Journal of Jilin University(Engineering and Technology Edition) ›› 2021, Vol. 51 ›› Issue (5): 1838-1844.doi: 10.13229/j.cnki.jdxbgxb20210400
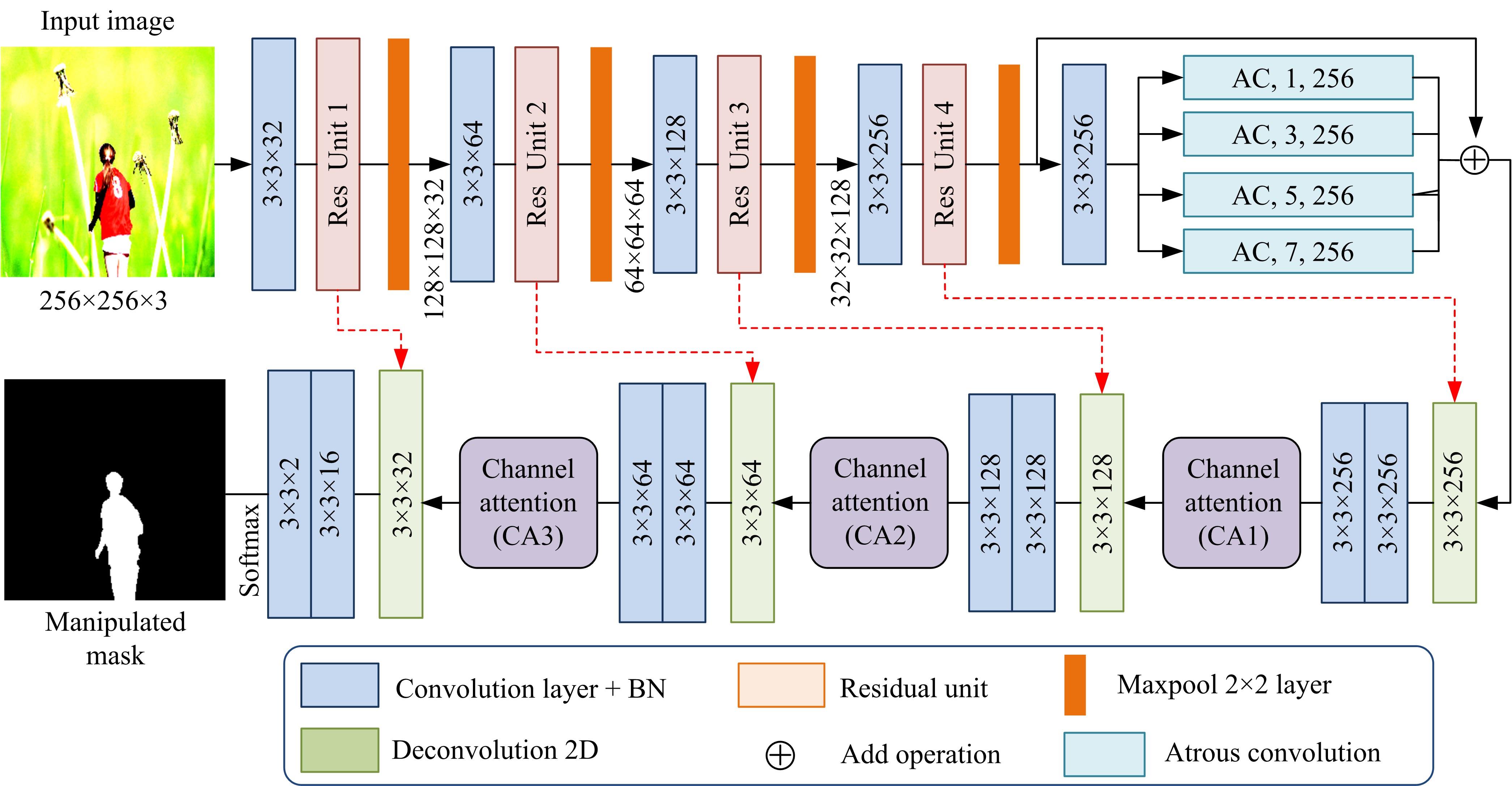
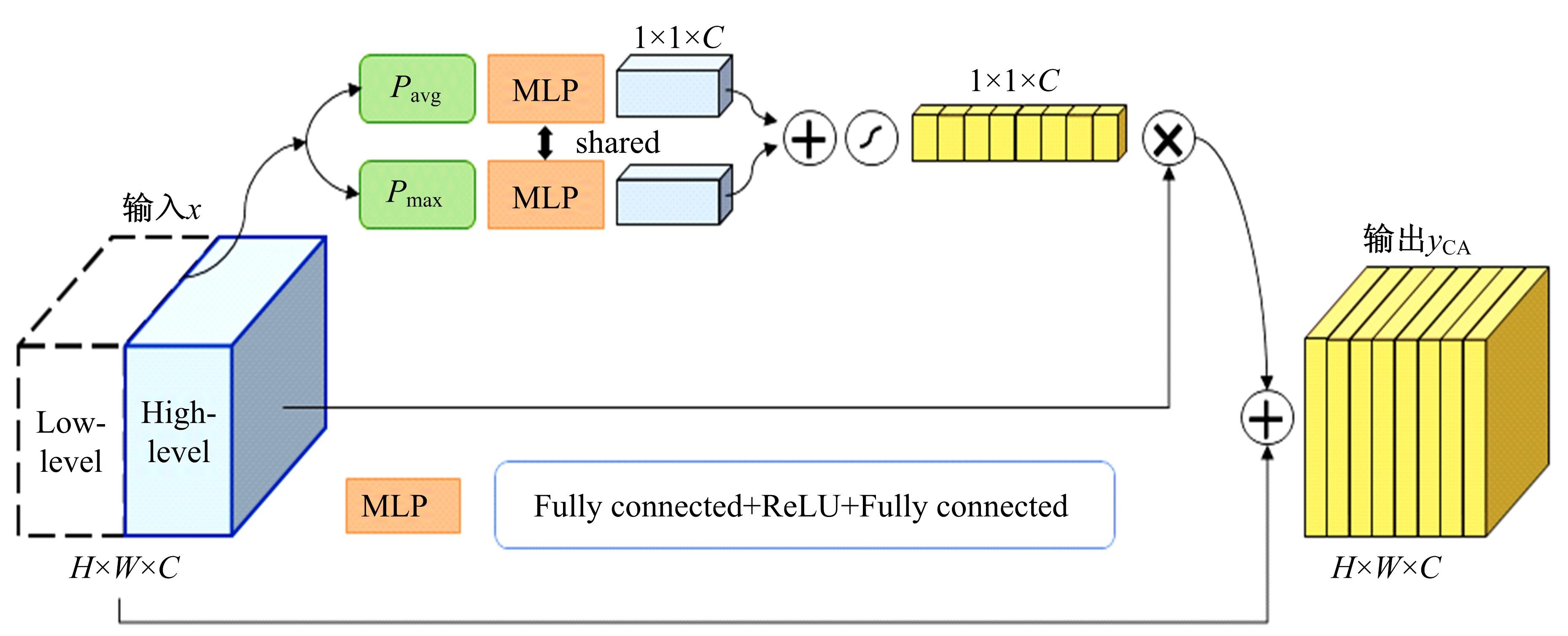
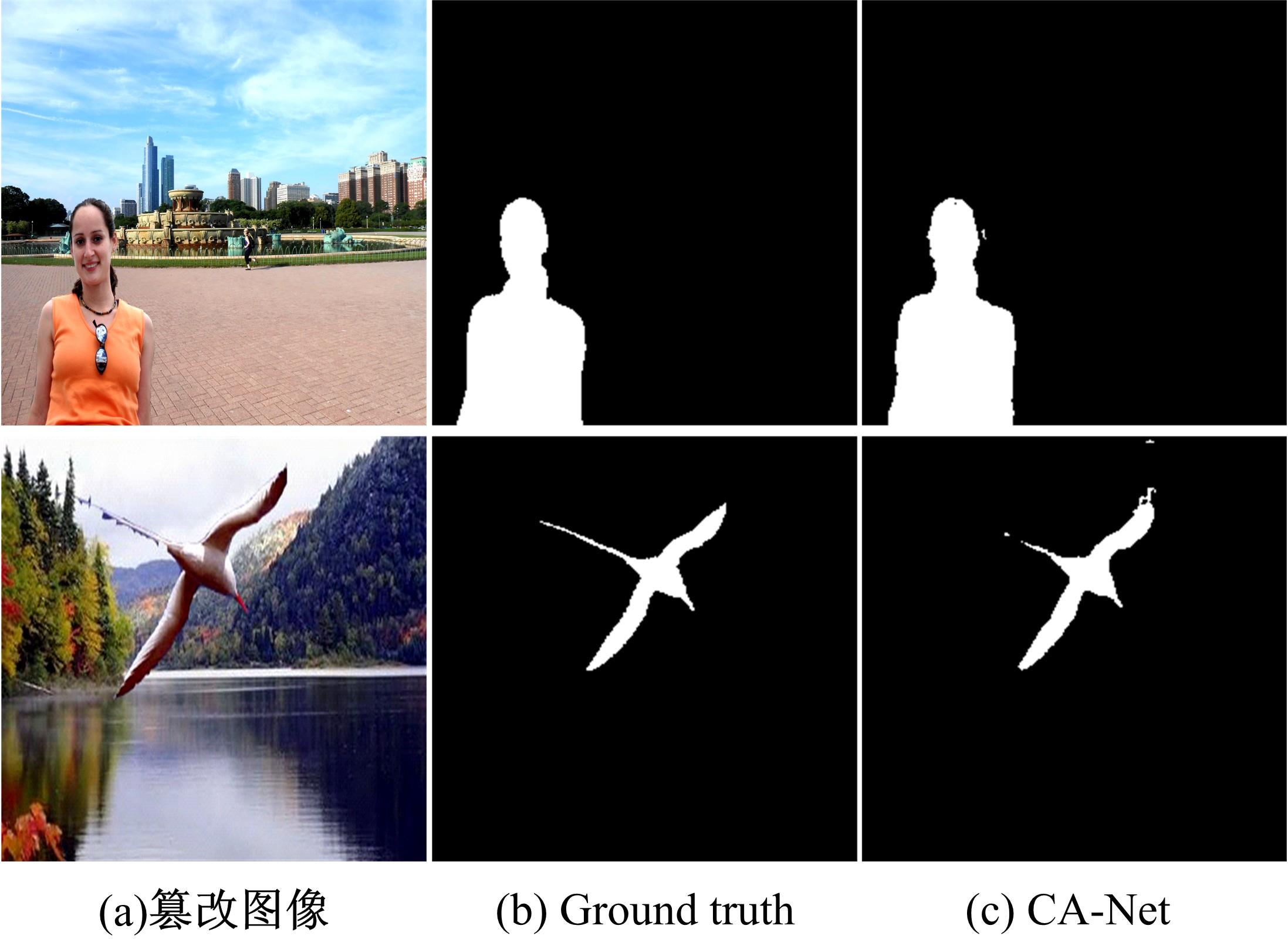
Image manipulation localization algorithm based on channel attention convolutional neural networks
Hui ZHONG1( ),Heng KANG2,Ying-da LYU3,Zhen-jian LI1,Hong LI1,Ruo-chuan OUYANG1
),Heng KANG2,Ying-da LYU3,Zhen-jian LI1,Hong LI1,Ruo-chuan OUYANG1
- 1.Management Center of Big Data and Network,Jilin University,Changchun 130012,China
2.ZICT Technology Co. ,Ltd. ,Shenzhen 518000,China
3.Center for Computer Fundamental Education,Jilin University,Changchun 130012,China
CLC Number:
- TP391
| 1 | 赵宏伟, 刘晓涵, 张媛, 等. 基于关键点注意力和通道注意力的服装分类算法[J]. 吉林大学学报: 工学版, 2020, 50(5): 1765-1770. |
| Zhao Hong-wei, Liu Xiao-han, Zhang Yuan, et al. Clothing classification algorithm based on landmark attention and channel attention[J]. Journal of Jilin University(Engineering and Technology Edition), 2020,50(5): 1765-1770. | |
| 2 | Zhuang P, Li H, Tan S, et al. Image tampering localization using a dense fully convolutional network[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2986-2999. |
| 3 | Ng T T, Chang S F, Sun Q. Blind detection of photomontage using higher order statistics[C]∥International Symposium on Circuits and Systems, Canada, 2004: 8189867. |
| 4 | Verdoliva L. Media forensics and deepfakes: an overview[J]. IEEE Journal of Selected Topics in Signal Processing, 2020, 14(5): 910-932. |
