吉林大学学报(工学版) ›› 2020, Vol. 50 ›› Issue (5): 1894-1904.doi: 10.13229/j.cnki.jdxbgxb20190448
• 通信与控制工程 • 上一篇
基于统计的物联网分布式拒绝服务攻击检测
- 北京科技大学 计算机与通信工程学院,北京 100083
Statistical based distributed denial of service attack detection research in internet of things
Hong-song CHEN( ),Jing-jiu CHEN
),Jing-jiu CHEN
- School of Computer and Communication Engineering, University of Science and Technology Beijing, Beijing 100083, China
摘要:
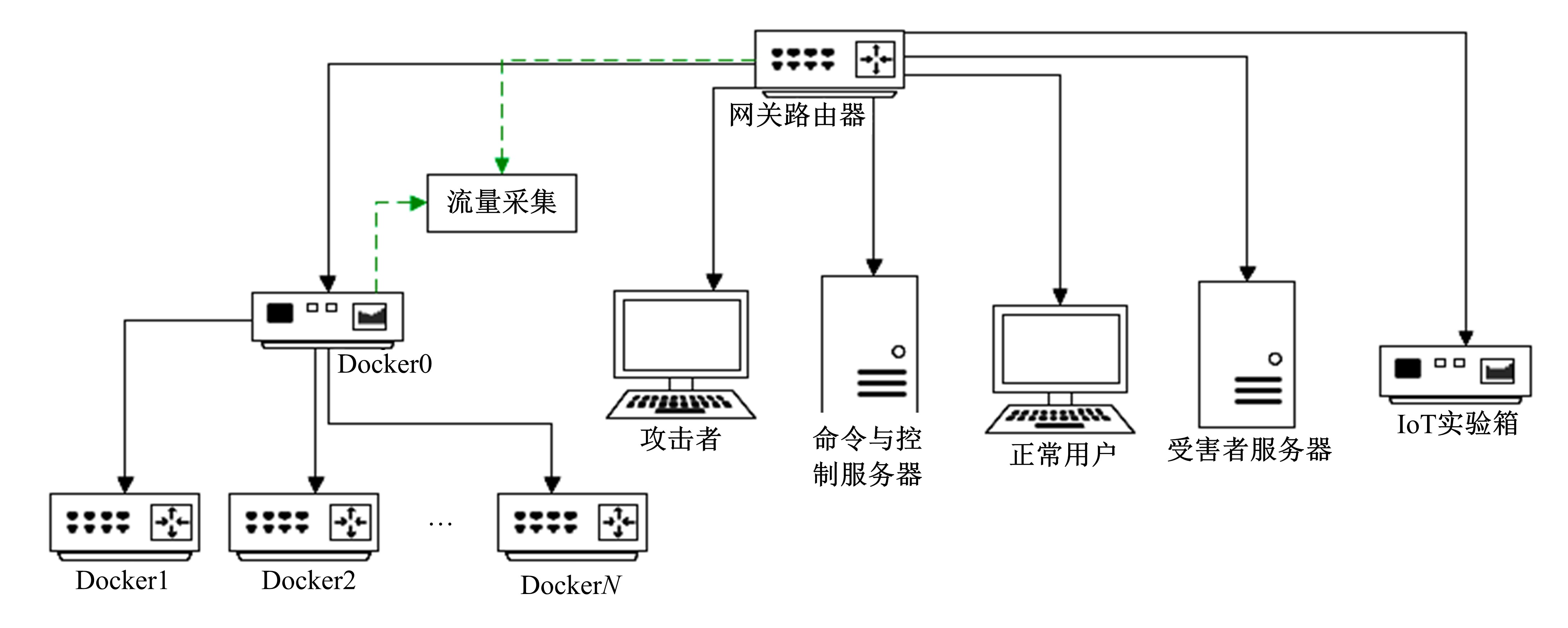
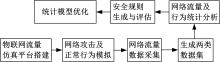
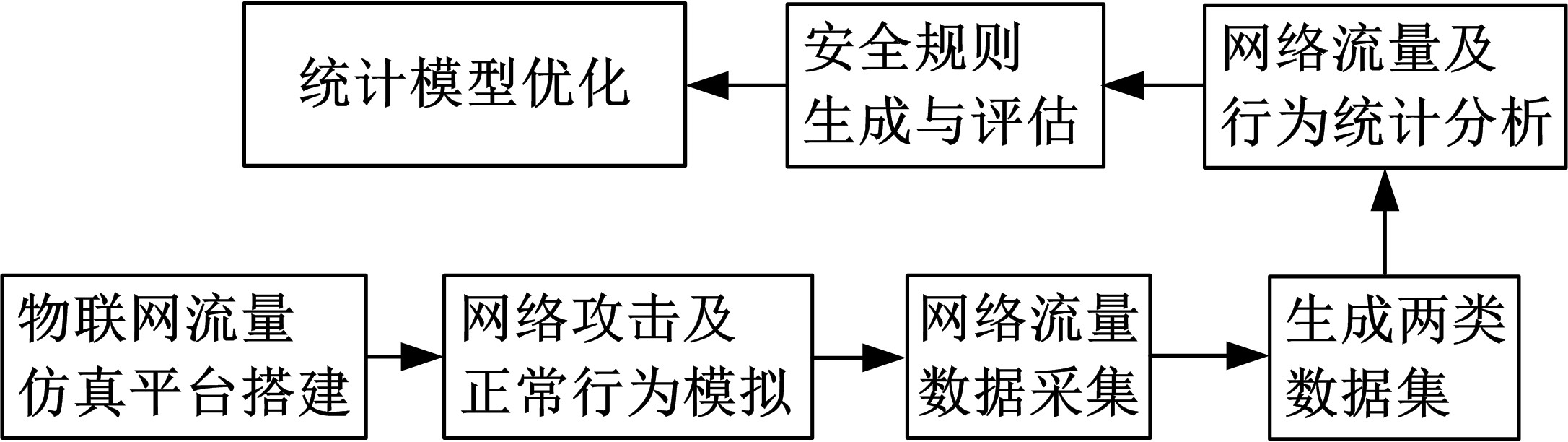
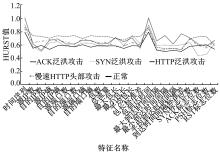
