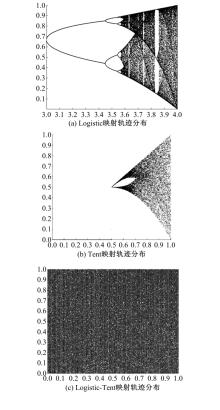
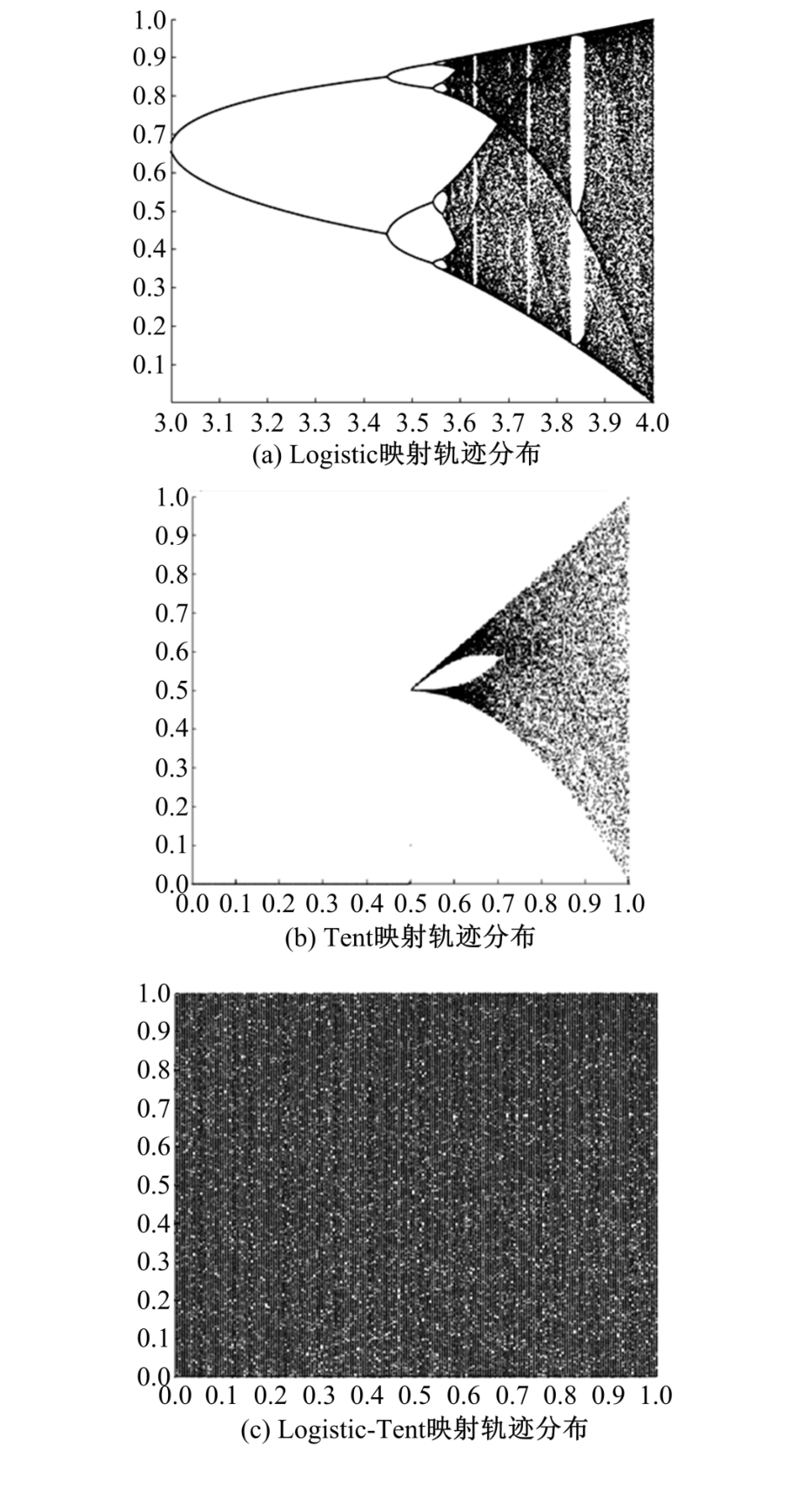
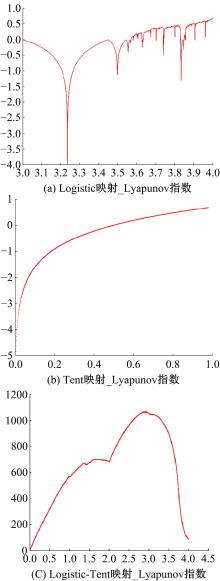
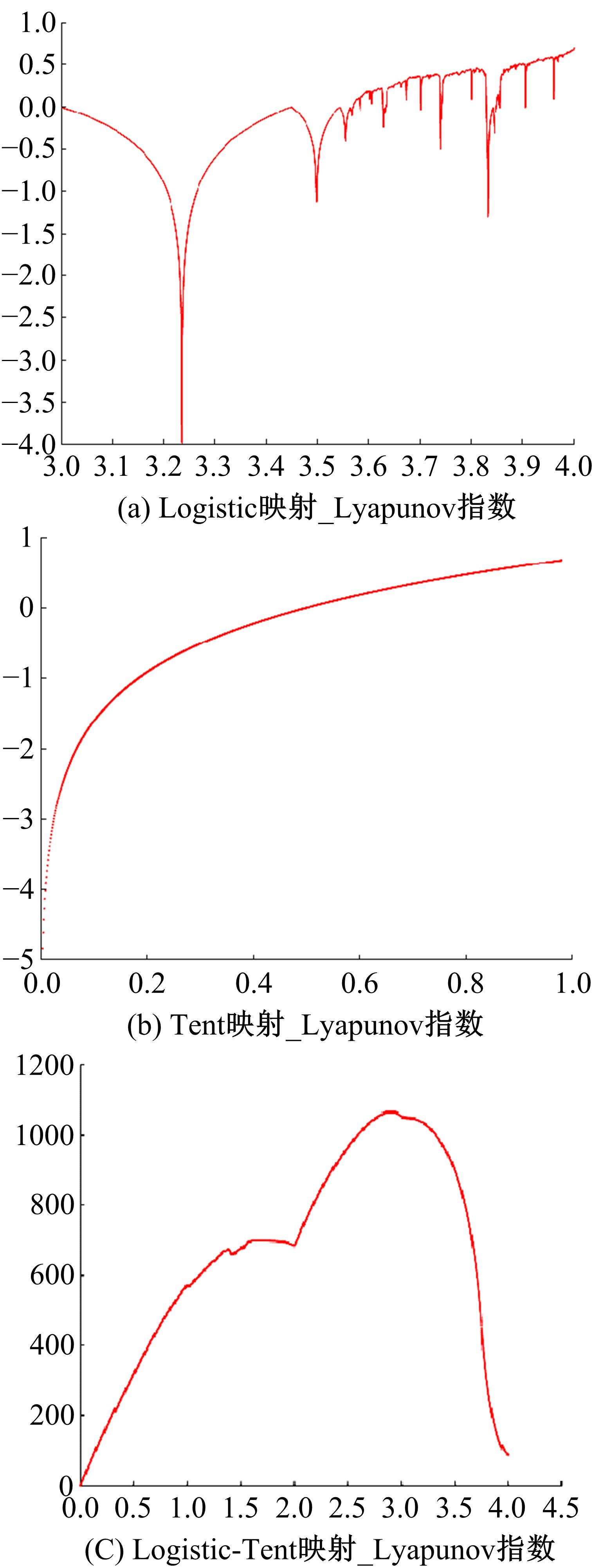
Journal of Jilin University(Engineering and Technology Edition) ›› 2023, Vol. 53 ›› Issue (7): 2115-2120.doi: 10.13229/j.cnki.jdxbgxb.20220799
Image encryption scheme based on Fibonacci transform and improved Logistic-Tent chaotic map
Xian-feng GUO( ),Hao-hua LI,Jin-yu WEI
),Hao-hua LI,Jin-yu WEI
- School of Computer Science and Engineering,Southwest Minzu University,Chengdu 610041,China
CLC Number:
- TP309.7
| 1 | Tong X J. Design of an image encryption scheme based on a multiple chaotic map[J]. Communications in Nonlinear Science & Numerical Simulation, 2013, 18(7): 1725-1733. |
| 2 | Parvin Z, Seyedarabi H, Shamsi M. A new secure and sensitive image encryption scheme based on new substitution with chaotic function[J]. Multimedia Tools & Applications, 2016, 75(17): 10631-10648. |
| 3 | 李春虎,罗光春,李春豹.基于斜帐篷混沌映射和Arnold变换的图像加密方案[J].计算机应用研究, 2018, 35(11): 3424-3427. |
| Li Chun-hu, Luo Guang-chun, Li Chun-bao. Image encryption scheme based on skew tent chaotic map and Arnold transformation[J]. Application Research of Computers, 2018, 35(11): 3424-3427. | |
| 4 | Pak C, Huang L. A new color image encryption using combination of the 1D chaotic map[J]. Signal Processing, 2017, 138: 129-137. |
| 5 | Arroyo D, Rhouma R, Alvarez G, et al. On the security of a new image encryption scheme based on chaotic map lattices[J]. Chaos: An Interdisciplinary Journal of Nonlinear Science, 2008, 18(3): No.033118. |
| 6 | Skrobek A. Cryptanalysis of chaotic stream cipher[J]. Physics Letters A, 2007, 363(12): 84-90. |
| 7 | Hua Z, Zhou Y, Pun C M, et al. 2D Sine logistic modulation map for image encryption[J]. Information Sciences: An International Journal, 2015, 297: 80-94. |
| 8 | Stefanski A, Dabrowski A, Kapitaniak T. Evaluation of the largest Lyapunov exponent in dynamical systems with time delay[J]. Chaos Solitons & Fractals, 2005, 23(5): 1651-1659. |
| 9 | Eckmann J, Ruelle D. Ergodic theory of chaos and strange attractors[J]. Review of Modern Physics, 2008, 57(3): 1115-1125. |
