吉林大学学报(工学版) ›› 2024, Vol. 54 ›› Issue (10): 3000-3008.doi: 10.13229/j.cnki.jdxbgxb.20230890
• 计算机科学与技术 • 上一篇
混沌加载PE文件水印数据率改进方法
- 西安财经大学 信息学院,西安 710100
Chaos theory to PE and improving method of watermark data rate
- School of Information,Xi'an University of Finance and Economics,Xi'an 710100,China
摘要:
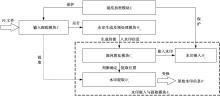
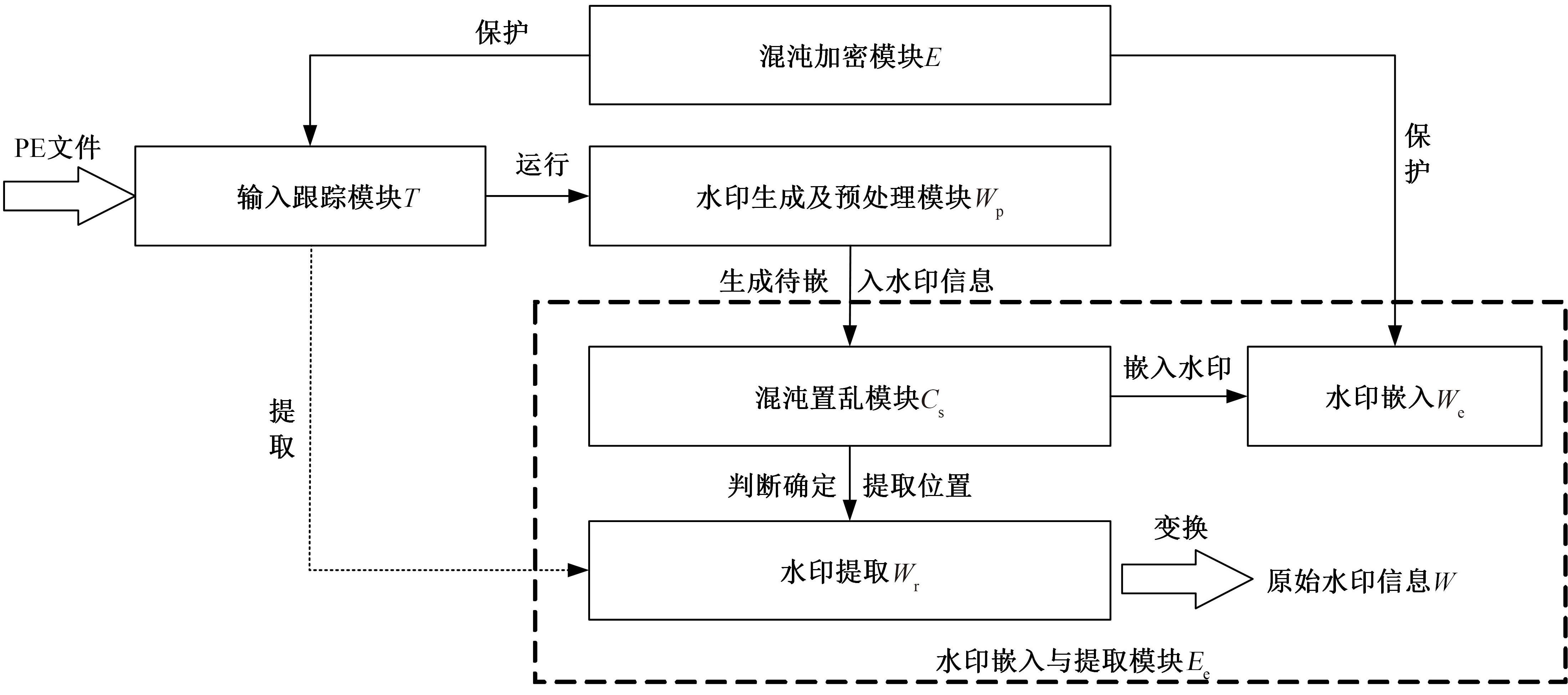
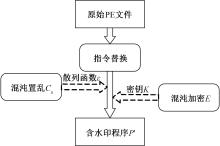
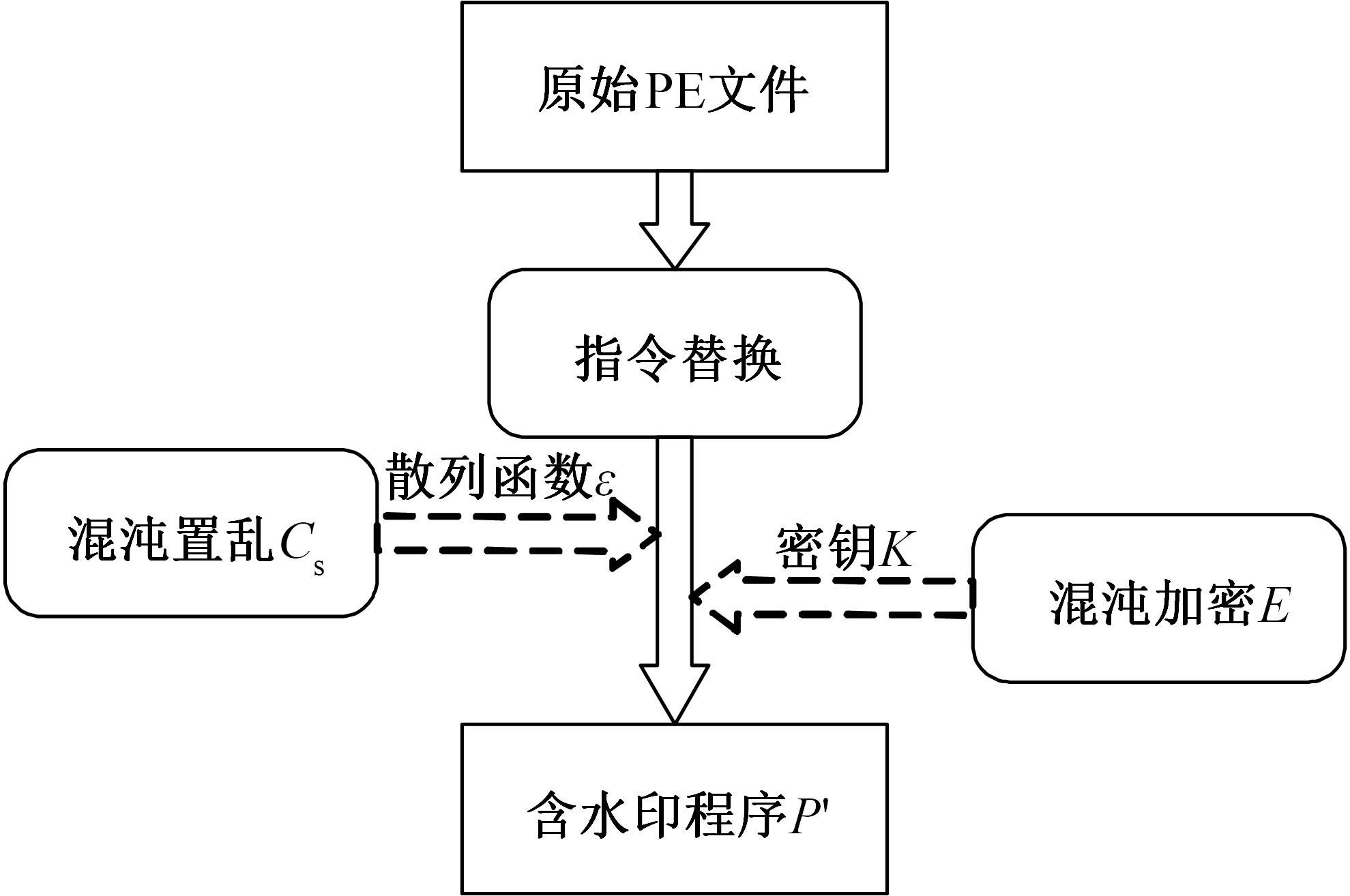
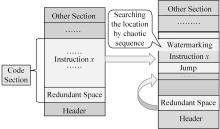
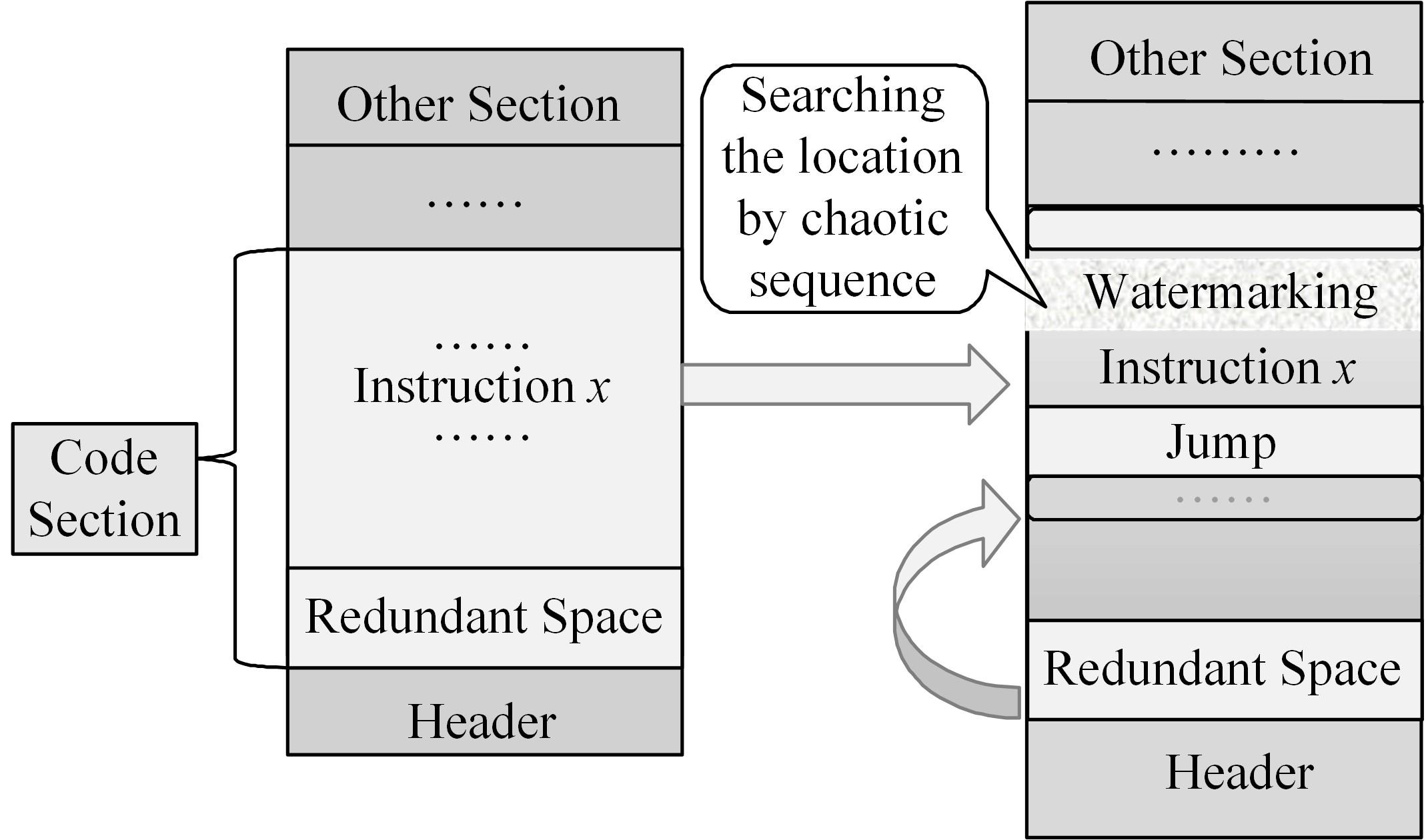
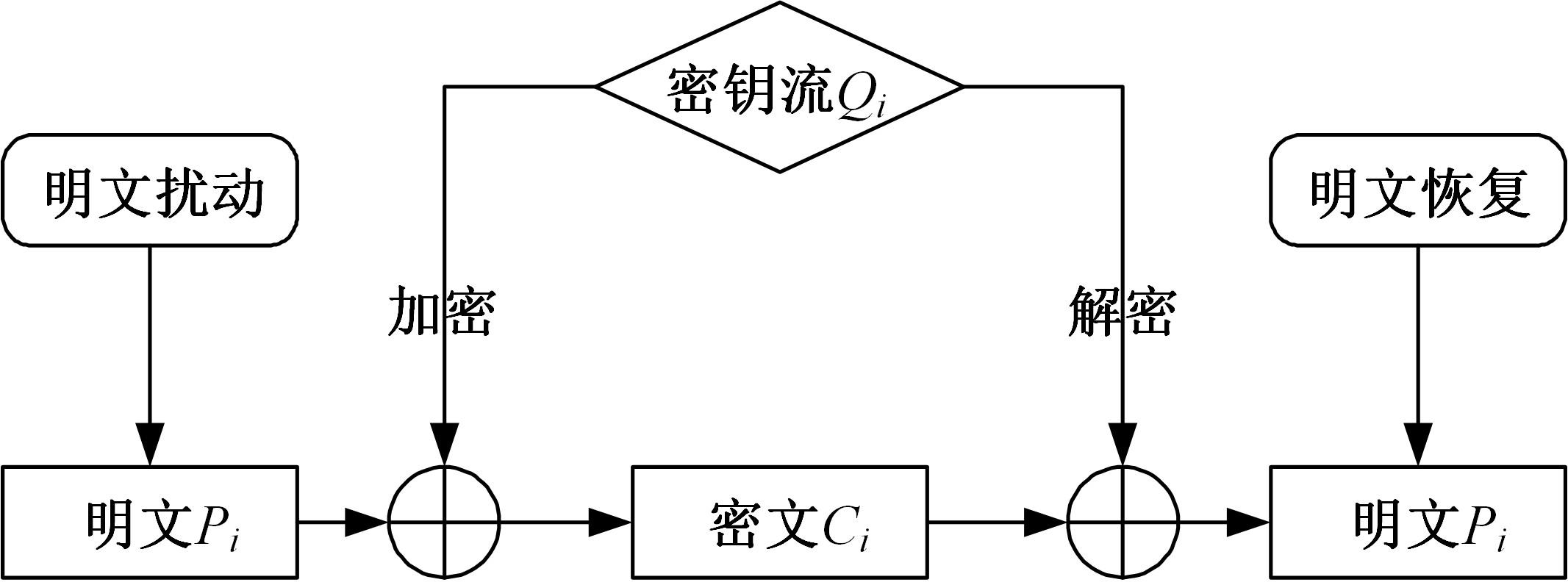
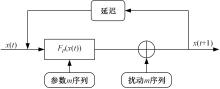
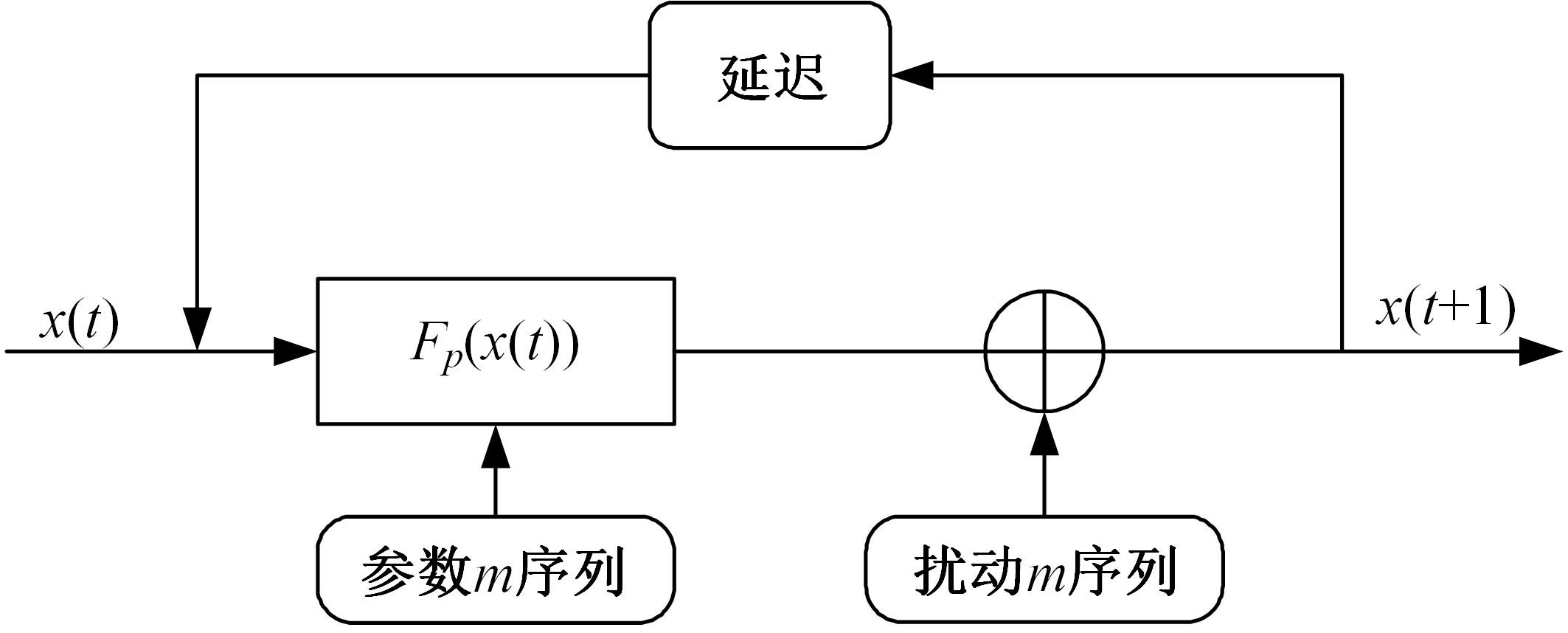
