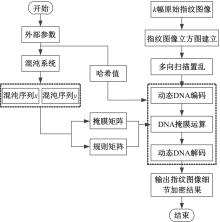
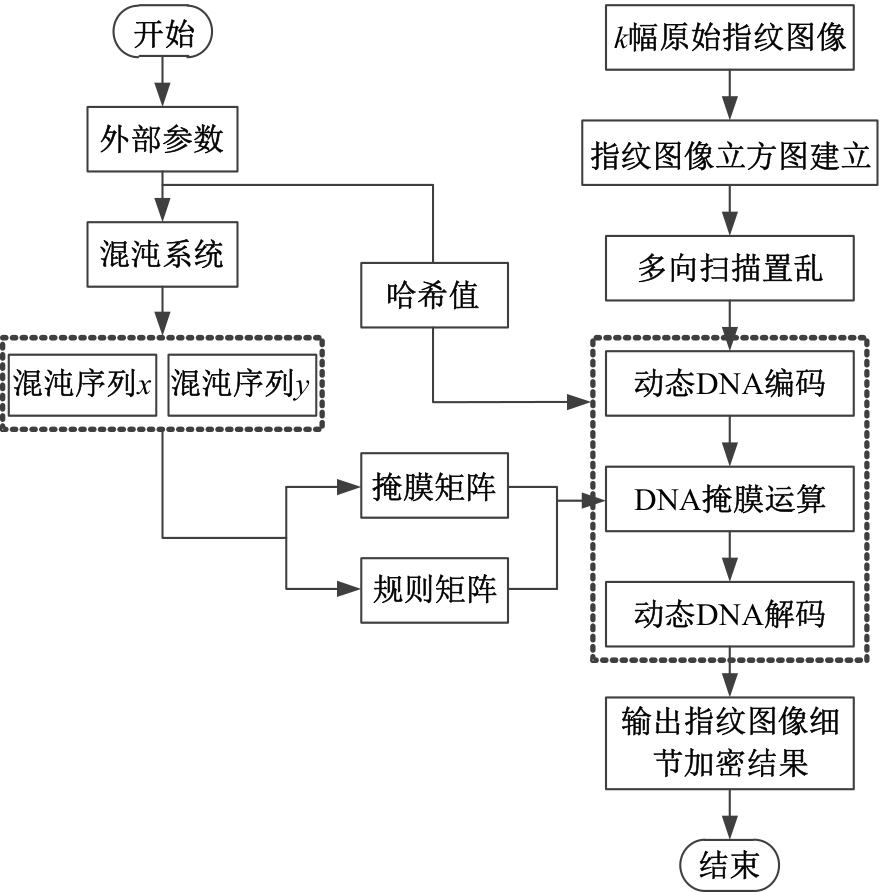
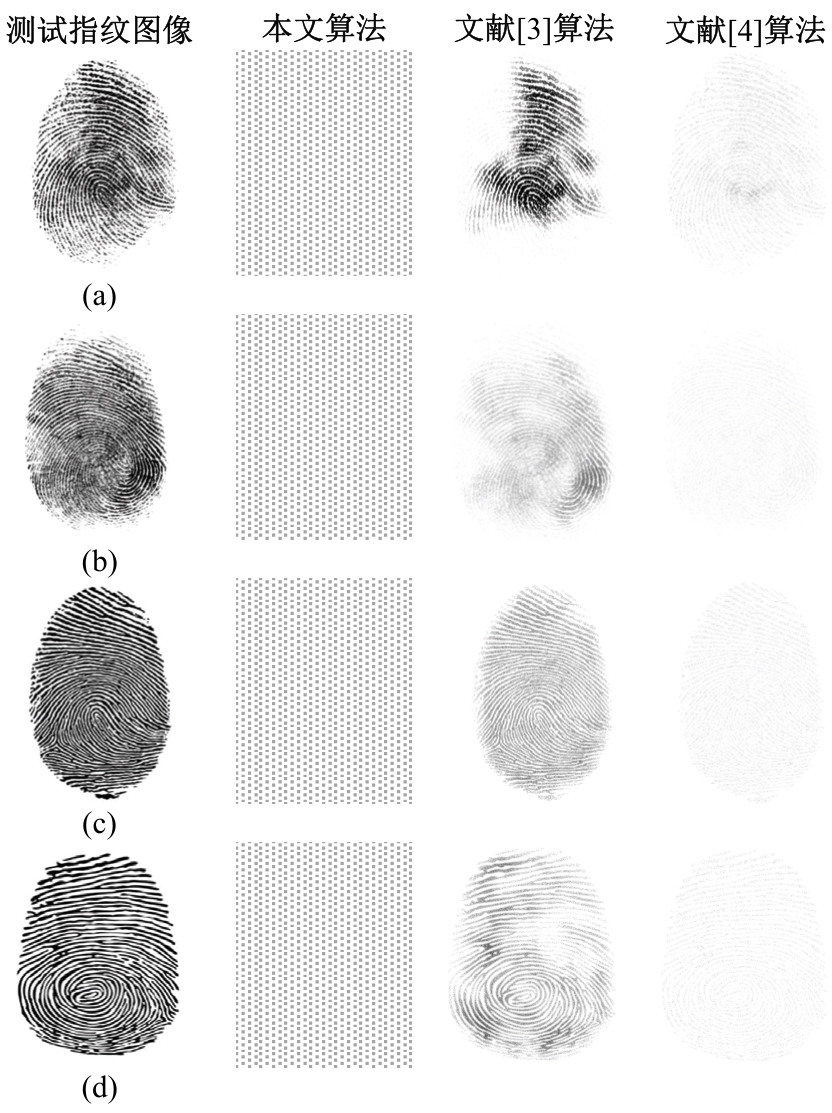
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (2): 687-692.doi: 10.13229/j.cnki.jdxbgxb.20231450
A few sample condition fingerprint image detail encryption algorithm considering privacy information security
- National Security Academy,Chinese People's Public Security University,Beijing 100038,China
CLC Number:
- TP309
| 1 | 史进, 蔡竞, 徐锋. 傅里叶变换耦合DNA编码的图像加密算法[J].计算机工程与设计, 2021, 42(7): 1874-1881. |
| Shi Jin, Cai Jing, Xu Feng. Image encryption algorithm based on Fourier transform and DNA coding [J]. Computer Engineering and Design, 2021, 42(7): 1874-1881. | |
| 2 | 周红亮, 刘洪娟. 结合DNA编码的快速混沌图像加密算法[J].东北大学学报: 自然科学版, 2021, 42(10): 1391-1399. |
| Zhou Hong-liang, Liu Hong-juan. Fast chaotic image encryption algorithm combined with DNA encoding [J]. Journal of Northeastern University (Natural Science), 2021, 42 (10): 1391-1399. | |
| 3 | 王佳, 刘丽. 基于混沌卷积的光学图像分块加密方法[J]. 激光与光电子学进展, 2023, 60(4): 101-109. |
| Wang Jia, Liu Li. Optical image block encryption method based on chaotic convolution[J]. Laser & Optoelectronics Progress, 2023, 60(4): 101-109. | |
| 4 | 李春彪, 赵云楠, 李雅宁, 等. 基于正弦反馈Logistic混沌映射的图像加密算法及其FPGA实现[J]. 电子与信息学报, 2021, 43(12): 3766-3774. |
| Li Chun-biao, Zhao Yun-nan, Li Ya-ning, et al. An image encryption algorithm based on logistic chaotic mapping with sinusoidal feedback and its FPGA implementation[J]. Journal of Electronics & Information Technology, 2021, 43(12): 3766-3774. | |
| 5 | 陈善学, 杜文正, 任丽丹. 一种动态密钥与DNA交错编码的多图像加密算法[J]. 电讯技术, 2023, 63(4): 529-535. |
| Chen Shan-xue, Du Wen-zheng, Ren Li-dan. A multi-image encryption algorithm based on dynamic key and DNA interleaved coding[J]. Telecommunication Engineering, 2023, 63(4): 529-535. | |
| 6 | 石玲玉, 吴雁南, 周铭, 等. 基于点阵行列变换的图像置乱算法[J]. 南昌大学学报: 理科版, 2022, 46(6): 674-681. |
