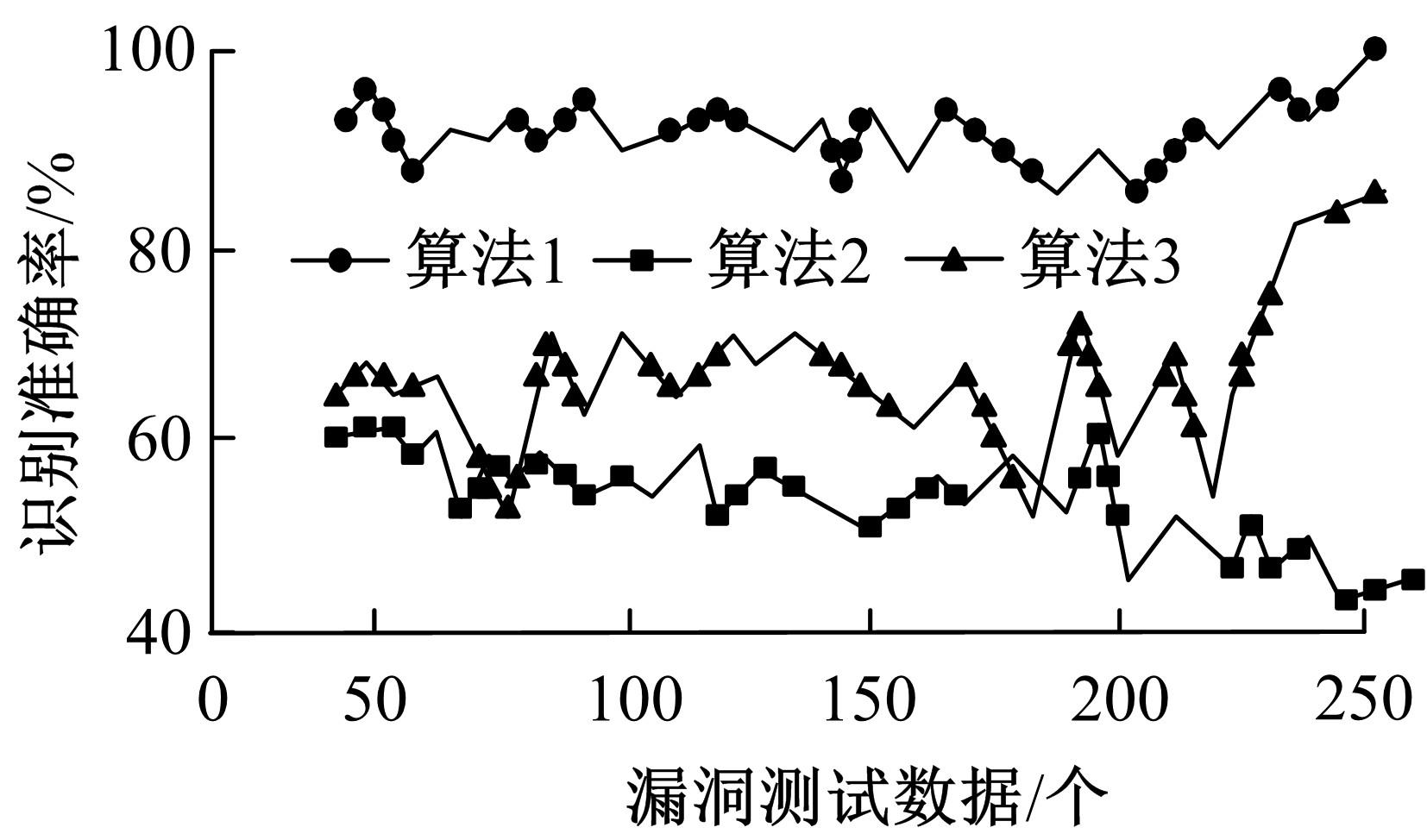
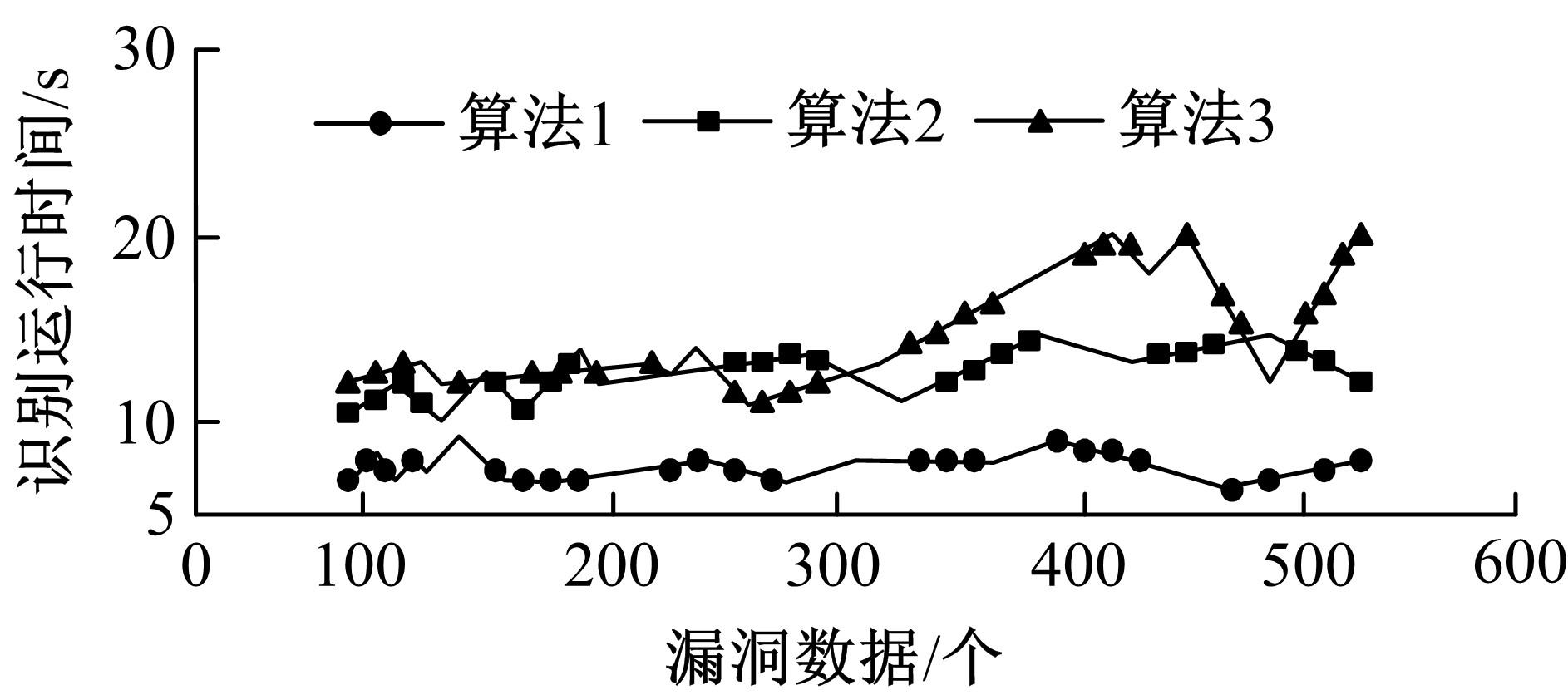
| 1 |
边寒, 陈小红, 金芝, 等. 基于环境建模的物联网系统TAP规则生成方法[J]. 软件学报, 2021, 32(4): 934-952.
|
|
Bian Han, Chen Xiao-hong, Jin Zhi, et al. Approach to generating TAP rules in IoT systems based on environment modeling[J]. Journal of Software, 2021, 32(4): 934-952.