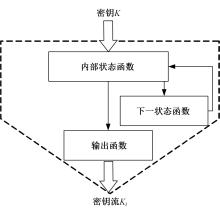
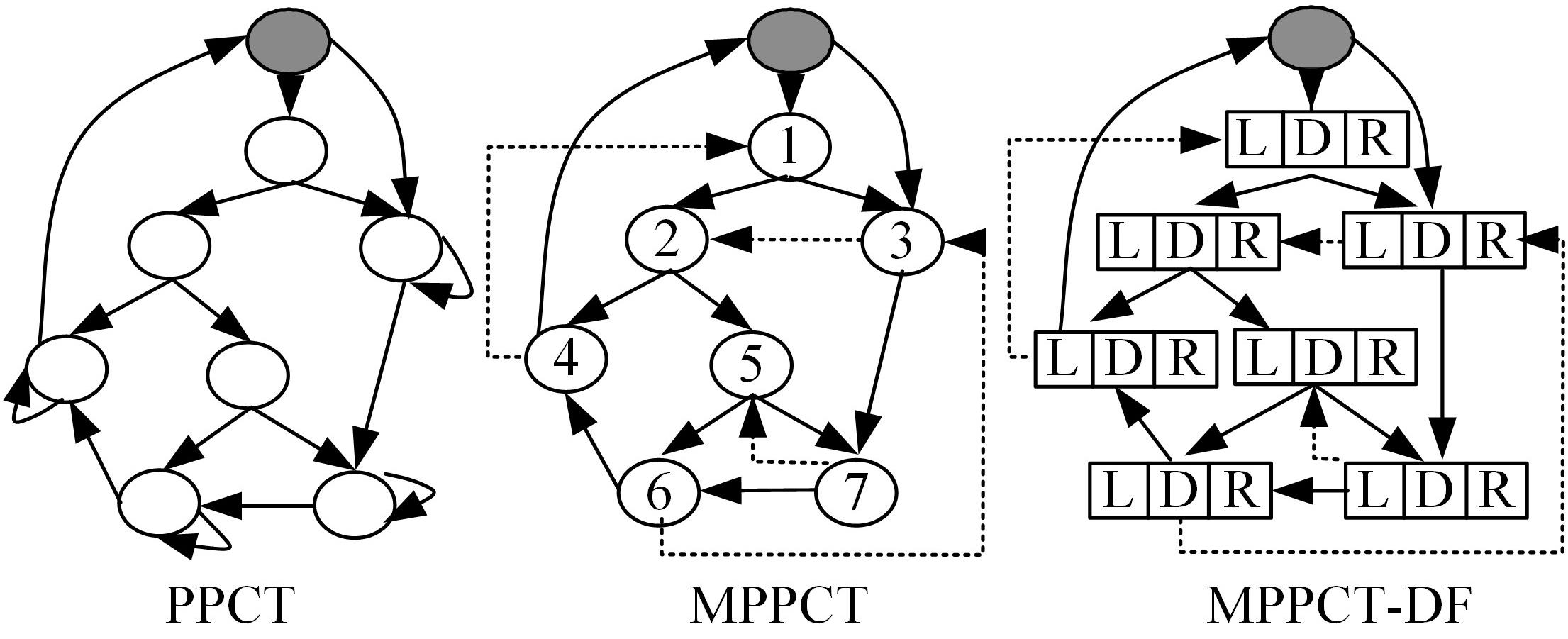
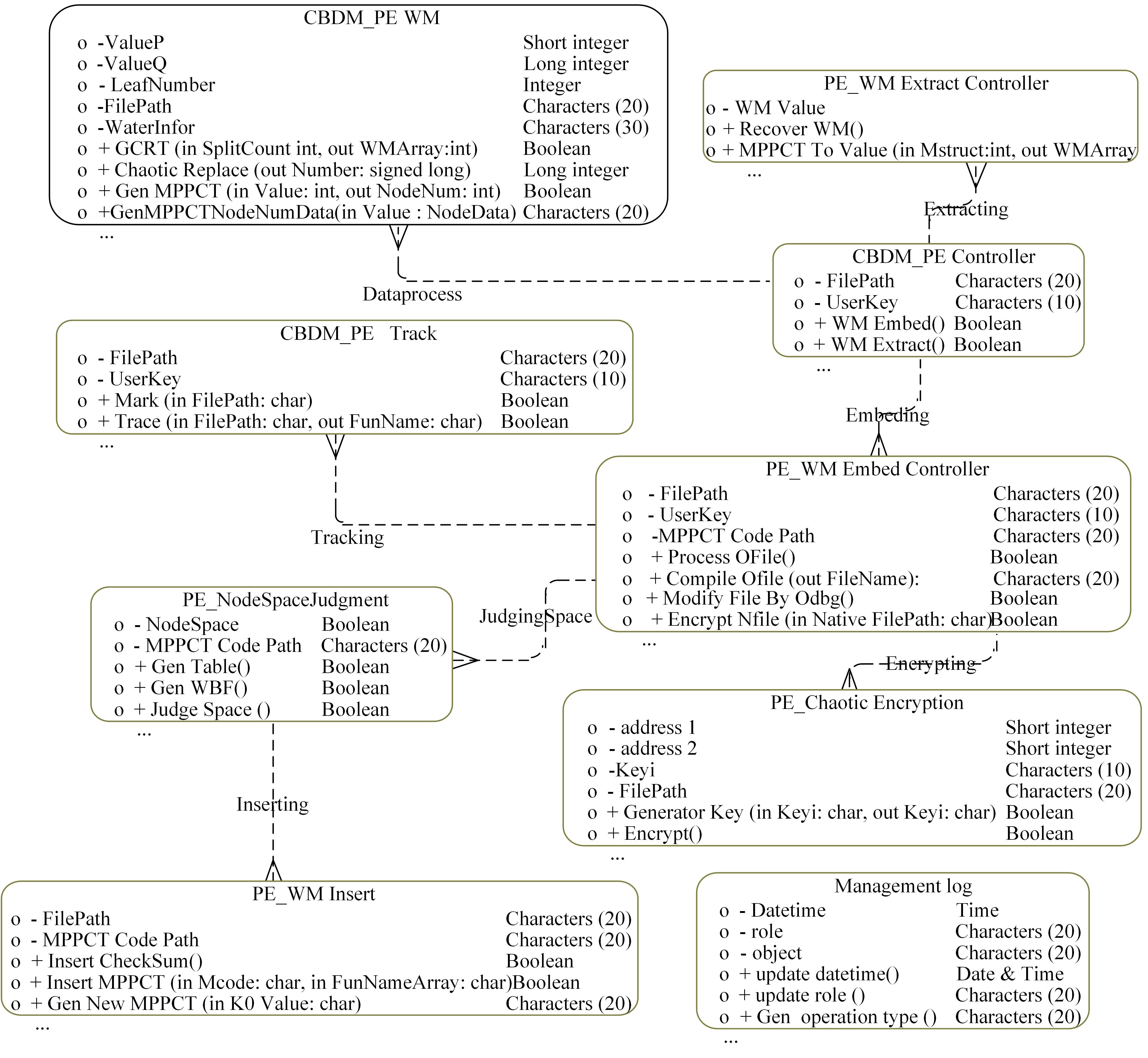
针对PE文件存在水印鲁棒性差和数据率低的不足,本文基于混沌扰动对子水印信息加密,提高了水印的鲁棒性;基于混沌散列把水印信息分散编码到整个代码段中,提高了水印的隐蔽性;应用MPPCT_DF动态图结构,增加图节点编码量,同时每个节点增加一个静态数据域,扩大了信息存储量。基于此,提出一种混沌加载PE文件的动态图水印(CBDW_PE)技术方案,并给出主要组成模块、关键算法,展示系统实现及概念数据模型,最后对算法进行对比和分析。经比较,该技术对剪切、篡改和逆向攻击等具有较好的效果,提高了水印的安全性与隐蔽性,有效改善了PE文件数据率低的问题,便于有意义水印的加载。
中图分类号:
- TP309
| 1 | Business Software Alliance(BSA). Software management: security imperative, business opportunity[R]. BSA Global Software Survey: Software Management: Security Imperative, Business Opportunity, Washington,USA, 2018. |
