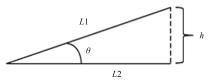
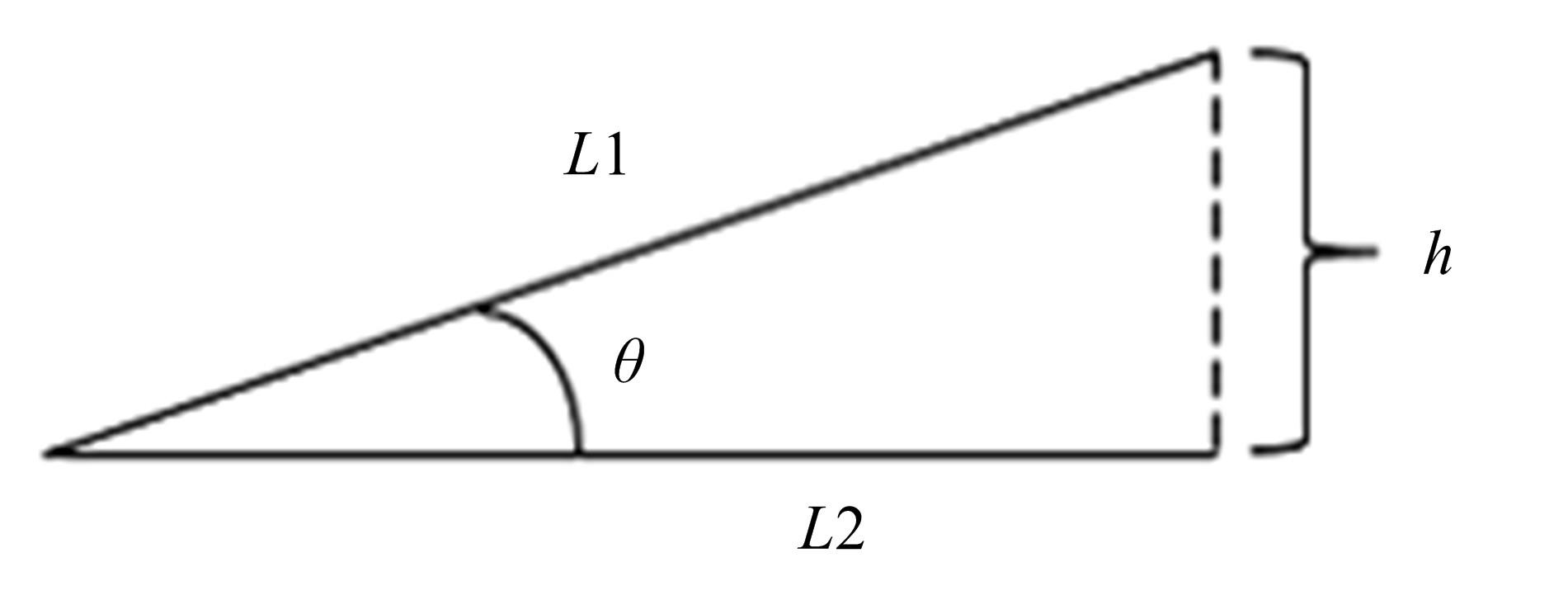
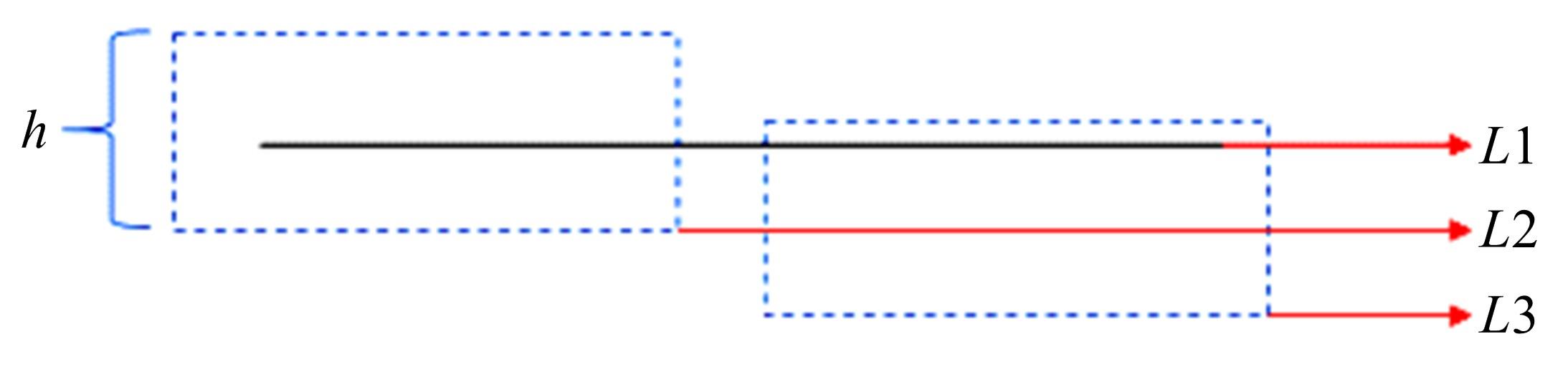
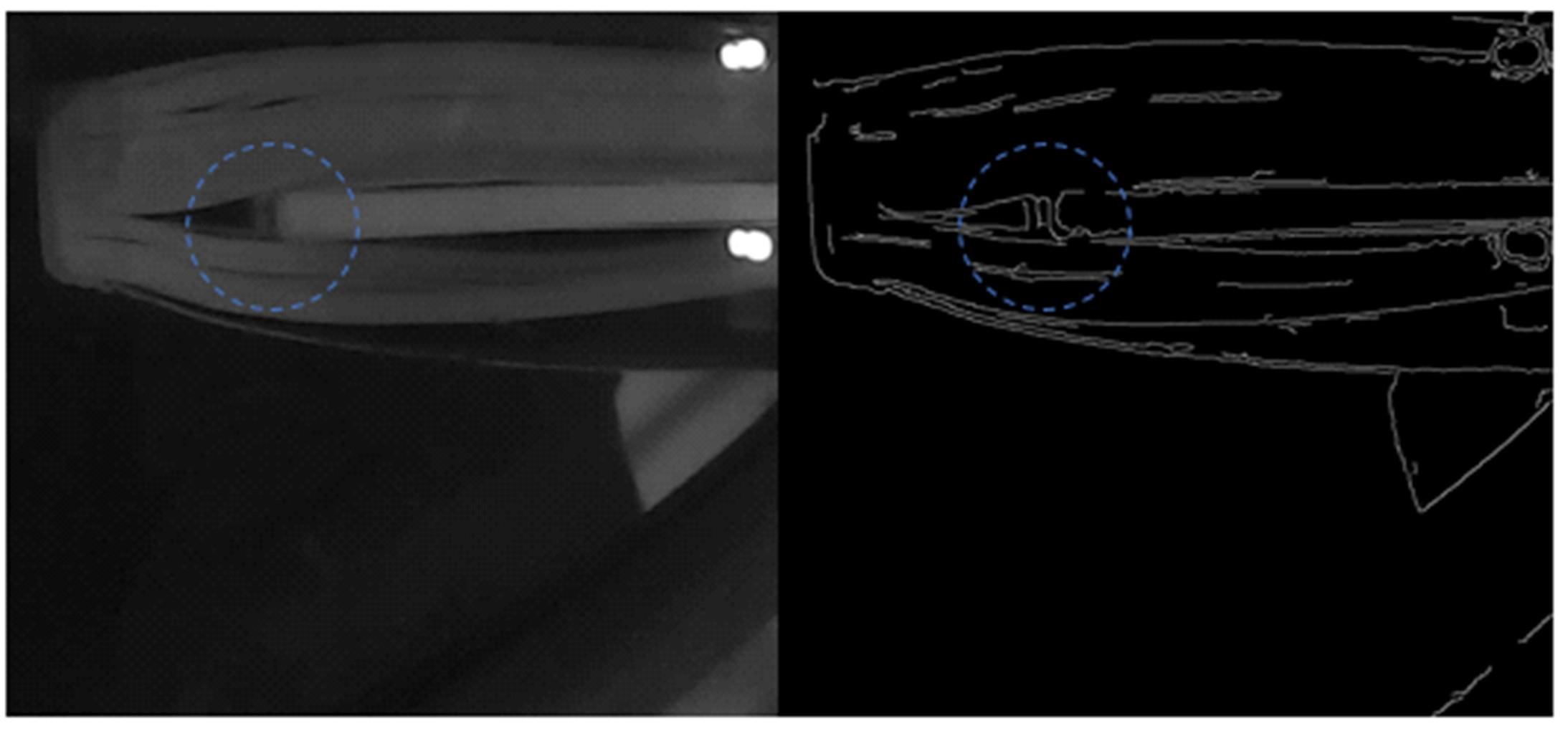
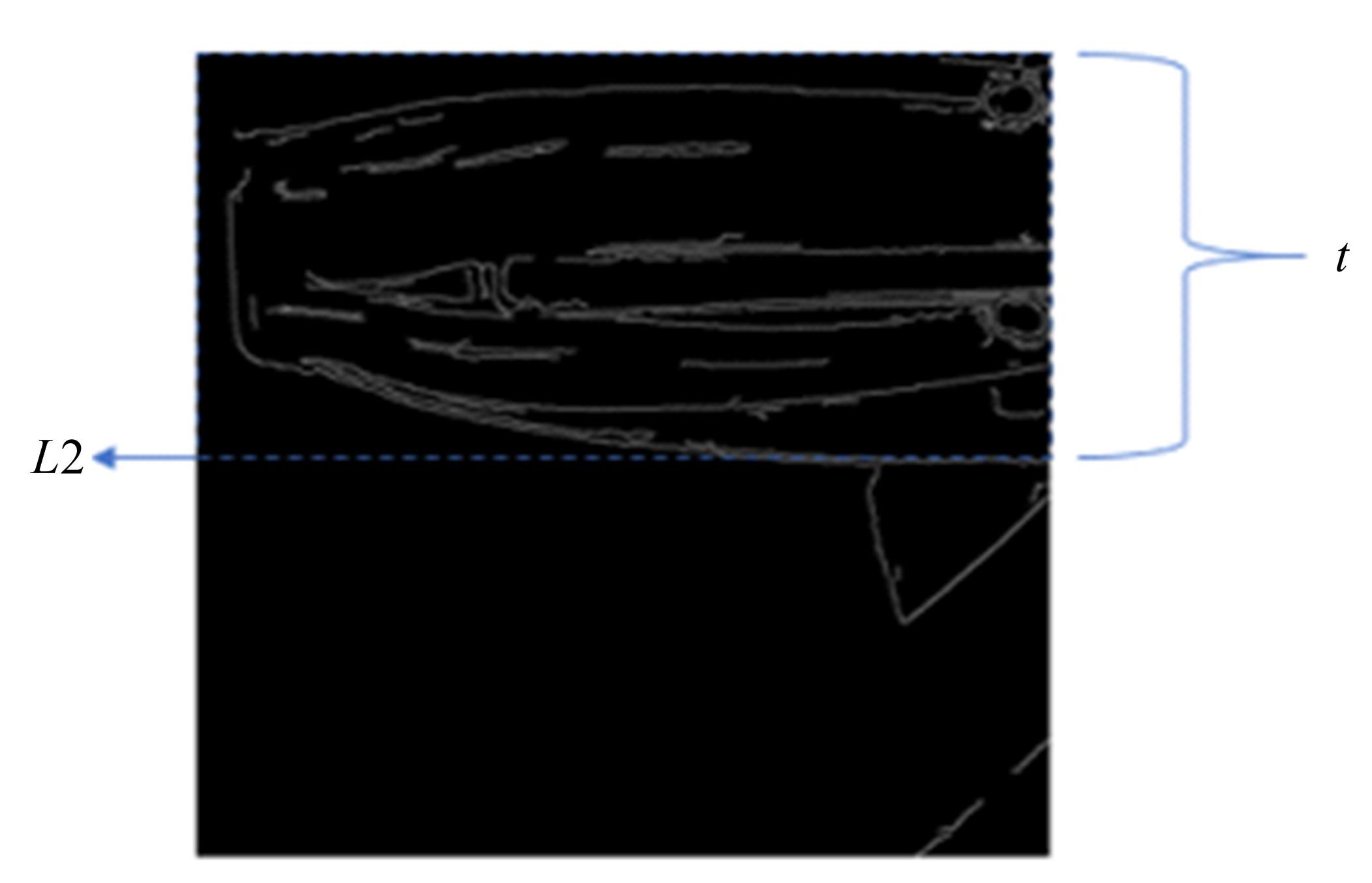
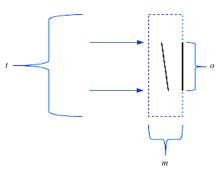
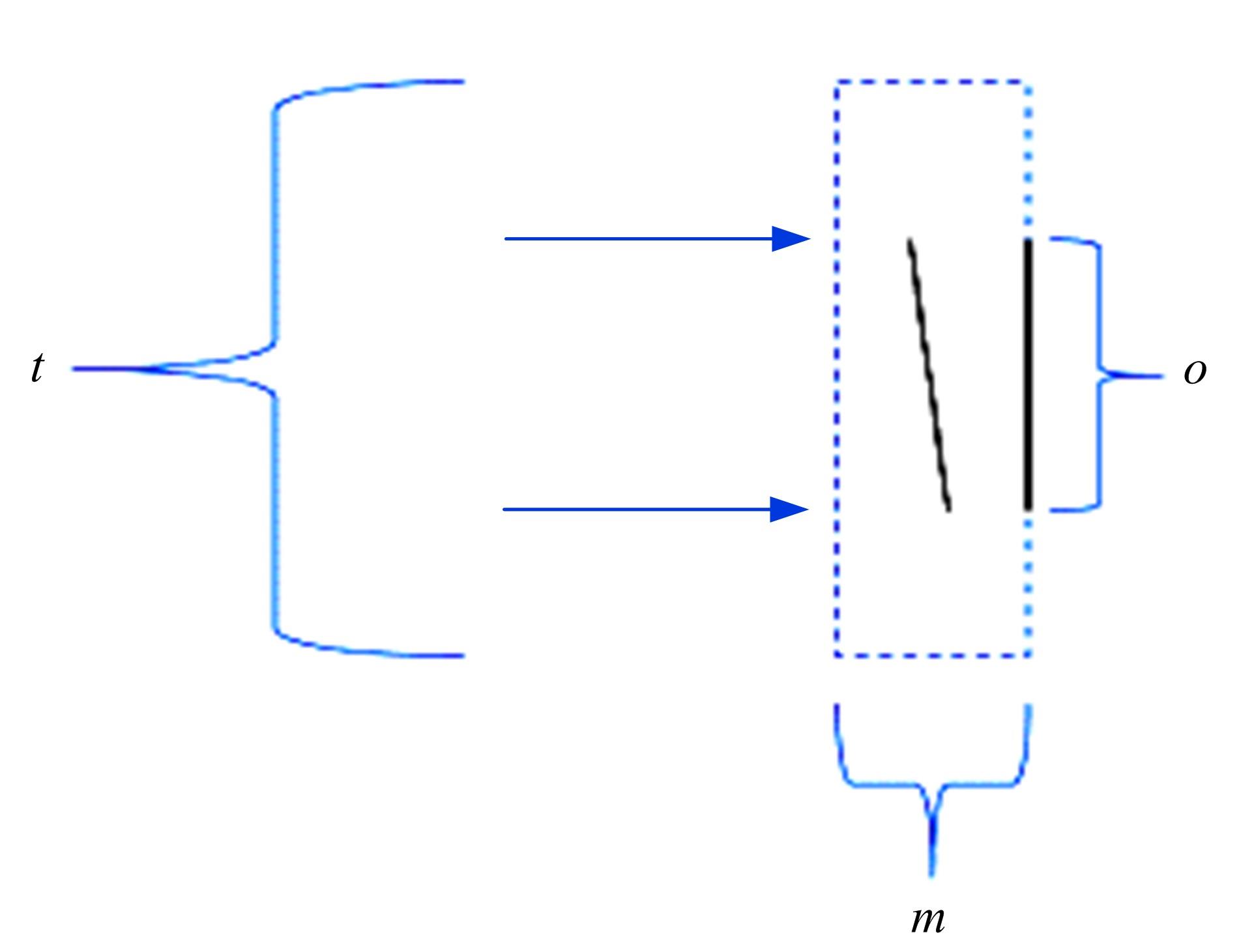
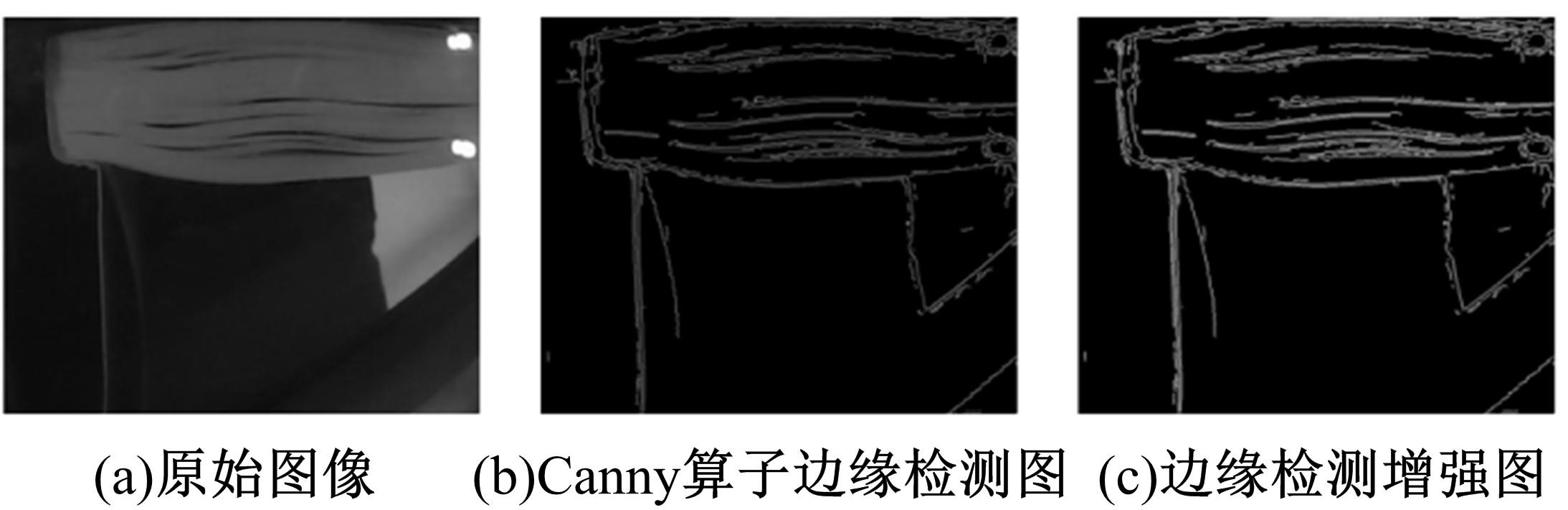
Journal of Jilin University(Engineering and Technology Edition) ›› 2022, Vol. 52 ›› Issue (4): 891-896.doi: 10.13229/j.cnki.jdxbgxb20200933
Application of enhanced edge detection image algorithm in multi-book recognition
Ming LIU1,2( ),Yu-hang YANG1,Song-lin ZOU1,Zhi-cheng XIAO1,Yong-gang ZHANG2
),Yu-hang YANG1,Song-lin ZOU1,Zhi-cheng XIAO1,Yong-gang ZHANG2
- 1.School of Mathematics and Statistics,Changchun University of Technology,Changchun 130012,China
2.Key Laboratory of Symbolic Computation and Knowledge Engineering of Ministry of Education,Jilin University,Changchun 130012,China
CLC Number:
- TP183
| 1 | 丁晓燕. 图书馆自助借还系统的比较分析[J]. 图书情报工作, 2018, 62(22): 78-81. |
