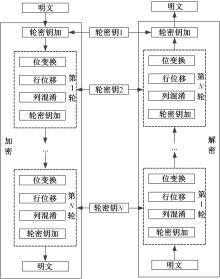
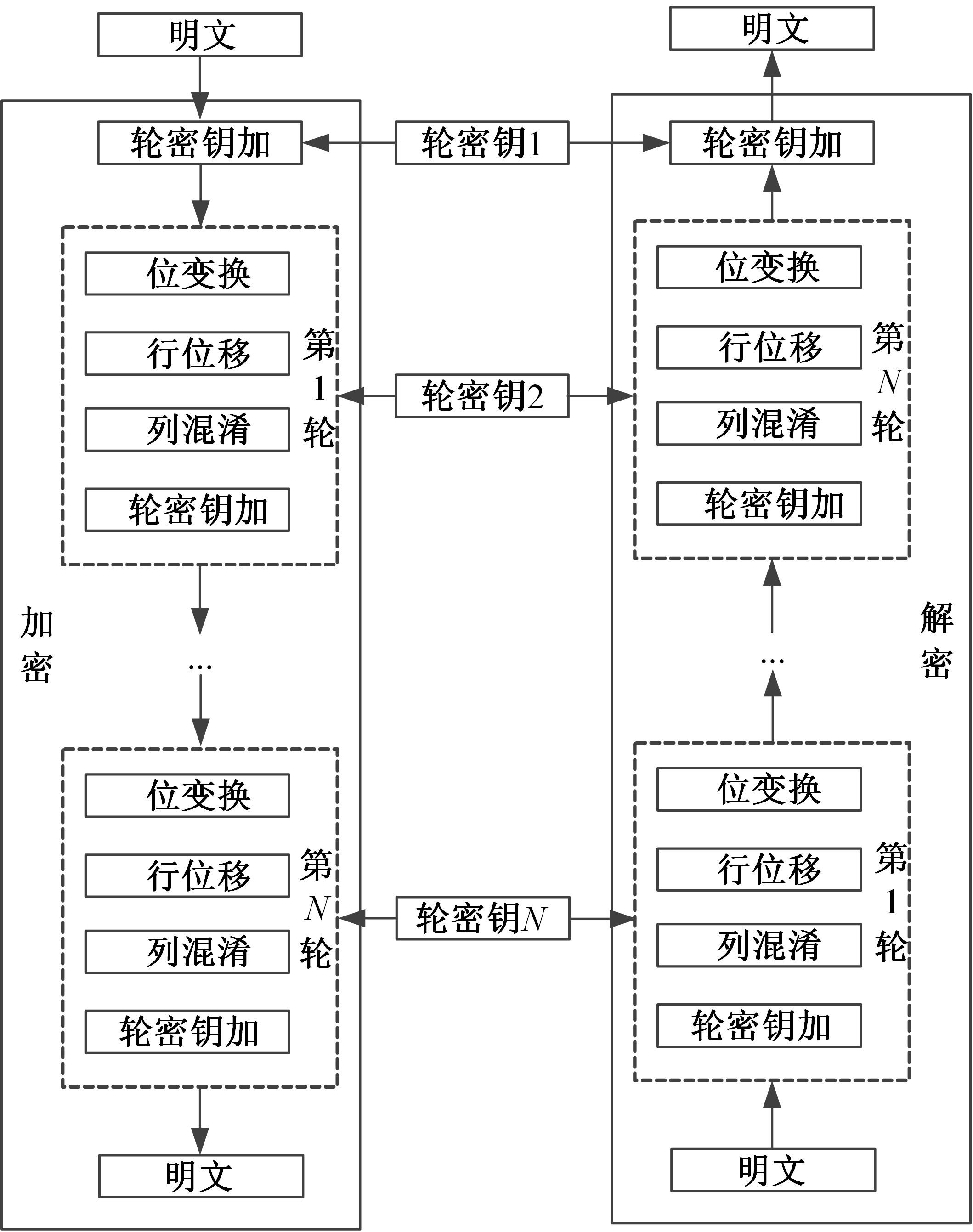
