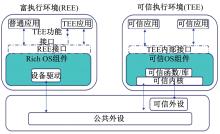
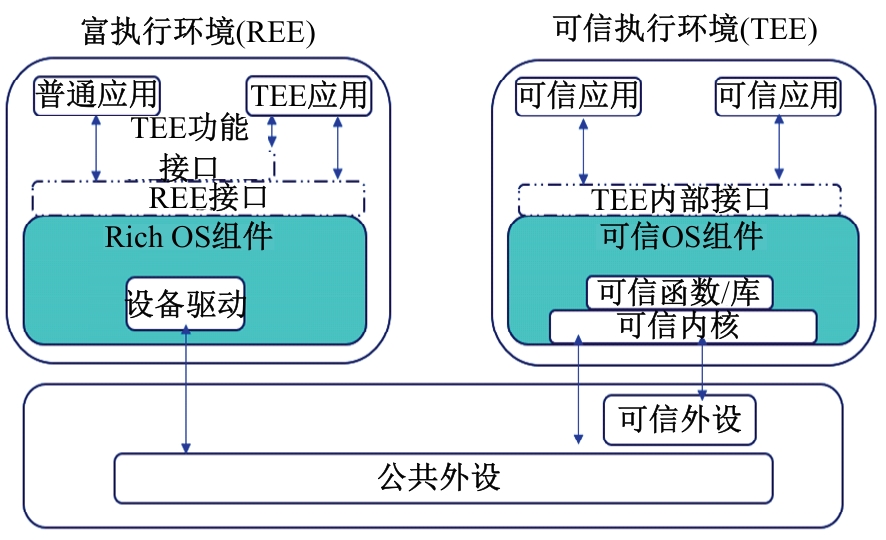
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (3): 755-770.doi: 10.13229/j.cnki.jdxbgxb.20231163
Overview of heterogeneous confidential computing
Tao XU1,2( ),Shuai-di KONG3,Cai-hua LIU2,3(
),Shuai-di KONG3,Cai-hua LIU2,3( ),Shi LI4
),Shi LI4
- 1.Institute of Scientific and Technological Innovation,Civil Aviation University of China,Tianjin 300300,China
2.Key Laboratory of Civil Aviation Smart Airport Theory and System,Civil Aviation University of China,Tianjin 300300,China
3.School of Computer Science and Technology,Civil Aviation University of China,Tianjin 300300,China
4.School of Cyberspace Security,Nankai University,Tianjin 300300,China
CLC Number:
- TP391
| 1 | 刘衍珩, 韩家伟, 孙鑫, 等. 基于量子密钥和云服务的身份加密方案[J]. 吉林大学学报:工学版, 2018,48(2): 551-557. |
| Liu Yan-heng, Han Jia-wei, Sun Xin, et al. Identity-based encryption scheme based on cloud and quantum keys[J].Journal of Jilin University(Engineering and Technology Edition), 2018,48(2): 551-557. | |
| 2 | Davis T A, Wong M L M, Paterson N M. The data security governance conundrum: practical solutions and best practices for the boardroom and the C-suite[J]. Columbia Business Law Review, 2015,25(6): 613. |
| 3 | Liu V, Musen M A, Chou T. Data breaches of protected health information in the United States[J]. Jama, 2015, 313(14): 1471-1473. |
| 4 | 方朝剑, 胡新荣. 基于模糊近似度的隐私敏感数据过滤算法[J]. 吉林大学学报: 工学版, 2023, 53(4): 1174-1180. |
| Fang Chao-jian, Hu Xin-rong.Privacy-sensitive data filtering algorithm based on fuzzy approximation[J].Journal of Jilin University(Engineering and Technology Edition),2023,53(4):1174-1180. | |
| 5 | Cachin C, Keidar I, Shraer A. Trusting the cloud[J]. Acm Sigact News, 2009, 40(2): 81-86. |
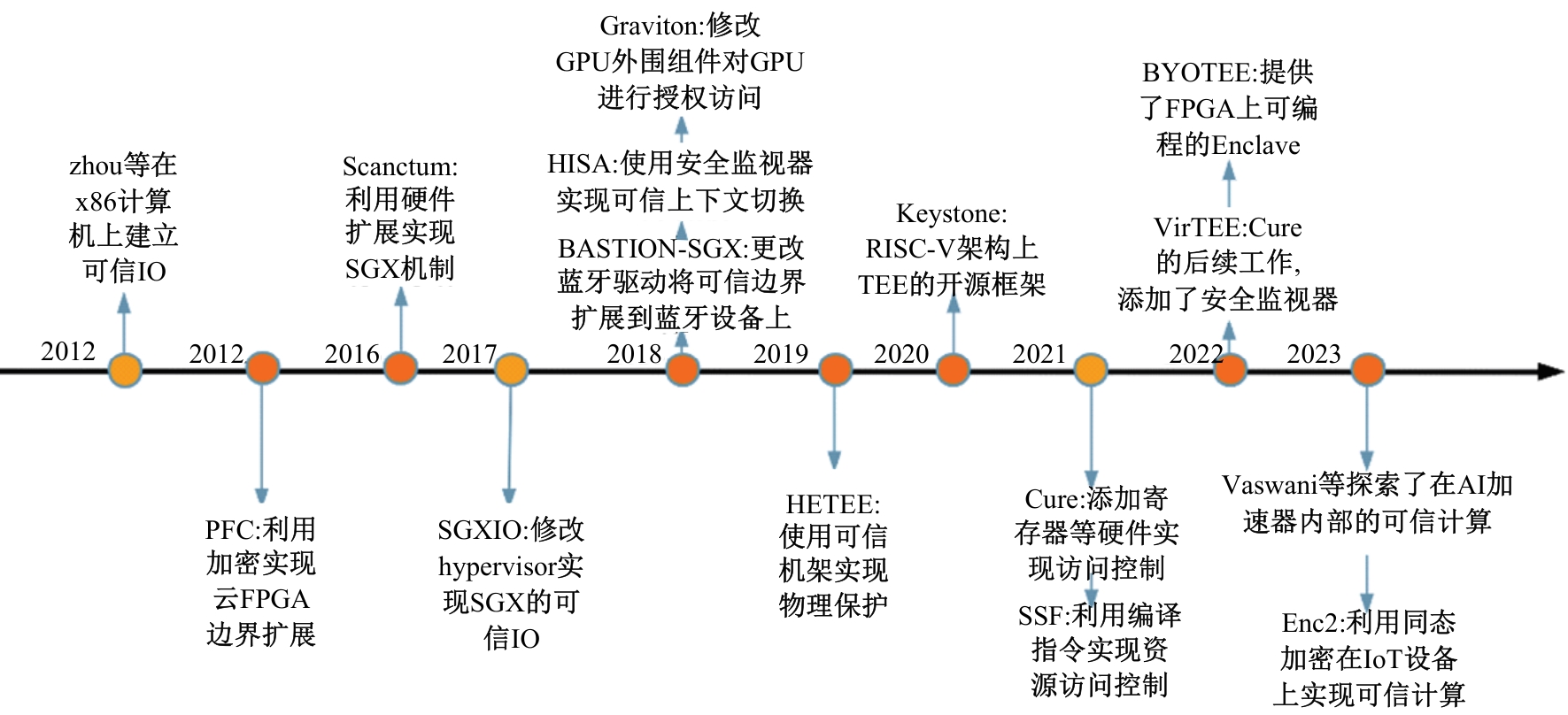
| 6 | Mofrad S, Zhang F, Lu S, et al. A comparison study of intel SGX and AMD memory encryption technology[C]∥Proceedings of the 7th International Workshop on Hardware and Architectural Support for Security and Privacy, Los Angeles California, 2018: 1-8. |
| 7 | Li Z, Yu H, Zhou T, et al. Byzantine resistant secure blockchained federated learning at the edge[J]. IEEE Network, 2021, 35(4): 295-301. |
| 8 | Choquette J, Gandhi W. Nvidia A100 GPU: performance & innovation for gpu computing[C]∥2020 IEEE Hot Chips 32 Symposium, Palo Alto,CA, USA, 2020: 1-43. |
| 9 | Ganusov I K, Iyer M A, Cheng N, et al. Agilex™ generation of Intel ® FPGAs[C]∥2020 IEEE Hot Chips 32 Symposium (HCS), Palo Alto, CA, USA, 2020: 1-26. |
| 10 | Jouppi N P, Young C, Patil N, et al. In-datacenter performance analysis of a tensor processing unit[C]∥Proceedings of the 44th Annual International Symposium on Computer Architecture, Toronto, ON, Canada, 2017: 1-12. |
| 11 | Horowitz M.1.1 Computing's energy problem (and what we can do about it)[C]∥2014 IEEE International Solid-State Circuits Conference, San Francisco, CA, USA, 2014: 10-14. |