| Shi Ling-yu, Wu Yan-nan, Zhou Ming, et al. Image scrambing algorithm based on row and column transformation of lattice[J]. Journal of Nanchang University (Natural Science), 2022, 46(6): 674-681. | |
| 7 | 杨盼盼, 赵继春. 基于状态视图的流媒体图像信息置乱隐藏算法[J]. 计算机应用, 2021, 41(6): 1729-1733. |
| Yang Pan-pan, Zhao Ji-chun. Scrambling and hiding algorithm of streaming media image information based on state view[J]. Journal of Computer Applications, 2021, 41(6): 1729-1733. | |
| 8 | 靳旭文, 李国东, 刘雯. 基于3D-CS混沌系统的双DNA编码图像加密算法[J]. 包装工程, 2021, 42(3): 259-269. |
| Jin Xu-wen, Li Guo-dong, Liu Wen. Image encryption algorithm based on 3D-CS chaotic system and dual DNA coding[J]. Packaging Engineering, 2021, 42(3): 259-269. | |
| 9 | 张军朋, 向菲. 基于DNA随机置换的新型图像加密算法研究[J]. 计算机仿真, 2022, 39(7): 355-361. |
| Zhang Jun-peng, Xiang Fei. A novel image encryption algorithm based on DNA random permutation[J]. Computer Simulation, 2022, 39(7): 355-361. | |
| 10 | 王一诺, 宋昭阳, 马玉林, 等. 基于DNA编码与交替量子随机行走的彩色图像加密算法[J]. 物理学报, 2021, 70(23): 32-41. |
| Wang Yi-nuo, Song Zhao-yang, Ma Yu-lin,et al. Color image encryption algorithm based on DNA code and alternating quantum random walk[J]. Acta Physica Sinica, 2021, 70(23): 32-41. |
| [1] | Han-chi YAN,Chun-lin SU. Hybrid encryption method for biological information database based on AES and hash algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(10): 2994-2999. |
| [2] | Yang-xia LUO,Yan-ling WU. Chaos theory to PE and improving method of watermark data rate [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(10): 3000-3008. |
| [3] | Wei-wei LUO,Shao-wei LIU,Bing-tao ZHANG,Meng LI,Hai-luan LIU,Ling-yan FAN. Steganalysis of spatial image combining fusion features and feature mapping [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(11): 3260-3267. |
| [4] | Xian-feng GUO,Hao-hua LI,Jin-yu WEI. Image encryption scheme based on Fibonacci transform and improved Logistic-Tent chaotic map [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(7): 2115-2120. |
