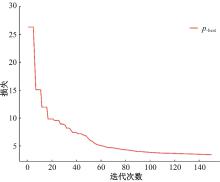
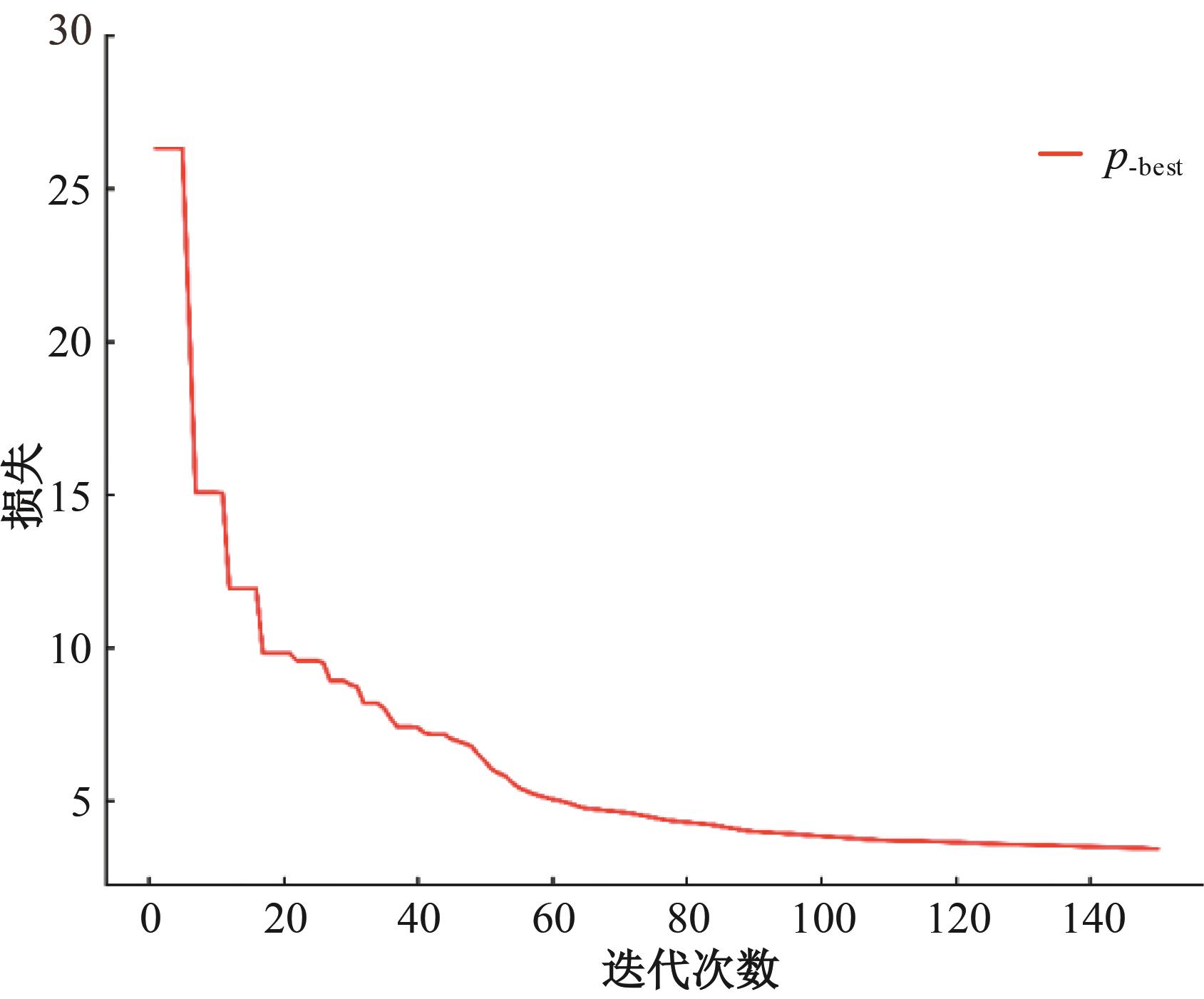
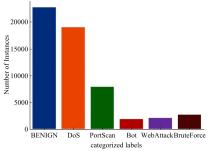
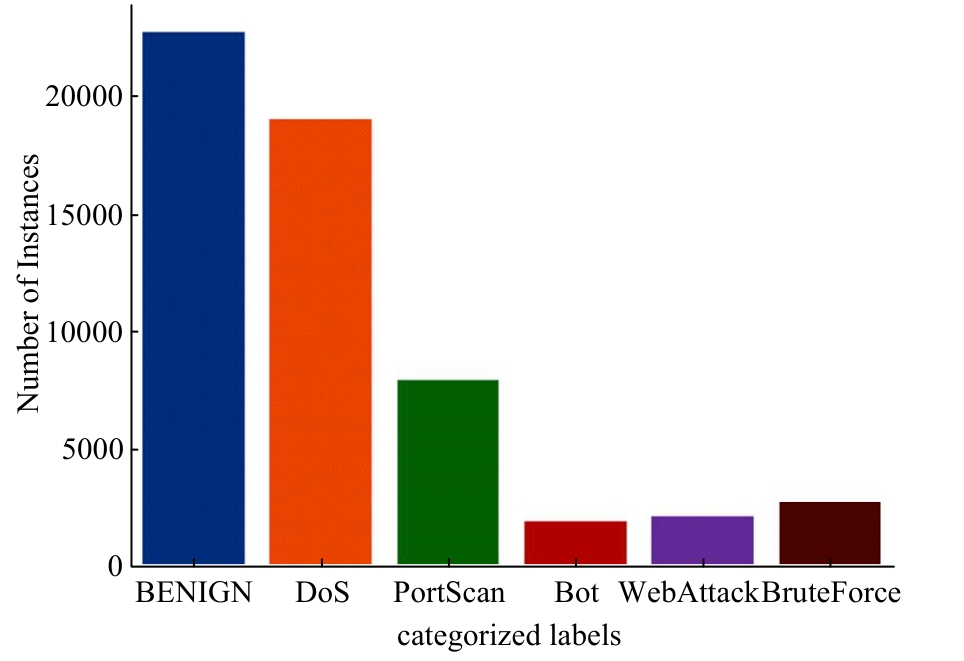
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (4): 1396-1405.doi: 10.13229/j.cnki.jdxbgxb.20230751
Previous Articles Next Articles
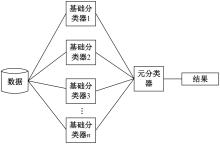
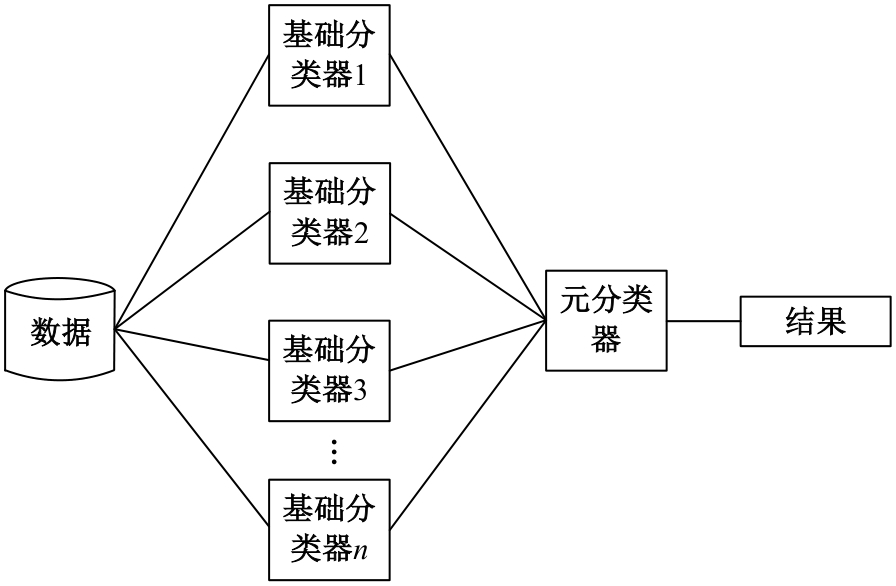
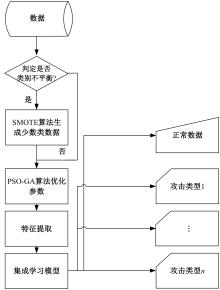
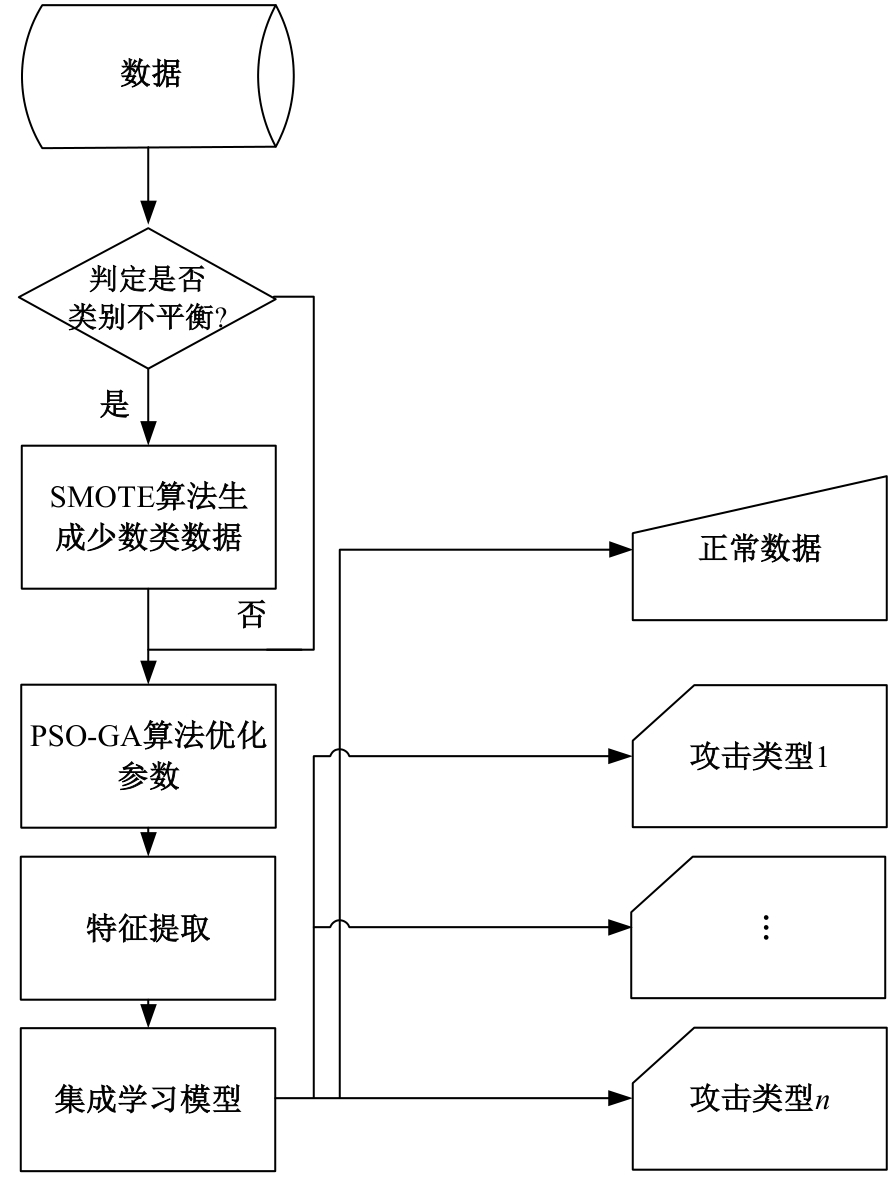
Intrusion detection method based on ensemble learning and feature selection by PSO-GA
Jun WANG( ),Chang-fu SI,Kai-peng WANG,Qiang FU(
),Chang-fu SI,Kai-peng WANG,Qiang FU( )
)
- College of Computer Science and Technology,Shenyang University of Chemical Technology,Shenyang 110142,China
CLC Number:
- TP399
| 1 | Gaikwad D P, Thool R C.Intrusion detection system using bagging ensemble method of machine learning[C]∥International Conference on Computing Communication Control and Automation, Pune, India,2015: 291-295. |
| 2 | Shen Y, Zheng K, Wu C, et al. An ensemble method based on selection using bat algorithm for intrusion detection[J]. The Computer Journal, 2018, 61(4): 526-538. |
| 3 | Bhati B S, Chugh G, Al‐Turjman F, et al. An improved ensemble based intrusion detection technique using XGBoost[J]. Transactions on Emerging TeleCommunications Technologies, 2021, 32(6): No.e4076. |