| Ding Xiao-yan. Comparative analysis of library self-check system[J]. Library and Information Service, 2018, 62(22): 78-81. | |
| 2 | 黄敏聪. 图书馆分布式借还书系统分析[J]. 图书情报工作, 2012, 56 (1): 102-106. |
| Huang Min-cong. Distributed system in books circulation of libraries[J]. Library And Information Service, 2012, 56 (1): 102-106. | |
| 3 | Yuan K H, Hong A C, Ang M, et al. Unmanned library: an intelligent robotic books retrieval & return system utilizing RFID tags[C]∥IEEE International Conference on Systems, Man and Cybernetics, Yasmine Hammamet, Tunisia, 2002: 1-5. |
| 4 | 齐凌, 宓永迪. RFID自助借还系统使用情况分析─以浙江图书馆为例[J]. 图书馆建设, 2011, 33(10): 77-79. |
| Qi Ling, Mi Yong-di. Analysis on the utilization situation of RFID self-service check-out system-taking Zhejiang library as an example[J]. Library Construction, 2011, 33(10): 77-79. | |
| 5 | Bahri S, Ibrahim A. RFID in libraries: a case study on implementation[J]. Library Hi-Tech News, 2013, 30(5): 21-26. |
| 6 | Coyle K. Management of RFID in libraries[J]. Journal of Academic Librarianship, 2005, 31(5): 486-489. |
