吉林大学学报(工学版) ›› 2021, Vol. 51 ›› Issue (1): 314-322.doi: 10.13229/j.cnki.jdxbgxb20200657
• 计算机科学与技术 • 上一篇
增强OpenStack Swift云存储系统安全功能的方法
- 1.中国人民大学 信息学院,北京 100872
2.中国人民大学 数据工程与知识工程教育部重点实验室,北京 100872
Method to enhance security function of OpenStack Swift cloud storage system
Yuan SONG1,2( ),Dan-yuan ZHOU1,2,Wen-chang SHI1,2(
),Dan-yuan ZHOU1,2,Wen-chang SHI1,2( )
)
- 1.School of Information,Renmin University of China,Beijing 100872,China
2.Key Laboratory of Data Engineering and Knowledge Engineering (Renmin University of China) of Ministry of Education,Beijing 100872,China
摘要:
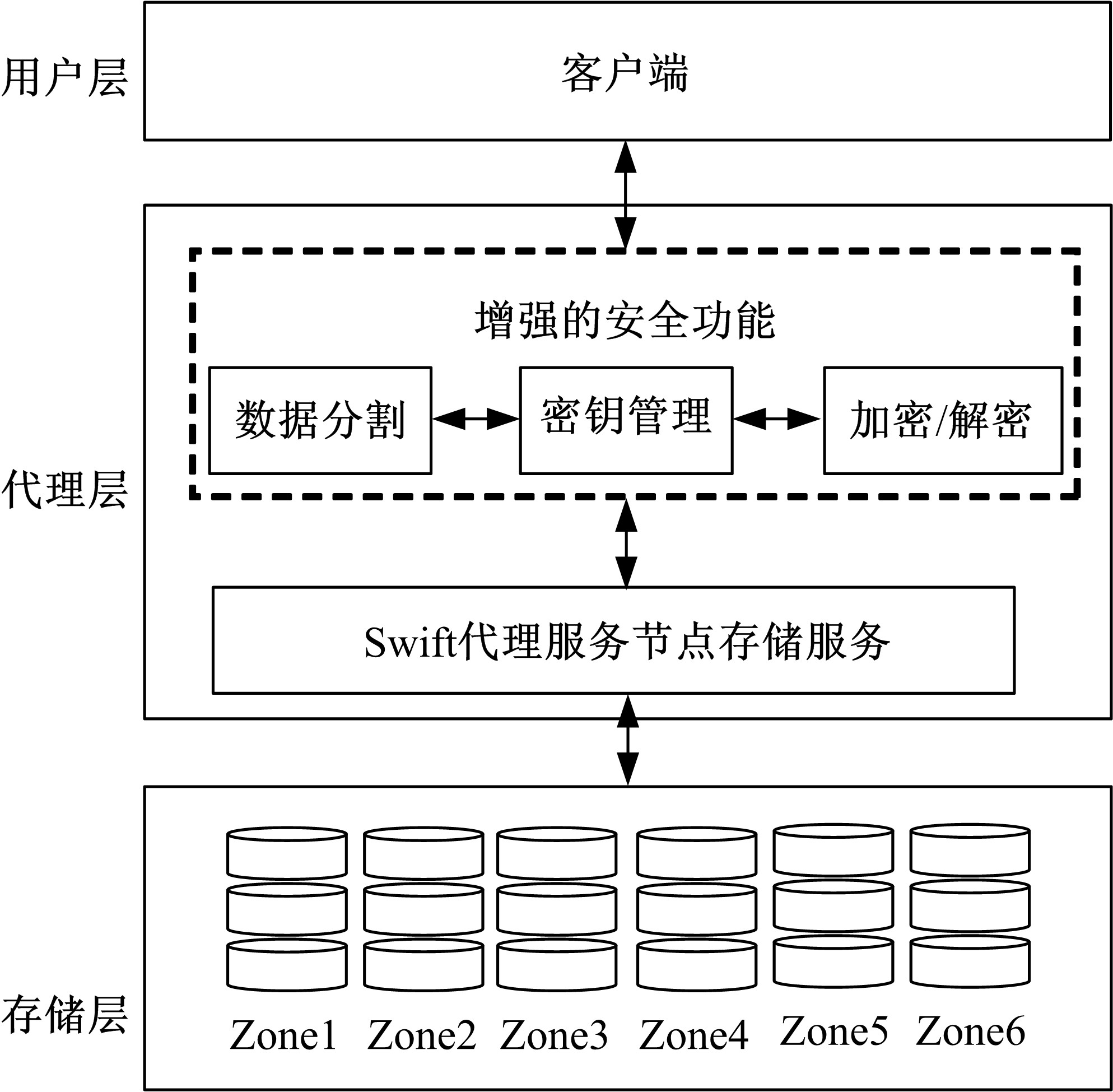
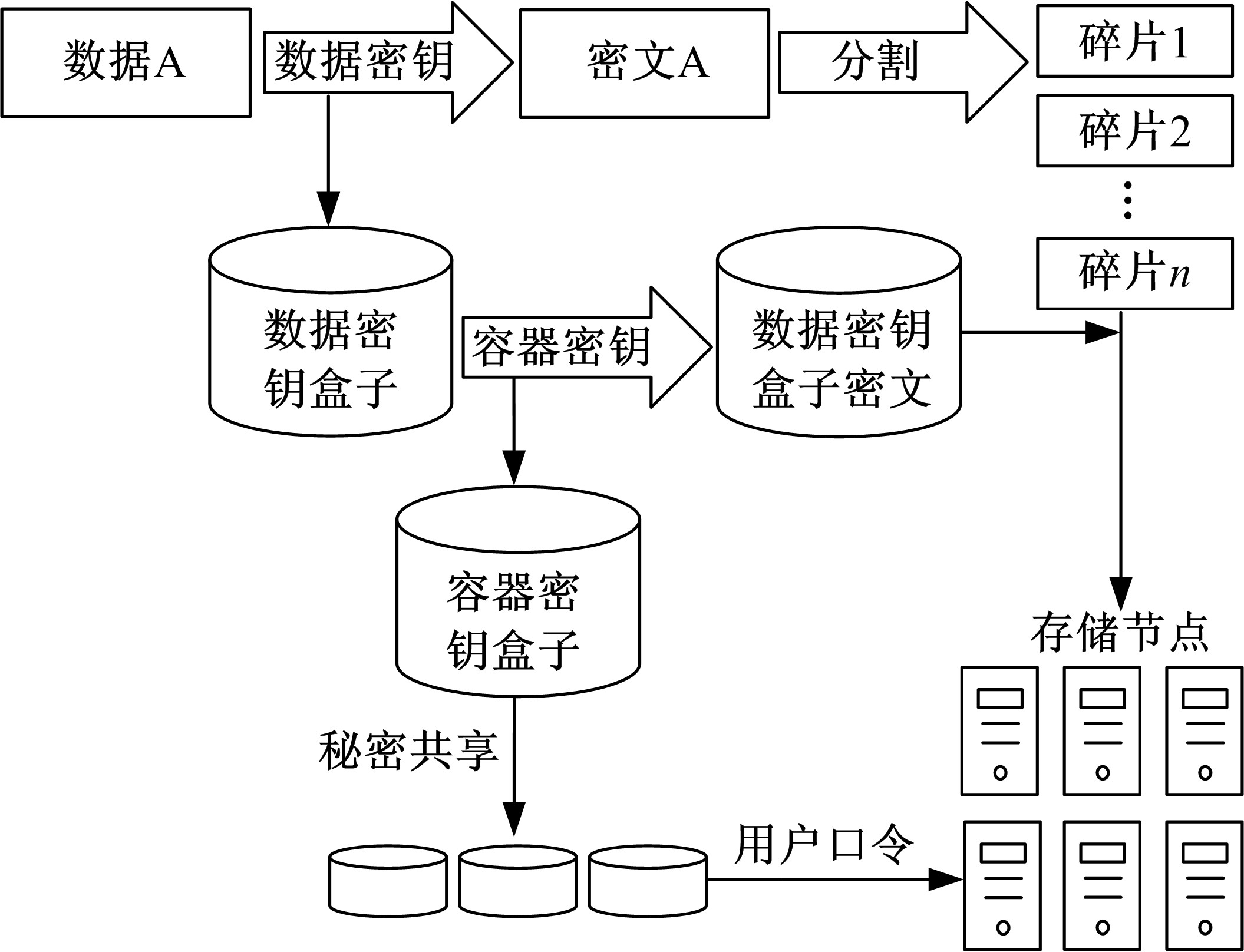
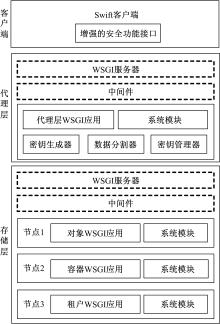
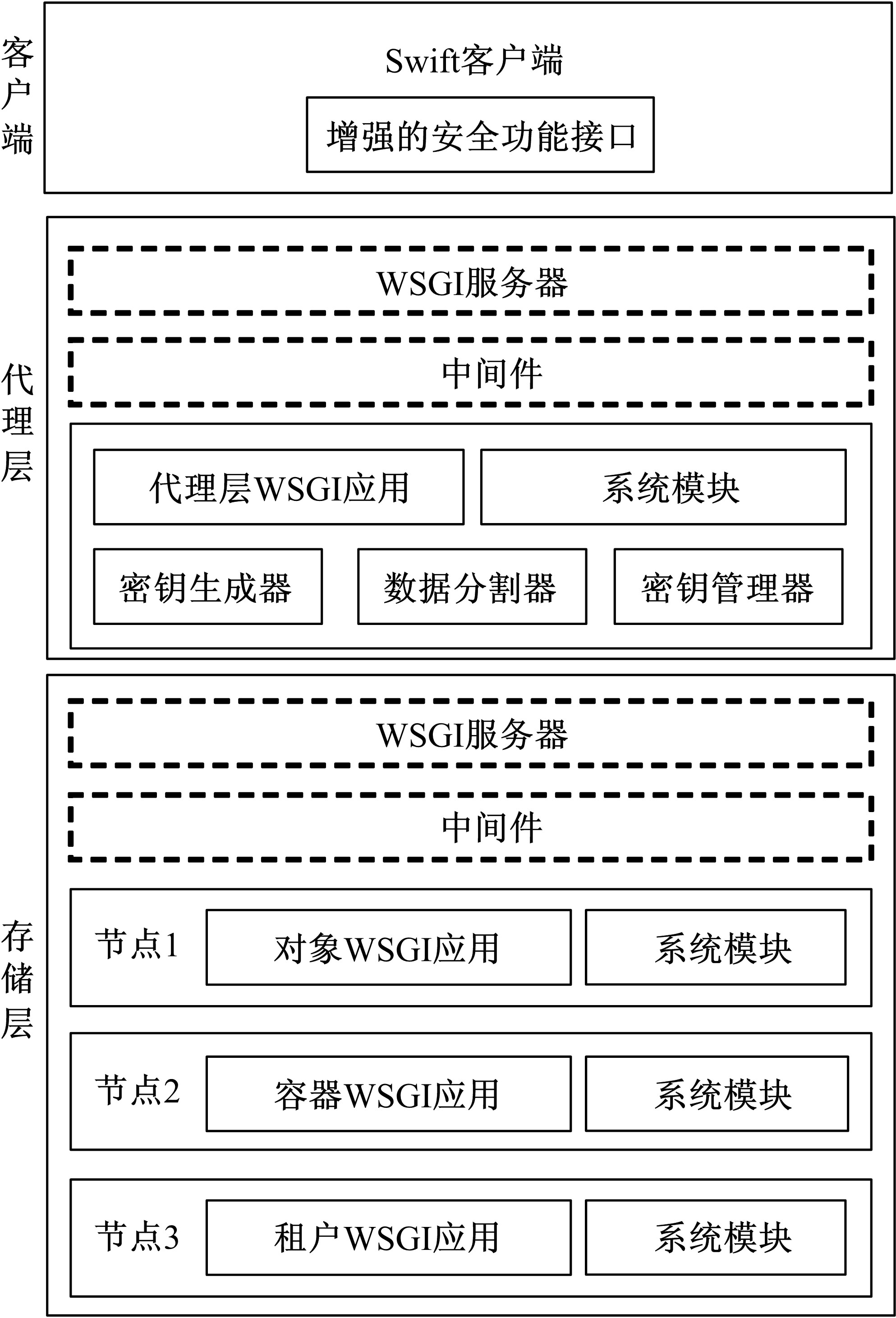
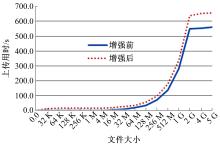
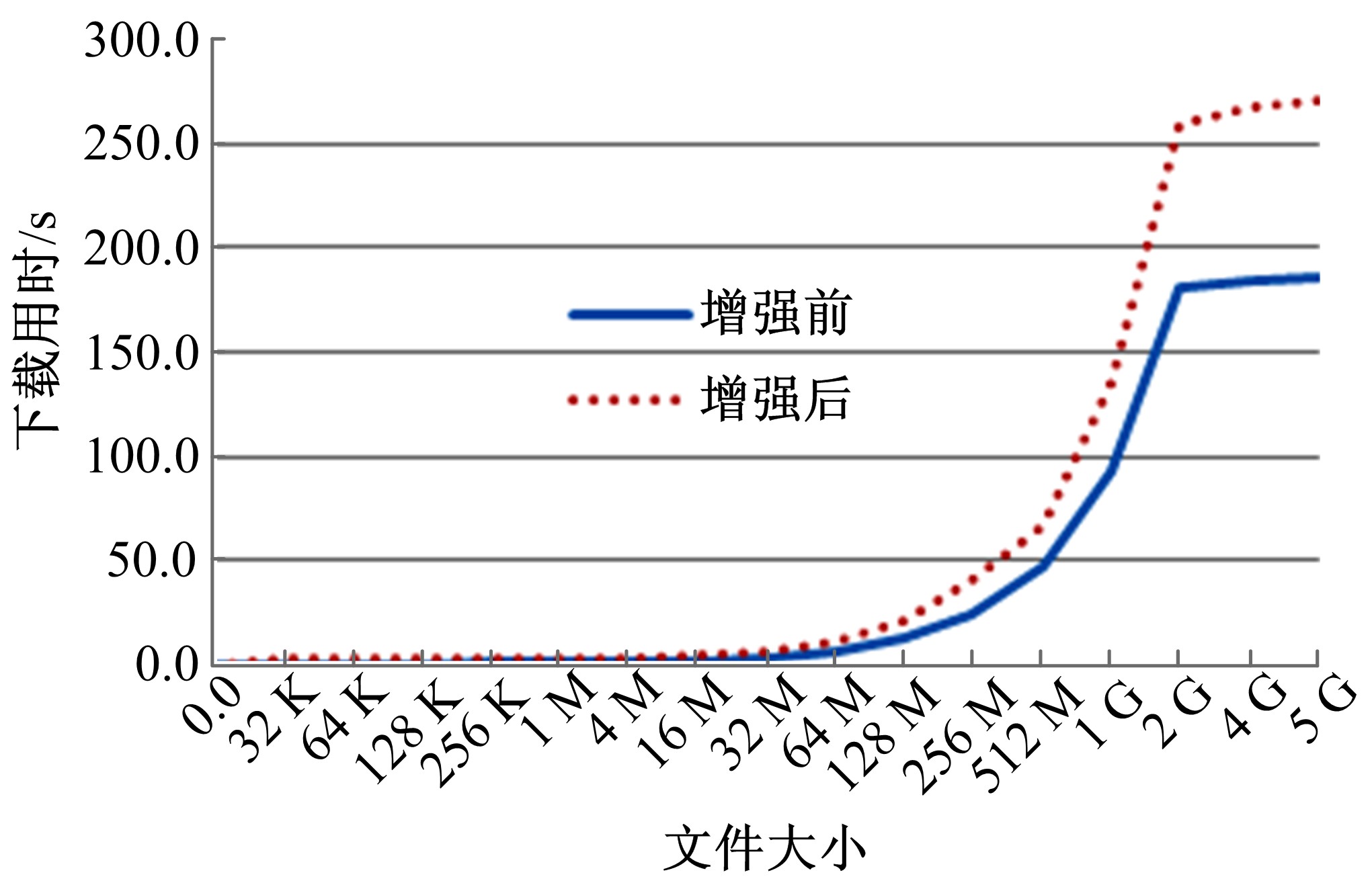
针对OpenStack Swift云存储系统直接且完整地存储用户文件带来的安全风险,为防止攻击者从Swift系统窃取完整的用户文件,本文采用数据分割技术将用户文件分割成若干块,分散存储至不同节点;为防止攻击者利用文件块内容之间的逻辑关系,恢复完整的用户文件,本文采用数据加密技术将分割后的文件以密文形式存储;为防止攻击者窃取密钥恢复用户文件,本文采用用户口令与秘密共享相结合的方式,以用户口令为基础分层级加密存储密钥。实验结果表明,本文方法加大了攻击者获取用户文件的难度,提高了OpenStack Swift云存储系统的安全性,性能开销属于可接受范围。
