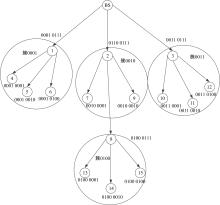
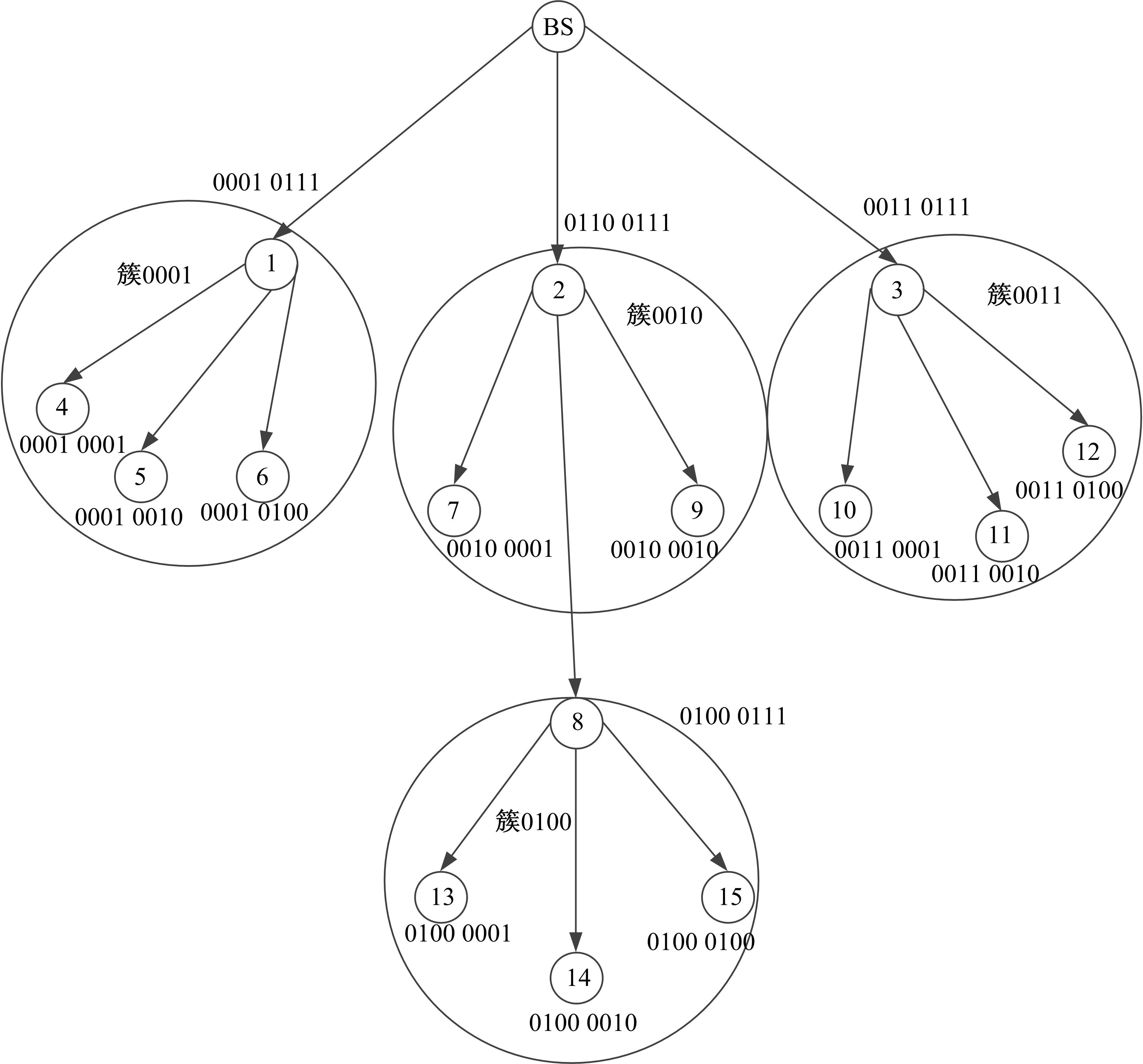
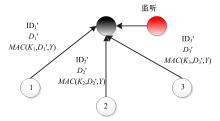
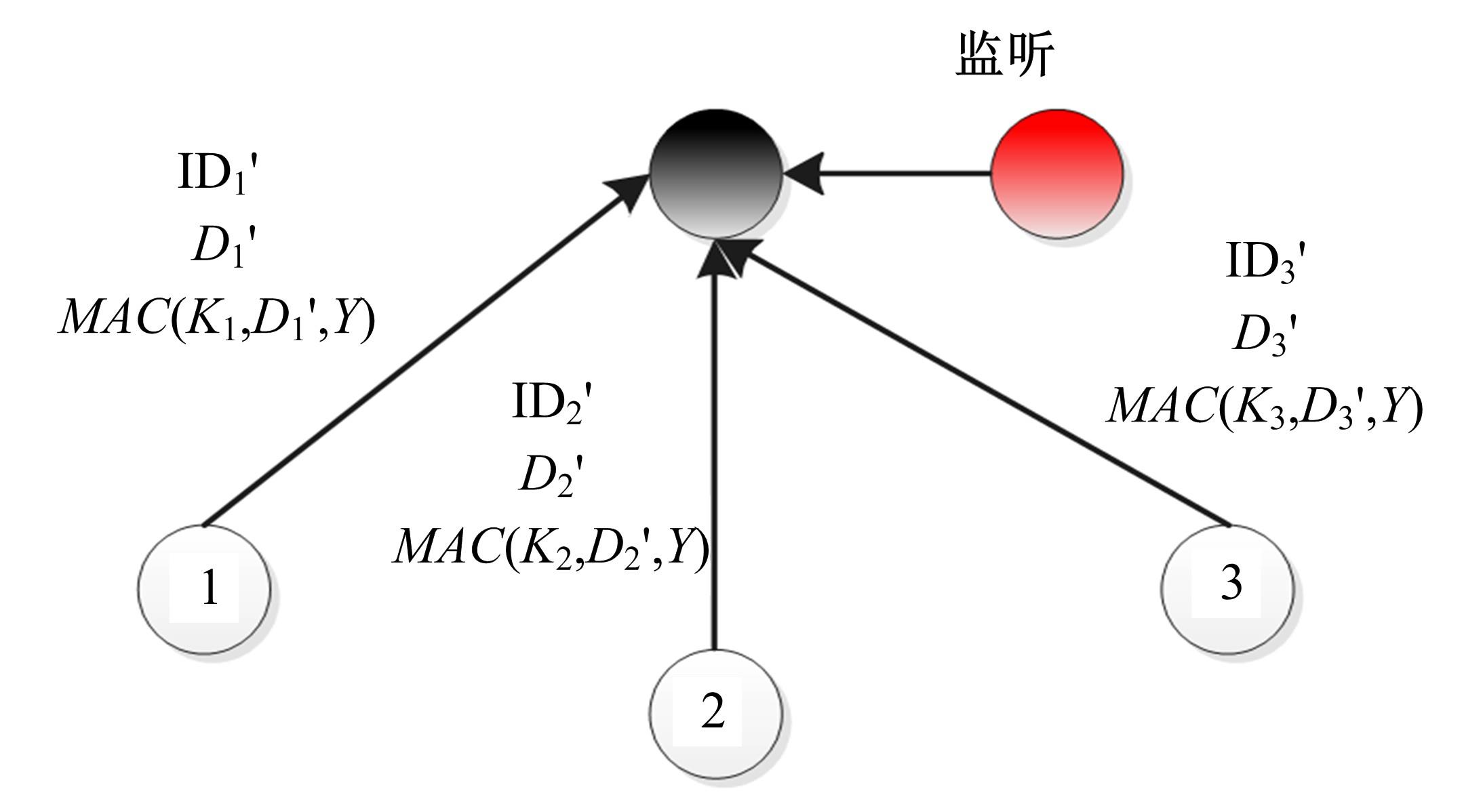
Journal of Jilin University(Engineering and Technology Edition) ›› 2022, Vol. 52 ›› Issue (7): 1657-1665.doi: 10.13229/j.cnki.jdxbgxb20210112
Data fusion privacy protection method with low energy consumption and integrity verification
Jun WANG1,2( ),Yan-hui XU1,2,Li LI1,2(
),Yan-hui XU1,2,Li LI1,2( )
)
- 1.College of Computer Science and Technology,Shenyang University of Chemical Technology,Shenyang 110142,China
2.Key Laboratory of Industrial Intelligence Technology on Chemical Process,Shenyang University of Chemical Technology,Shenyang 110142,China
CLC Number:
- TP393
| 1 | 于斌斌,武欣雨,初剑峰,等.基于群密钥协商的无线传感器网络签名协议[J]. 吉林大学学报:工学版, 2017,47(3):924-929. |
| Yu Bin-bin, Wu Xin-yu, Chu Jian-feng, et al. Wireless sensor network signature protocol based on group key agreement[J]. Journal of Jilin University (Engineering and Technology Edition), 2017, 47(3):924-929. | |
| 2 | 范时平,何超杰. 基于NARX神经网络的分簇数据融合算法[J]. 计算机工程与设, 2018, 39(4): 938-942. |
| Fan Shi-ping, He Chao-jie. Clustering data fusion algorithm based on NARX neural network [J]. Computer Engineering and Design, 2018, 39(4): 938-942. | |
| 3 | 许建,杨庚,陈正宇,等. WSN数据融合中的隐私保护技术研究[J]. 计算机工程, 2012, 38(15): 134-138. |
| Xu Jian, Yang Geng, Chen Zheng-yu, et al. Research on privacy protection technology in WSN data fusion[J]. Computer Engineering, 2012, 38(15): 134-138. | |
| 4 | Gao F, Zhu W. A dual-head cluster based secure aggregation scheme for sensor networks[C]∥Proceedings of the International Conference on Network and Parallel Computing, Shanghai, China, 2008: 103-110. |
| 5 | 杨文文,马春光,黄予洛. 基于分布式认证的完整性保护数据融合方法[J].计算机应用, 2014, 34(3): 714-719, 732. |
| Yang Wen-wen, Ma Chun-guang, Huang Yu-luo. Integrity protection data fusion scheme based on distributed authentication[J]. Computer Applications, 2014, 34(3): 714-719, 732. | |