| 7 | San Francisco Public Library Technology and Privacy Advisory Committee. Radio Frequency Identification and the San Francisco Public Library: Summary Report[M]. New York: American Academic Press, 2005. |
| 8 | Molnar D, Wagner D. Privacy and security in library RFID: issues, practices, and architectures[C]∥Proceedings of the 11th ACM Conference on Computer and Communications Security, CCS Washington, DC, USA, 2004: 1-20. |
| 9 | 刘喜球. 论网络环境下图书馆自助借阅的几种发展模式[J]. 图书馆学研究, 2018, 38(16): 31-35. |
| Liu Xi-qiu. On several development models of library's self-service borrowing and reading[J]. Research on Library Science, 2018, 38(16): 31-35. | |
| 10 | 陈章. 我国24小时自助图书馆的发展困境与对策研究[D]. 青岛:青岛科技大学传媒学院, 2018. |
| Chen Zhang. Study on the development predicaments and strategies of China's 24-hour self-service libraries[D]. Qingdao: College of Communication, Qingdao University of Science and Technology, 2018. | |
| 11 | 肖宇锋, 江洪. 我国自助图书馆服务理论与实践现状分析[J]. 图书馆学研究, 2011, 31(18): 60-63. |
| Xiao Yu-feng, Jiang Hong. Analysis on the current situation of the theory and practice of self-service library service in my country[J]. Research on Library Science, 2011, 31(18): 60-63. | |
| 12 | 姜元鹏, 王群, 史慧丹. 图书馆自助借还书系统的测试与评析[J]. 农业图书情报学刊, 2015, 27(12): 49-53. |
| Jiang Yuan-peng, Wang Qun, Shi Hui-dan. Testing and analysis of self-cheek system in libraries[J]. Journal of Library and Information Sciences in Agriculture, 2015, 27(12): 49-53. | |
| 13 | Peilegrino F A, Vanzdla W. Edge detection revisited[J]. IEEE Trans on Systems,Man and Cyberrnetics, 2004, 34(3): 1500-1518. |
| 14 | Ziou D . Tabbone S. Edge detection techniques--an overview[J]. International Journal of Pattern Recognition and Image Analysis, 1998, 8(4): 537-559. |
| 15 | Gupta S, Mazumdar S G. Sobel edge detection algorithm[J]. International journal of computer science and management Research, 2013, 2(2): 1578-1583. |
| 16 | Shrivakshan G T, Chandrasekar C. A comparison of various edge detection techniques used in image processing[J]. International Journal of Computer Science Issues, 2012, 9(5): 269-276. |