| 12 | Choquette J. NVIDIA Hopper H100 GPU: scaling performance[J]. IEEE Micro, 2023, 43(3): 9-17. |
| 13 | NVIDIA H 100 tensor core GPU[EB/OL]. [2023-09-25]. |
| 14 | Chen Y T, Cong J, Fang Z,et al.When spark meets FPGAs: a case study for next-generation DNA sequencing acceleration[C]∥Usenix Conference on Hot Topics in Cloud Computing, Washington, DC, USA, 2016: 64-70. |
| 15 | Choi Y K, Cong J, Fang Z,et al.A quantitative analysis on microarchitectures of modern CPU-FPGA platforms[C]∥Design Automation Conference, Austin, USA,2016:1-6. |
| 16 | El-Ghazawi T, El-Araby E, Huang M, et al. The promise of high-performance reconfigurable computing[J]. Computer, 2008, 41(2): 69-76. |
| 17 | Huang M, Wu D, Yu C H, et al. Programming and runtime support to blaze FPGA accelerator deployment at datacenter scale[C]∥Proceedings of the Sev⁃ enth ACM Symposium on Cloud Computing, Haikou, China,2016: 456-469. |
| 18 | Lee D, Kohlbrenner D, Shinde S, et al. Keystone: An open framework for architecting trusted execution environments[C]∥Proceedings of the 5th European Conference on Computer Systems, Heraklion,Greece, 2020: 1-16. |
| 19 | Feng E H, Lu X, Du D, et al. Scalable memory protection in the PENGLAI enclave[J/OL].[2023-09-25]. |
| 20 | Costan V, Lebedev I, Devadas S. Sanctum: minimal hardware extensions for strong software isolation[C]∥25th USENIX Security Symposium, Vancouver, BC, Canada,2016: 857-874. |
| 21 | Bahmani R, Brasser F, Dessouky G, et al.CURE: a security architecture with CUstomizable and resilient Enclaves[C]∥30th USENIX Security Symposium, Vancouver, Canada 2021: 1073-1090. |
| 22 | Ferraiuolo A, Baumann A, Hawblitzel C, et al. Komodo: using verification to disentangle secure-Enclave hardware from software[C]∥Proceedings of the 26th Symposium on Operating Systems Principles, Shanghai, China, 2017: 287-305. |
| 23 | Costan V, Devadas S. Intel SGX explained[J]. Cryptology ePrint Archive, 2016(86): 1-118. |
| 24 | Thapa C, Camtepe S. Precision health data: requirements, challenges and existing techniques for data security and privacy[J]. Computers in Biology and Medicine, 2021, 129: No.104130. |
| 25 | Chakrabarti S, Knauth T, Kuvaiskii D, et al. Trusted Execution Environment with Intel SGX[M].New York: Academic Press, 2020: 161-190. |
| 26 | Li M, Zhang Y, Wang H, et al. TLB poisoning attacks on AMD secure encrypted virtualization[C]∥Annual Computer Security Applications Conference, New York, NY, USA, 2021: 609-619. |
| 27 | 王文宇. 现代密码技术发展及在数据安全中的应用[J].计算机安全, 2012(2): 36-39. |
| Wang Wen-yu. The development of contemporary cryptography technology and application in data security[J]. Computer Security, 2012(2): 36-39. | |
| 28 | Shi S, He D, Li L, et al. Applications of blockchain in ensuring the security and privacy of electronic health record systems: a survey[J]. Computers & Security, 2020, 97: No.101966. |
