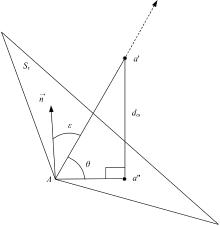
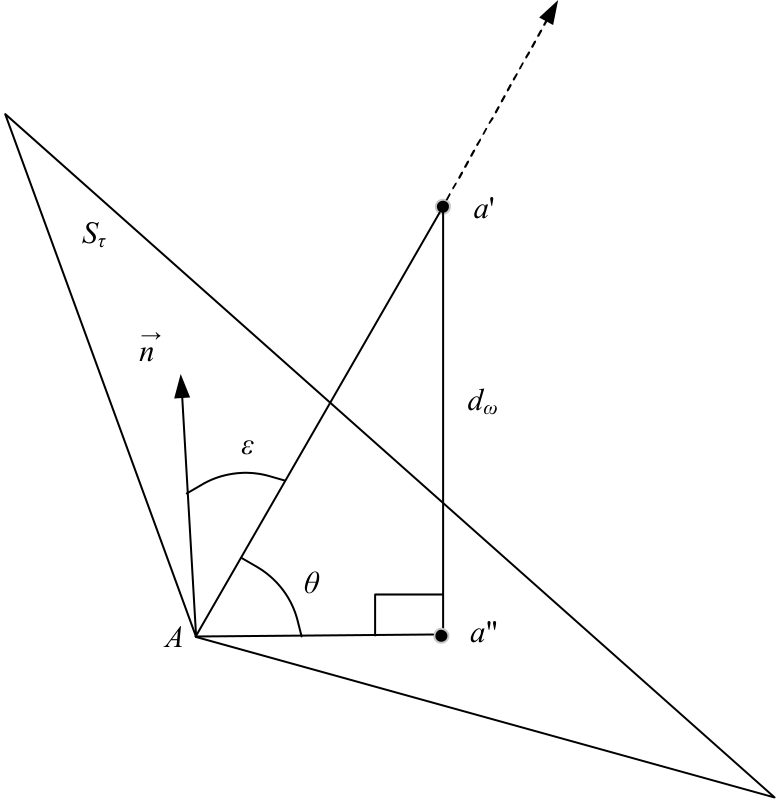
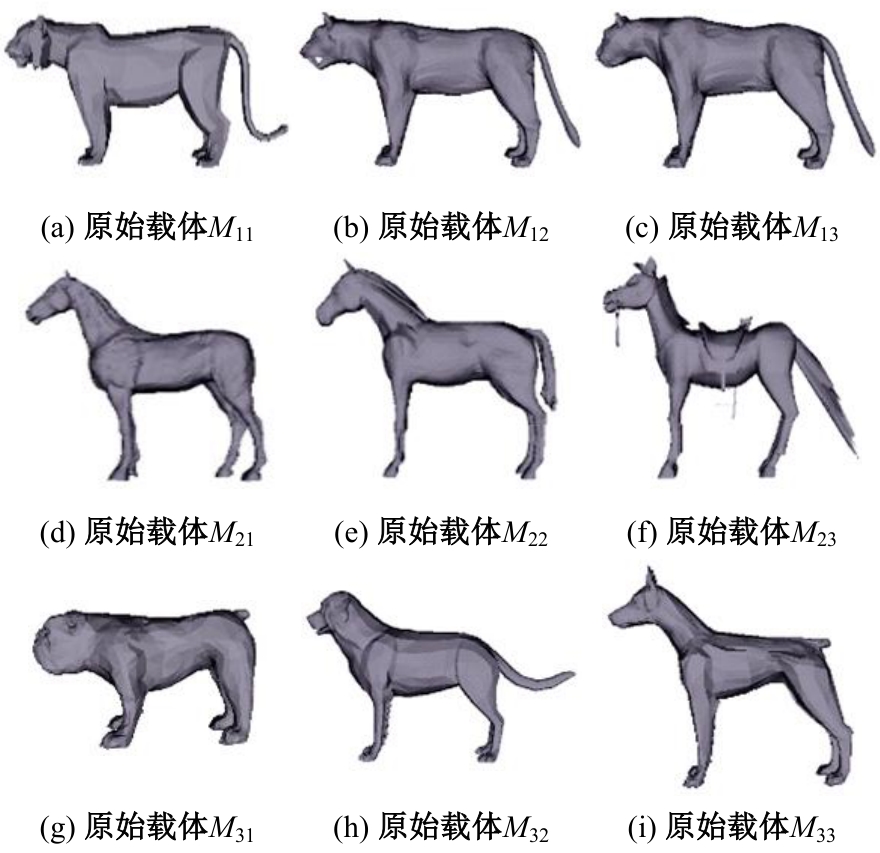
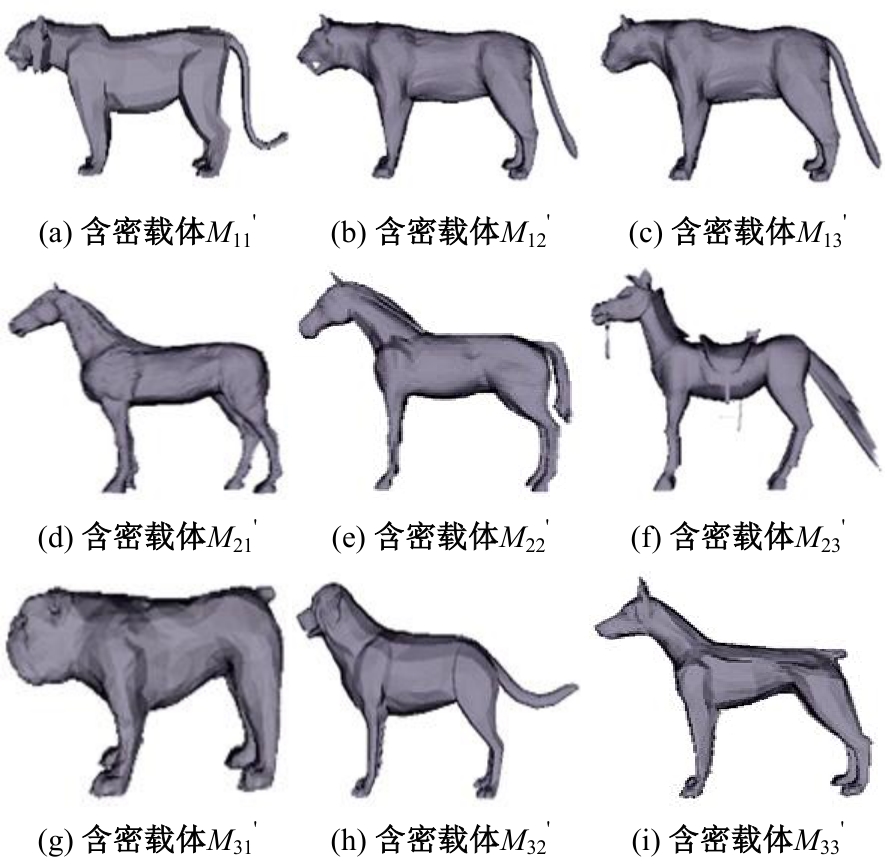
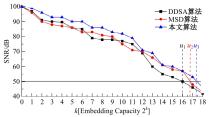
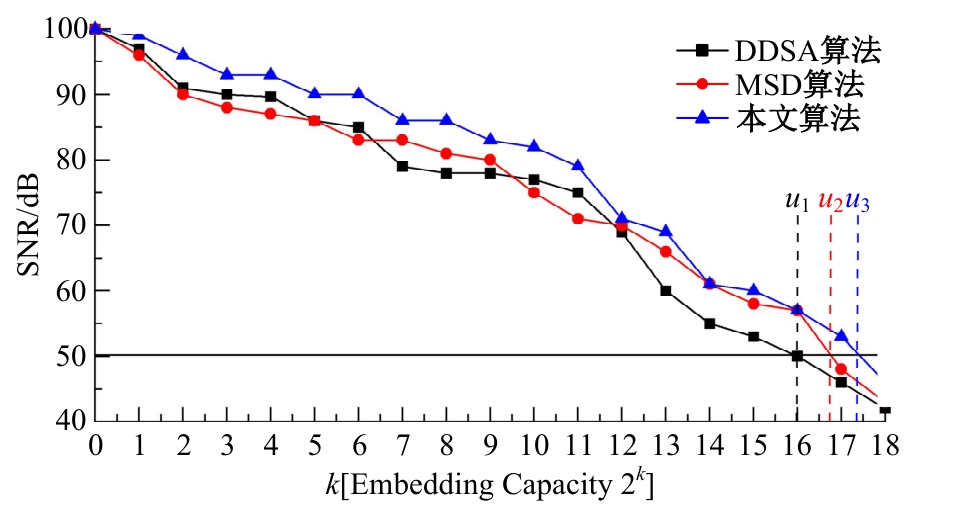
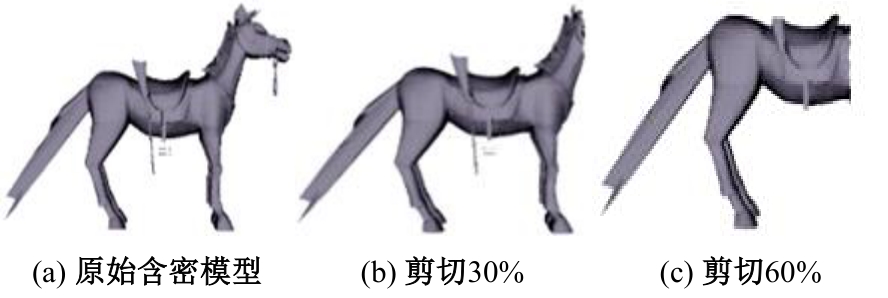
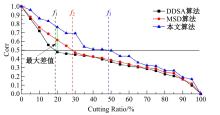
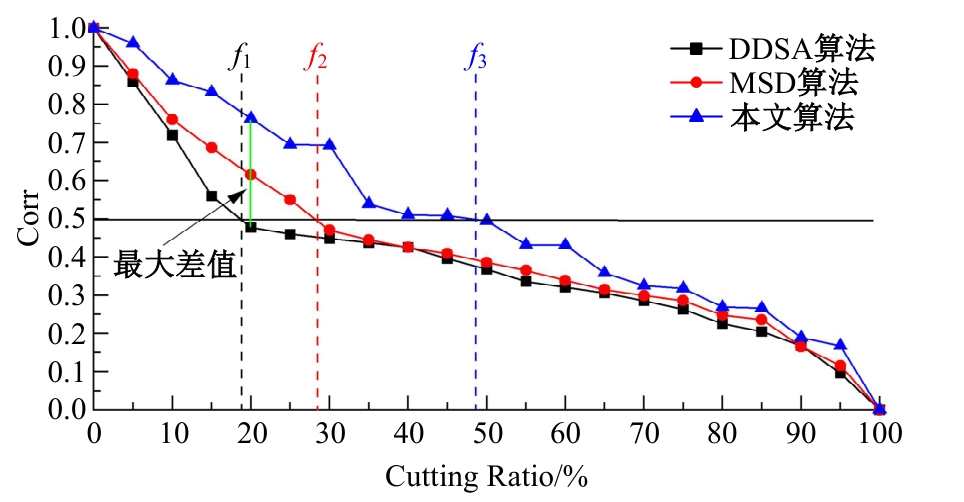
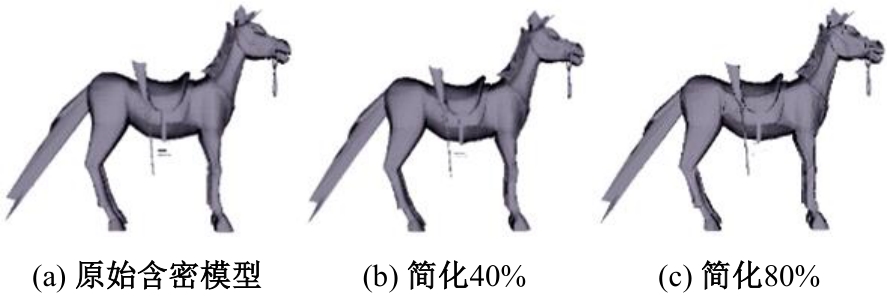
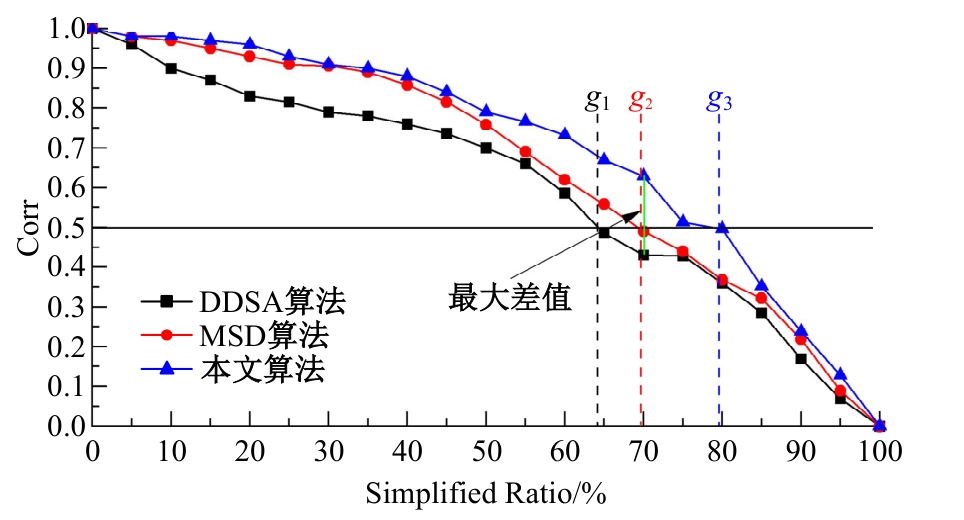
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (8): 2711-2721.doi: 10.13229/j.cnki.jdxbgxb.20240018
An information hiding algorithm based on the normal vector of multiple surface images in 3D models
Yue-fa OU1( ),Wei DENG2(
),Wei DENG2( ),Shuai REN3,Sheng-xia LIU3
),Shuai REN3,Sheng-xia LIU3
- 1.School of Mechanical and Marine Engineering,Beibu Gulf University,Qinzhou 535011,China
2.School of Computer Science & Engineering,Guilin University of Aerospace Technology,Guilin 541004,China
3.School of Information Engineering,Chang'an University,Xi'an 710064,China
CLC Number:
- TP309.2
| [1] | 张小梅. 三维网格模型数字水印的相关理论及关键技术研究[D]. 武汉: 武汉理工大学信息工程学院, 2007. |