| 5 | Gaborini L, Bestagini P, Milani S, et al. Multi-clue image tampering localization[C]∥IEEE International Workshop on Information Forensics and Security, Atlanta, 2014: 125-130. |
| 6 | Ferrara P, Bianchi T, Rosa A D, et al. Image forgery localization via fine-grained analysis of CFA artifacts[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(5): 1566-1577. |
| 7 | Amerini I, Uricchio T, Ballan L, et al. Localization of JPEG double compression through multi-domain convolutional neural networks[C]∥IEEE Conference on Computer Vision and Pattern Recognition Workshops, Honolulu, 2017: 1865-1871. |
| 8 | Salloum R, Ren Y, Kuo C-C J. Image splicing localization using a multi-task fully convolutional network[J]. Journal of Visual Communication Image Representation, 2018, 51: 201-209. |
| 9 | Bappy J H, Simons C, Nataraj L, et al. Hybrid LSTM and Encoder-Decoder architecture for detection of image forgeries[J]. IEEE Transactions on Image Processing, 2019, 28(7): 3286-3300. |
| 10 | 陈绵书, 于录录, 苏越, 等. 基于卷积神经网络的多标签图像分类[J]. 吉林大学学报: 工学版, 2020, 50(3): 1077-1084. |
| Chen Mian-shu, Yu Lu-lu, Su Yue, et al. Multi-label images classification based on convolutional neural network [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(3): 1077-1084. | |
| 11 | Woo S, Park J, Lee J Y, et al. CBAM: convolutional block attention module[C]∥Proceedings of Europeon Conference on Computer Vision, Cham, Springer: 2018: 3-19. |
| 12 | Ronneberger O, Fischer P, Brox T. U-Net: convolutional networks for biomedical image segmentation[C]∥International Conference on Medical Image Computing and Computer-Assisted Intervention, Cham, Springer: 2015: 234-241. |