中图分类号:
- TP309
| 1 | Li J, Zhang Y, Chen X, et al. Secure attribute-based data sharing for resource-limited users in cloud computing[J]. Computers & Security, 2018, 72: 1-12. |
| 2 | Zhang Y, Chen X, Li J, et al. Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing[J]. Information Sciences, 2017, 379: 42-61. |
| 3 | Cloud Security Alliance. Top threats to cloud computing: deep dive [EB/OL]. [2018-08-08]. |
| 4 | OpenStack. OSSA-2015-006: Unauthorized delete of versioned Swift object [EB/OL]. [2015-04-14]. |
| 5 | OpenStack. OSSA-2015-016: Information leak via Swift tempurls [EB/OL]. [2015-08-26]. |
| 6 | OpenStack. OpenStack security notes [EB/OL]. [2020-08-16]. |
| 7 | OpenStack. OpenStack security advisories [EB/OL]. [2020-08-16]. |
| 8 | Common Vulnerabilities and exposures. CVE-ID: CVE-2015-5223 [EB/OL]. [2020-08-16]. |
| 9 | Common vulnerabilities and exposures. CVE-ID: CVE-2016-9590 [EB/OL]. [2020-08-16]. |
| 10 | Shah S Y, Paulovicks B, Zerfos P. Data-at-rest security for Spark[C]∥ IEEE International Conference on Big Data, BigData, Washington DC, USA, 2016: 1464-1473. |
