吉林大学学报(工学版) ›› 2021, Vol. 51 ›› Issue (2): 659-666.doi: 10.13229/j.cnki.jdxbgxb20191077
• 计算机科学与技术 • 上一篇
一种单服务器环境下的匿名认证协议
- 吉林大学 计算机科学与技术学院,长春 130012
An anonymous authentication protocol for single⁃server architectures
Yi-cheng YU( ),Liang HU,Ling CHI,Jian-feng CHU(
),Liang HU,Ling CHI,Jian-feng CHU( )
)
- College of Computer Science and Technology,Jilin University,Changchun 130012,China
摘要:
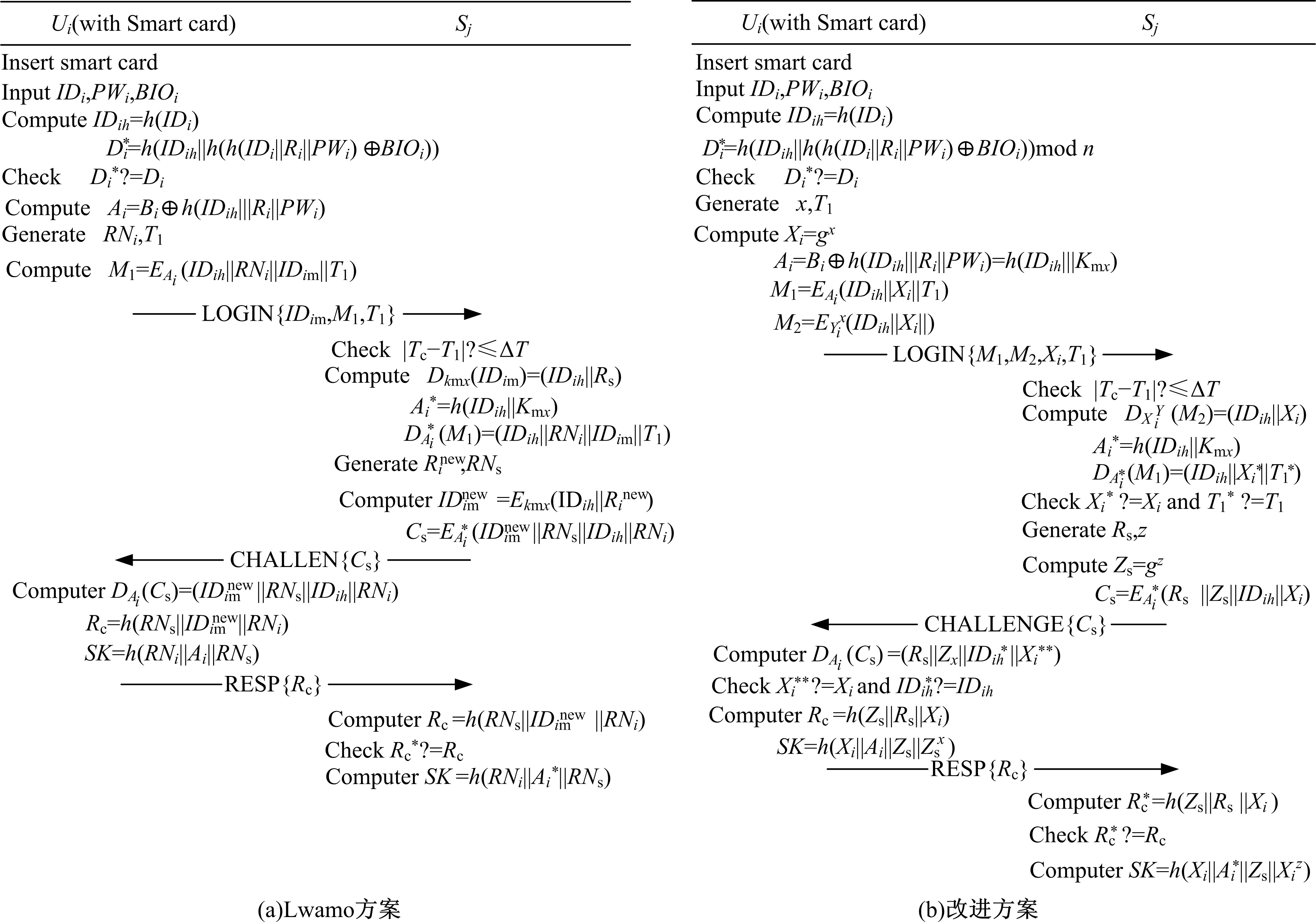
为实现用户与服务器之间安全高效的身份认证,保障双方的通信安全,设计有效的身份认证协议,本文针对Lwamo等提出的协议不能抵御离线口令猜测攻击,且无法实现所声称的用户不可追踪性和前向安全性等安全漏洞,通过使用传统的Diffie-Hellman密钥交换算法和模糊验证技术,提出了改进的适用于单服务环境的匿名认证协议。安全性分析及性能分析表明:改进协议有效解决了上述安全漏洞,能实现安全高效的身份认证。
中图分类号:
- TP309
| 1 | 冯登国. 网络安全原理与技术[M]. 北京: 科学出版化, 2003. |
| 2 | Zhang J, Varadharajan V. Wireless sensor network key management survey and taxonomy[J]. Journal of Network and Computer Applications, 2010, 33(2): 63-75. |
| 3 | Kumari S, Khan M K, Atiquzzaman M. User authentication schemes for wireless sensor networks: a review[J]. Ad Hoc Networks, 2015, 27: 159-194. |
| 4 | Lamport L. Password authentication with insecure communication[J]. Communications of the ACM, 1981, 24(11): 770-772. |
| 5 | 李艳平, 刘小雪, 屈娟, 等.基于智能卡的多服务器远程匿名认证密钥协商协议[J]. 四川大学学报: 工程科学版, 2016, 48(1): 91-98. |
| Li Yan-ping, Liu Xiao-xue, Qu Juan, et al. Multi-server anonymous remote authenticated key agreement protocol based on smart card[J]. Journal of Sichuan University (Engineering Science Edition), 2016, 48(1): 91-98. | |
| 6 | Chen B L, Kuo W C, Wu L C. Robust smart-card-based remote user password authentication scheme[J]. International Journal of Communication Systems, 2014, 27(2): 377-389. |
| 7 | Li X, Niu J, Khan M K, et al. An enhanced smart card based remote user password authentication scheme[J]. Journal of Network and Computer Applications, 2013, 36(5): 1365-1371. |
| 8 | 余宜诚, 胡亮, 迟令, 等. 一种改进的适用于多服务器架构的匿名认证协议[J]. 吉林大学学报: 工学版, 2018, 48(5): 1586-1592. |
| Yu Yi-cheng, Hu Liang, Chi Ling, et al. Improved anonymous authentication protocol for multi-server architectures[J]. Journal of Jilin University (Engineering and Technology Edition), 2018, 48(5): 1586-1592. | |
