吉林大学学报(工学版) ›› 2024, Vol. 54 ›› Issue (4): 1065-1077.doi: 10.13229/j.cnki.jdxbgxb.20220647
• 计算机科学与技术 • 上一篇
基于Tucker分解和双置乱加密的立体图像零水印算法
- 1.中国民航大学 工程技术训练中心,天津 300300
2.天津品源科技有限公司,天津 300300
3.中国民航大学 电子信息与自动化学院,天津 300300
Stereo image zero watermarking algorithm based on Tucker decomposition and double scrambling encryption technology
Shao-cheng HAN1( ),Peng ZHANG2,Huan LIU3,Bo WANG1
),Peng ZHANG2,Huan LIU3,Bo WANG1
- 1.Engineering Technology Training Center,Civil Aviation University of China,Tianjin 300300,China
2.Tianjin Pinyuan Technology Co. ,Ltd,Tianjin 300300,China
3.College of Electronic Information and Automation,Civil Aviation University of China,Tianjin 300300,China
摘要:
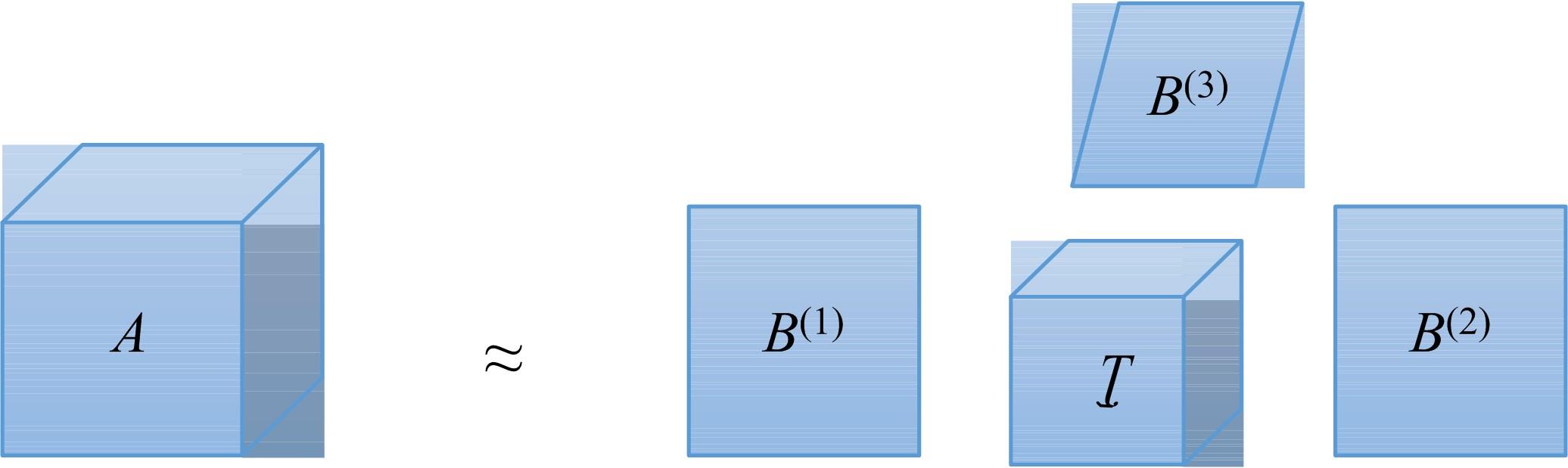
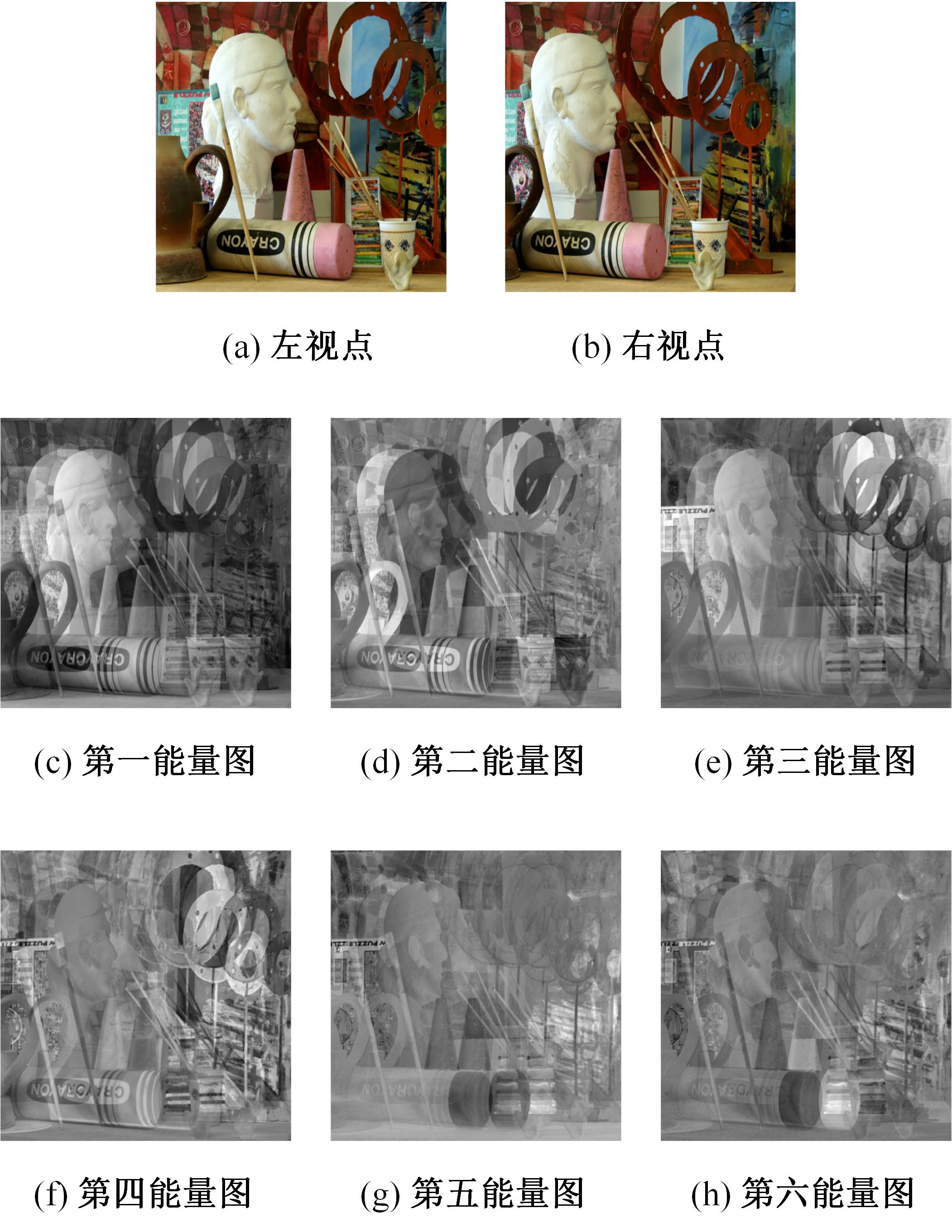
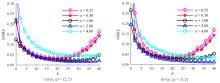
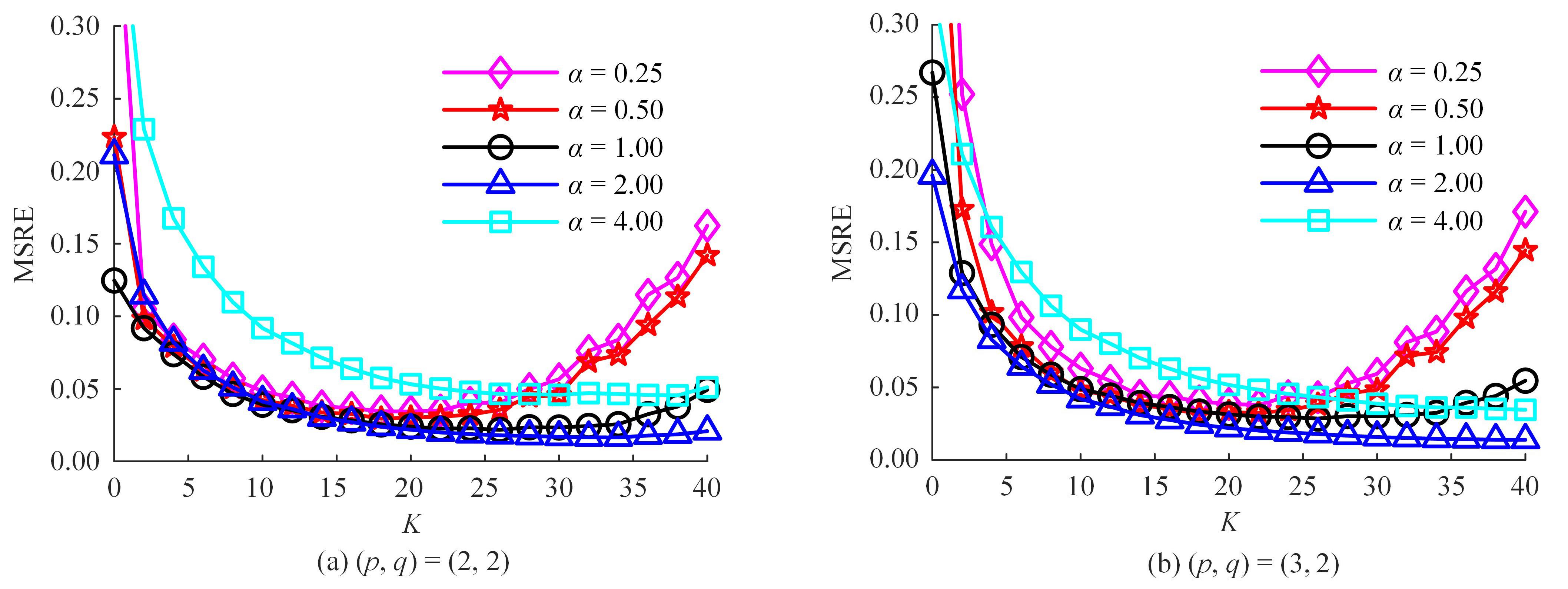