| 29 | Sartakov V A, O'Keeffe D, Eyers D, et al. Spons & Shields: practical isolation for trusted execution[C]∥Proceedings of the 17th ACM SIGPLAN/SIGOPS International Conference on Virtual Execution Environments, New York, NY,USA, 2021: 186-200. |
| 30 | Wahbe R, Lucco S, Anderson T E, et al. Efficient software-based fault isolation[C]∥Proceedings of the fourteenth ACM Symposium on Operating Systems Principles, Asheville, North Carolina, USA, 1993: 203-216. |
| 31 | Abadi M, Budiu M, Erlingsson U, et al. Control-flow integrity principles, implementations, and applications[J]. ACM Transactions on Information and System Security, 2009, 13(1): 1-40. |
| 32 | Oleksenko O, Kuvaiskii D, Bhatotia P, et al. Intel mpx explained: A cross-layer analysis of the intel mpx system stack[J]. Proceedings of the ACM on Measurement and Analysis of Computing Systems, 2018, 2(2): 1-30. |
| 33 | Armanuzzaman M, Sadeghi A R, Zhao Z. Building your own trusted execution environments using fpga[C]∥Proceedings of the 19th ACM Asia Conference on Computer and Communications Security,Singapore, 2024: 1584-1599. |
| 34 | Cerdeira D, Martins J, Santos N, et al. ReZone: Disarming TrustZone with TEE privilege reduction[C]∥31st USENIX Security Symposium (USENIX Security 22), Bostion, MA, USA, 2022: 2261-2279. |
| 35 | Cerdeira D, Martins J, Santos N, et al. ReZone: Disarming TrustZone with TEE Privilege Reduction[C]∥31st USENIX Security Symposium, Boston, MA, USA, 2022: 2261-2279. |
| 36 | Nasahl P, Schilling R, Werner M, et al. Hector-V: a heterogeneous CPU architecture for a secure RISC-V execution environment[C]∥Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security, Hong Kong, China, 2021: 187-199. |
| 37 | Deng Y, Wang C, Yu S, et al. Strongbox: a GPU TEE on arm endpoints[C]∥Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 2022: 769-783. |
| 38 | Xia K, Luo Y, Xu X, et al. SGX-FPGA: trusted execution environment for CPU-FPGA heterogeneous architecture[C]∥2021 58th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 2021: 301-306. |
| 39 | Kang L, Xue Y, Jia W, et al. IceClave: a trusted execution environment for in-storage computing[C]∥MICRO-54: 54th Annual IEEE/ACM International Symposium on Microarchitecture, Greece, 2021: 199-211. |
| 40 | Zhao M, Gao M, Kozyrakis C. ShEF: shielded enclaves for cloud FPGAS[C]∥Proceedings of the 27th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Lausanne, Switzerland, 2022: 1070-1085. |
| 41 | Xu L, Shi W, Suh T. PFC: Privacy preserving FPGA cloud—a case study of MapReduce[C]∥2014 IEEE 7th International Conference on Cloud Computing, Anchorage, AK, USA, 2014: 280-287. |
| 42 | Chien H J, Khalili H, Hass A, et al. Enc2: privacy-preserving inference for tiny IoTs via encoding and encryption[C]∥Proceedings of the 29th Annual International Conference on Mobile Computing and Networking, Madrid, Spain, 2023: 1-16. |