| 11 | Liu Z, Huang Y, Li J, et al. DivORAM: Towards a practical oblivious RAM with variable block size[J]. Information Sciences, 2018, 447: 1-11. |
| 12 | Zhang X, Chen X, Wang J, et al. Verifiable privacy-preserving single-layer perceptron training scheme in cloud computing[J]. Soft Computing, 2018, 22(23): 7719-7732. |
| 13 | Gao C, Cheng Q, He P, et al. Privacy-preserving Naive Bayes classifiers secure against the substitution-then-comparison attack[J]. Information Sciences, 2018, 444: 72-88. |
| 14 | Li P, Li T, Ye H, et al. Privacy-preserving machine learning with multiple data providers[J]. Future Generation Computer Systems, 2018, 87: 341-350. |
| 15 | Albelooshi B, Damiani E, Salah K, et al. Securing Cryptographic Keys in the Cloud: A Survey[J]. IEEE Cloud Computing, 2016, 3(4): 42-56. |
| 16 | AlBelooshi B, Salah K, Martin T, et al. Securing cryptographic keys in the IaaS cloud model[C]∥The 8th IEEE/ACM International Conference on Utility and Cloud Computing, Limassol, Cyprus, 2015: 397-401. |
| 17 | Zerfos P, Yeo H, Paulovicks B D, et al. SDFS: Secure distributed file system for data-at-rest security for Hadoop-as-a-service[C]∥ IEEE International Conference on Big Data, Santa Clara, USA, 2015: 1262-1271. |
| 18 | Zhou J, Duan H, Liang K, et al. Securing outsourced data in the multi-authority cloud with fine-grained access control and efficient attribute revocation[J]. The Computer Journal, 2017, 60(8): 1210-1222. |
| 19 | Shao J, Lu R, Lin X. Fine-grained data sharing in cloud computing for mobile devices[C]∥ IEEE Conference on Computer Communications, Hong Kong, 2015: 2677-2685 |
| 20 | Han S, Han K, Zhang S. A data sharing protocol to minimize security and privacy risks of cloud storage in big data era[J]. IEEE Access, 2019, 7: 60290-60298. |
| 21 | Wang T, Mei Y, Jia W, et al. Edge-based differential privacy computing for sensor-cloud systems[J]. Journal of Parallel and Distributed Computing, 2020, 136: 75-85. |
| 22 | Zheng X, Zhou Y, Ye Y, et al. A cloud data deduplication scheme based on certificateless proxy re-encryption[J]. Journal of Systems Architecture, 2020, 102: 101666. |