| 9 | Xie Q, Dong N, Wong D S, et al. Cryptanalysis and security enhancement of a robust two-factor authentication and key agreement protocol[J]. International Journal of Communication Systems, 2016, 29(3): 478-487. |
| 10 | Ratha N K, Connell J H, Bolle R M. Enhancing security and privacy in biometrics-based authentication systems[J]. IBM systems Journal, 2001, 40(3): 614-634. |
| 11 | 屈娟, 冯玉明, 李艳平, 等.可证明安全的面向无线传感器网络的三因素认证及密钥协商方案[J]. 通信学报, 2018, 39(): 189-197. |
| Qu Juan, Feng Yu-ming, Li Yan-ping, et al. Provably secure three-factor authentication and key agreement scheme for wireless sensor network[J]. Journal of Communications, 2018, 39(Sup.2): 189-197. | |
| 12 | Wang C Y, Xu G A, Sun J. An enhanced three-factor user authentication scheme using elliptic curve cryptosystem for wireless sensor networks[J]. Sensors, 2017, 17(12): 17122946. |
| 13 | Giri D, Maitra T. A three factor remote user authentication scheme using collision resist fuzzy extractor in single server environment[C]∥ITM Web of Conferences. EDP Sciences, 2017: 01020. |
| 14 | 丁勇, 胡健, 李亚晖, 等. 基于双线性对的无线传感器网络匿名广播认证协议[J]. 吉林大学学报: 工学版, 2011, 41(2): 468-472. |
| Ding Yong, Hu Jian, Li Ya-hui, et al. Anonymous broadcast authentication protocol for wireless sensor networks based on bilinear pairing[J]. Journal of Jilin University (Engineering and Technology Edition), 2011, 41(2): 468-472. | |
| 15 | Park Y H, Park Y H. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks[J]. Sensors, 2016, 16(12): 2123. |
| 16 | 房卫东, 张武雄, 杨旸, 等.基于生物特征标识的无线传感器网络三因素用户认证协议[J]. 电子学报, 2018, 46(3): 702-713. |
| Fang Wei-dong, Zhang Wu-xiong, Yang Yang, et al. BTh-UAP: biometric-based three-factor user authentication protocol for wireless sensor network[J]. Acta Electronica Sinica, 2018, 46(3): 702-713. | |
| 17 | Lwamo N M R, Zhu L, Xu C, et al. SUAA: a secure user authentication scheme with anonymity for the single & multi-server environments[J]. Information Sciences, 2019, 477: 369-385. |