| Zhang Xiao-mei. Research on relevant theories and key technologies of digital watermarking for 3d mesh models[D]. Wuhan: School of Information Engineering, Wuhan University of Technology, 2007. | |
| [2] | Zein O M E, Bakrawy L M E, Ghali N I. A non-blind robust watermarking approach for 3D mesh models[J]. Journal of Theoretical & Applied Information Technology, 2016, 83(3): 353-359. |
| [3] | Lyu W L, Cheng L, Yin Z. High-capacity reversible data hiding in encrypted 3D mesh models based on multi-MSB prediction[J]. Signal Processing, 2022, 201: 108686. |
| [4] | Wang X, Zhan Y. A zero-watermarking scheme for three-dimensional mesh models based on multi-features[J]. Multimedia Tools and Applications, 2019, 78(19): 27001-27028. |
| [5] | Farrag S, Alexan W. Secure 3D data hiding technique based on a mesh traversal algorithm[J]. Multimedia Tools and Applications, 2020, 79(39): 29289-29303. |
| [6] | Zhang Q, Song X, Wen T, et al. Reversible data hiding for 3D mesh models with hybrid prediction and multilayer strategy[J]. Multimedia Tools and Applications, 2019, 78(21): 29713-29729. |
| [7] | Zaid A O, Hachani M, Puech W, et al. Wavelet-based high-capacity watermarking of 3-D irregular meshes[J]. Multimedia Tools and Applications, 2015, 74(15): 5897-5915. |
| [8] | Li Z, Bors A G. Steganalysis of meshes based on 3D wavelet multiresolution analysis[J]. Information Sciences, 2020, 522: 164-179. |
| [9] | Tsai Y Y. Separable reversible data hiding for encrypted three-dimensional models based on spatial subdivision and space encoding[J]. IEEE Transactions on Multimedia, Piscataway, 2021, 23: 2286-2296. |
| [10] | Jiang R, Zhou H, Zhang W, et al. Reversible data hiding in encrypted three-dimensional mesh models[J]. IEEE Transactions on Multimedia, 2018, 20(1): 55-67. |
| [11] | 任帅, 雷雪梅, 淡卓异, 等. 一种基于三维模型顶点分区的多载体信息隐藏算法[J]. 北京邮电大学学报, 2023, 46(1): 109-114. |
| Ren Shuai, Lei Xue-mei, Dan Zhuo-yi, et al. A multi-carrier information hiding algorithm based on vertex partitioning of 3d models[J]. Journal of Beijing University of Posts and Telecommunications, 2023, 46(1): 109-114. | |
| [12] | Liu G, Wang Q, Wu L, et al. Zero-watermarking method for resisting rotation attacks in 3D models[J]. Neurocomputing, 2021, 421: 39-50. |