| 43 | Oh H, Nam K, Jeon S, et al. MeetGo: a trusted execution environment for remote applications on FPGA[J]. IEEE Access, 2021, 9: 51313-51324. |
| 44 | Ren W, Kozlowski W, Koteshwara S, et al. AccShield: a new trusted execution environment with machine-learning accelerators[C]∥2023 60th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 2023: 1-6. |
| 45 | Jang I, Tang A, Kim T, et al. Heterogeneous isolated execution for commodity gpus[C]∥Proceedings of the 24th International Conference on Architectural Support for Programming Languages and Operating Systems, Providence, RI, USA, 2019: 455-468. |
| 46 | Kadav A, Swift M M. Understanding modern device drivers[J/OL].[2023-09-25]. |
| 47 | Boyd-Wickizer S, Zeldovich N. Tolerating malicious device drivers in Linux[C]∥2010 USENIX Annual Technical Conference, Boston, MA, USA, 2010: 117-130. |
| 48 | Peters T, Lal R, Varadarajan S, et al. BASTION-SGX: bluetooth and architectural support for trusted I/O on SGX[C]∥Proceedings of the 7th International Workshop on Hardware and Architectural Support for Security and Privacy, Los Angeles, California, USA, 2018: 1-9. |
| 49 | Weiser S, Werner M. SGXIO: generic trusted I/O path for intel SGX[C]∥Proceedings of the 7th ACM on Conference on Data and Application Security and Privacy, Scottsdale, Arizona, USA, 2017: 261-268. |
| 50 | Suzuki Y, Kato S, Yamada H, et al. GPUvm: why not virtualizing GPUs at the hypervisor?[C]∥2014 USENIX Annual Technical Conference, Philadelphia, PA, USA, 2014: 109-120. |
| 51 | Yu H, Rossbach C J. Full virtualization for GPUs reconsidered[J/OL]. [2023-09-27]. |
| 52 | Zhou Z, Gligor V D, Newsome J, et al. Building verifiable trusted path on commodity x86 computers[C]∥2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 2012: 616-630. |
| 53 | Ye M, Feng X, Wei S. HISA: Hardware isolation-based secure architecture for CPU-FPGA embedded systems[C]∥2018 IEEE/ACM International Conference on Computer-Aided Design, San Diego, CA, USA, 2018: 1-8. |
| 54 | Dessouky G, Isakov M, Kinsy M A, et al. Distributed memory guard: enabling secure enclave computing in NoC-based architectures[C]∥2021 58th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 2021: 985-990. |
| 55 | Jiang J, Qi J, Shen T, et al. CRONUS: fault-isolated, secure and high-performance heterogeneous computing for trusted execution environment[C]∥2022 55th IEEE/ACM International Symposium on Microarchitecture, Chicago, IL, USA, 2022: 124-143. |
| 56 | Oliveira D, Gomes T, Pinto S. uTango: an open-source TEE for IoT devices[J]. IEEE Access, 2022, 10: 23913-23930. |
| 57 | Brasser F, Gens D, Jauernig P, et al. SANCTUARY: ARMing TrustZone with user-space enclaves[C]∥NDSS, San Diego, California, 2019: 1-15. |
| 58 | Gong R, Wang L, Shi W, et al. A hardware security isolation architecture for intelligent accelerator[C]∥2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Wuhan, China, 2022: 984-991. |
