Journal of Jilin University(Engineering and Technology Edition) ›› 2021, Vol. 51 ›› Issue (3): 1055-1059.doi: 10.13229/j.cnki.jdxbgxb20200655
Double chaos identifiable tampering image encryption method based on blockchain technology
- School of Information Science and Technology,Tibet University,Lhasa 850012,China
CLC Number:
- TP393
| 1 | 冉维, 韦鹏程, 段昂. 融合多混沌映射和DNA编码的图像加密算法[J]. 计算机工程与设计, 2018, 39(7):228-234. |
| Ran Wei, Wei Peng-cheng, Duan Ang. Image encryption algorithm combining multiple chaotic maps and DNA encoding[J]. Computer Engineering and Design, 2018, 39(7):228-234. | |
| 2 | 胡春杰, 陈晓, 陈霞. 基于改进广义Arnold映射的多混沌图像加密算法[J]. 包装工程, 2017, 38(3):144-149. |
| Hu Chun-jie, Chen Xiao, Chen Xia. Multi-chaotic image encryption algorithm based on improved generalized Arnold map[J]. Packaging Engineering, 2017, 38(3):144-149. | |
| 3 | 姚丽莉, 袁操今, 强俊杰, 等. 基于Gyrator变换和矢量分解的非对称图像加密方法[J]. 物理学报, 2016, 65(21):214203. |
| Yao Li-li, Yuan Cao-jin, Qiang Jun-jie, et al. Asymmetric image encryption method based on Gyrator transformation and vector decomposition[J]. Acta Physica Sinica, 2016, 65(21):No.214203. | |
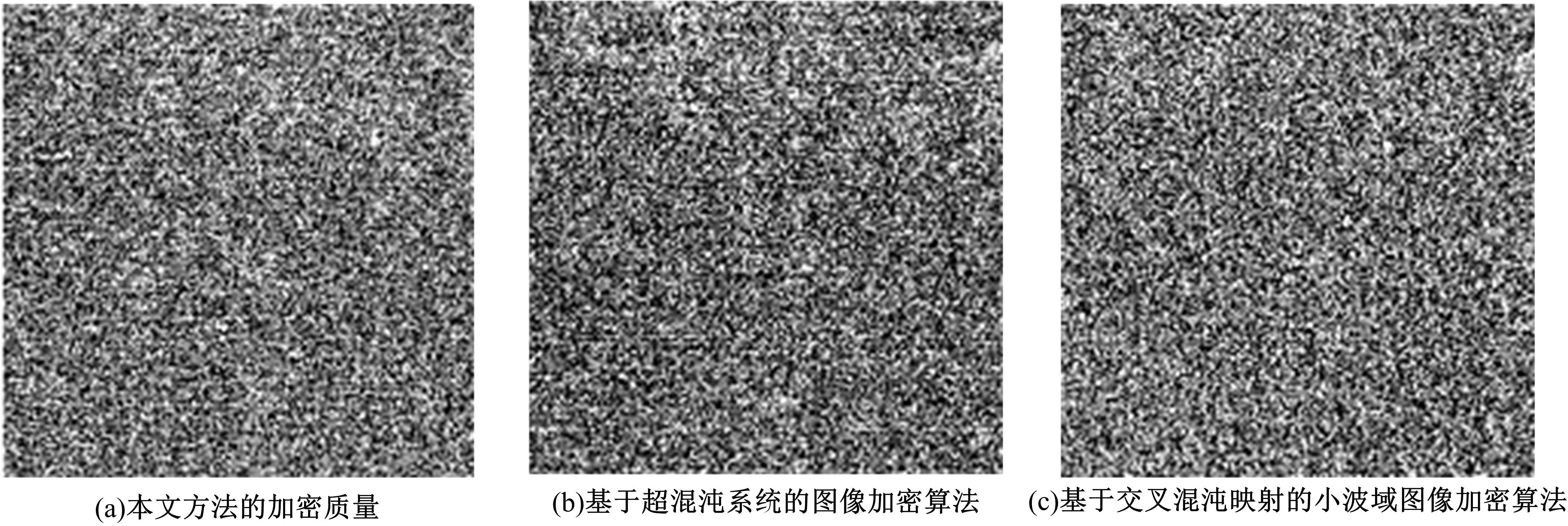
| 4 | 林青, 王延江, 王珺. 基于超混沌系统的图像加密算法[J]. 中国科学:技术科学, 2016, 46(9):910-912. |
| Lin Qing, Wang Yan-jiang, Wang Jun. Image encryption algorithm based on hyperchaotic system[J]. Science China: Technical Sciences, 2016, 46(9):910-912. | |
| 5 | 闫兵, 柏森, 刘博文,等. 基于交叉混沌映射的小波域图像加密算法[J]. 计算机应用研究, 2018, 35(6):203-205, 217. |
| Yan Bing, Bai Sen, Liu Bo-wen, et al. Image encryption algorithm in wavelet domain based on cross-chaotic mapping[J]. Application Research of Computers, 2018, 35(6):203-205, 217. | |
| 6 | 底晓强,王英政,李锦青,等. 基于量子细胞神经网络超混沌的视频加密方法[J]. 吉林大学学报:工学版,2018,48(3):919-928. |
| Di Xiao-qiang, Wang Ying-zheng, Li Jin-qing, et al. Video encryption method based on hyperchaos of quantum cellular neural networks[J]. Journal of Jilin University(Engineering and Technology Edition), 2018,48(3):919-928. | |
| 7 | 韩思敏, 张薇, 张翔,等. 基于光场成像原理和混沌系统的多图像加密方法[J]. 光子学报, 2020, 49(3):199-208. |
| Han Si-min, Zhang Wei, Zhang Xiang, et al. Multi-image encryption method based on light field imaging principle and chaotic system[J]. Acta Photonica Sinica, 2020, 49(3):199-208. | |
| 8 | 唐永军. 基于伪随机的图像水印算法[J]. 液晶与显示, 2020, 35(3):287-291. |
| Tang Yong-jun. Image watermarking algorithm based on pseudo-random[J]. Liquid Crystal Display, 2020, 35(3):287-291. | |
| 9 | 韩家伟,刘衍珩,孙鑫,等. 基于量子密钥和云服务的身份加密方案[J]. 吉林大学学报:工学版,2018,48(2):551-557. |
| Han Jia-wei, Liu Yan-heng, Sun Xin, et al. Identity-based encryption scheme based on cloud and quantum keys[J] . Journal of Jilin University(Engineering and Technology Edition), 2018,48(2):551-557. | |
| 10 | 赵锋, 吴成茂. 自编码和超混沌映射相结合的图像加密算法[J]. 计算机辅助设计与图形学学报, 2016, 28(1):119-128. |
| Zhao Feng, Wu Cheng-mao. Image encryption algorithm combining self-encoding and hyperchaotic mapping[J]. Journal of Computer Aided Design and Graphics, 2016, 28(1):119-128. |