| 13 | Wu Y, Abd-Almageed W, Natarajan P. Deep matching and validation network: an end-to-end solution to constrained image splicing localization and detection[C]∥Proceedings of the 25th ACM International Conference on Multimedia, CA, 2017: 1480-1502. |
| 14 | Chen L, Papandreou G, Kokkinos I, et al. Deeplab: semantic image segmentation with deep convolutional nets, atrous convolution, and fully connected crfs[J]. IEEE Transactions on Pattern Analysis Machine Intelligence, 2017, 40(4): 834-848. |
| 15 | Badrinarayanan V, Kendall A, Cipolla R. Segnet: a deep convolutional encoder-decoder architecture for scene segmentation[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2017, 39(12): 2481-2495. |
| 16 | Kingma D P, Ba J. Adam: a method for stochastic optimization[C]∥3rd International Conference for Learning Representations, San Diego, 2015: arXiv:. |
| 17 | Guan H, Kozak M, Robertson E, et al. MFC datasets: large-scale benchmark datasets for media forensic challenge evaluation[C]∥IEEE Winter Applications of Computer Vision Workshops, Waikoloa, 2019: 63-72. |
| 18 | Dong J, Wang W, Tan T. Casia image tampering detection evaluation database[C]∥IEEE China Summit and International Conference on Signal and Information Processing, Beijing, 2013: 422-426. |
| 19 | Chen L, Papandreou G, Kokkinos I, et al. DeepLab: semantic image segmentation with deep convolutional nets, atrous convolution, and fully connected CRFs[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2018, 40(4): 834-848. |
| 20 | Luo W, Huang J, Qiu G. JPEG error analysis and its applications to digital image forensics[J]. IEEE Transactions on Information Forensics & Security, 2010, 5(3): 480-491. |