| 10 | 王海珍, 廉佐政, 谷文成. 基于L-P混沌映射和AES的图像加密算法[J]. 计算机仿真, 2021, 38(10): 217-221. |
| Wang Hai-zhen, Lian Zuo-zheng, Gu Wen-cheng. Image encryption algorithm based on L-P chaotic map and AES[J]. Computer Simulation, 2021, 38(10): 217-221. | |
| 11 | 芮杰, 杭后俊. 基于超混沌系统的明文关联图像加密算法[J]. 图学学报, 2020, 41(6): 917-921. |
| Rui jie, Hang hou-jun. Plaintext correlation image encryption algorithm based on hyper-chaotic system[J]. Journal of Graphics, 2020, 41(6): 917-921. | |
| 12 | 班多晗, 吕鑫, 王鑫元. 基于一维混沌映射的高效图像加密算法[J].计算机科学, 2020, 47(4): 278-284. |
| Ban Duo-han, Lv Xin, Wang Xin-yuan. Efficient image encryption algorithm based on 1D chaotic map[J]. Computer Science, 2020, 47(4): 278-284. | |
| 13 | 朱凯歌, 武相军, 任广龙. 基于DNA动态编码和混沌系统的彩色图像无损加密算法[J].计算机应用研究, 2020, 37(): 230-233. |
| Zhu Kai-ge, Wu Xiang-jun, Ren Guang-long. Color image lossless encryption algorithm based on DNA dynamic coding and chaotic system[J]. Application Research of Computers, 2020, 37(Sup.2): 230-233. | |
| 14 | Liu H, Kadir A. Asymmetric color image encryption scheme using 2D discrete-time map[J]. Signal Processing, 2015, 113: 104-112. |
| [1] | Zhen-hai ZHANG,Kun JI,Jian-wu DANG. Crack identification method for bridge based on BCEM model [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(5): 1418-1426. |
| [2] | Chao-jian FANG,Xin-rong HU. Privacy-sensitive data filtering algorithm based on fuzzy approximation [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(4): 1174-1180. |
| [3] | Yu JIANG,Jia-zheng PAN,He-huai CHEN,Ling-zhi FU,Hong QI. Segmentation-based detector for traditional Chinese newspaper [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(4): 1146-1154. |
| [4] | Lin BAI,Lin-jun LIU,Xuan-ang LI,Sha WU,Ru-qing LIU. Depth estimation algorithm of monocular image based on self-supervised learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(4): 1139-1145. |
| [5] | Hong-wei ZHAO,Jian-rong ZHANG,Jun-ping ZHU,Hai LI. Image classification framework based on contrastive self⁃supervised learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(8): 1850-1856. |