| 4 | Mnih V, Heess N, Graves A, et al. Recurrent models of visual attention[J]. Advances in Neural Information Processing Systems, 2014, 27:1-12. |
| 5 | Ahmad I. Feature selection using particle swarm optimization in intrusion detection[J]. International Journal of Distributed Sensor Networks, 2015, 11(10):No. 806954. |
| 6 | Dickson A, Thomas C. Improved PSO for optimizing the performance of intrusion detection systems[J]. Journal of Intelligent & Fuzzy Systems, 2020, 38(5): 6537-6547. |
| 7 | Aziz M R, Alfoudi A S. Feature selection of the anomaly network intrusion detection based on restoration particle swarm optimization[J]. International Journal of Intelligent Engineering & Systems, 2022, 15(5):592-600. |
| 8 | Wei P, Li Y F, Zhang Z, et al. An optimization method for intrusion detection classification model based on deep belief network[J]. IEEE Access, 2019, 7: 87593-87605. |
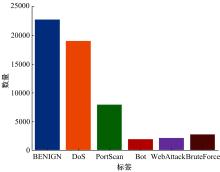
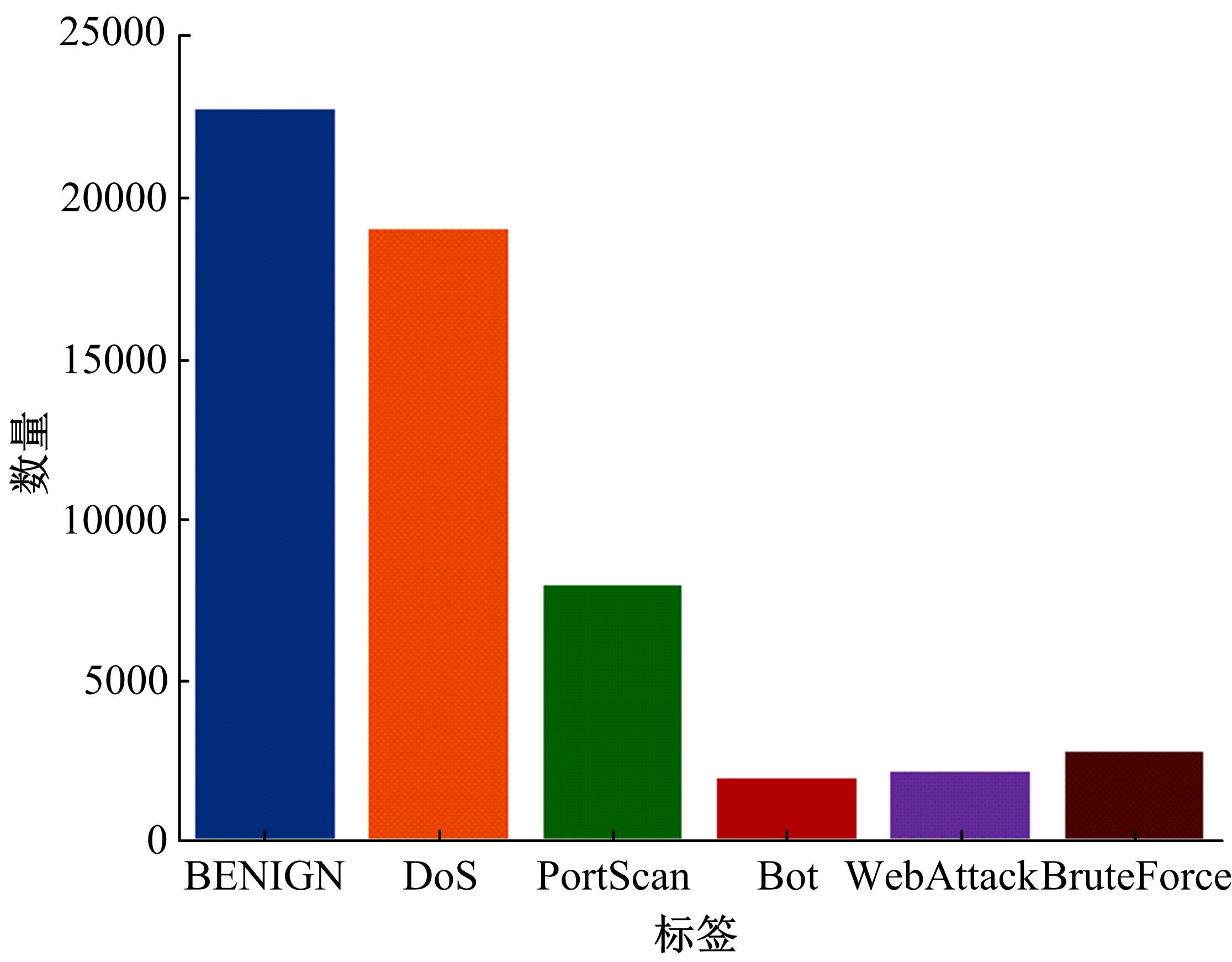
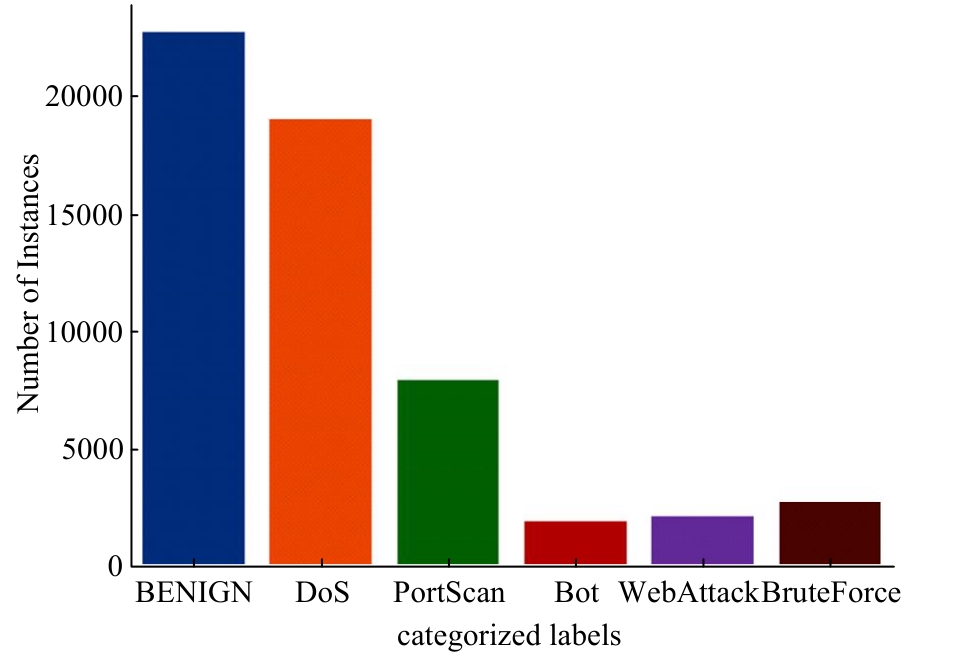
| 9 | Panigrahi R, Borah S. A detailed analysis of CICIDS2017 dataset for designing intrusion detection systems[J]. International Journal of Engineering & Technology, 2018, 7(3): 479-482. |