| [5] | Xi-yan LI,Xia-bing ZHOU,Zheng LIU. High-capacity and robust image watermarking algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(1): 174-179. |
| [6] | Guang-song LI,Wen-qing LI,Qing LI. Encrypted and compressed traffic classification based on random feature set [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1375-1386. |
| [7] | Chun-bo WANG,Xiao-qiang DI. Cloud storage integrity verification audit scheme based on label classification [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1364-1369. |
| [8] | Yi-cheng YU,Liang HU,Ling CHI,Jian-feng CHU. An anonymous authentication protocol for single⁃server architectures [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 659-666. |
| [9] | Yuan SONG,Dan-yuan ZHOU,Wen-chang SHI. Method to enhance security function of OpenStack Swift cloud storage system [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 314-322. |
| [10] | Hong-song CHEN,Jing-jiu CHEN. Statistical based distributed denial of service attack detection research in internet of things [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1894-1904. |
| [11] | YU Yi-cheng, HU Liang, CHI Ling, CHU Jian-feng. Improved anonymous authentication protocol for multi-server architectures [J]. Journal of Jilin University(Engineering and Technology Edition), 2018, 48(5): 1586-1592. |
| [12] | YANG Hong-yu, XU Jin. An Android malware static detection model [J]. 吉林大学学报(工学版), 2018, 48(2): 564-570. |
| [13] | ZHAO Bo, QIN Gui-He, ZHAO Yong-Zhe, YANG Wen-Di. Public key cryptosystem based on semi-trapdoor one-way function [J]. 吉林大学学报(工学版), 2018, 48(1): 259-267. |
| [14] | LUO Yang-xia, GUO Ye. Software recognition based on features of data dependency [J]. 吉林大学学报(工学版), 2017, 47(6): 1894-1902. |
| [15] | HAN Jia-ling, ZHAO Xiao-hui. Adjustable reversible data hiding algorithm with large embedded capacity based on image gradient prediction [J]. 吉林大学学报(工学版), 2016, 46(6): 2074-2079. |
|
||