| 18 | Wang D, Zhang Z, Wang P, et al. Targeted online password guessing: an underestimated threat[C]∥Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, ACM, New York, 2016: 1242-1254. |
| 19 | Wang D, Wang P. On the implications of Zipf's law in passwords[C]∥European Symposium on Research in Computer Security. Cham: Springer, 2016: 111-131. |
| 20 | Wang D, Gu Q, Cheng H, et al. The request for better measurement: a comparative evaluation of two-factor authentication schemes[C]∥Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi'an, China, 2016: 475-486. |
| 21 | 汪定, 李文婷, 王平. 对三个多服务器环境下匿名认证协议的分析[J]. 软件学报, 2018, 29(7): 1937-1952. |
| Wang Ding, Li Wen-ting, Wang Ping. Crytanalysis of three anonymous authentication schemes for multi-server environment[J]. Journal of Software, 2018, 29(7): 1937-1952. |
| [1] | 余宜诚, 胡亮, 迟令, 初剑峰. 一种改进的适用于多服务器架构的匿名认证协议[J]. 吉林大学学报(工学版), 2018, 48(5): 1586-1592. |
| [2] | 赵博, 秦贵和. 高 鲁 棒 性 的 图 像 水 印 算 法[J]. 吉林大学学报(工学版), 2017, 47(1): 249-254. |
| [3] | 王浩, 张晓, 王平, 张鸯. 传感器网络轻量级无证书签名算法及密钥协商机制[J]. 吉林大学学报(工学版), 2014, 44(2): 465-470. |
| [4] | 蔡朝晖, 张健沛, 杨静. 基于贝叶斯网络的路网位置匿名区域估计[J]. 吉林大学学报(工学版), 2014, 44(2): 454-458. |
| [5] | 王波, 杨静, 张健沛. 基于熵分类的个性化隐私匿名方法[J]. 吉林大学学报(工学版), 2013, 43(01): 179-185. |
| [6] | 赵鑫,王晓东. 高效的无线传感器网络自适应广播认证机制[J]. 吉林大学学报(工学版), 2011, 41(03): 758-764. |
| [7] | 丁勇, 胡健, 李亚晖, 王育民. 基于双线性对的无线传感器网络匿名广播认证协议[J]. 吉林大学学报(工学版), 2011, 41(02): 468-0472. |
| [8] | 苗丰满, 张秋余, 袁占亭, 张启坤, 蔡志鹏. 基于格的多信任域认证路径的选择及密码体制[J]. 吉林大学学报(工学版), 2011, 41(02): 463-0467. |
| [9] | 张立斌,单洪颖,苏建,葛淑斌,常化磊. 汽车检测线质量认证评价体系[J]. 吉林大学学报(工学版), 2009, 39(增刊2): 225-0228. |
| [10] | 徐涛,张艳宁 . 基于内容认证的网格模型半脆弱数字水印算法 [J]. 吉林大学学报(工学版), 2008, 38(02): 429-0433. |
| [11] | 曹春杰,杨超,郭渊博,马建峰 . 可证明安全的WLAN Mesh接入认证协议[J]. 吉林大学学报(工学版), 2007, 37(06): 1354-1358. |
| [12] | 赵永哲, 黄声烈, 赵焱, 邢磊. 程序功能的局限性与密码系统[J]. 吉林大学学报(工学版), 2004, (3): 507-511. |
| [13] | 刘卫江, 刘庆怀, 安玉伟. 奇特征正交几何上另一Cartesian认证码的构作[J]. 吉林大学学报(工学版), 2000, 30(01): 63-66. |
|
||