| 6 | He Wen-bo, Nguyen Hoang, Liu Xue, et al. PDA:privacy- preserving data aggregation in wireless sensor networks[C]∥Proceedings of 26th IEEE International Conference on Computer Communications(INFOCOMM), Anchorage, USA, 2007: 2045-2053. |
| 7 | He Wen-bo, Nguyen Hoang, Liu Xue, et al. iPDA:an integrity-protecting private data aggregation scheme for wireless sensor networks[C]∥Proceedings of IEEE Military Communications Conference, San Diego, USA, 2008: 1-7. |
| 8 | 丁晓娇. 可保护数据隐私性和完整性的安全数据融合算法研究[D]. 开封: 河南大学计算机科学与技术学院, 2015. |
| Ding Xiao-jiao. Research on secure data fusion algorithm that protects data privacy and integrity[D]. Kaifeng: School of Computer Science and Technology, Henan University, 2015. | |
| 9 | 贾宗璞,王冠琼,彭维平,等.基于复数域的高效完整性保护数据融合算法[J]. 计算机应用与软件, 2017, 34(4): 70-74, 148. |
| Jia Zong-pu, Wang Guan-qiong, Peng Wei-ping, et al. High efficiency integrity protection data fusion algorithm based on complex domain[J]. Computer Applications and Software, 2017, 34(4): 70-74, 148. | |
| 10 | 李敏. 无线传感器网络数据融合完整性认证机制[D].大连:大连理工大学计算机科学与技术学院,2013. |
| Li Min. Authentication mechanism of data fusion integrity in wireless sensor networks[D]. Dalian: School of Computer Science and Technology, Dalian University of Technology, 2013. | |
| 11 | 梁学利. 无线传感器网络中数据融合隐私保护方法研究[D]. 杭州: 浙江工业大学计算机科学与技术学院, 2015. |
| Liang Xue-li. Research on privacy protection method of data fusion in wireless sensor networks[D]. Hangzhou: College of Computer Science and Technology, Zhejiang University of Technology, 2015. | |
| 12 | 鄂旭,杨明婧,励建荣,等. 能量均衡的数据融合隐私保护算法研究[J].计算机工程, 2016, 42(4): 126-130. |
| Xu E, Yang Ming-jing, Li Jian-rong, et al. Research on data fusion privacy protection algorithm for energy balance [J]. Computer Engineering, 2016, 42(4): 126-130. | |
| 13 | 邵莉莉. 无线传感器网络中基于同态加密的安全数据融合技术研究[D]. 合肥: 安徽大学计算机科学与技术学院,2017. |
| Shao Li-li. Research on secure data fusion technology based on homomorphic encryption in wireless sensor networks[D]. Hefei: School of Computer Science and Technology, Anhui University, 2017. | |