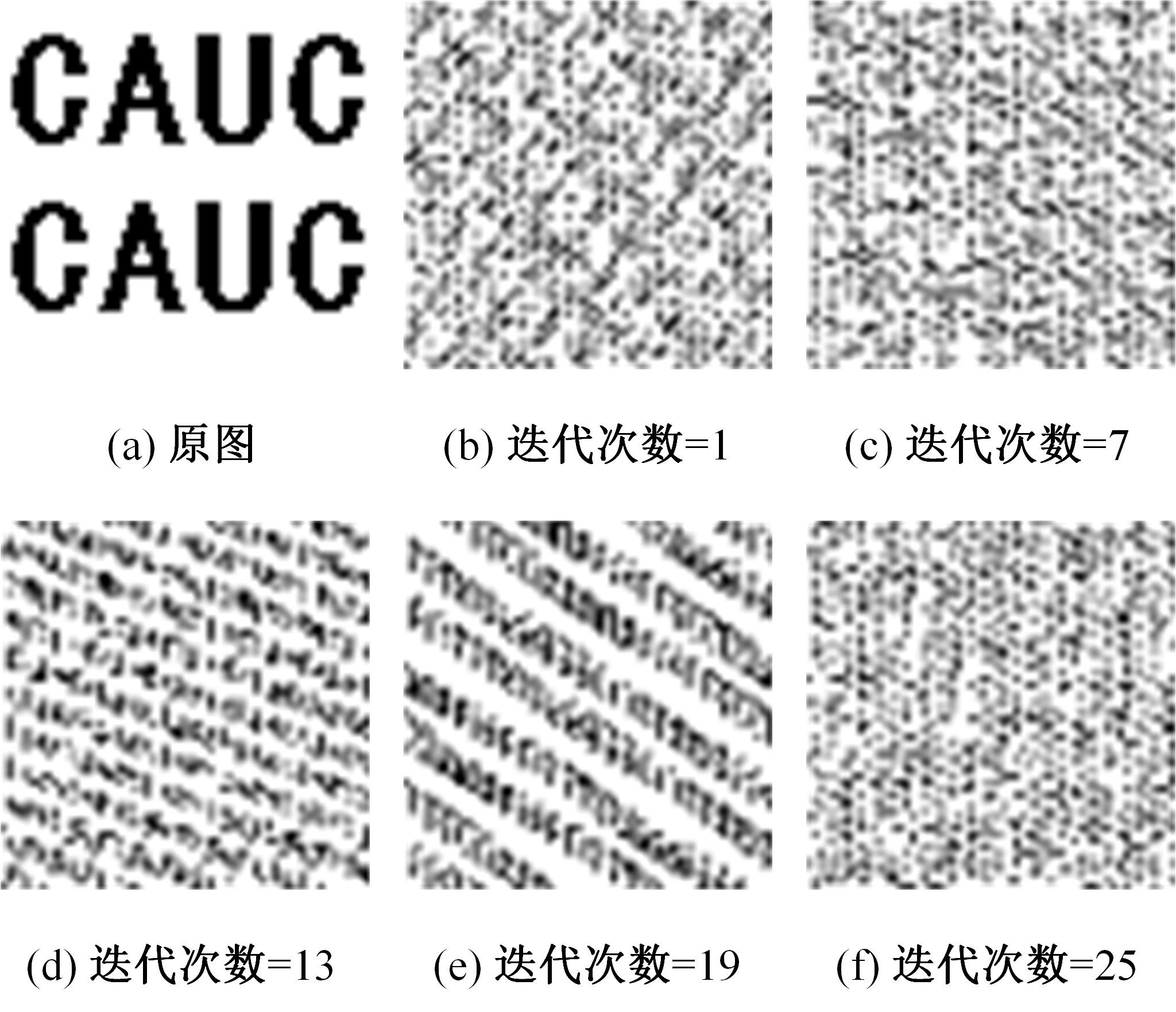
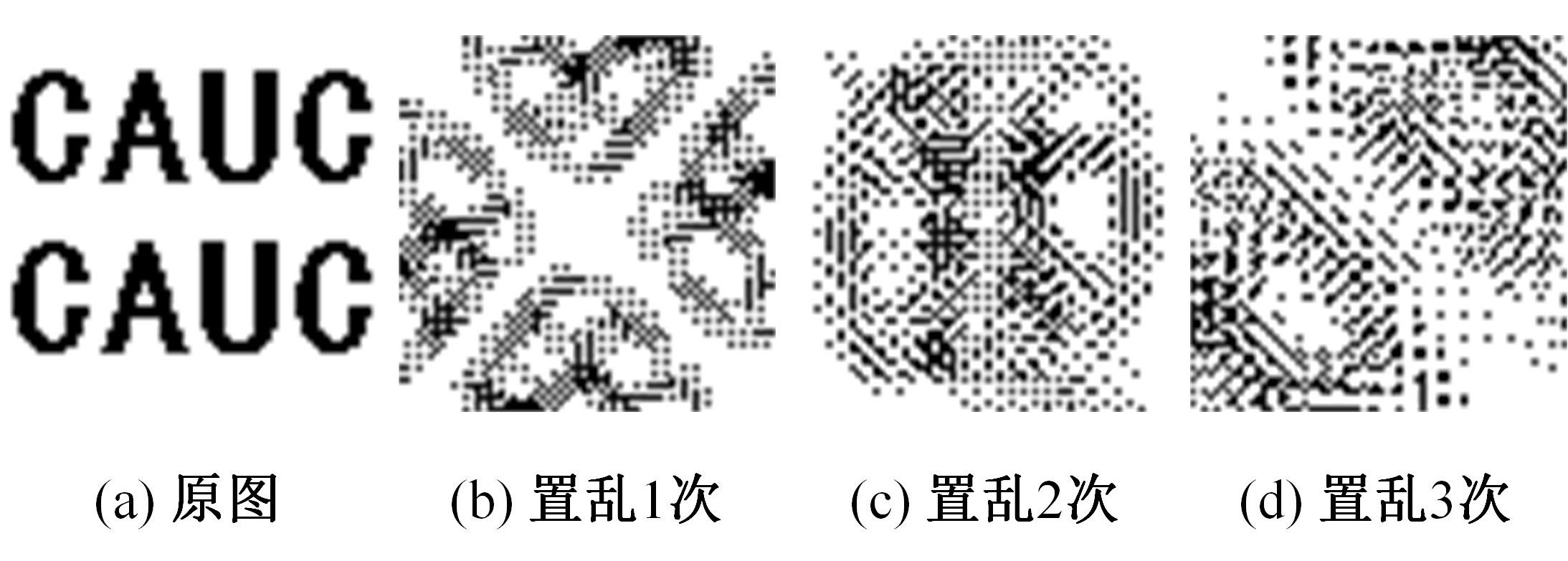
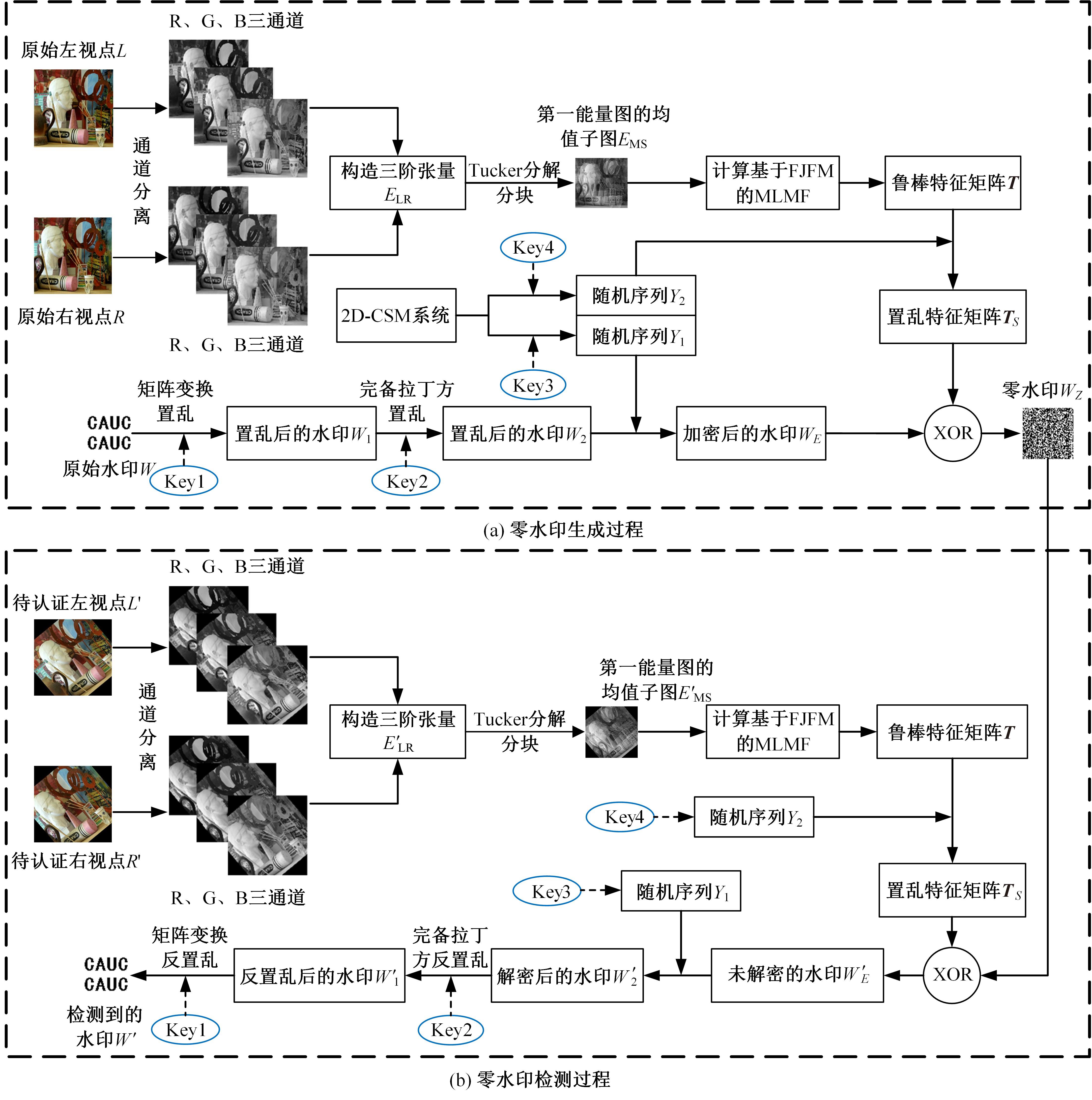
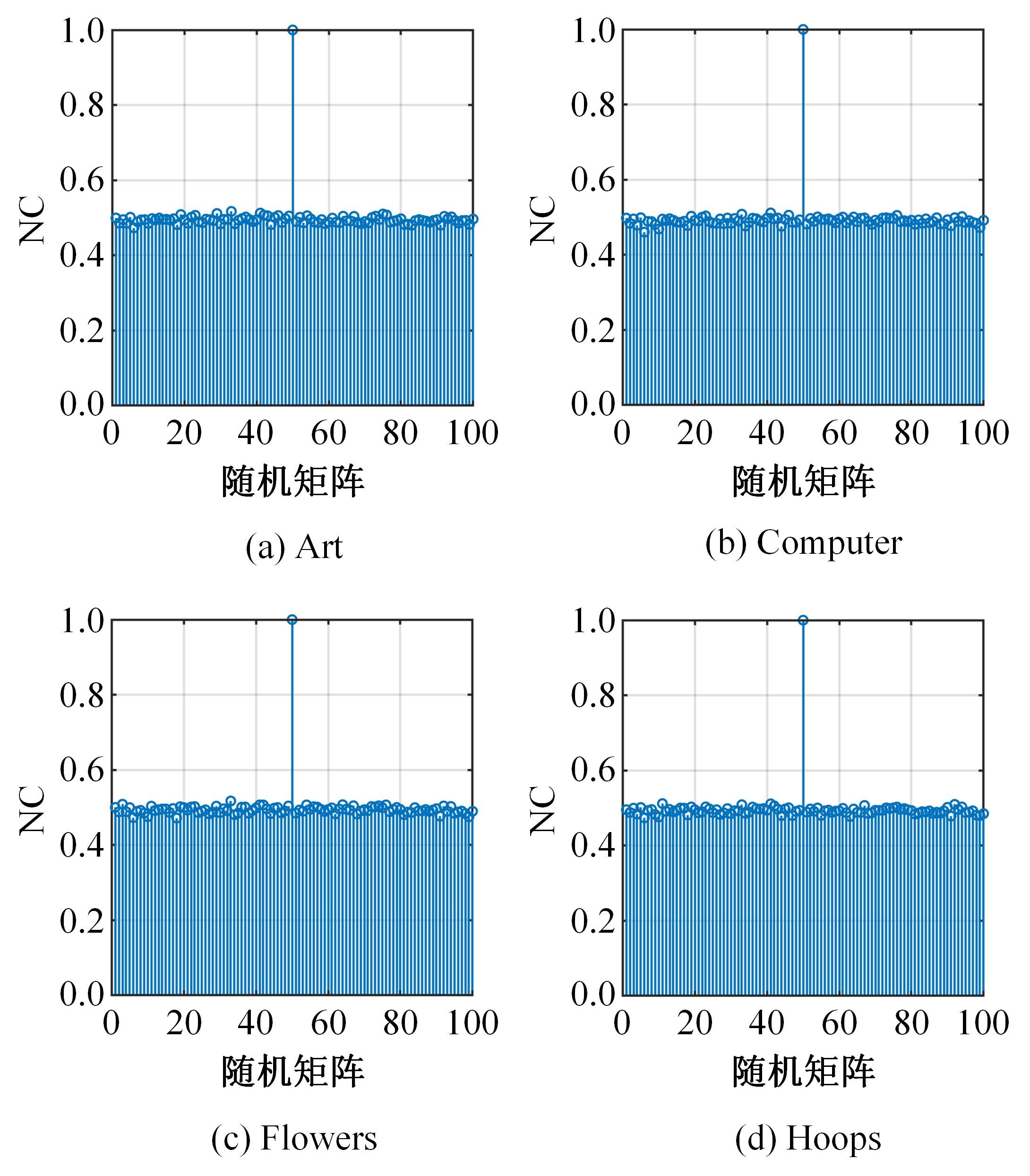
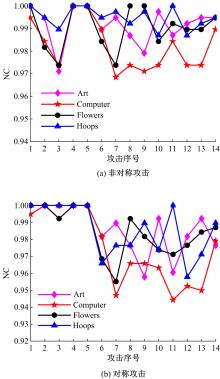
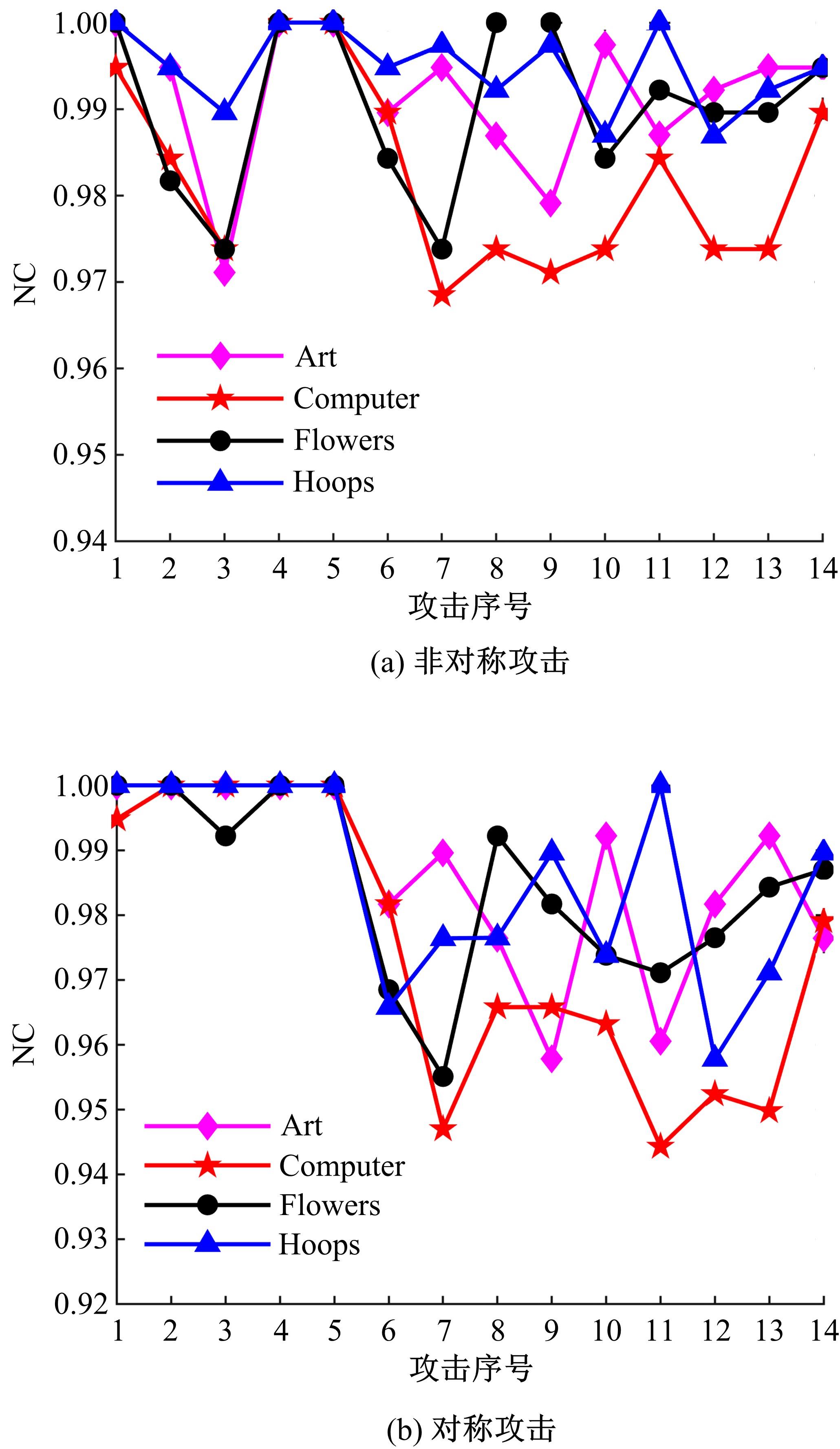
针对立体图像版权保护和现有零水印方案抵御几何攻击鲁棒性能欠佳的问题,提出了一种新的基于Tucker分解和分数阶Jacobi-Fourier矩(FJFM)的彩色立体图像抗几何攻击零水印算法。首先对原始彩色立体图像的左、右视点分别进行R、G、B通道分离,接着将分离后的6个通道联合并视作一个三阶张量进行Tucker分解,获得包含左、右视点相关性的第一能量图;然后计算该能量图4×4非重叠分块后均值子图的FJFM混合低阶矩特征,并利用该特征构造二值鲁棒特征矩阵;最后将经过双重置乱加密后的原始水印和混沌排序置乱后的特征矩阵进行异或操作,得到最终的认证零水印。实验结果表明,本文算法对添加噪声、滤波、压缩等常见非几何攻击均表现出很强的鲁棒性,水印检测NC值均在0.98以上;在抵抗旋转、缩放、平移和剪切几何攻击性能方面整体优于对比算法。
中图分类号:
- TP391
| 1 | Huang Ying, Niu Bao-ning, Guan Hu, et al. Enhancing image watermarking with adaptive embedding parameter and PSNR guarantee[J]. IEEE Transactions on Multimedia, 2019, 21(10):2447-2460. |