| [1] | Yuan-ning LIU,Di WU,Xiao-dong ZHU,Qi-xian ZHANG,Shuang-shuang LI,Shu-jun GUO,Chao WANG. User interface components detection algorithm based on improved YOLOv3 [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1026-1033. |
| [2] | Xiao-long ZHU,Zhong XIE. Geospatial data extraction algorithm based on machine learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1011-1016. |
| [3] | Dan-tong OUYANG,Yang LIU,Jie LIU. Fault diagnosis method based on test set under fault response guidance [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1017-1025. |
| [4] | Rong QIAN,Ru ZHANG,Ke-jun ZHANG,Xin JIN,Shi-liang GE,Sheng JIANG. Capsule graph neural network based on global and local features fusion [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1048-1054. |
| [5] | Xiao-hui WEI,Chang-bao ZHOU,Xiao-xian SHEN,Yuan-yuan LIU,Qun-chao TONG. Accelerating CALYPSO structure prediction with machine learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 667-676. |
| [6] | Bing-hai ZHOU,Qiong WU. Balancing and bi⁃objective optimization of robotic assemble lines [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 720-727. |
| [7] | Tian-qi GU,Chen-jie HU,Yi TU,Shu-wen LIN. Robust reconstruction method based on moving least squares algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 685-691. |
| [8] | Qian-yi XU,Gui-he QIN,Ming-hui SUN,Cheng-xun MENG. Classification of drivers' head status based on improved ResNeSt [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(2): 704-711. |
| [9] | Xiao-yu WANG,Xin-hao HU,Chang-lin HAN. Face pencil drawing algorithms based on generative adversarial network [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 285-292. |
| [10] | Ming FANG,Wen-qiang CHEN. Face micro-expression recognition based on ResNet with object mask [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 303-313. |
| [11] | Yuan SONG,Dan-yuan ZHOU,Wen-chang SHI. Method to enhance security function of OpenStack Swift cloud storage system [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(1): 314-322. |
| [12] | Hong-wei ZHAO,Xiao-han LIU,Yuan ZHANG,Li-li FAN,Man-li LONG,Xue-bai ZANG. Clothing classification algorithm based on landmark attention and channel attention [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1765-1770. |
| [13] | Nai-yan GUAN,Juan-li GUO. Component awareness adaptive model based on attitude estimation algorithms [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1850-1855. |
| [14] | Yang LI,Shuo LI,Li-wei JING. Estimate model based on Bayesian model and machine learning algorithms applicated in financial risk assessment [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1862-1869. |
| [15] | Bing-hai ZHOU,Zhao-xu HE. Dynamic material handling scheduling for mixed⁃model assembly lines based on line⁃integrated supermarkets [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(5): 1809-1817. |
|
||