| 14 | 李伟. 面向完整性检测的WSN数据融合隐私保护算法研究[D]. 南京: 南京邮电大学计算机科学与技术学院, 2014. |
| Li Wei. Research on privacy protection algorithm of wsn data fusion for integrity detection[D]. Nanjing: School of Computer Science and Technology, Nanjing University of Posts and Telecommunications, 2014. | |
| 15 | 赵小敏,梁学利,蒋双双,等.安全的WSN数据融合隐私保护方法设计[J]. 通信学报,2014,35(11):154-161. |
| Zhao Xiao-min, Liang Xue-li, Jiang Shuang-shuang, et al. Design of a secure PRIVACY protection scheme for WSN data fusion [J]. Communications, 2014, 35(11): 154-161. | |
| 16 | 吉佳,温巧燕,张华. 无线传感器网络中基于分簇的数据聚合机制[J]. 传感器与微系统,2015,34(1):17-20. |
| Ji jia, Wen Qiao-yan, Zhang Hua. Clustering based data aggregation mechanism in wireless sensor networks[J]. Sensors and Microsystems, 2015, 34(1): 17-20. | |
| 17 | 于斌斌,胡亮,迟令.可抵抗内外部攻击的无线传感器网络数字签名方案[J]. 吉林大学学报: 工学版, 2019, 49(5):1676-1681. |
| Yu Bin-bin, Hu Liang, Chi Ling. A digital signature scheme for wireless sensor networks resisting internal and external attacks[J]. Journal of Jilin University (Engineering and Technology Edition), 2019, 49(5): 1676-1681. |
| [1] | Feng-feng ZHOU,Yi-chi ZHANG. Unsupervised feature engineering algorithm BioSAE based on sparse autoencoder [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(7): 1645-1656. |
| [2] | Qiang GUO,Yu-qiang CUI,Yong WANG. Nodes scheduling algorithm based on dynamic cluster in wireless sensor network [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(6): 1466-1476. |
| [3] | Yao-long KANG,Li-lu FENG,Jing-an ZHANG,Fu CHEN. Outlier mining algorithm for high dimensional categorical data streams based on spectral clustering [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(6): 1422-1427. |
| [4] | Wen-jun WANG,Yin-feng YU. Automatic completion algorithm for missing links in nowledge graph considering data sparsity [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(6): 1428-1433. |
