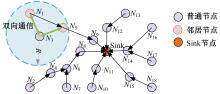
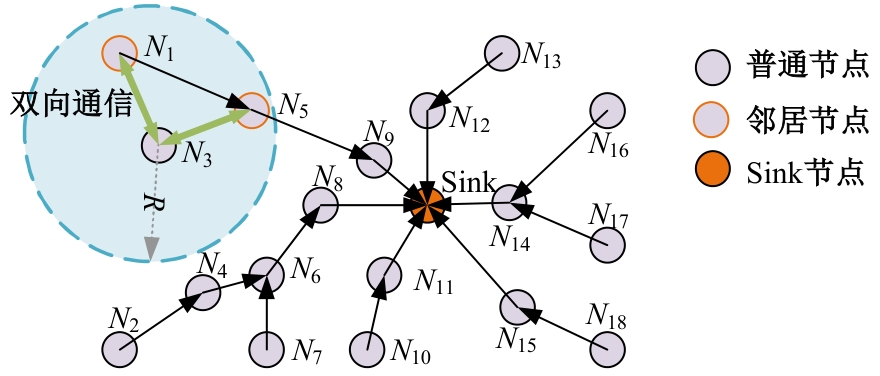
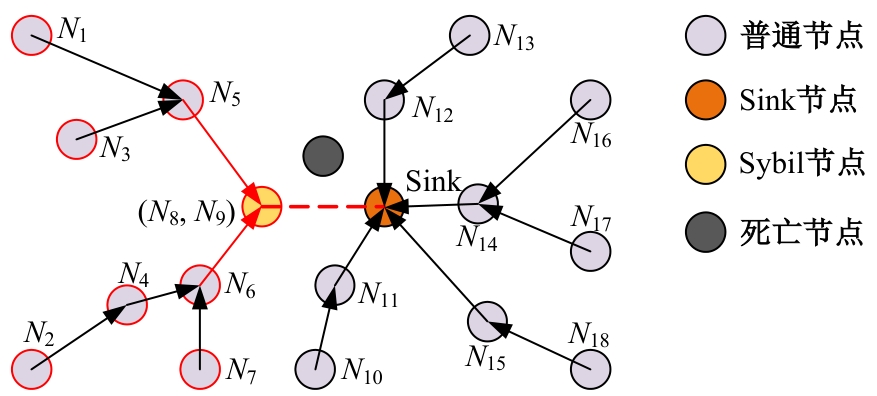
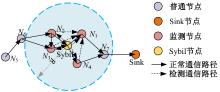
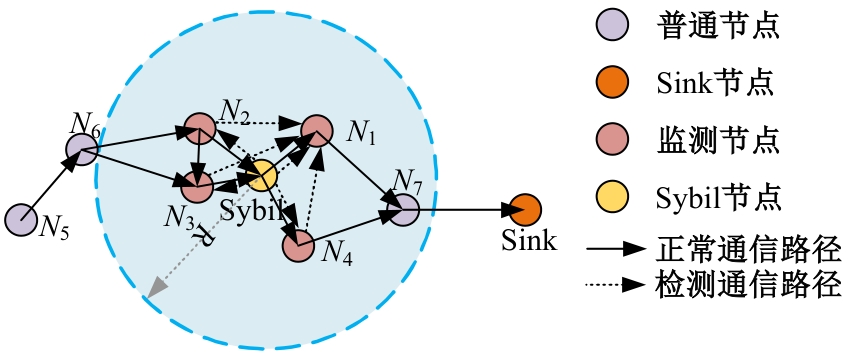
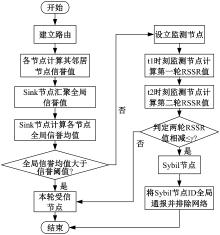
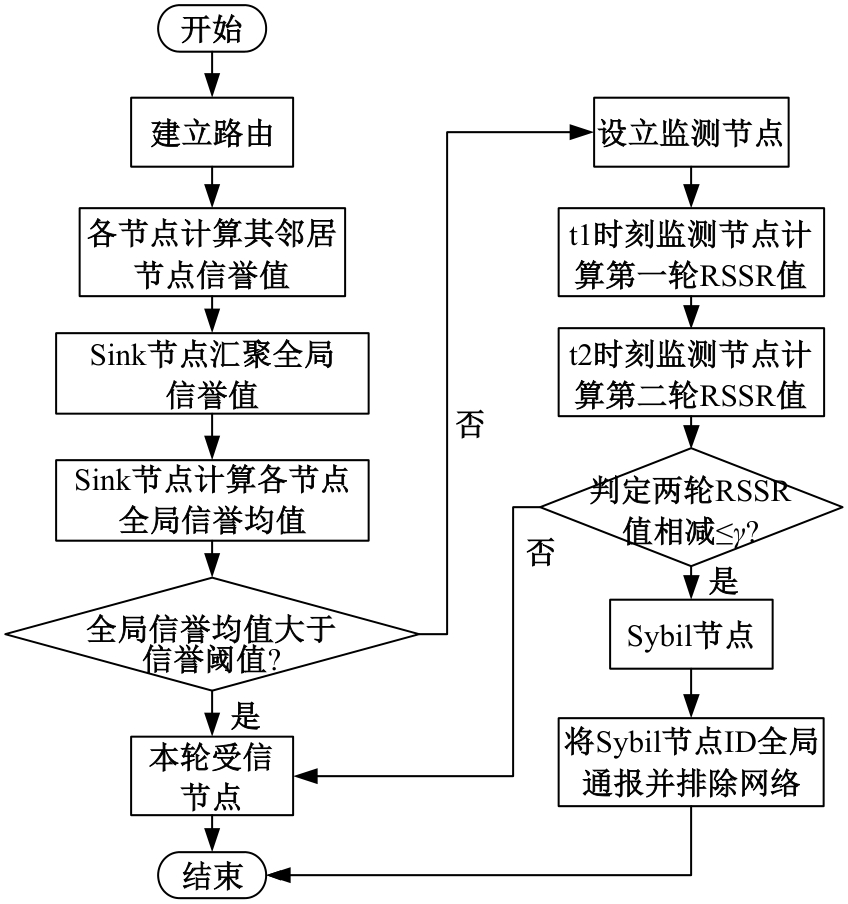
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (7): 2455-2463.doi: 10.13229/j.cnki.jdxbgxb.20230919
WSNs sybil attack detection strategy integrating interactive reputation and RSSR
Zhi-jun TENG1,2( ),Li-bo YU2,Ming-zhe LI2,Run-sheng MIAO2,Ji-hong WANG1,2
),Li-bo YU2,Ming-zhe LI2,Run-sheng MIAO2,Ji-hong WANG1,2
- 1.Key Laboratory of Modern Power System Simulation and Control & Renewable Energy Technology,Ministry of Education,Northeast Electric Power University,Jilin 132012,China
2.School of Electrical Engineering,Northeast Electric Power University,Jilin 132012,China
CLC Number:
- TN92
| [1] | 金明, 丁蓉. 一种联合时域和空域残差的网络异常检测与节点定位方法[J]. 电子学报, 2023, 51(5): 1172-1178. |
| Jin Ming, Ding Rong. Detection and localization of outlier nodes in wireless sensor networks via Temporal and Spatial Residuals[J]. Acta Electronica Sinica, 2023, 51(5): 1172-1178. | |
| [2] | 王建元, 李南南. 基于一致性算法的直流微电网分布式储能系统能量控制策略[J]. 东北电力大学学报,2023, 43(2): 73-81. |
| Wang Jian-yuan, Li Nan-nan. Energy control strategy of DC miciogrid distributed energu storage system based on consensus algorithm[J]. Journal of Northeast Electric Power University, 2023, 43(2): 73-81. | |
| [3] | Wang H, Liu W, Xiong N N, et al. LIAA: a listen interval adaptive adjustment scheme for green communication in event-sparse IoT systems[J]. Information Sciences, 2022, 584: 235-268. |
| [4] | Amol V, Manu S. On the vulnerability of the mobile ad hoc network to transmission power controlled Sybil attack: adopting the mobility-based clustering[J]. Journal of King Saud University - Computer and Information Sciences, 2022, 34(9): 7025-7044. |
| [5] | 滕志军, 杜春秋, 孙汇阳, 等. 融合节点信誉度和路径跳数的WSNs虫洞攻击检测策略[J]. 哈尔滨工业大学学报, 2021, 53(8): 67-71, 131. |