| 21 | Mahdian B, Saic S. Using noise inconsistencies for blind image forensics[J]. Image and Vision Computing, 2009, 27(10): 1497-1503. |
| 22 | Zhou P, Han X, Morariu V, et al. Learning rich features for image manipulation detection[C]∥Proceedings of IEEE Conference Computer Vision and Pattern Recognition, Salt Lake City, 2018: 1053-1061. |
| 23 | Bappy M, Roy-Chowdhury A K, Bunk J, et al. Exploiting spatial structure for localizing manipulated image regions[C]∥IEEE International Conference on Computer Vision, Venice, 2017: 17467965. |
| 24 | Wu Y, Abdalmageed W, Natarajan P. Mantra-Net: manipulation tracing network for detection and localization of image forgeries with anomalous features[C]∥Proceedings of IEEE Conference Computer Vision and Pattern Recognition, Long Beach, 2019: 9543-9552. |
| [1] | Hou⁃jie LI,Fa⁃sheng WANG,Jian⁃jun HE,Yu ZHOU,Wei LI,Yu⁃xuan DOU. Pseudo sample regularization Faster R⁃CNN for traffic sign detection [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1251-1260. |
| [2] | Xiao-long ZHU,Zhong XIE. Automatic construction of knowledge graph based on massive text data [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(4): 1358-1363. |
| [3] | Tao XU,Ke MA,Cai-hua LIU. Multi object pedestrian tracking based on deep learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 27-38. |
| [4] | Yi-bin LI,Jia-min GUO,Qin ZHANG. Methods and technologies of human gait recognition [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 1-18. |
| [5] | GENG Qing-tian, YU Fan-hua, WANG Yu-ting, GAO Qi-kun. New algorithm for vehicle type detection based on feature fusion [J]. 吉林大学学报(工学版), 2018, 48(3): 929-935. |