| 23 | Rabin M O. Efficient dispersal of information for security, load balancing, and fault tolerance[J]. Journal of the ACM (JACM), 1989, 36(2): 335-348. |
| 24 | Luo W, Shen Q N, Xia Y T, et al. Container-IMA: a privacy-preserving integrity measurement architecture for containers[C]∥ The 22nd International Symposium on Research in Attacks, Intrusions and Defenses, Beijing, China, 2019: 487-500. |
| 25 | Zhang T W, Lee R B. CloudMonatt: an architecture for security health monitoring and attestation of virtual machines in cloud computing [C]∥ Proceedings of the 42nd Annual International Symposium on Computer Architecture, Portland, USA, 2015: 362-374. |
| 26 | Shamir A. How to share a secret [J]. Communications of the ACM, 1979, 22(11): 612-613. |
| 27 | Wang W, Li Z, Owens R, et al. Secure and efficient access to outsourced data[C]∥ Proceedings of the first ACM Cloud Computing Security Workshop, Chicago, USA, 2009: 55-66. |
| [1] | 车翔玖,董有政. 基于多尺度信息融合的图像识别改进算法[J]. 吉林大学学报(工学版), 2020, 50(5): 1747-1754. |
| [2] | 金顺福,郄修尘,武海星,霍占强. 基于新型休眠模式的云虚拟机分簇调度策略及性能优化[J]. 吉林大学学报(工学版), 2020, 50(1): 237-246. |
