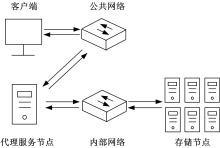
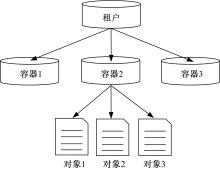
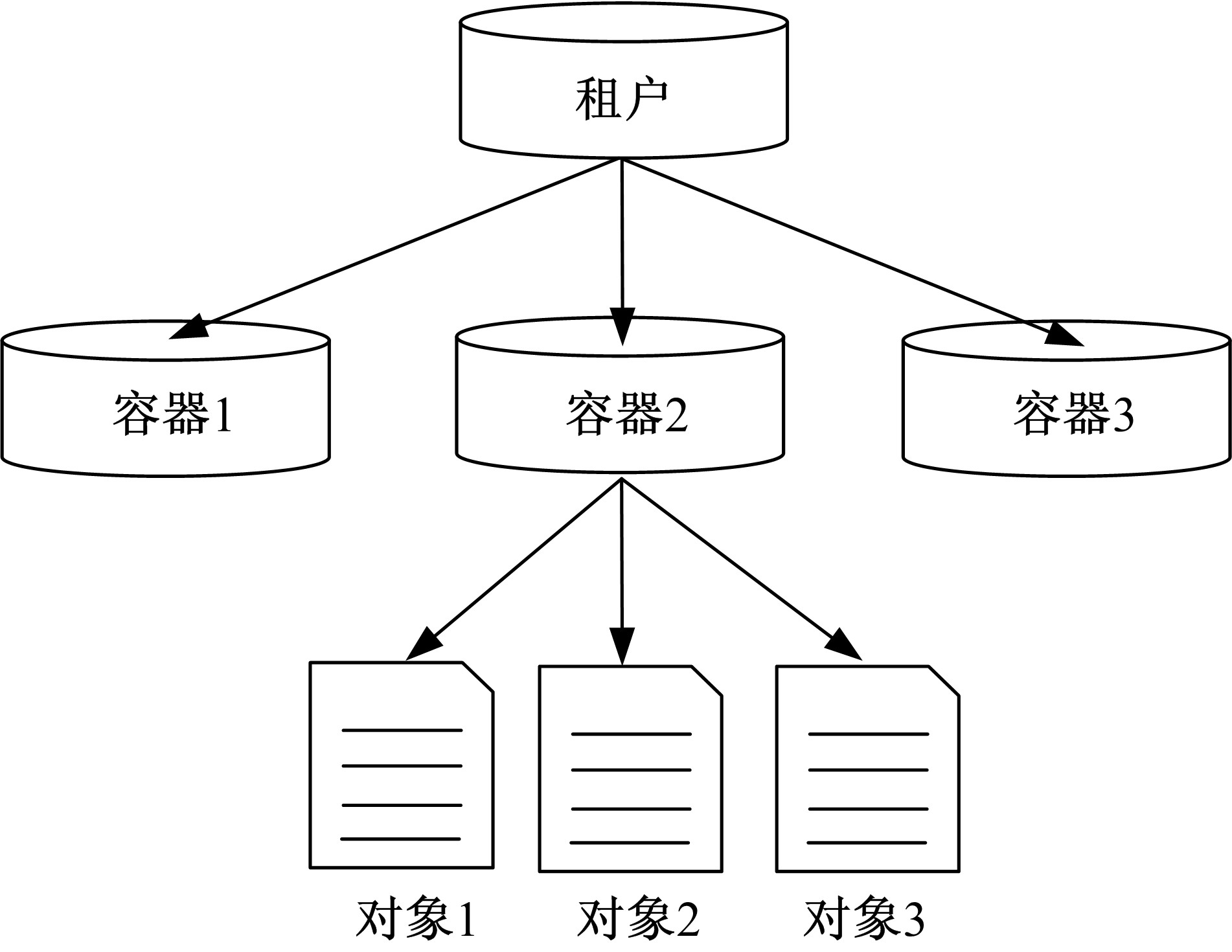
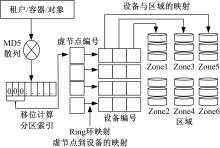
Journal of Jilin University(Engineering and Technology Edition) ›› 2021, Vol. 51 ›› Issue (1): 314-322.doi: 10.13229/j.cnki.jdxbgxb20200657
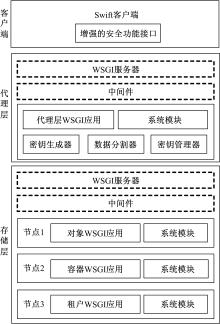
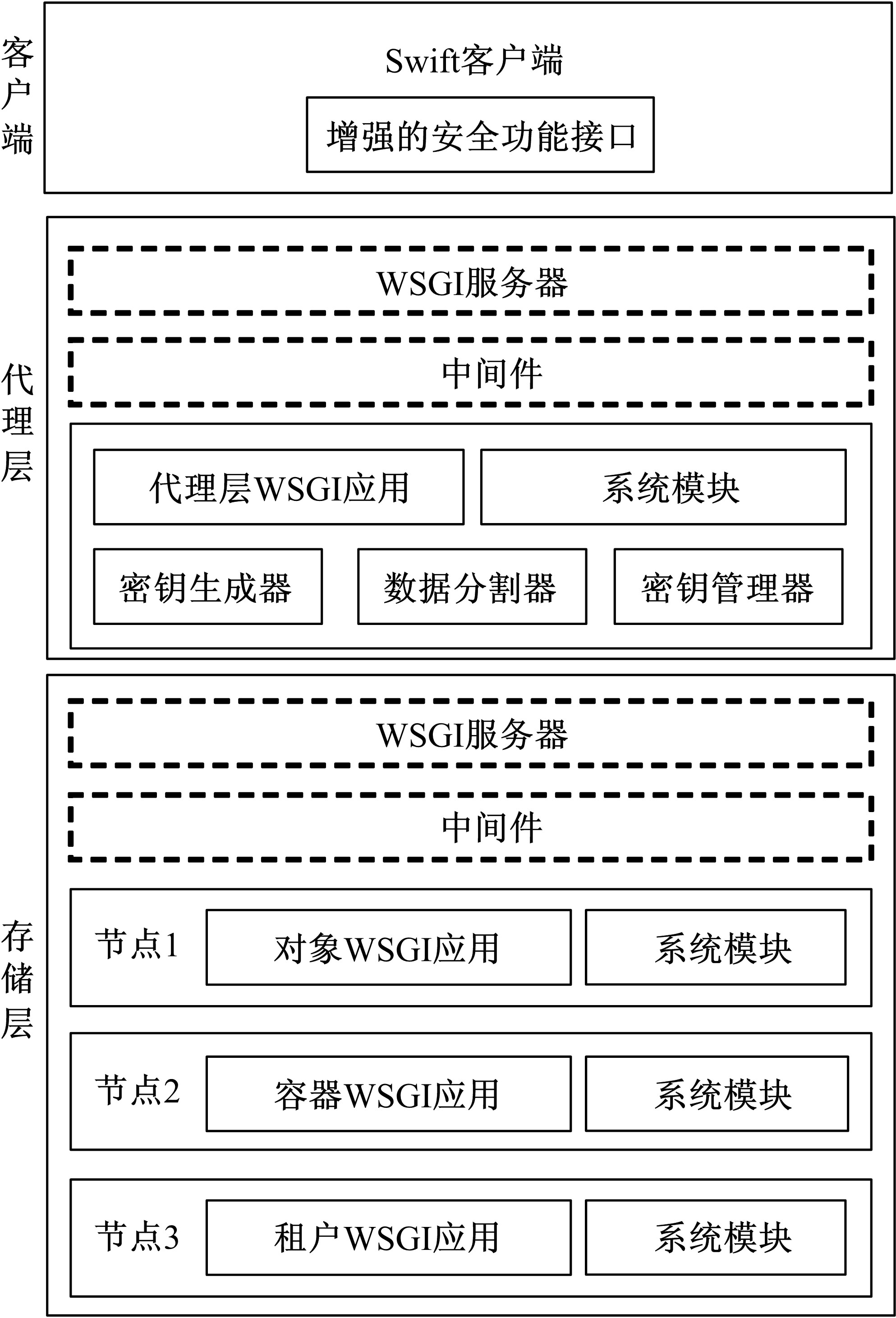
Method to enhance security function of OpenStack Swift cloud storage system
Yuan SONG1,2( ),Dan-yuan ZHOU1,2,Wen-chang SHI1,2(
),Dan-yuan ZHOU1,2,Wen-chang SHI1,2( )
)
- 1.School of Information,Renmin University of China,Beijing 100872,China
2.Key Laboratory of Data Engineering and Knowledge Engineering (Renmin University of China) of Ministry of Education,Beijing 100872,China
CLC Number:
- TP309
| 1 | Li J, Zhang Y, Chen X, et al. Secure attribute-based data sharing for resource-limited users in cloud computing[J]. Computers & Security, 2018, 72: 1-12. |
| 2 | Zhang Y, Chen X, Li J, et al. Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing[J]. Information Sciences, 2017, 379: 42-61. |
| 3 | Cloud Security Alliance. Top threats to cloud computing: deep dive [EB/OL]. [2018-08-08]. |
| 4 | OpenStack. OSSA-2015-006: Unauthorized delete of versioned Swift object [EB/OL]. [2015-04-14]. |
| 5 | OpenStack. OSSA-2015-016: Information leak via Swift tempurls [EB/OL]. [2015-08-26]. |
| 6 | OpenStack. OpenStack security notes [EB/OL]. [2020-08-16]. |
| 7 | OpenStack. OpenStack security advisories [EB/OL]. [2020-08-16]. |
| 8 | Common Vulnerabilities and exposures. CVE-ID: CVE-2015-5223 [EB/OL]. [2020-08-16]. |
| 9 | Common vulnerabilities and exposures. CVE-ID: CVE-2016-9590 [EB/OL]. [2020-08-16]. |
| 10 | Shah S Y, Paulovicks B, Zerfos P. Data-at-rest security for Spark[C]∥ IEEE International Conference on Big Data, BigData, Washington DC, USA, 2016: 1464-1473. |