| 10 | Goryunov M N, Matskevich A G, Rybolovlev D A. Synthesis of a machine learning model for detecting computer attacks based on the Cicids2017 dataset[J]. Proceedings of the Institute for System Programming of the RAS, 2020, 32(5): 81-94. |
| 11 | Stiawan D, Idris M Y B, Bamhdi A M, et al. CICIDS-2017 dataset feature analysis with information gain for anomaly detection[J]. IEEE Access, 2020, 8:132911-132921. |
| 12 | Salo F, Injadat M, Nassif A B, et al. Data mining techniques in intrusion detection systems: a systematic literature review[J]. IEEE Access, 2018, 6: 56046-56058. |
| 13 | Turnipseed I P. A new scada dataset for intrusion detection research[D]. Starkville:James Worth Bagley College of Engineering,Mississippi State University, 2015. |
| 14 | Rastogi A K, Narang N, Siddiqui Z A. Imbalanced big data classification: a distributed implementation of smote[C]∥Proceedings of the Workshop Program of the 19th International Conference on Distributed Computing and Networking, Varanasi, India,2018: 1-6. |
| 15 | Myles A J, Feudale R N, Liu Y, et al. An introduction to decision tree modeling[J]. Journal of Chemometrics: a Journal of the Chemometrics Society, 2004, 18(6): 275-285. |
| 16 | Biau G, Scornet E. A random forest guided tour[J]. Test, 2016, 25: 197-227. |
| 17 | Chen T, He T, Benesty M, et al. Xgboost: extreme gradient boosting(version 0.4-2)[DB/OL]. [2015-12-13]. . |