|
| 2 |
杨婷婷, 李志一, 赵冬泉.基于物联网大数据的城市降雨径流控制率分析[J]. 水电能源科学, 2020, 38(5): 15-17, 210.
|
|
Yang Ting-ting, Li Zhi-yi, Zhao Dong-quan. Analysis of urban rainfall and runoff control rate based on IoT big data[J]. Water Resources and Power, 2020, 38(5): 15-17, 210.
|
| 3 |
张帅钦, 张荣杰, 温旭东. 基于一维像选择双谱的神经网络识别算法[J]. 现代雷达, 2020, 42(4): 46-49.
|
|
Zhang Shuai-qin, Zhang Rong-jie, Wen Xu-dong. A neural network recognition algorithm based on one-dimensional image selection bispectrum[J]. Modern Radar, 2020, 42(4): 46-49.
|
| 4 |
唐作栋, 龚晓峰, 雒瑞森.一种小波特征与深度神经网络结合的信号制式识别算法[J]. 计算机工程与科学, 2020, 42(5): 902-909.
|
|
Tang Zuo-dong, Gong Xiao-feng, Luo Rui-sen. A signal system recognition algorithm combining wavelet features and deep neural networks[J]. Computer Engineering and Science, 2020, 42(5): 902-909.
|
| 5 |
苟泽中, 许华, 郑万泽, 等.基于半监督联合神经网络的调制识别算法[J]. 信号处理, 2020, 36(2): 168-176.
|
|
Gou Ze-zhong, Xu Hua, Zheng Wan-ze, et al. Semi-supervised joint neural network based recognition algorithm of modulation signal[J]. Journal of Signal Processing, 2020, 36(2): 168-176.
|
| 6 |
丑义凡, 易波, 王兴伟, 等. IPv6网络中基于MF-DL的DDoS攻击快速防御机制[J]. 计算机学报, 2021, 44(10): 2047-2060.
|
|