| 17 | 宋人杰, 刘超, 王保军. 一种自适应的Canny边缘检测算法[J]. 南京邮电大学学报: 自然科学版, 2018, 38(3): 72-76. |
| Song Ren-jie, Liu Chao, Wang Bao-jun. Adaptive Canny edge detection algorithm[J]. Journal of Nanjing University of Posts and Telecommunications (Natural Science), 2018, 38(3): 72-76. |
| [1] | Shi-min FANG. Multiple source data selective integration algorithm based on frequent pattern tree [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 885-890. |
| [2] | Sheng-sheng WANG,Jing-yu CHEN,Yi-nan LU. COVID⁃19 chest CT image segmentation based on federated learning and blockchain [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(6): 2164-2173. |
| [3] | Hong-wei ZHAO,Zi-jian ZHANG,Jiao LI,Yuan ZHANG,Huang-shui HU,Xue-bai ZANG. Bi⁃direction segmented anti⁃collision algorithm based on query tree [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(5): 1830-1837. |
| [4] | Jie CAO,Xue QU,Xiao-xu LI. Few⁃shot image classification method based on sliding feature vectors [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(5): 1785-1791. |
| [5] | Chun-bo WANG,Xiao-qiang DI. Cloud storage integrity verification audit scheme based on label classification [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1364-1369. |
| [6] | Hua-wei JIANG,Zhen YANG,Xin ZHANG,Qian-lin DONG. Research progress of image dehazing algorithms [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1169-1181. |
| [7] | Rong QIAN,Ru ZHANG,Ke-jun ZHANG,Xin JIN,Shi-liang GE,Sheng JIANG. Capsule graph neural network based on global and local features fusion [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1048-1054. |
| [8] | Qian-yi XU,Gui-he QIN,Ming-hui SUN,Cheng-xun MENG. Classification of drivers' head status based on improved ResNeSt [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 704-711. |
| [9] | Fu LIU,Lu LIU,Tao HOU,Yun LIU. Night road image enhancement method based on optimized MSR [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 323-330. |
| [10] | Yuan SONG,Dan-yuan ZHOU,Wen-chang SHI. Method to enhance security function of OpenStack Swift cloud storage system [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 314-322. |
| [11] | Xiang-jiu CHE,You-zheng DONG. Improved image recognition algorithm based on multi⁃scale information fusion [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1747-1754. |
| [12] | HU Guan-yu, QIAO Pei-li. High dimensional differential evolutionary algorithm based on cloud population for network security prediction [J]. 吉林大学学报(工学版), 2016, 46(2): 568-577. |
| [13] | LI Zhen-hui, WANG Hong-guang, WANG Yue-chao, JIANG Yong, YUE Xiang. Line-grasping control for a power transmission line inspection robot [J]. 吉林大学学报(工学版), 2015, 45(5): 1519-1526. |
| [14] | ZHANG Bao-hua, HUANG Wen-qian, LI Jiang-bo, ZHAO Chun-jiang, LIU Cheng-liang, HUANG Dan-feng. Online sorting of irregular potatoes based on I-RELIEF and SVM method [J]. 吉林大学学报(工学版), 2014, 44(6): 1811-1817. |
| [15] | WU Yi-quan,WU Shi-hua,ZHANG Yu-fei. Infrared image adaptive enhancement in Contourlet domain based on chaotic particle swarm optimization [J]. 吉林大学学报(工学版), 2014, 44(5): 1466-1473. |
|
||