| 2 | 产业调研网. 2023—2029年中国软件行业研究与趋势预测报告[EB/OL]. [2023-08-20].. |
| 3 | Kadian P, Arora S M, Arora N. Robust digital watermarking techniques for copyright protection of digital data: a survey[J]. Wireless Personal Communications, 2021, 118: 3225-3249. |
| 4 | Collberg C, Nagra J. Surreptitious Software: Obfuscation, Watermarking, and Tamperproofing for Software Protection[M]. London:Pearson Education, 2009. |
| 5 | Ayan D, Skiti B, Nabenku C.Software watermarking: progress and challenges[J]. INAE Letters, 2019, 4(1): 65-75. |
| 6 | 苏庆, 林昊, 黄剑锋, 等. 基于Petri网编码的动态图水印技术研究[J]. 计算机科学, 2019, 46(7): 120-125. |
| Su Qing, Lin Hao, Huang Jian-feng, et al. Study on dynamic-graph watermarking based on petri net coding[J]. Computer Science, 2019, 46(7): 120-125. | |
| 7 | Dey A, Ghosh S, Bhattacharya S, et al. A robust software watermarking framework using shellcode[J]. Multimedia Tools and Applications, 2020, 79: 2555-2576. |
| 8 | Chen Z, Li D. A software watermarking algorithm based on instruction encoding and resource section format[C]∥Proceedings of Advances in 3D Image and Graphics Representation, Analysis, Computing and Information Technology: Methods and Algorithms, Singapore, 2020: 359-367. |
| 9 | 张颖君, 陈恺, 鲍旭华. 一种基于程序执行时间量化分析的软件水印方法[J]. 电子与信息学报, 2020, 42(8): 1811-1819. |