| 11 | Liu Z, Huang Y, Li J, et al. DivORAM: Towards a practical oblivious RAM with variable block size[J]. Information Sciences, 2018, 447: 1-11. |
| 12 | Zhang X, Chen X, Wang J, et al. Verifiable privacy-preserving single-layer perceptron training scheme in cloud computing[J]. Soft Computing, 2018, 22(23): 7719-7732. |
| 13 | Gao C, Cheng Q, He P, et al. Privacy-preserving Naive Bayes classifiers secure against the substitution-then-comparison attack[J]. Information Sciences, 2018, 444: 72-88. |
| 14 | Li P, Li T, Ye H, et al. Privacy-preserving machine learning with multiple data providers[J]. Future Generation Computer Systems, 2018, 87: 341-350. |
| 15 | Albelooshi B, Damiani E, Salah K, et al. Securing Cryptographic Keys in the Cloud: A Survey[J]. IEEE Cloud Computing, 2016, 3(4): 42-56. |
| 16 | AlBelooshi B, Salah K, Martin T, et al. Securing cryptographic keys in the IaaS cloud model[C]∥The 8th IEEE/ACM International Conference on Utility and Cloud Computing, Limassol, Cyprus, 2015: 397-401. |
| 17 | Zerfos P, Yeo H, Paulovicks B D, et al. SDFS: Secure distributed file system for data-at-rest security for Hadoop-as-a-service[C]∥ IEEE International Conference on Big Data, Santa Clara, USA, 2015: 1262-1271. |
| 18 | Zhou J, Duan H, Liang K, et al. Securing outsourced data in the multi-authority cloud with fine-grained access control and efficient attribute revocation[J]. The Computer Journal, 2017, 60(8): 1210-1222. |
| 19 | Shao J, Lu R, Lin X. Fine-grained data sharing in cloud computing for mobile devices[C]∥ IEEE Conference on Computer Communications, Hong Kong, 2015: 2677-2685 |
| 20 | Han S, Han K, Zhang S. A data sharing protocol to minimize security and privacy risks of cloud storage in big data era[J]. IEEE Access, 2019, 7: 60290-60298. |
| 21 | Wang T, Mei Y, Jia W, et al. Edge-based differential privacy computing for sensor-cloud systems[J]. Journal of Parallel and Distributed Computing, 2020, 136: 75-85. |