| 2 | 温泉, 孙锬锋, 王树勋. 零水印的概念与应用[J]. 电子学报, 2003, 31(2): 214-216. |
| Wen Quan, Sun Tan-feng, Wang Shu-xun. Concept and application of zero-watermark[J]. Chinese Journal of Electronics, 2003, 31(2):214-216. | |
| 3 | Xiong Xiang-guang. A zero watermarking scheme with strong robustness in spatial domain[J]. Acta Automatica Sinica, 2018, 44(1):160-175. |
| 4 | 刘万军, 孙思宇, 曲海成, 等. 一种抗几何旋转攻击零水印算法[J]. 计算机应用研究, 2019, 36(9): 2803-2808. |
| Liu Wan-jun, Sun Si-yu, Qu Hai-cheng, et al. Anti-geometric rotation attack zero watermarking algorithm[J]. Application Research of Computers, 2019, 36(9): 2803-2808. | |
| 5 | Kang Xiao-bing, Lin Guang-feng, Chen Ya-jun, et al. Robust and secure zero-watermarking algorithm for color images based on majority voting pattern and hyper-chaotic encryption[J]. Multimedia Tools and Applications, 2020, 79(1): 1169-1202. |
| 6 | Yang Hong-ying, Qi Shu-ren, Niu Pan-pan, et al. Color image zero-watermarking based on fast quaternion generic polar complex exponential transform[J]. Signal Processing: Image Communication, 2020, 82(5):115747-115765. |
| 7 | 吴德阳, 赵静, 汪国平, 等. 一种基于改进奇异值和子块映射的图像零水印技术[J]. 光学学报, 2020, 40(20):85-97. |
| Wu De-yang, Zhao Jing, Wang Guo-ping, et al. An image zero watermarking technology based on ameliorated singular value and subblock mapping[J]. Acta Optica Sinica, 2020, 40(20): 85-97. | |
| 8 | 张天骐, 叶绍鹏, 柏浩钧, 等. 结合编码交织的频数质心零水印算法[J]. 北京邮电大学学报, 2021,44(5):67-73. |
| Zhang Tian-qi, Ye Shao-peng, Bai Hao-jun, et al. Frequency centroid zero watermarking algorithm combine with coding interleaving[J]. Journal of Beijing University of Posts and Telecommunications, 2021, 44(5):67-73. | |