| Teng Zhi-jun, Du Chun-qiu, Sun Hui-yang, et al. A wormhole attack detection strategy integrating node creditworthiness and path hops in WSNs[J]. Journal of Harbin Institute of Technology, 2021, 53(8): 67-71, 131. | |
| [6] | 国强, 崔玉强, 王勇. 无线传感器网络中基于动态簇的节点调度算法[J]. 吉林大学学报: 工学版, 2022, 52(6): 1466-1476. |
| Guo Qiang, Cui Yu-qiang, Wang Yong. Nodes scheduling algorithm based on dynamic cluster in wireless sensor network[J]. Journal of Jilin University (Engineering and Technology Edition), 2022, 52(6): 1466-1476. | |
| [7] | 邵春雨, 窦会光, 张海东, 等. 递归式变分模态分解在电力变压器声音信号降噪中的应用[J]. 东北电力大学学报, 2022, 42(5): 90-96. |
| Shao Chun-yu, Dou Hui-guang, Zhang Hai-dong, et al. Recursive variational modal decomposition for noise reduction of power transformer sound signals[J]. Journal of Northeast Electric Power University, 2022, 42(5): 90-96. | |
| [8] | Khan T, Singh K, Abdel-Basset M, et al. A novel and comprehensive trust estimation clustering based approach for large scale wireless sensor networks[J]. IEEE Access, 2019, 7: 58221-58240. |
| [9] | Anwar R W, Zainal A, Outay F, et al.BTEM: belief based trust evaluation mechanism for wireless sensor networks[J]. Future Generation Computer Systems, 2019, 96: 605-616. |
| [10] | Feng R, Han X, Liu Q, et al. A credible Bayesian-based trust management scheme for wireless sensor networks[J]. International Journal of Distributed Sensor Networks, 2015, 11(11): No.678926. |
| [11] | 叶正旺, 温涛, 刘振宁, 等. 基于信誉模型的WSNs安全数据融合算法[J]. 东北大学学报: 自然科学版, 2019, 40(6): 789-794. |
| Ye Zheng-wang, Wen Tao, Liu Zhen-ning, et al. An algorithm of trust-based secure data aggregation for wireless sensor networks[J]. Journal of Northeastern University (Natural Science), 2019, 40(6): 789-794. | |
| [12] | Urooj S, Lata S, Ahmad S, et al. Cryptographic data security for reliable wireless sensor network[J]. Alexandria Engineering Journal, 2023, 72: 37-50. |