| 22 | Zheng X, Zhou Y, Ye Y, et al. A cloud data deduplication scheme based on certificateless proxy re-encryption[J]. Journal of Systems Architecture, 2020, 102: 101666. |
| 23 | Rabin M O. Efficient dispersal of information for security, load balancing, and fault tolerance[J]. Journal of the ACM (JACM), 1989, 36(2): 335-348. |
| 24 | Luo W, Shen Q N, Xia Y T, et al. Container-IMA: a privacy-preserving integrity measurement architecture for containers[C]∥ The 22nd International Symposium on Research in Attacks, Intrusions and Defenses, Beijing, China, 2019: 487-500. |
| 25 | Zhang T W, Lee R B. CloudMonatt: an architecture for security health monitoring and attestation of virtual machines in cloud computing [C]∥ Proceedings of the 42nd Annual International Symposium on Computer Architecture, Portland, USA, 2015: 362-374. |
| 26 | Shamir A. How to share a secret [J]. Communications of the ACM, 1979, 22(11): 612-613. |
| 27 | Wang W, Li Z, Owens R, et al. Secure and efficient access to outsourced data[C]∥ Proceedings of the first ACM Cloud Computing Security Workshop, Chicago, USA, 2009: 55-66. |
| [1] | Xiang-jiu CHE,You-zheng DONG. Improved image recognition algorithm based on multi⁃scale information fusion [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1747-1754. |
| [2] | Shun-fu JIN,Xiu-chen QIE,Hai-xing WU,Zhan-qiang HUO. Clustered virtual machine allocation strategy in cloud computing based on new type of sleep-mode and performance optimization [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 237-246. |
| [3] | ZHAO Wei, QU Hui-yan. Fast collision detection algorithm based on Cloud Map-Reduce model [J]. 吉林大学学报(工学版), 2016, 46(2): 578-584. |
| [4] | HU Guan-yu, QIAO Pei-li. High dimensional differential evolutionary algorithm based on cloud population for network security prediction [J]. 吉林大学学报(工学版), 2016, 46(2): 568-577. |