| 18 | 温博文, 董文瀚, 解武杰, 等. 基于改进网格搜索算法的随机森林参数优化[J]. 计算机工程与应用, 2018, 54(10): 154-157. |
| Wen Bo-wen, Dong Wen-han, Xie Wu-jie, et al. Parameter optimization method for random forest based on improved grid search algorithm[J]. Computer Engineering and Applications,2018,54(10):154-157. | |
| 19 | Pattawaro A, Polprasert C. Anomaly-based network intrusion detection system through feature selection and hybrid machine learning technique[C]∥The 16th International Conference on ICT and Knowledge Engineering(ICT&KE), Bangkok, Thailand, 2018: 1-6. |
| 20 | 李红亚, 彭昱忠, 邓楚燕, 等. GA与PSO的混合研究综述[J]. 计算机工程与应用,2018, 54(2): 20-28. |
| Li Hong-ya, Peng Yu-zhong, Deng Chu-yan, et al. Review of hybrids of GA and PSO[J]. Computer Engineering and Applications, 2018, 54(2):20-28. | |
| 21 | Mohammed M, Mwambi H, Omolo B, et al. Using stacking ensemble for microarray-based cancer classification[C]∥International Conference on Computer, Control, Electrical, and Electronics Engineering, Khartoum, Sudan, 2018: 1-8. |
| 22 | 王辉, 李昌刚.Stacking集成学习方法在销售预测中的应用[J]. 计算机应用与软件, 2020, 37(8): 85-90. |
| Wang Hui, Li Chang-gang. Application of Stacking integrated learning method in sales forecasting[J]. Computer Applications and Software, 2020, 37(8):85-90. | |
| 23 | 张开放, 苏华友, 窦勇. 一种基于混淆矩阵的多分类任务准确率评估新方法[J].计算机工程与科学,2021, 43(11): 1910-1919. |