| [13] | Dong S, Zhang X, Zhou W. A security localization algorithm based on DV-hop against Sybil attack in wireless sensor networks[J]. Journal of Electrical Engineering & Technology, 2020, 15: 919-926. |
| [14] | Jamshidi M, Zangeneh E, Esnaashari M, et al. A novel model of sybil attack in cluster-based wireless sensor networks and propose a distributed algorithm to defend it[J]. Wireless Personal Communications, 2019, 105: 145-173. |
| [15] | 邢小东. 基于动态WSN的抗合谋Sybil攻击检测方法[J]. 计算机仿真, 2021, 38(1): 416-420. |
| Xing Xiao-dong. Anti collusion sybil attack detection method based on dynamin wireless sensor network[J]. Computer Simulation, 2021, 38(1): 416-420. | |
| [16] | Hussain K, Xia Y, Onaizah A N, et al. Hybrid of WOA-ABC and proposed CNN for intrusion detection system in wireless sensor networks[J]. Optik, 2022, 271: 170145. |
| [17] | 李翠然, 王雪洁, 谢健骊, 等. 基于改进PSO的铁路监测线性无线传感器网络路由算法[J]. 通信学报, 2022, 43(5):155-165. |
| Li Cui-ran, Wang Xue-jie, Xie Jian-li, et al. Routing algorithm for railway monitoring linear WSN based on improved PSO[J]. Journal on Communications, 2022, 43(5): 155-165. |
| [1] | Jian-po LI,Kun LIU,Wei-hua ZHU. Link quality optimization based data transmission algorithm for wireless sensor network [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(9): 2668-2675. |
| [2] | Chao-lu TEMUR,Ya-ping ZHANG. Link anomaly detection algorithm for wireless sensor networks based on convolutional neural networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(8): 2295-2300. |
| [3] | Xiao-ying Wang,Xiao-hai Chen. Random backoff algorithm for multi link transmission in embedded wireless sensor networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(7): 2057-2062. |
| [4] | Jin DUAN,An-ni YAO,Zhen WANG,Lin-tao YU. Improved sparrow search algorithm optimizes coverage in wireless sensor networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(3): 761-770. |
| [5] | Zhong-xing DUAN,Rui-xing LIU,Chong LIU. 3DDV⁃Hop node localization optimized based on multi⁃strategy improved sparrow search algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(3): 771-784. |