Yi-fan Chou, Yi Bo, Wang Xing-wei, et al. A rapid defense mechanism based on MF-DL for DDoS attack in IPv6 networks[J]. Chinese Journal of Computers, 2021, 44(10): 2047-2060.
|
| 7 |
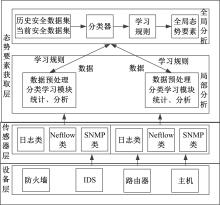
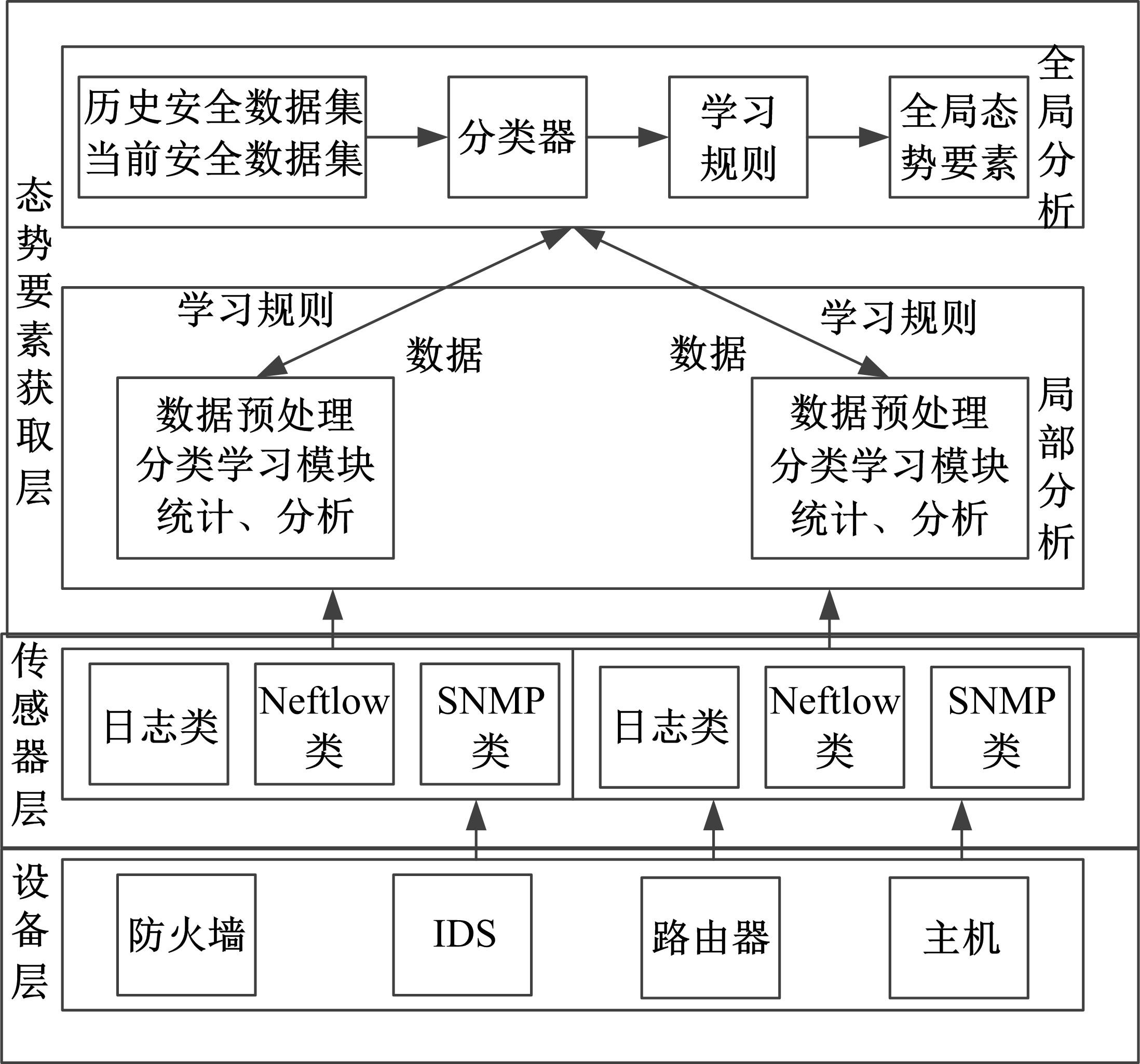
张欣, 朱江.面向样本不平衡的网络安全态势要素获取[J]. 计算机工程与应用, 2022, 58(1): 134-142.
|
|
Zhang Xin, Zhu Jiang. Network security situation element acquisition for sample imbalance[J]. Computer Engineering and Applications, 2022, 58(1): 134-142.
|
| 8 |
牛祥.基于门限联合判别的同质网络入侵检测仿真[J]. 计算机仿真, 2020, 37(3): 309-313.
|
|
Niu Xiang. Simulation of homogeneous network intrusion detection based on threshold joint discrimination[J]. Computer Simulation, 2020, 37(3): 309-313.
|
| 9 |
景惠甜, 韩丽, 高志宇. 基于卷积神经网络特征提取的风电功率爬坡预测[J]. 电力系统自动化, 2021, 45(4): 98-105.
|
|
Jing Hui-tian, Han Li, Gao Zhi-yu. Wind power ramp prediction based on feature extraction of convolutional neural network[J]. Automation of Electric Power Systems, 2021, 45(4): 98-105.
|
| 10 |
曲岳晗, 赵洪山, 马利波, 等. 多深度神经网络综合的电力变压器故障识别方法[J]. 中国电机工程学报, 2021, 41(23): 8223-8231.
|
|
Qu Yue-han, Zhao Hong-shan, Ma Li-bo, et al. Multi-depth neural network synthesis method for power transformer fault identification[J]. Proceedings of the CSEE, 2021, 41(23): 8223-8231.
|