on development scenarios[J]. Computing, 2019, 101(2):161-185. |
| 13 | 荆琛, 傅晓彤, 董伟,等. 基于Q-学习算法的有状态网络协议模糊测试方法研究[J]. 电子技术应用, 2020, 46(4):49-52, 56. |
| Jing Chen, Fu Xiao-tong, Dong Wei, et al. Research on fuzzy testing method of stateful network protocol based on Q-learning algorithm[J]. Electronic Technology Application, 2020, 46 (4): 49-52, 56. | |
| 14 | He F, Zhang B. A protocol of potential advantage in the low frequency range to gravitational wave detection with space based optical atomic clocks[J]. The European Physical Journal D, 2020, 74(5):1-6. |
| 15 | 张志华. 基于渗透测试的网络安全漏洞实时侦测技术[J]. 科学技术与工程, 2018, 18(20):297-302. |
| Zhang Zhi-hua, Real time detection technology of network security vulnerability based on penetration test [J]. Science, technology and engineering, 2018, 18(20): 297-302. | |
| 16 | Kim J, Cho K, Kim Y K, et al. Study on peak misdetection recovery of key exchange protocol using heartbeat[J]. Journal of supercomputing, 2019, 75(6):3288-3301. |
| 17 | 王培超, 周鋆, 朱承, 等. 基于贝叶斯网络的XSS攻击检测方法[J]. 中国科学技术大学学报, 2019, 49(2):166-172. |
| Wang Pei-chao, Zhou Yun, Zhu Cheng, et al. XSS attack detection method based on Bayesian networks [J]. Journal of China University of Science and Technology, 2019, 49 (2): 166-172. | |
| 18 | Han Y, Seed D, Wang C, et al. Delay-aware application protocol for internet of things[J]. IEEE Network, 2018 (1):1-8. |
| 19 | 许力, 李光辉. 基于信任机制的无线传感器网络多协议层入侵检测方法[J]. 传感技术学报, 2019, 32(5):101-110. |
| Xu Li, Li Guang-hui. Multi protocol layer intrusion detection method for wireless sensor networks based on trust mechanism [J]. Journal of sensing technology, 2019, 32 (5): 101-110. | |
| 20 | Wei X, Gao S, Huang T, et al. Complex network-based cascading faults graph for the analysis of transmission network vulnerability[J]. IEEE Transactions on Industrial Informatics, 2019, 15(3):1265-1276. |
| [1] | Li-li DONG,Dan YANG,Xiang ZHANG. Large⁃scale semantic text overlapping region retrieval based on deep learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(5): 1817-1822. |
| [2] | Li-sheng JIN,Bai-cang GUO,Fang-rong WANG,Jian SHI. Dynamic multiple object detection algorithm for vehicle forward based on improved YOLOv3 [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1427-1436. |
| [3] | Feng-chong LAN,Ji-wen LI,Ji-qing CHEN. DG-SLAM algorithm for dynamic scene compound deep learning and parallel computing [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1437-1446. |
| [4] | Jin-qing LI,Jian ZHOU,Xiao-qiang DI. Learning optical image encryption scheme based on CycleGAN [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1060-1066. |
| [5] | Zhe-ming YUAN,Hong-jie YUAN,Yu-xuan YAN,Qian LI,Shuang-qing LIU,Si-qiao TAN. Automatic recognition and classification of field insects based on lightweight deep learning model [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1131-1139. |
| [6] | Bo PENG,Yuan-yuan ZHANG,Yu-ting WANG,Ju TANG,Ji-ming XIE. Automatic traffic state recognition from videos based on auto⁃encoder and classifiers [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 886-892. |
| [7] | Zhen SONG,Jun-liang LI,Gui-qiang LIU. Constant flow prediction method of variable speed hydraulic power source based on deep learning and limitation fuzzy [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1106-1110. |
| [8] | Hong-wei ZHAO,Xiao-han LIU,Yuan ZHANG,Li-li FAN,Man-li LONG,Xue-bai ZANG. Clothing classification algorithm based on landmark attention and channel attention [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1765-1770. |
| [9] | Hua CHEN,Wei GUO,Jing-wen YAN,Wen-hao ZHUO,Liang-bin WU. A new deep learning method for roads recognition from SAR images [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1778-1787. |
| [10] | Qian XU,Ying LI,Gang WANG. Pedestrian-vehicle detection based on deep learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(5): 1661-1667. |
| [11] | Li⁃min GUO,Xin CHEN,Tao CHEN. Radar signal modulation type recognition based on AlexNet model [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(3): 1000-1008. |
| [12] | LI Di-fei, TIAN Di, HU Xiong-wei. A method of deep learning based on distributed memory computing [J]. 吉林大学学报(工学版), 2015, 45(3): 921-925. |
|
||