| [13] | Yan T, Xin F, Qiang C. 3D model simplification algorithm based on degree centrality[C]∥2nd IEEE International Conference on Broadband Network & Multimedia Technology, Beijing, China, 2009: 179-182. |
| [14] | 陶海跻, 达飞鹏. 一种基于法向量的点云自动配准方法[J]. 中国激光, 2013, 40(8): 184-189. |
| Tao Hai-ji, Fei-peng Da. An automatic point cloud registration method based on normal vectors[J]. Chinese Lasers, 2013, 40(8): 184-189. | |
| [15] | Zhou H, Chen K, Zhang W, et al. Distortion design for secure adaptive 3-d mesh steganography[J]. IEEE Transactions on Multimedia, 2019, 21(6): 1384-1398. |
| [16] | 任帅, 王震, 苏东旭, 等. 基于三维模型贴图与结构数据的信息隐藏算法[J]. 通信学报, 2019, 40(5): 211-222. |
| Ren Shuai, Wang Zhen, Su Dong-xu, et al. Information hiding algorithm based on texture mapping and structural data of 3d models[J]. Journal of Communications, 2019, 40(5): 211-222. |
| [1] | Ru-bo ZHANG,Shi-qi CHANG,Tian-yi ZHANG. Review on image information hiding methods based on deep learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1497-1515. |
|
||