| [5] | HAN Jia-wei, LIU Yan-heng, SUN Xin, SONG Li-jun. Quantum key management algorithm based on sliding window [J]. 吉林大学学报(工学版), 2016, 46(2): 535-541. |
| [6] | LI Qi, MA Jian-feng, XIONG Jin-bo,ZHANG Tao,LIU Xi-meng. Attribute-based encryption based access control scheme withconstant-size ciphertext in cloud computing [J]. 吉林大学学报(工学版), 2014, 44(3): 788-794. |
| [7] | LIU Guo-qi, LIU Hui, GAO Yu, LIU Ying, ZHU Zhi-liang. Resource dynamic pricing strategy based on utility in cloud computing [J]. 吉林大学学报(工学版), 2013, 43(06): 1631-1637. |
| [8] | TONG Jin, WANG Ya-hui, FAN Xue-mei, ZHANG Shu-jun, CHEN Dong-hui. Monitoring system of cold chain logistics for farm fresh produce [J]. 吉林大学学报(工学版), 2013, 43(06): 1707-1711. |
| [9] | YANG Qing-fang, MEI Duo, HAN Zhen-bo, ZHANG Biao. Ant colony optimization for the shortest path of urban road network based on cloud computing [J]. 吉林大学学报(工学版), 2013, 43(05): 1210-1214. |
| [10] | MENG Chao, SUN Zhi-xin, LIU San-min. Multiple execution paths for virus based on cloud computing [J]. 吉林大学学报(工学版), 2013, 43(03): 718-726. |
| [11] | CHEN Long, LI Jun-zhong. Verifiable method for remote data integrity supporting different granular operation [J]. 吉林大学学报(工学版), 2012, 42(增刊1): 295-299. |
| [12] | NIE Xiong-ding, HAN De-zhi, BI Kun. Cloud computing data security [J]. 吉林大学学报(工学版), 2012, 42(增刊1): 332-336. |
| [13] | GUO Ping, DAN Guang-xiang. Mixed encryption algorithm in cloud computing [J]. 吉林大学学报(工学版), 2012, 42(增刊1): 327-331. |
| [14] | HU Liang,CHU Jian-feng,LIN Yu,WANG Shou-dao,JIN Zhe . IBE system based on trust service [J]. 吉林大学学报(工学版), 2009, 39(03): 737-0742. |
| [15] | Wang Wei,Ma Jian-feng,Yang Shi-ping,Zhao Wen-hong . Secure and efficient group key management scheme in dynamic peer groups [J]. 吉林大学学报(工学版), 2008, 38(01): 131-136. |
|
||