| 59 | Wang J, Mahmoody P, Brasser F, et al. VirTEE: a full backward-compatible TEE with native live migration and secure I/O[C]∥Proceedings of the 59th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 2022: 241-246. |
| 60 | Gu J Y, Li H, Xia Y B, et al. Unified enclave abstraction and secure enclave migration on heterogeneous security architectures[J]. Journal of Computer Science and Technology, 2022, 37(2): 468-486. |
| 61 | Zhu J, Hou R, Wang X F, et al. Enabling rack-scale confidential computing using heterogeneous trusted execution environment[C]∥2020 IEEE Symposium on Security and Privacy, San Francisco, CA, USA,2020: 1450-1465. |
| 62 | Volos S, Vaswani K, Bruno R. Graviton: trusted execution environments on GPUs[C]∥13th USENIX Symposium on Operating Systems Design and Implementation, Carlsbad, CA, USA, 2018: 681-696. |
| 63 | Korona M, Zabołotny B, Kozioł F, et al. IoTrust—a HW/SW framework supporting security core baseline features for IoT[C]∥2023 18th Conference on Computer Science and Intelligence Systems, Warsaw, Poland, 2023: 1029-1034. |
| 64 | Vaswani K, Volos S, Fournet C, et al. Confidential computing within an AI accelerator[C]∥2023 USENIX Annual Technical Conference, Boston, Ma, USA, 2023: 501-518. |
| 65 | Banerjee S, Wei S, Ramrakhyani P, et al. Triton: software-defined threat model for secure multi-tenant ML inference accelerators[C]∥Proceedings of the 12th International Workshop on Hardware and Architectural Support for Security and Privacy, Toronto Canada, 2023: 19-28. |
| 66 | Lee S, Shih M W, Gera P, et al. Inferring fine-grained control flow inside SGX Enclaves with branch shadowing[C]∥26th USENIX Security Symposium, Vancouver, Canada, 2017: 557-574. |
| 67 | Van Bulck J, Piessens F, Strackx R. Nemesis: Studying microarchitectural timing leaks in rudimentary CPU interrupt logic[C]∥Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 178-195. |
| 68 | Van Bulck J, Weichbrodt N, Kapitza R, et al. Telling your secrets without page faults: stealthy page table-based attacks on enclaved execution[C]∥26th USENIX Security Symposium, Vancouver, Canada, 2017: 1041-1056. |
| 69 | Xu Y, Cui W, Peinado M. Controlled-channel attacks: deterministic side channels for untrusted operating systems[C]∥2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 2015: 640-656. |
| 70 | Chen S, Zhang X, Reiter M K, et al. Detecting privileged side-channel attacks in shielded execution with Déjá Vu[C]∥Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, United Arab Emirates, 2017: 7-18. |
| 71 | Kocher P, Horn J, Fogh A, et al. Spectre attacks: exploiting speculative execution[J]. Communications of the ACM, 2020, 63(7): 93-101. |
| 72 | Shinde S, Chua Z L, Narayanan V, et al. Preventing page faults from telling your secrets[C]∥Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi'an, China, 2016: 317-328. |