| Zhang Kai-fang, Su Hua-you, Dou Yong. A new multi-classification task accuracy evaluation method based on confusion matrix[J]. Computer Engineering & Science, 2021, 43(11): 1910-1919. | |
| 24 | Belarbi O, Khan A, Carnelli P, et al. An intrusion detection system based on deep belief networks[C]∥International Conference on Science of Cyber Security,Matsue, Japan, 2022: 377-392. |
| 25 | Yao Y, Su L, Lu Z. DeepGFL: deep feature learning via graph for attack detection on flow-based network traffic[C]∥IEEE Military Communications Conference(MILCOM),Los Angeles, USA, 2018: 579-584. |
| 26 | Roopak M, Tian G Y, Chambers J. Deep learning models for cyber security in IoT networks[C]∥IEEE The 9th Annual Computing and Communication Workshop and Conference, Las Vegas, USA,2019: 452-457. |
| [1] | Yue HOU,Jin-song GUO,Wei LIN,Di ZHANG,Yue WU,Xin ZHANG. Multi-view video speed extraction method that can be segmented across lane demarcation lines [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1692-1704. |
| [2] | Hong-wei ZHAO,Ming-zhu ZHOU,Ping-ping LIU,Qiu-zhan ZHOU. Medical image segmentation based on confident learning and collaborative training [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1675-1681. |