| 9 | Zhou Wu-jie, Jiang Gang-yi, Yu Mei, et al. Reduced-reference stereoscopic image quality assessment based on view and disparity zero-watermarks[J]. Signal Processing: Image Communication, 2014, 29(1):167-176. |
| 10 | Wang Chun-peng, Wang Xing-yuan, Xia Zhi-qiu, et al. Ternary radial harmonic Fourier moments based robust stereo image zero-watermarking algorithm[J]. Information Sciences, 2019, 470:109-120. |
| 11 | Yamni M, Karmouni H, Sayyouri M, et al. Novel octonion moments for color stereo image analysis[J]. Digital Signal Processing, 2021, 108: 102878-102894. |
| 12 | Wang Chun-peng, Hao Qi-xian, Ma Bin, et al. Octonion continuous orthogonal moments and their applications in color stereoscopic image reconstruction and zero-watermarking[J]. Engineering Applications of Artificial Intelligence, 2021, 106: 104450-104468. |
| 13 | 韩绍程, 张鹏. 基于DOCT和SURF的立体图像零水印算法[J]. 图学学报, 2022, 43(2): 254-262. |
| Han Shao-cheng, Zhang Peng. Stereo image zero watermarking algorithm based on DOCT and SURF[J]. Journal of Graphics, 2022, 43(2): 254-262. | |
| 14 | 韩绍程, 张鹏, 李鹏程. 基于FFST和Hessenberg分解的立体图像零水印算法[J]. 包装工程, 2022, 43(9): 197-206. |
| Han Shao-cheng, Zhang Peng, Li Peng-cheng. Stereo image zero watermarking algorithm based on FFST and Hessenberg decomposition[J]. Packaging Engineering, 2022, 43(9): 197-206. | |
| 15 | Wang Lei, Bai Jing, Wu Jia-qi, et al. Hyperspectral image compression based on lapped transform and Tucker decomposition[J]. Signal Processing: Image Communication, 2015, 36(1):63-69. |
| 16 | 张芳燕, 骆挺, 蒋刚毅,等. 基于左右视点相关性的立体图像鲁棒水印方法[J]. 光电工程, 2018, 45(12):4-14. |
| Zhang Fang-yan, Luo Ting, Jiang Gang-yi, et al. Robust stereo images watermarking based on correlations of left and right views[J]. Opto-Electronic Engineering, 2018, 45(12):4-14. | |