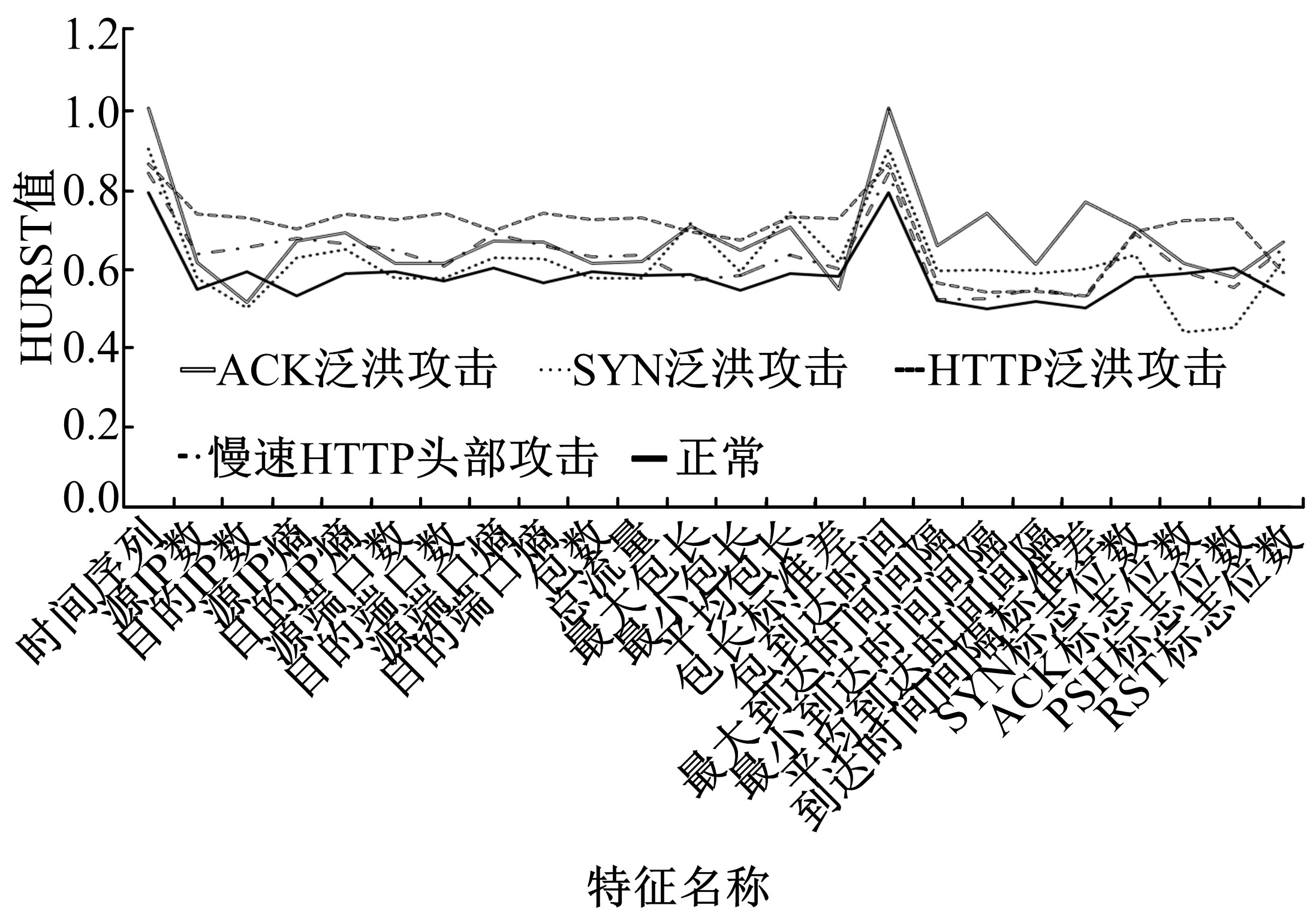
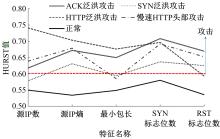
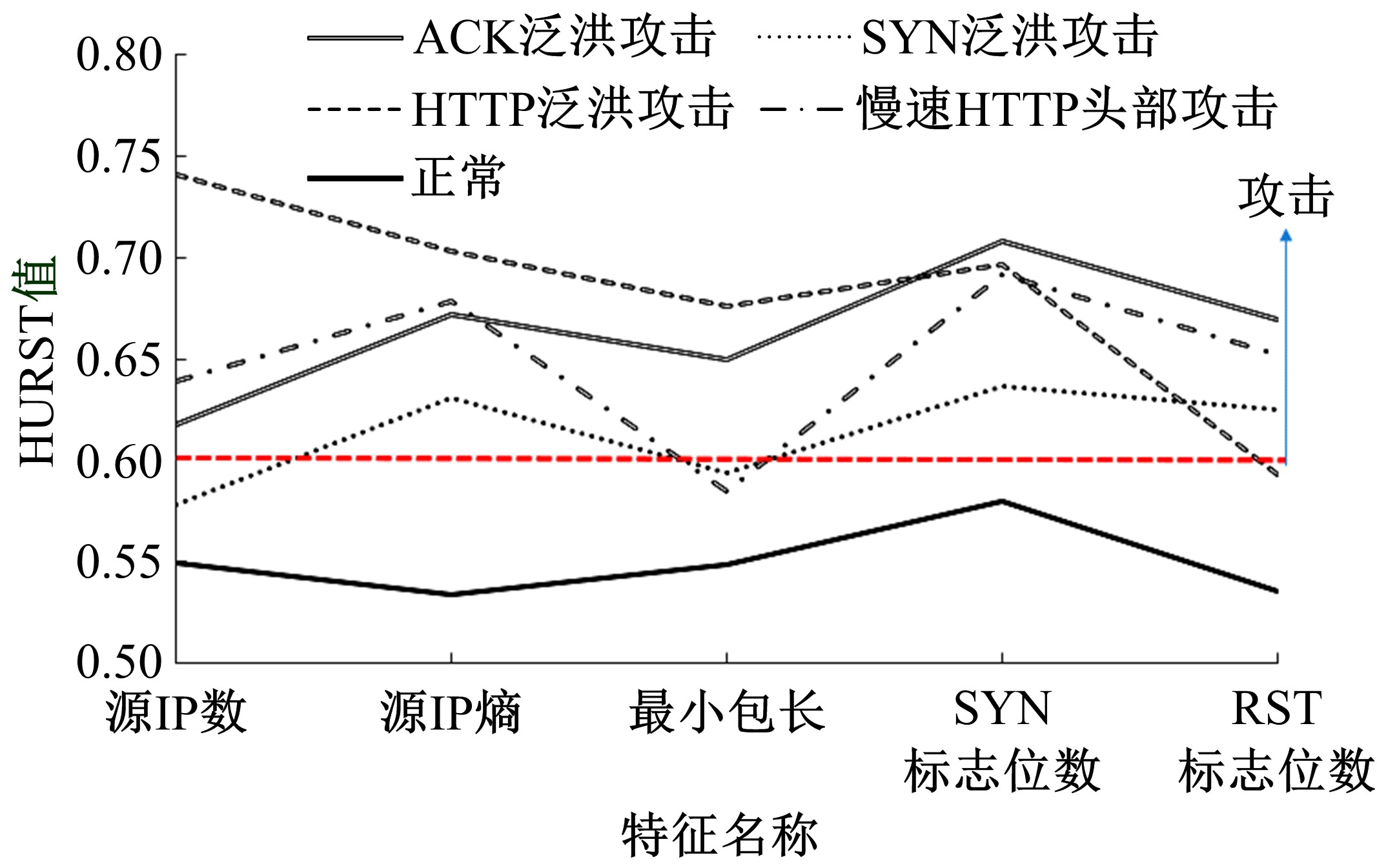
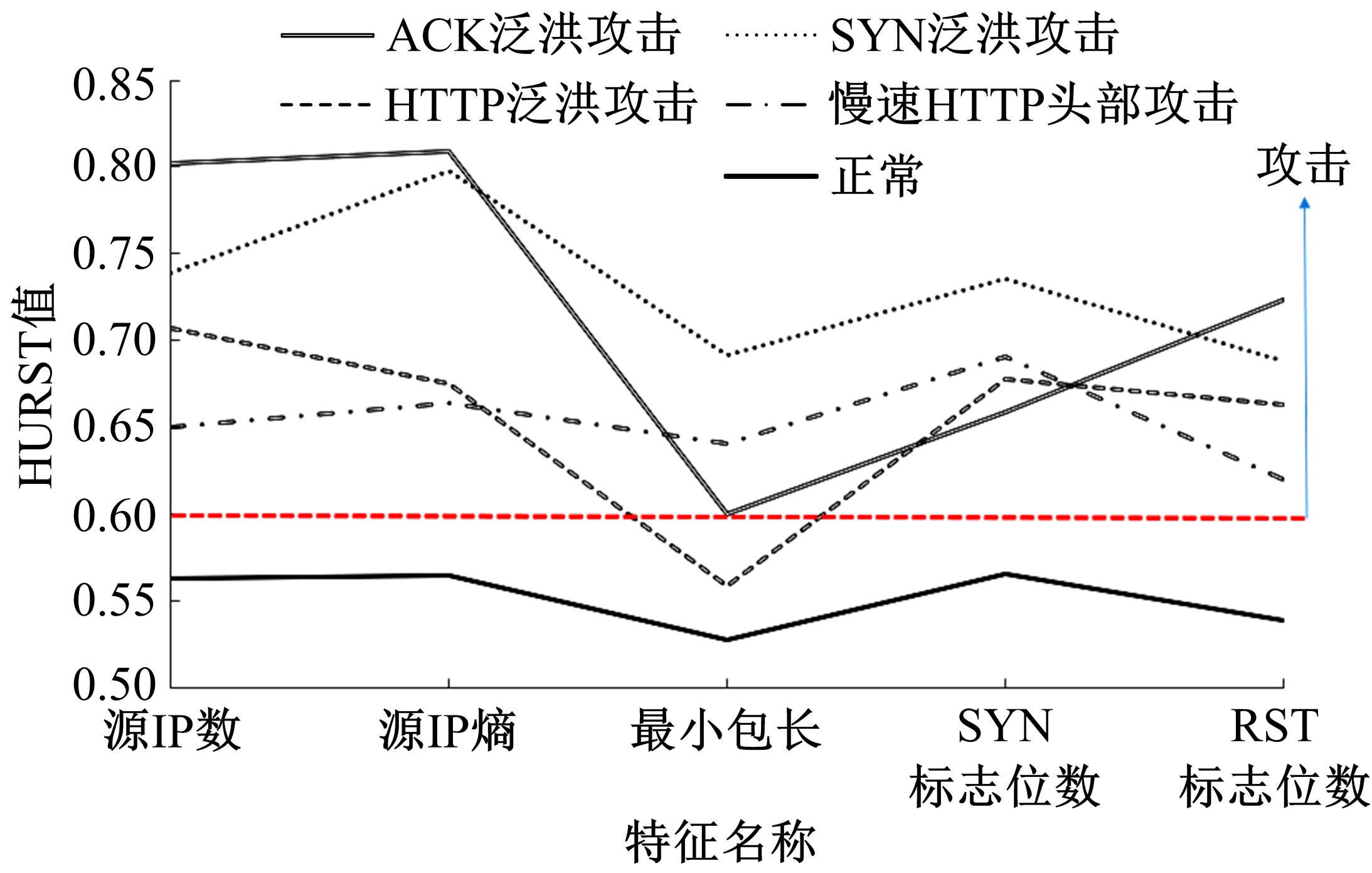
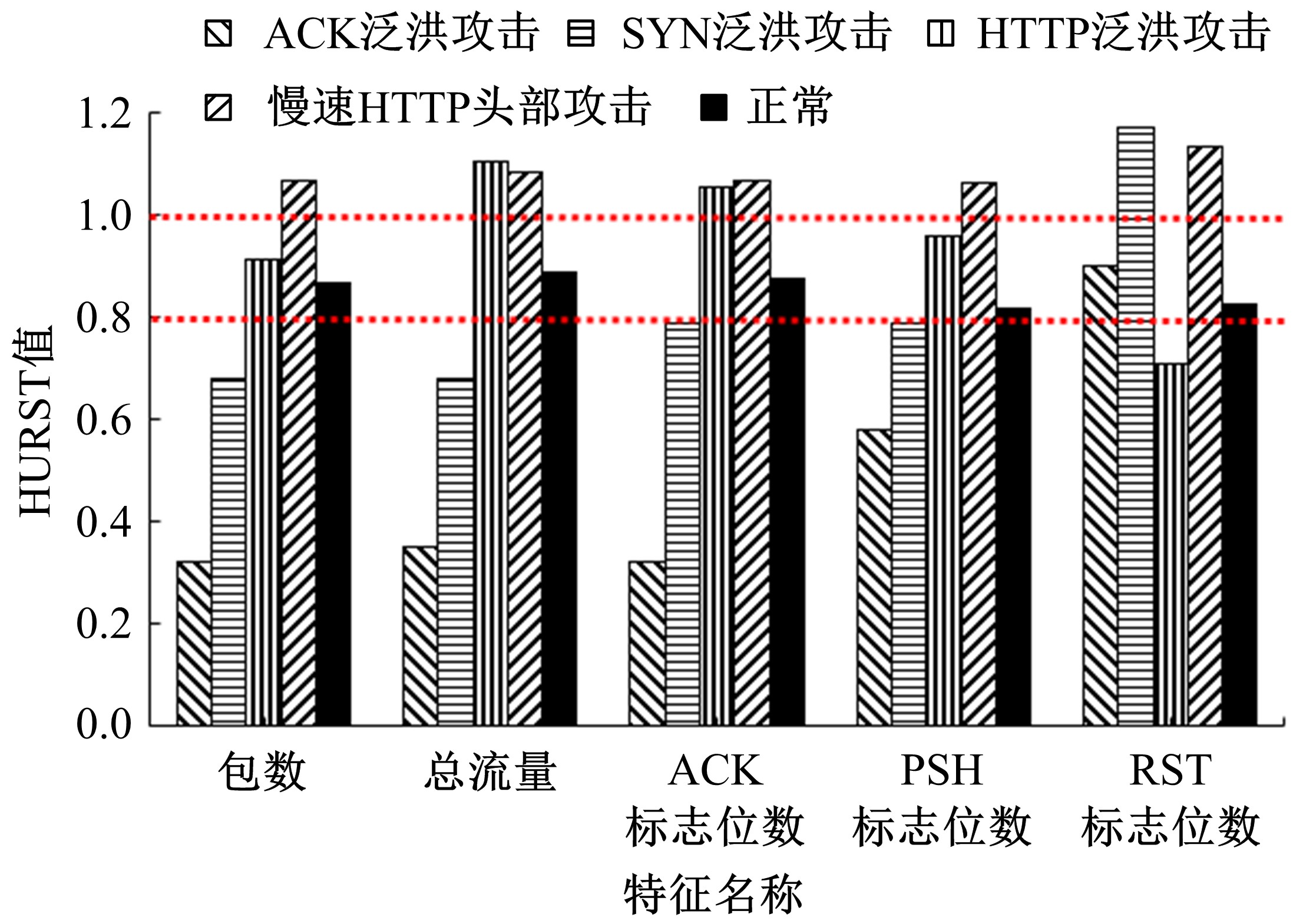
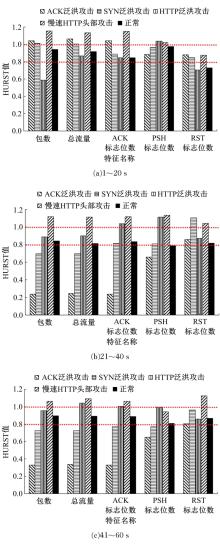
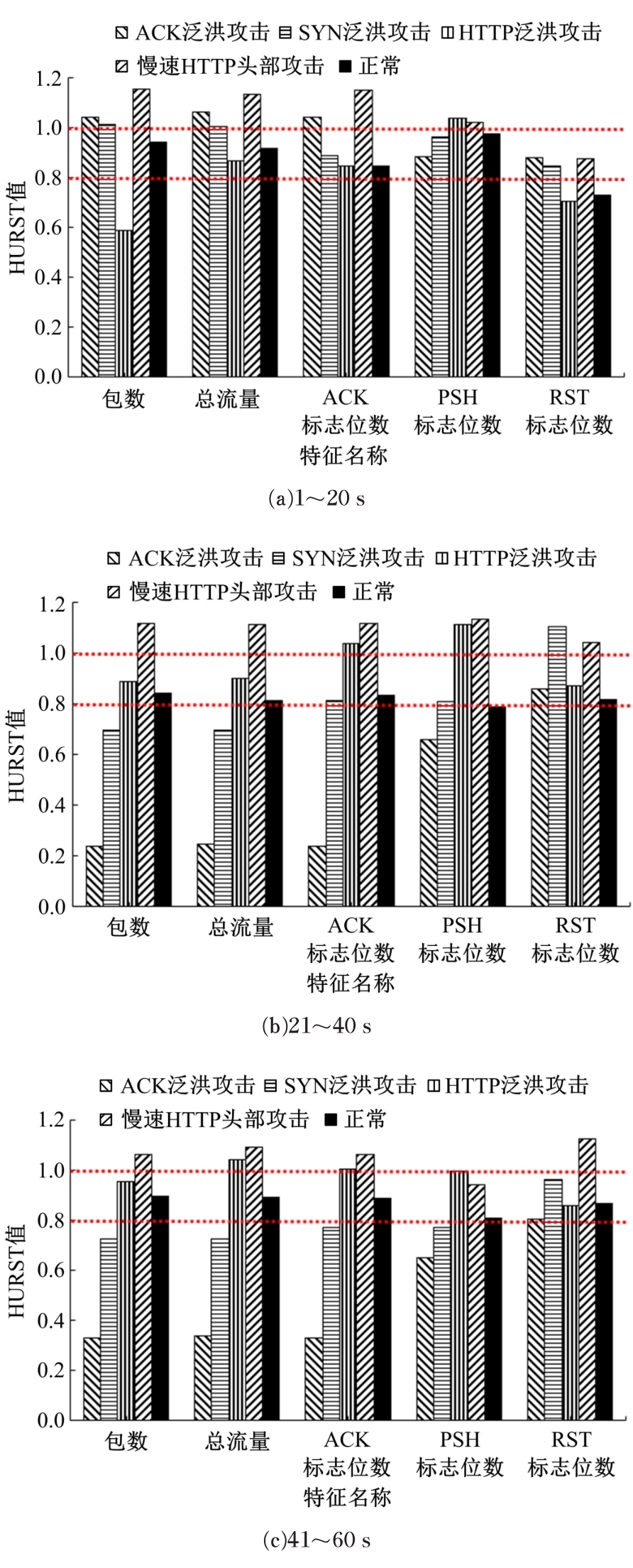
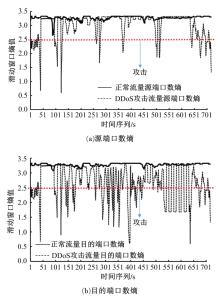
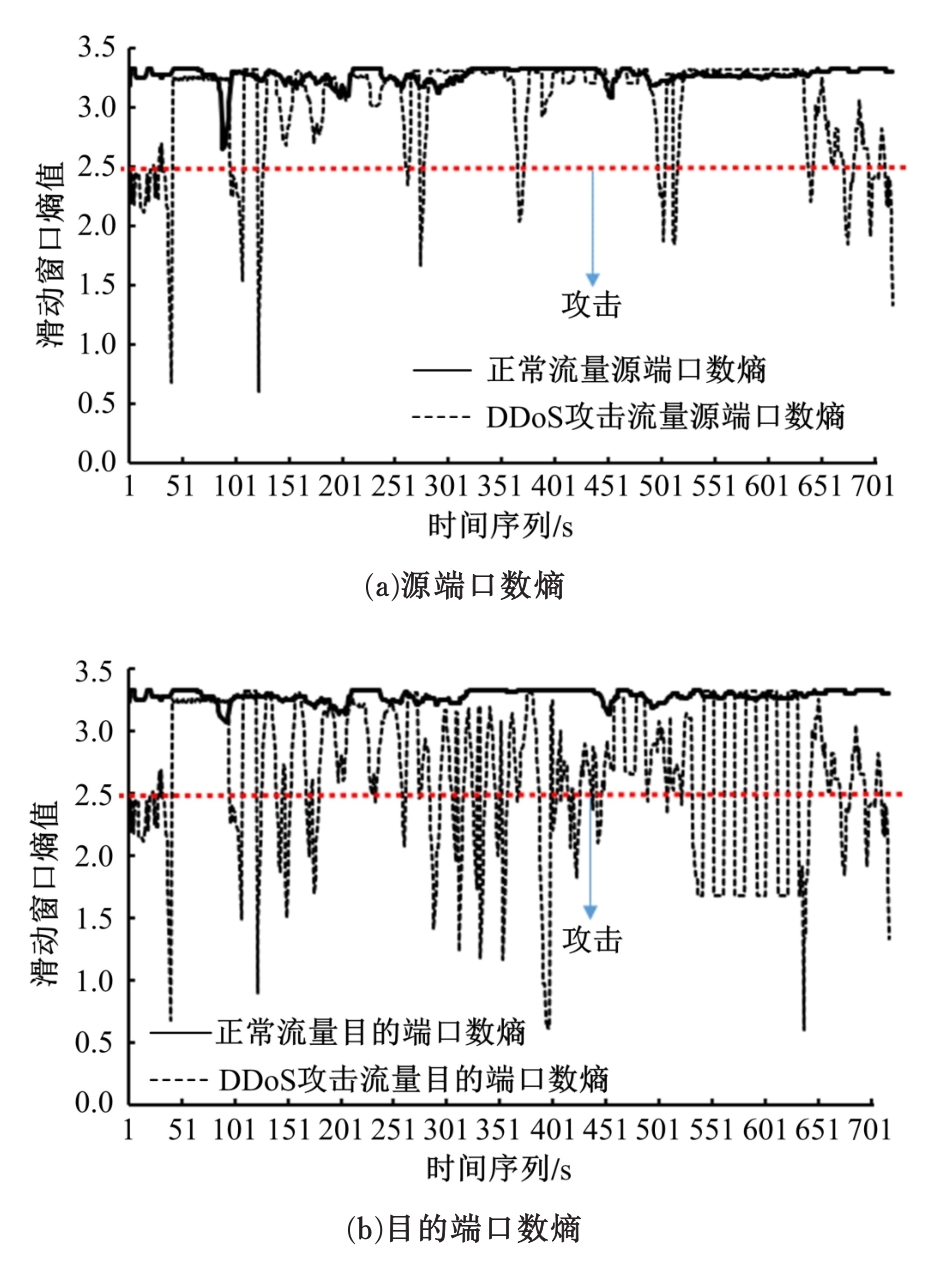
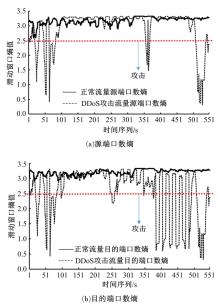
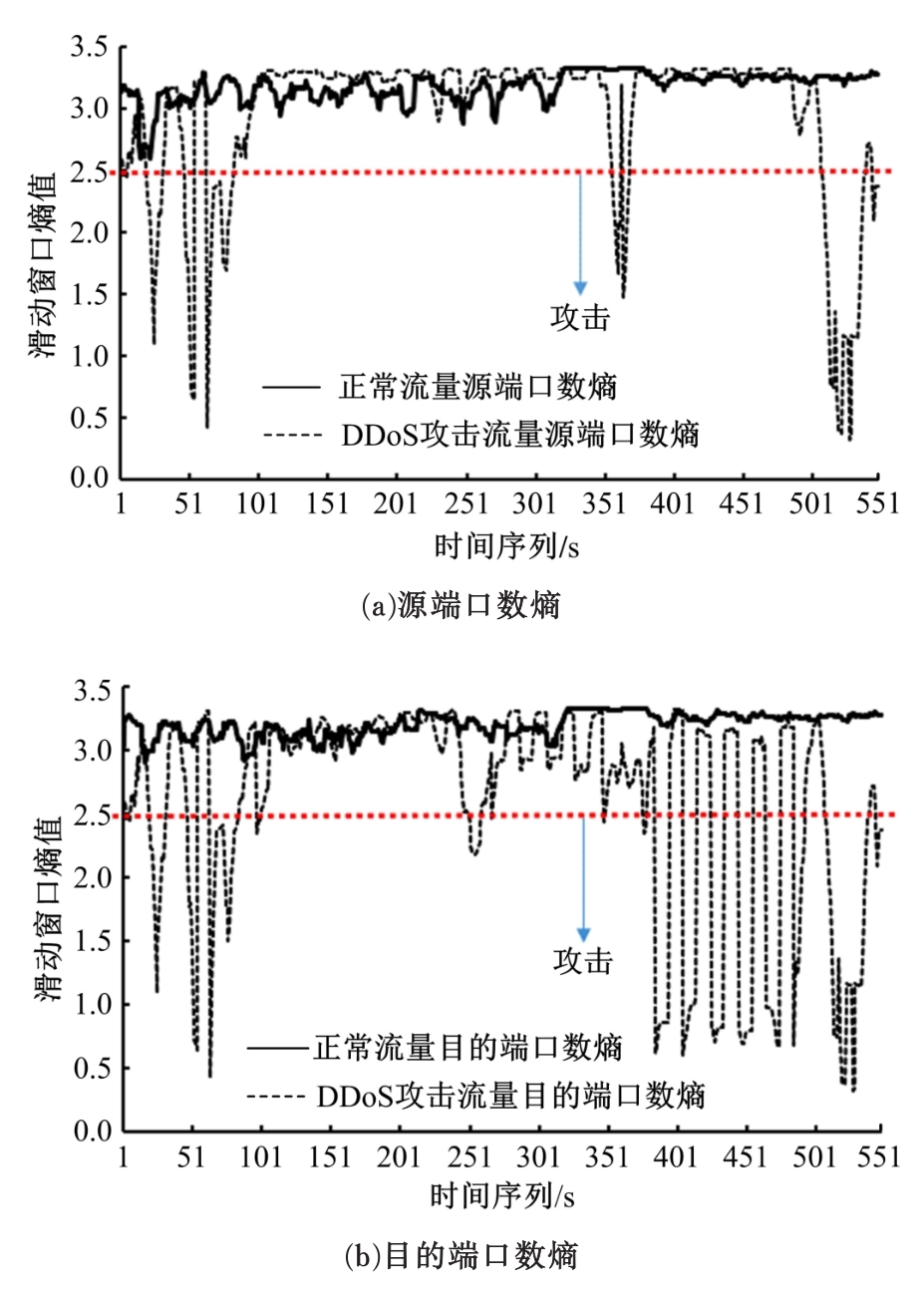
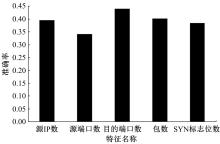
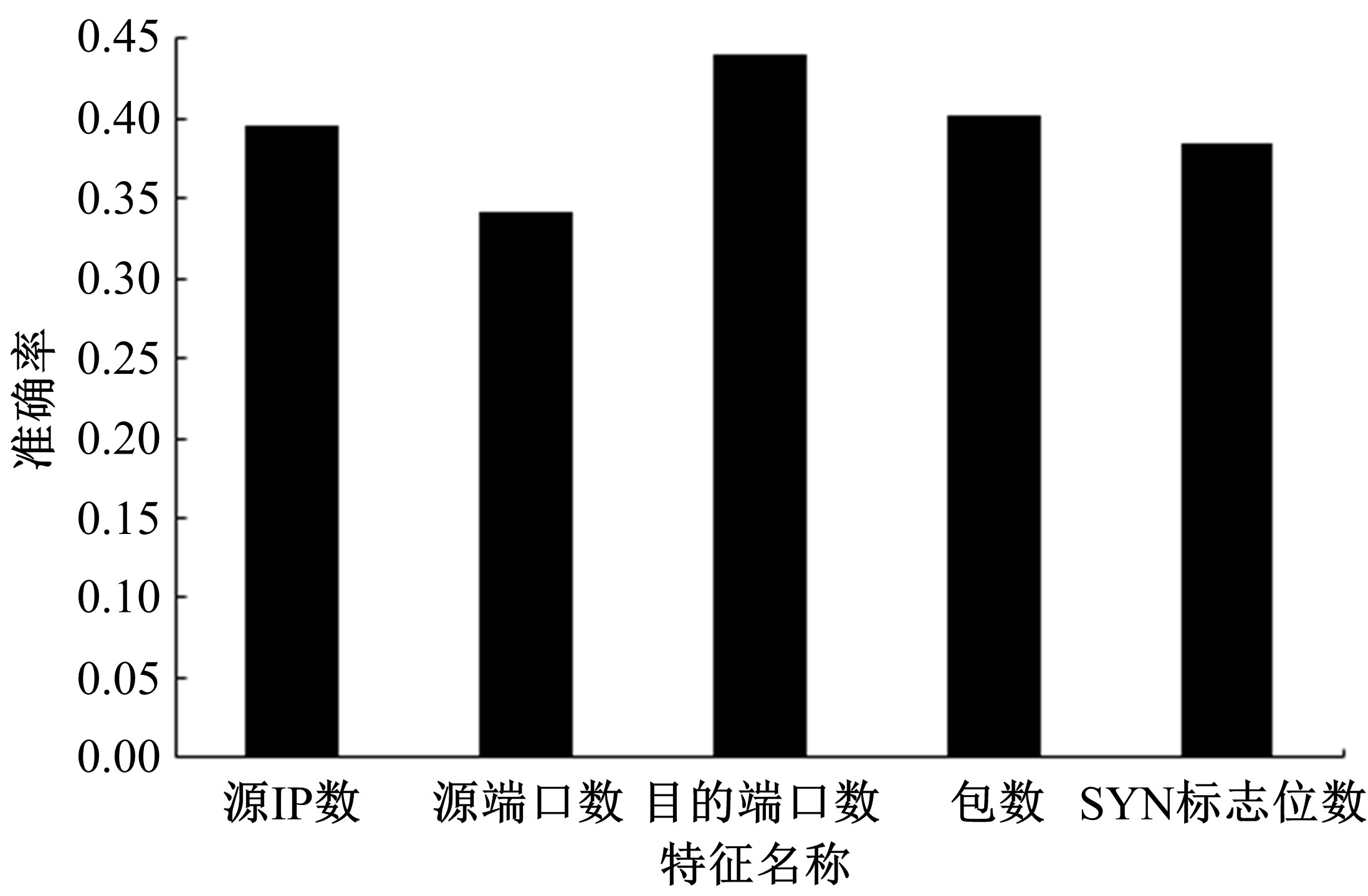
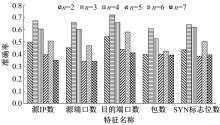
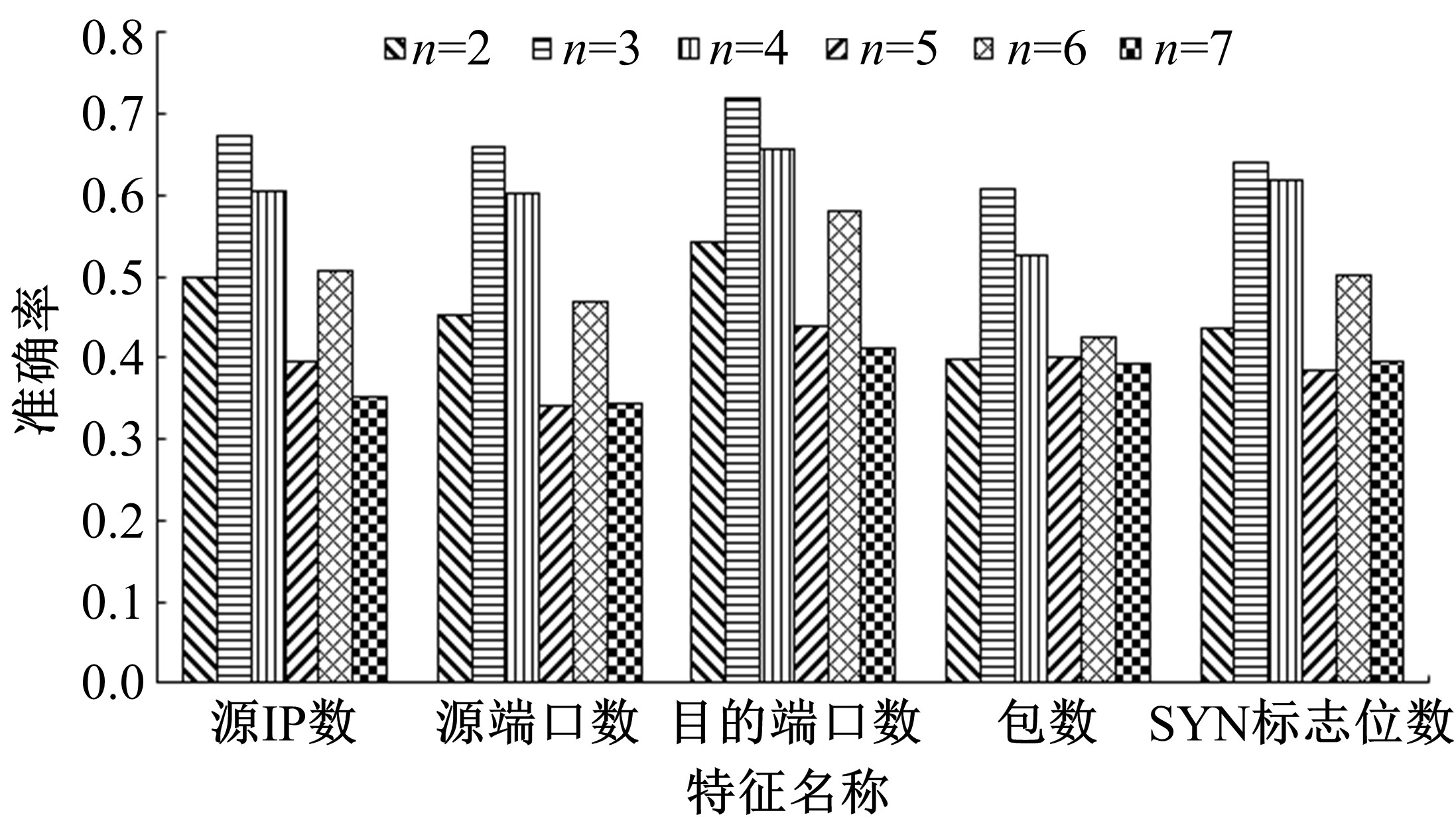