| [6] | DONG Qiang, LIU Jing-hong, ZHOU Qian-fei. Improved SURF algorithm used in image mosaic [J]. 吉林大学学报(工学版), 2017, 47(5): 1644-1652. |
| [7] | YIN Ming, ZHAN Yin-wei, PEI Hai-long. Co-sparse analysis operator learning for image fusion [J]. 吉林大学学报(工学版), 2016, 46(6): 2052-2058. |
| [8] | XIAO Zhong-jie. Recognition of digital image based on wavelet space feature spectrum entropy [J]. 吉林大学学报(工学版), 2015, 45(6): 1994-1998. |
| [9] | LIU Hong,SUN Shuang-zi,WANG Qing-yuan,LI Yan-zhong. PSO based feature extraction method for analog circuit fault information [J]. 吉林大学学报(工学版), 2015, 45(2): 675-680. |
| [10] | PAN Hai-yang, LIU Shun-an, YAO Yong-ming. Depth information-basd autonomous aerial refueling [J]. 吉林大学学报(工学版), 2014, 44(6): 1750-1756. |
| [11] | GU Bo-yu,SUN Jun-xi,LI Hong-zuo,LIU Hong-xi,LIU Guang-wen. Face recognition based on eigen weighted modular two-directional two-dimensional PCA [J]. 吉林大学学报(工学版), 2014, 44(3): 828-833. |
| [12] | WANG Zhuo-zheng, JIA Ke-bin. Application of matrix completion and principal component analysis to corrupted image registration [J]. 吉林大学学报(工学版), 2013, 43(增刊1): 78-83. |
| [13] | SHI Dong-cheng, ZHENG Chao. Eye states detection algorithm based on phase information [J]. 吉林大学学报(工学版), 2013, 43(增刊1): 265-269. |
| [14] | ZHAO Hong-wei, CHEN Xiao, LONG Man-li, PEI Shi-hui. Image edge detection based on Riesz transformation [J]. 吉林大学学报(工学版), 2013, 43(增刊1): 133-137. |
| [15] | ZHANG Xu, GUO Bao-long, MENG Fan-jie, SUN Wei. Image retrieval based on IPDSH and region division [J]. 吉林大学学报(工学版), 2013, 43(05): 1408-1414. |
|
||