| 17 | Yang Hong-ying, Qi Shu-ren, Tian Jia-lin, et al. Robust and discriminative image representation: Fractional-order Jacobi-Fourier moments[J]. Pattern Recognition, 2021, 115: No. 107898. |
| 18 | 杨刘洋, 吕翔. 一种基于完备拉丁方的图像加密算法[J]. 计算机应用研究, 2015, 32(11):3435-3438. |
| Yang Liu-yang, Xiang Lyu. Image encryption algorithm based on complete Latin square[J]. Application Research of Computers, 2015, 32(11):3435-3438. | |
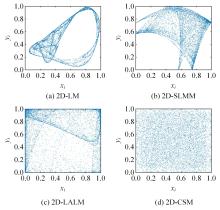
| 19 | Wu Yue, Yang Ge-lan, Jin Hui-xia, et al. Image encryption using the two-dimensional logistic chaotic map[J]. Journal of Electronic Imaging, 2012, 21(1):No. 13014. |
| 20 | Hua Zhong-yun, Zhou Yi-cong, Chi-man Pun, et al. 2D Sine Logistic modulation map for image encryption[J]. Information Sciences, 2015, 297: 80-94. |
| 21 | Madhu S. Image encryption based on a new 2D logistic adjusted logistic map[J]. Multimedia Tools and Applications, 2020, 79(1):355-374. |
| 22 | Daniel S, Chris P. Learning conditional random fields for stereo[C]∥ IEEE Conference on Computer Vision and Pattern Recognition, Minneapolis, USA, 2007:1-8. |
| [1] | 陆文琦,周天,谷远利,芮一康,冉斌. 基于张量分解理论的车道级交通流数据修复算法[J]. 吉林大学学报(工学版), 2021, 51(5): 1708-1715. |
| [2] | 赵岩,孟丽茹,王世刚,陈贺新. 符合人眼视觉感知特性的改进PSNR评价方法[J]. 吉林大学学报(工学版), 2015, 45(1): 309-313. |
| [3] | 沈丽丽, 孟宪茂, 张晶, 高强, 侯春萍. 平面和立体图像的ERP特性研究[J]. 吉林大学学报(工学版), 2013, 43(增刊1): 101-105. |
| [4] | 张春彦, 王世刚, 贾丛新, 孙爱朦, 陈贺新. 基于LED屏的立体图像生成方法[J]. 吉林大学学报(工学版), 2013, 43(增刊1): 394-397. |
| [5] | 孙建国,张国印,门朝光,姚爱红,曹刘娟. 基于分形理论的小波域水印模型[J]. 吉林大学学报(工学版), 2011, 41(01): 203-0208. |
| [6] | 徐涛,张艳宁 . 三维网格模型零水印技术[J]. 吉林大学学报(工学版), 2007, 37(04): 901-904. |
|
||