| Zhang Ying-jun, Chen Kai, Bao Xu-hua. A software watermarking method based on program execution time[J]. Journal of Electronics & Information Technology, 2020, 42(8): 1811-1819. | |
| 10 | Aiswarya K K, Praveen K, Amritha P P, et al. Application of secret sharing scheme in software watermarking[C]∥Information and Communication Technology for Intelligent Systems, Singapore, 2021: 345-353. |
| 11 | Goyal R, Kim S, Waters B, et al. Beyond software watermarking: traitor-tracing for pseudorandom functions[C]∥Proceedings of the 27th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 2021: 250-280. |
| 12 | 王巍, 何颖, 谭永坤, 等. 一种增强型动态图的软件水印算法[J]. 吉林大学学报:理学版, 2022, 60(5): 1161-1166. |
| Wang Wei, He Ying, Tan Yong-kun, et al. A software watermarking algorithm for enhanced dynamic graph[J]. Journal of Jilin University(Science Edition), 2022, 60(5): 1161-1166. | |
| 13 | 李凌俐, 王春东, 张清华. 一种基于自修改的动态耦合水印方法[J]. 天津理工大学学报, 2023, 39(1): 29-34. |
| Li Ling-li, Wang Chun-dong, Zhang Qing-hua. Dynamic coupled watermark method based on self-modifying code[J]. Journal of Tianjin University of Technology, 2023, 39(1): 29-34. | |
| 14 | Dridi F, El A S, El H Y W, et al. Design, hardware implementation on FPGA and performance analysis of three chaos-based stream ciphers[J]. Fractal and Fractional, 2023, 7(2): 197-203. |