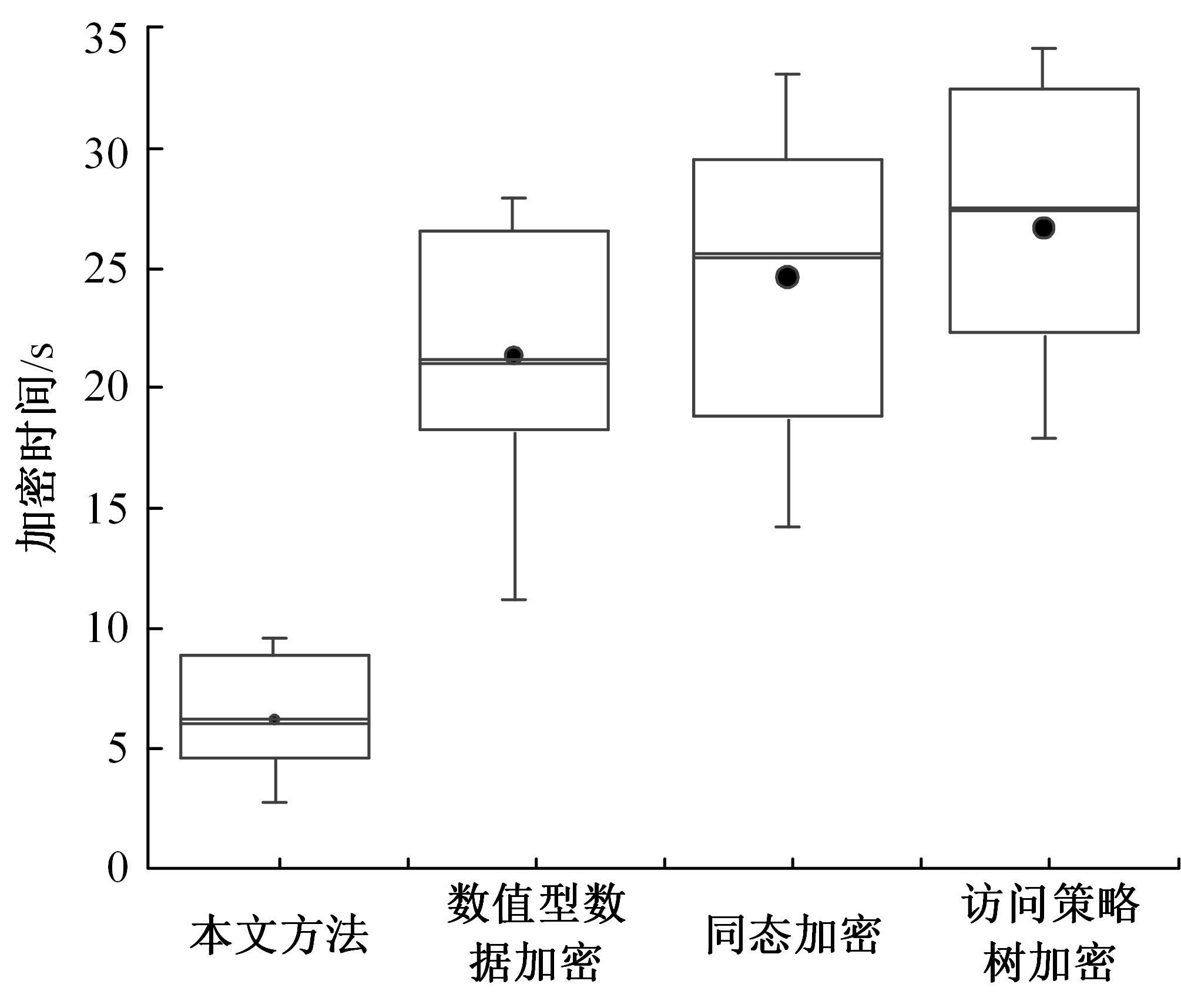
| 1 |
曹慧,刘馨莲,张录顺.生物信息数据库分析INHBA在结直肠癌中的表达及临床意义[J].电子科技大学学报,2022,51(2): 295-304.