| [3] | 赵伟, 曲慧雁. 基于云计算Map-Reduce模型的快速碰撞检测算法[J]. 吉林大学学报(工学版), 2016, 46(2): 578-584. |
| [4] | 胡冠宇, 乔佩利. 基于云群的高维差分进化算法及其在网络安全态势预测上的应用[J]. 吉林大学学报(工学版), 2016, 46(2): 568-577. |
| [5] | 李琦,马建峰,熊金波,张涛,刘西蒙. 云中基于常数级密文属性基加密的访问控制机制[J]. 吉林大学学报(工学版), 2014, 44(3): 788-794. |
| [6] | 刘国奇, 刘慧, 高宇, 刘莹, 朱志良. 基于效用的云计算动态资源计费策略[J]. 吉林大学学报(工学版), 2013, 43(06): 1631-1637. |
| [7] | 佟金, 王亚辉, 樊雪梅, 张书军, 陈东辉. 生鲜农产品冷链物流状态监控信息系统[J]. 吉林大学学报(工学版), 2013, 43(06): 1707-1711. |
| [8] | 杨庆芳, 梅朵, 韩振波, 张彪. 基于云计算的蚁群算法求解城市路网最短路径[J]. 吉林大学学报(工学版), 2013, 43(05): 1210-1214. |
| [9] | 孟超, 孙知信, 刘三民. 基于云计算的病毒多执行路径[J]. 吉林大学学报(工学版), 2013, 43(03): 718-726. |
| [10] | 张华, 彭来湖, 胡旭东, 王献美. 一种应用于纺织加工业的企业云制造模型[J]. 吉林大学学报(工学版), 2012, 42(增刊1): 337-340. |
| [11] | 陈龙, 李俊中. 支持不同粒度运算的远程数据完整性验证[J]. 吉林大学学报(工学版), 2012, 42(增刊1): 295-299. |
| [12] | 聂雄丁, 韩德志, 毕坤. 云计算数据安全[J]. 吉林大学学报(工学版), 2012, 42(增刊1): 332-336. |
| [13] | 郭平, 但光祥. 云计算中的混合加密算法[J]. 吉林大学学报(工学版), 2012, 42(增刊1): 327-331. |
| [14] | 胡亮,初剑峰,林宇,王首道,金哲 . 基 于 信 任 服 务 的 IBE 系 统[J]. 吉林大学学报(工学版), 2009, 39(03): 737-0742. |
| [15] | 王巍,马建峰,杨世平,赵文红 . 动态对等群组中高效安全的群组密钥管理方案[J]. 吉林大学学报(工学版), 2008, 38(01): 131-136. |
|
||