| [6] | Nan ZHANG,Jian-hua SHI,Ji YI,Ping WANG. Real⁃time tracking method of underground moving target based on weighted centroid positioning [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(5): 1458-1464. |
| [7] | Dong-yuan GE,Wen-jiang XIANG,Jian LI,En-chen LIU,Xi-fan YAO. Automatic positioning method of electric vehicle charging based on machine vision [J]. Journal of Jilin University(Engineering and Technology Edition), 2023, 53(12): 3465-3471. |
| [8] | Jun WANG,Yan-hui XU,Li LI. Data fusion privacy protection method with low energy consumption and integrity verification [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(7): 1657-1665. |
| [9] | Qiang GUO,Yu-qiang CUI,Yong WANG. Nodes scheduling algorithm based on dynamic cluster in wireless sensor network [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(6): 1466-1476. |
| [10] | Bin-bin YU,Liang HU,Ling CHI. Digital signature scheme against internal and external attack for wireless sensor networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(5): 1676-1681. |
| [11] | LIU Zhou-zhou, PENG Han. Topology control algorithm based on node reliability in WSN [J]. 吉林大学学报(工学版), 2018, 48(2): 571-577. |
| [12] | TANG Kun, SHI Rong-hua. Detection of wireless sensor network failure area based on butterfly effect signal [J]. 吉林大学学报(工学版), 2017, 47(6): 1939-1948. |
| [13] | YU Bin-bin, WU Xin-yu, CHU Jian-feng, HU Liang. Signature protocol for wireless sensor network based on group key agreement [J]. 吉林大学学报(工学版), 2017, 47(3): 924-929. |
| [14] | DONG Ying, ZHOU Zhan-ying, SU Zhen-zhen, XU Yang, QIAN Zhi-hong. Cross-layer MAC protocol based on routing information for WSN [J]. 吉林大学学报(工学版), 2017, 47(2): 647-654. |
| [15] | ZHU Hai-yang, ZHANG He, MA Shao-jie. Parameter optimization of enhanced ultrasonic circumferential scanning node in WSN [J]. 吉林大学学报(工学版), 2017, 47(1): 262-267. |
|
||