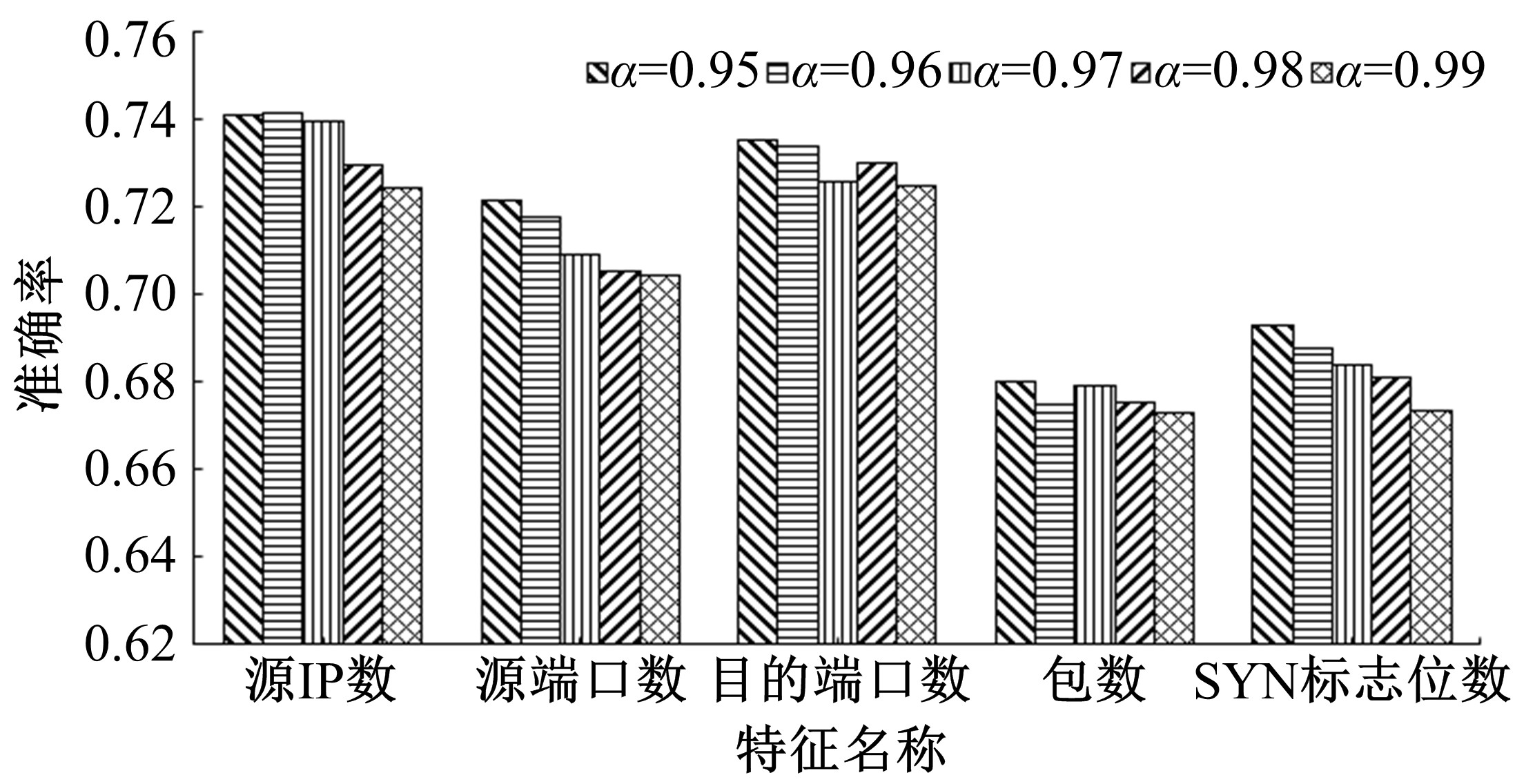
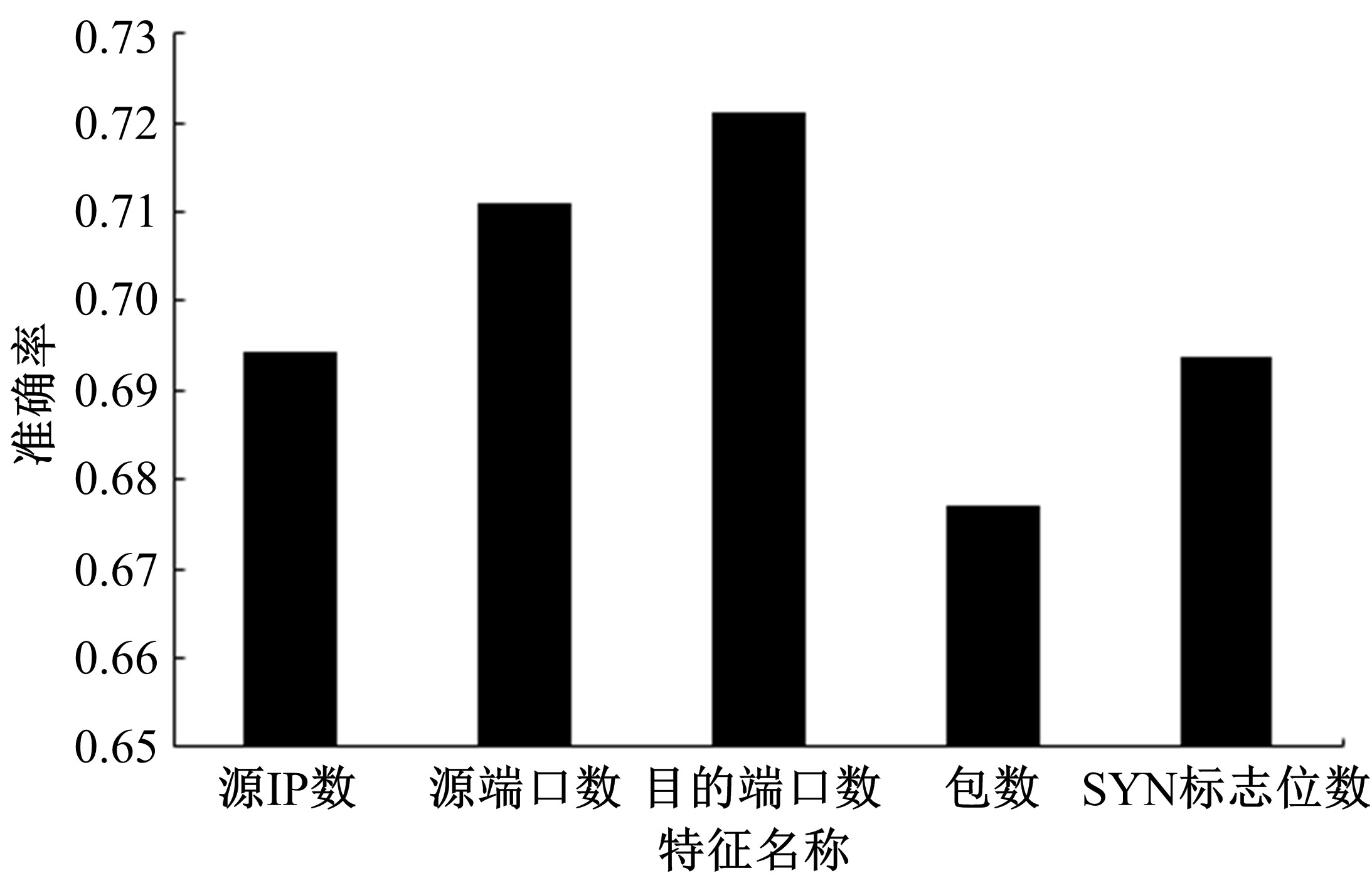
针对物联网大规模分布式拒绝服务攻击检测难题,基于Docker虚拟化容器技术搭建了物联网流量仿真平台,通过模拟Mirai僵尸网络和执行命令产生4种不同的攻击流量。人工执行与物联网实验箱自动产生正常流量。对原始流量进行统计分析生成包级和秒级两种不同等级的物联网流量数据集。提出了分段HURST指数、滑动窗口熵和滑动窗口置信区间3种统计指标和分析方法,并制定了攻击检测规则。实验结果表明:基于滑动窗口均值置信区间的异常流量检测方法可达72.11%的准确率。
中图分类号:
- TP309
| 1 | Kolias C, Kambourakis G, Stavrou A, et al. DDoS in the IoT: mirai and other botnets[J]. Computer, 2017, 50(7): 80-84. |
| 2 | Hilton S. Dyn analysis summary of friday october 21 attack Dyn[EB/OL]. [2016-10-01]. |