|
|
Cao Hui, Liu Xin-lian, Zhang Lu-shun. Expression and clinical significance of INHBA in colorectal cancer based on bioinformatics databases[J]. Journal of University of Electronic Science and Technology of China, 2022, 51(2): 295-304.
|
| 2 |
王建茹,彭广操,朱明军.基于GEO数据库和生物信息学分析筛选小鼠心肌缺血再灌注损伤相关的潜在枢纽基因[J].上海交通大学学报:医学版,2022,42(1): 51-62.
|
|
Wang Jian-ru, Peng Guang-cao, Zhu Ming-jun. Screening potential hub genes associated with myocardial ischemia-reperfusion injury in mice based on GEO database and bioinformatics analysis[J]. Journal of Shanghai Jiaotong University(Medical Science), 2022,42(1): 51-62.
|
| 3 |
王一鹤,王焱,底斐瑶,等.基于TCGA数据库对前列腺癌中免疫相关的长链非编码RNA(lncRNA)的生物信息学分析[J].细胞与分子免疫学杂志,2021,37(2): 113-118.
|
|
Wang Yi-he, Wang Yan, Di Fei-yao, et al. Bioinformatic analysis of immune-related lncRNA based on TCGA database in patients with prostate cancer[J]. Chinese Journal of Cellular and Molecular Immunology, 2021,37(2): 113-118.
|
| 4 |
龙草芳,肖衡.无线传感器网络分布式数据库加密方法研究[J].传感技术学报,2022,35(8):1131-1136.
|
|
Long Cao-fang, Xiao Heng. Research on encryption method of distributed database in wireless sensor network[J]. Chinese Journal of Sensors and Actuators, 2022,35(8): 1131-1136.
|
| 5 |
孙僖泽,周福才,李宇溪,等.基于可搜索加密机制的数据库加密方案[J].计算机学报,2021,44(4):806-819.
|
|
Sun Xi-ze, Zhou Fu-cai, Li Yu-xi, et al. A database encryption scheme based on searchable encryption[J]. Chinese Journal of Computers, 2021,44(4): 806-819.
|
| 6 |
陈君.基于B/S结构的异构数据库加密算法仿真[J].计算机仿真,2021,38(4):236-239, 262.
|
|
Chen Jun. Simulation of heterogeneous database encryption algorithm based on B/S structure[J]. Computer Simulation, 2021,38(4): 236-239, 262.
|
| 7 |
聂一,郑博文,柴志雷.基于异构可重构计算的AES加密系统研究[J].计算机应用研究,2022,39(7):2143-2148.
|
|
Nie Yi, Zheng Bo-wen, Chai Zhi-lei. AES encryption system based on heterogeneous reconfigurable computing[J]. Application Research of Computers, 2022,39(7): 2143-2148.
|
| 8 |
Jiang H, Zhu X, Pang J, et al. A method for fault recognition in the last three rounds of advanced encryption standard[J]. Electronics Letters, 2021, 57(13): 511-513.
|
| 9 |
Garipcan A M, Design Erdem E., FPGA implementation and statistical analysis of a high-speed and low-area TRNG based on an AES S-box post-processing technique[J]. ISA Transactions, 2021,117: 160-171.
|
| 10 |
辜双佳,刘万平,黄东.基于AES和QR的快递信息加密应用[J].计算机科学,2021,48(): 588-591, 624.