| 73 | van Bulck J, Minkin M, Weisse O, et al. Foreshadow: extracting the keys to the intel SGX kingdom with transient out-of-order execution[C]∥27th USENIX Security Symposium, Baltimore, USA, 2018: 991–1008. |
| 74 | Kocher P, Horn J, Fogh A, et al. Spectre attacks: Exploiting speculative execution[J]. Communications of the ACM, 2020, 63(7): 93-101. |
| 75 | Lipp M, Schwarz M, Gruss D, et al. Meltdown: Reading kernel memory from user space[J]. Communications of the ACM, 2020, 63(6): 46-56. |
| 76 | Ramesh C, Patil S B, Dhanuskodi S N, et al. FPGA side channel attacks without physical access[C]∥2018 IEEE 26th Annual International Symposium on Field-Programmable Custom Computing Machines, Boulder, CO, USA, 2018: 45-52. |
| 77 | Buhren R, Jacob H N, Krachenfels T, et al. One glitch to rule them all: fault injection attacks against amd's secure encrypted virtualization[C]∥Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Korea, 2021: 2875-2889. |
| 78 | Halderman J A, Schoen S D, Heninger N, et al. Lest we remember: cold-boot attacks on encryption keys[J]. Communications of the ACM, 2009, 52(5): 91-98. |
| 79 | Pandey S S, Banerjee N, Xie Y, et al. Self‐destructing secured microchips by on‐chip triggered energetic and corrosive attacks for transient electronics[J]. Advanced Materials Technologies, 2018, 3(7): No. 1800044. |
| 80 | Srilatha P. Self destructing electronics[J]. IOSR Journal of Electrical and Electronics Engineering, 2014, 9(3): 24-30. |
| 81 | Yitbarek S F, Aga M T, Das R, et al. Cold boot attacks are still hot: security analysis of memory scramblers in modern processors[C]∥2017 IEEE International Symposium on High Performance Computer Architecture, Austin, TX, USA, 2017: 313-324. |
| 82 | Halderman J A, Schoen S D, Heninger N, et al. Lest we remember: cold-boot attacks on encryption keys[J]. Communications of the ACM, 2009, 52(5): 91-98. |
| 83 | Gruhn M, Müller T. On the practicability of cold boot attacks[C]∥2013 International Conference on Availability, Reliability and Security, Regensburg, Germany, 2013: 390-397. |
| 84 | Jyothi V, Thoonoli M, Stern R,et al.FPGA trust zone: incorporating trust and reliability into FPGA designs[C]∥2016 IEEE 34th International Conference on Computer Design,Scottsdale,AZ,USA, 2016: 600-605. |
| 85 | Azab A M, Swidowski K, Bhutkar R, et al. SKEE: a lightweight secure kernel-level execution environment for ARM[C]∥NDSS, San Diego, CA, USA 2016: 21-24. |
| 86 | Mark H. Computing's energy problem (and what we can do about it)[C]∥Proceedings of the IEEE International Solid-State Circuits Conference, San Francisco, CA, USA. 2014: 9-13. |
| [1] | Qian CAO,Zhi-hui LI,Peng-fei TAO,Hai-tao LI,Yong-jian MA. Deployment of heterogeneous sensors for traffic accident detection and prevention [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(4): 969-978. |