| 3 | Sahi A, Lai D, Li Y, et al. An efficient DDoS TCP flood attack detection and prevention system in a cloud environment[J]. IEEE Access, 2017(5): 6036-6048. |
| 4 | Gurulakshmi K, Nesarani A. Analysis of IoT bots against DDOS attack using machine learning algorithm[C]∥2018 2nd International Conference on Trends in Electronics and Informatics(ICOEI), Tirunelveli, 2018: 1052-1057. |
| 5 | Doshi R, Apthorpe N, Feamster N. Machine learning DDoS detection for consumer internet of things devices[C]∥2018 IEEE Security and Privacy Workshops(SPW), San Francisco, CA, 2018: 29-35. |
| 6 | Özçelik M, Chalabianloo N, Gür G. Software-Defined edge defense against IoT-based DDoS[C]∥2017 IEEE International Conference on Computer and Information Technology(CIT), Helsinki, 2017: 308-313. |
| 7 | Mishra A, Dixit A. Resolving threats in IoT: ID spoofing to DDoS[C]∥2018 9th International Conference on Computing, Communication and Networking Technologies(ICCCNT), Bangalore, 2018: 1-7. |
| 8 | Ben S N, Biondi F, Bontchev V, et al. Detection of mirai by syntactic and behavioral analysis[C]∥2018 IEEE 29th International Symposium on Software Reliability Engineering(ISSRE), Memphis, TN, USA, 2018: 224-235. |