| [5] | Xue-yun CHEN,Xue-yu BEI,Qu YAO,Xin JIN. Pedestrian segmentation and detection in multi-scene based on G-UNet [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 925-933. |
| [6] | Shi-min FANG. Multiple source data selective integration algorithm based on frequent pattern tree [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 885-890. |
| [7] | Da-xiang LI,Meng-si CHEN,Ying LIU. Spontaneous micro-expression recognition based on STA-LSTM [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 897-909. |
| [8] | Ming LIU,Yu-hang YANG,Song-lin ZOU,Zhi-cheng XIAO,Yong-gang ZHANG. Application of enhanced edge detection image algorithm in multi-book recognition [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 891-896. |
| [9] | Xiao-hui WEI,Yan-wei MIAO,Xing-wang WANG. Rhombus sketch: adaptive and more accurate sketch for streaming data [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(4): 874-884. |
| [10] | Xue WANG,Zhan-shan LI,Ying-da LYU. Medical image segmentation based on multi⁃scale context⁃aware and semantic adaptor [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 640-647. |
| [11] | Ji-hong OUYANG,Ze-qi GUO,Si-guang LIU. Dual⁃branch hybrid attention decision net for diabetic retinopathy classification [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 648-656. |
| [12] | Lin MAO,Feng-zhi REN,Da-wei YANG,Ru-bo ZHANG. Two⁃way feature pyramid network for panoptic segmentation [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 657-665. |
| [13] | Xue-zhi WANG,Qing-liang LI,Wen-hui LI. Spatio⁃temporal model of soil moisture prediction integrated with transfer learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 675-683. |
| [14] | Su-ming KANG,Ye-e ZHANG. Hadoop⁃based local timing link prediction algorithm across social networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(3): 626-632. |
| [15] | You QU,Wen-hui LI. Single-stage rotated object detection network based on anchor transformation [J]. Journal of Jilin University(Engineering and Technology Edition), 2022, 52(1): 162-173. |
|
||