| 15 | Chen B, Yu S, Li D D U, et al. Cryptanalysis of some self-synchronous chaotic stream ciphers and their improved schemes[J]. International Journal of Bifurcation and Chaos, 2021, 31(8): 215-242. |
| 16 | 芦斌, 罗向阳, 刘粉林. 一种基于混沌的软件水印算法框架及实现[J]. 软件学报, 2007(2): 351-360. |
| Lu Bin, Luo Xiang-yang, Liu Fen-lin. A chaos-based framework and implementation for software watermarking algorithm[J]. Journal of Software, 2007(2): 351-360. | |
| 17 | Ke-xin Y, Ke Y, Jian-qi Z. A robust dynamic software watermarking[C]∥International Conference on Information Technology and Computer Science. Kiev,Ukraine,2009: 15-18. |
| 18 | 陈刚. 基于PE文件的软件水印研究[D]. 长沙: 湖南大学计算机与通信学院, 2008. |
| Chen Gang. Research on software watermark based on PE file[D]. Changsha: School of Computer and Communication, Hunan University, 2008. | |
| 19 | 罗养霞, 房鼎益. 基于混沌优化的动态水印算法研究[J].中国科学技术大学学报, 2012, 42(1): 77-84. |
| Luo Yang-xia, Fang Ding-yi. Dynamic watermarking algorithm based on chaptic optimization[J]. Journal of University of Science and Technology of China, 2012, 42(1): 77-84. | |
| 20 | Barbora H, Sascha W. Confidential quantum computing[C]∥Proceedings of the 18th International Conference on Availability, Reliability and Security, New York,USA, 2023, 46: 1-10. |
| [1] | 汪波, 冯久超 . 基于H.264标准的视频混沌密写算法[J]. 吉林大学学报(工学版), 2008, 38(04): 960-965. |
| [2] | 张雪松,李昕,崔维力,赫枫龄,左万利 . 动态自我验证的软件水印防篡改技术[J]. 吉林大学学报(工学版), 2007, 37(05): 1148-1153. |
|
||