| 9 | Agrawal N, Tapaswi S. Low rate cloud DDoS attack defense method based on power spectral density analysis[J]. Information Processing Letters, 2018, 138: 44-50. |
| 10 | Hirakawa T, Ogura K, Bista B B, et al. A defense method against distributed slow HTTP DoS attack[C]∥2016 19th International Conference on Network-Based Information Systems(NBiS), Ostrava, 2016: 152-158. |
| 11 | Muraleedharan N, Janet B. Behaviour analysis of HTTP based slow denial of service attack[C]∥2017 International Conference on Wireless Communications, Signal Processing and Networking(WiSPNET), Chennai, 2017: 1851-1856. |
| 12 | Ahmed M E, Ullah S, Kim H. Statistical application fingerprinting for DDoS attack mitigation[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(6): 1471-1484. |
| 13 | Kolias C, Kambourakis G, Stavrou A, et al. Intrusion detection in 802.11 networks: empirical evaluation of threats and a public dataset[J]. IEEE Communications Surveys & Tutorials, 2016, 18(1): 184-208. |
| 14 | Charles E. KDD Cup 1999: computer network intrusion detection[EB/OL]. [1999-09-01]. |
| 15 | 李金明, 王汝传. 基于Hurst参数的DoS/DDoS攻击实时检测技术研究[J]. 计算机工程与应用, 2007, 43(6): 20-23. |
| Li Jin-ming, Wang Ru-chuan. DoS/DDoS attack detection based on Hurst parameter[J]. Computer Engineering and Applications, 2007, 43(6): 20-23. | |
| 16 | 徐江平. 基于统计分析的分布式流量异常检测应用研究[D]. 成都: 电子科技大学通信与信息工程学院, 2015. |
| Xu Jiang-ping. Research on distributed traffic anomaly detection based on statistical analysis[D]. Chengdu: School of Communication and Information Engineering, University of Electronic Science and Technology of China, 2015. |
| [1] | 王天皓, 王忠福, 王雨蒙, 杨开宇, 高印寒, 马喜来. 基于混沌多项式展开法的线束串扰统计模型[J]. 吉林大学学报(工学版), 2017, 47(5): 1568-1576. |
| [2] | 李洪萍,裴玉龙,杨中良 . 快速路自由流速度及其影响因素 [J]. 吉林大学学报(工学版), 2007, 37(04): 772-776. |
|
||