| [3] | Zi-hao SHEN,Yong-sheng GAO,Hui WANG,Pei-qian LIU,Kun LIU. Deep deterministic policy gradient caching method for privacy protection in Internet of Vehicles [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1638-1647. |
| [4] | You-wei WANG,Ao LIU,Li-zhou FENG. New method for text sentiment classification based on knowledge distillation and comment time [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1664-1674. |
| [5] | Tao XU,Shuai-di KONG,Cai-hua LIU,Shi LI. Overview of heterogeneous confidential computing [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(3): 755-770. |
| [6] | Yin-fei DAI,Xiu-zhen ZHOU,Yu-bao LIU,Zhi-yuan LIU. In⁃vehicle network intrusion detection system based on CAN bus data [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(3): 857-865. |
| [7] | Meng-xue ZHAO,Xiang-jiu CHE,Huan XU,Quan-le LIU. A method for generating proposals of medical image based on prior knowledge optimization [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(2): 722-730. |
| [8] | Xiao-dong CAI,Qing-song ZHOU,Yan-yan ZHANG,Yun XUE. Social recommendation based on global capture of dynamic, static and relational features [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(2): 700-708. |
| [9] | Xiang-jiu CHE,Yu-ning WU,Quan-le LIU. A weighted isomorphic graph classification algorithm based on causal feature learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(2): 681-686. |
| [10] | Xiao-ran GUO,Tie-jun WANG,Yue YAN. Entity relationship extraction method based on local attention and local remote supervision [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(1): 307-315. |
| [11] | Hao WANG,Bin ZHAO,Guo-hua LIU. Temporal and motion enhancement for video action recognition [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(1): 339-346. |
| [12] | Yuan-ning LIU,Zi-nan ZANG,Hao ZHANG,Zhen LIU. Deep learning-based method for ribonucleic acid secondary structure prediction [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(1): 297-306. |
| [13] | Lu Li,Jun-qi Song,Ming Zhu,He-qun Tan,Yu-fan Zhou,Chao-qi Sun,Cheng-yu Zhou. Object extraction of yellow catfish based on RGHS image enhancement and improved YOLOv5 network [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(9): 2638-2645. |
| [14] | Hong-wei ZHAO,Hong WU,Ke MA,Hai LI. Image classification framework based on knowledge distillation [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(8): 2307-2312. |
| [15] | Yun-zuo ZHANG,Yu-xin ZHENG,Cun-yu WU,Tian ZHANG. Accurate lane detection of complex environment based on double feature extraction network [J]. Journal of Jilin University(Engineering and Technology Edition), 2024, 54(7): 1894-1902. |
|