|
|
Gu Shuang-jia, Liu Wan-ping, Huang Dong. Application of express information encryption based on AES and QR[J]. Computer Science, 2021,48(Sup.2): 588-591, 624.
|
| 11 |
Choi P, Kong W, Kim J H, et al. Architectural supports for block ciphers in a RISC CPU core by instruction overloading[J]. IEEE Transactions on Computers, 2021(99): 1-13.
|
| 12 |
Kumar R, Liu X, Suresh V, et al. A time-/frequency-domain side-channel attack resistant AES-128 and RSA-4K crypto-processor in 14 nm CMOS[J]. IEEE Journal of Solid-State Circuits, 2021(99):1-14.
|
| 13 |
童宇,蔡婧雯.针对AES算法的两点联合能量分析攻击及仿真[J].系统仿真学报,2021,33(8): 1980-1988.
|
|
Tong Yu, Cai Jing-wen. Two-point joint CPA attacks against AES and its simulation[J]. Journal of System Simulation, 2021,33(8): 1980-1988.
|
| 14 |
张丽,吴文玲,张蕾,等.基于交换等价的缩减轮AES-128的密钥恢复攻击[J].计算机研究与发展,2021,58(10): 2213-2221.
|
|
Zhang Li, Wu Wen-ling, Zhang Lei, et al. Key-Recovery attack on reduced-round AES-128 using the exchange-equivalence[J]. Journal of Computer Research and Development, 2021,58(10): 2213-2221.
|
| 15 |
谷正川,郭渊博,方晨.基于代理重加密的消息队列遥测传输协议端到端安全解决方案[J].计算机应用,2021,41(5): 1378-1385.
|
|
Gu Zheng-chuan, Guo Yuan-bo, Fang Chen. End-to-end security solution for message queue telemetry transport protocol based on proxy re-encryption[J]. Journal of Computer Applications, 2021,41(5): 1378-1385.
|
| 16 |
Zhang Q, Han J, Ye Y. Multi-image encryption algorithm based on image hash, bit-plane decomposition and dynamic DNA coding[J]. IET Image Processing, 2021,15(4): 885-896.
|
| 17 |
Mao J Y, Pan Q K, Miao Z H, et al. A hash map-based memetic algorithm for the distributed permutation flowshop scheduling problem with preventive maintenance to minimize total flowtime[J]. Knowledge-based Systems, 2022,242(6): No.108413.
|
| 18 |
邓宇乔,宋歌,杨波,等.基于身份的可验证密钥的公钥内积函数加密算法[J].计算机学报,2021,44(1):209-221.
|
|
Deng Yu-qiao, Song Ge, Yang Bo, et al. Identity-based inner product functional encryption with verified secret key[J]. Chinese Journal of Computers, 2021,44(1): 209-221.
|
| 19 |
魏爽,江荣旺,乔艳琰.基于无证书代理环签名的光纤通信数据加密传输[J].激光杂志,2022,43(9):154-158.
|
|
Wei Shuang, Jiang Rong-wang, Qiao Yan-yan. Encryption transmission of optical fiber communication data based on certificateless proxy ring signature[J]. Laser Journal, 2022,43(9): 154-158.
|
| 20 |
潘登,钟诚.二级Hash全局和局部索引筛选的长序列比对并行算法[J].小型微型计算机系统,2022,43(9): 1999-2004.
|
|
Pan Deng, Zhong Cheng. Parallel algorithm for long-read alignment using two-level global and local hash index filtering[J]. Journal of Chinese Computer Systems, 2022,43(9): 1999-2004.
|
| 21 |
黎琳,张芳,张闻宇.一种实现数据库同态计算的ELGamal重加密算法[J]. 北京交通大学学报,2021,45(2): 127-134.
|
|
Li Lin, Zhang Fang, Zhang Wen-yu. ELGamal re-encryption algorithm for database homomorphic computation[J]. Journal of Beijing Jiaotong University, 2021,45(2): 127-134.
|