| [6] | Xuan-jing SHEN,Xue-feng ZHANG,Yu WANG,Yu-bo JIN. Multi⁃focus image fusion algorithm based on pixel⁃level convolutional neural network [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(8): 1857-1864. |
| [7] | Fu-heng QU,Tian-yu DING,Yang LU,Yong YANG,Ya-ting HU. Fast image codeword search algorithm based on neighborhood similarity [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(8): 1865-1871. |
| [8] | Na LI,Shao-sheng TAN. Image segmentation of fencing continuous action based on spatial neighborhood information [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(7): 1639-1644. |
| [9] | Zhen WANG,Meng GAI,Heng-shuo XU. Surface reconstruction algorithm of 3D scene image based on virtual reality technology [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(7): 1620-1625. |
| [10] | Sheng-sheng WANG,Lin-yan JIANG,Yong-bo YANG. Transfer learning of medical image segmentation based on optimal transport feature selection [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(7): 1626-1638. |
| [11] | Huai-jiang YANG,Er-shuai WANG,Yong-xin SUI,Feng YAN,Yue ZHOU. Simplified residual structure and fast deep residual networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(6): 1413-1421. |
| [12] | Ming LIU,Yu-hang YANG,Song-lin ZOU,Zhi-cheng XIAO,Yong-gang ZHANG. Application of enhanced edge detection image algorithm in multi-book recognition [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 891-896. |
| [13] | Hai-yang JIA,Rui XIA,An-qi LYU,Ceng-xuan GUAN,Juan CHEN,Lei WANG. Panoramic mosaic approach of ultrasound medical images based on template fusion [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 916-924. |
| [14] | Xue WANG,Zhan-shan LI,Ying-da LYU. Medical image segmentation based on multi⁃scale context⁃aware and semantic adaptor [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 640-647. |
| [15] | Xiang-jun LI,Jie-ying TU,Zhi-bin ZHAO. Validity classification of melting curve based on multi⁃scale fusion convolutional neural network [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 633-639. |
|
||