| [2] | Zhi-gang JIN,Ren-jun SU,Xiao-fang ZHAO. Psychological assessment method based on heterogeneous graph network [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(4): 1078-1085. |
| [3] | Qiu-ju YANG. Multisource heterogeneous sensor data fusion model based on fuzzy theory [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(10): 3058-3063. |
| [4] | Ze-qiang ZHANG,Wei LIANG,Meng-ke XIE,Hong-bin ZHENG. Elite differential evolution algorithm for mixed⁃model two⁃side disassembly line balancing problem [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(5): 1297-1304. |
| [5] | Zhi-fa YANG,Bo SUN,Xian-jun FAN,Wen-cai SUN,Jing-jing TIAN,Ning SUN. Simulation on energy consumption of truck fleet on expressway under background of vehicle⁃infrastructure cooperative environment [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(12): 3452-3457. |
| [6] | Qian CAO,Zhi-hui LI,Peng-fei TAO,Yong-jian MA,Chen-xi YANG. Traffic accident risk assessment method for road network considering risk heterogeneity [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(10): 2817-2825. |
| [7] | Xiao-ning LI,Hong-wei ZHAO,Dan-yang ZHANG,Yuan ZHANG. Image retrieval algorithm based on response value center weighted convolution feature [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(11): 2669-2675. |
| [8] | Dong-ming SUN,Liang HU,Yong-heng XING,Feng WANG. Text fusion based internet of things service recommendation for trigger⁃action programming pattern [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(6): 2182-2189. |
| [9] | Li-li REN,Zhi-jun WANG,Dong-mei YAN. Improved multi⁃verse algorithm with combined slime mould foraging behavior [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(6): 2190-2197. |
| [10] | Bing-hai ZHOU,Qiong WU. Balancing and bi⁃objective optimization of robotic assemble lines [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 720-727. |
| [11] | Xiao-hui WEI,Bing-yi SUN,Jia-xu CUI. Recommending activity to users via deep graph neural network [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 278-284. |
| [12] | Bing-hai ZHOU,Qiong WU. Balancing and optimization of robotic assemble lines withtool and space constraint [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2069-2075. |
| [13] | Bin LI,Guo⁃jun SHEN,Geng SUN,Ting⁃ting ZHENG. Improved chicken swarm optimization algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(4): 1339-1344. |
| [14] | Xiao⁃qin LUO,Dian⁃hai WANG,Sheng JIN. Traffic signal actuated control at isolated intersections for heterogeneous traffic [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(3): 695-704. |
| [15] | WU Wei-nan,CUI Nai-gang,GUO Ji-feng,ZHAO Yang-yang. Distributed integrated method for mission planning of heterogeneous unmanned aerial vehicles [J]. Journal of Jilin University(Engineering and Technology Edition), 2018, 48(6): 1827-1837. |
|
||