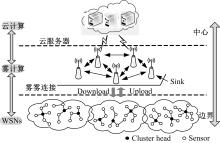
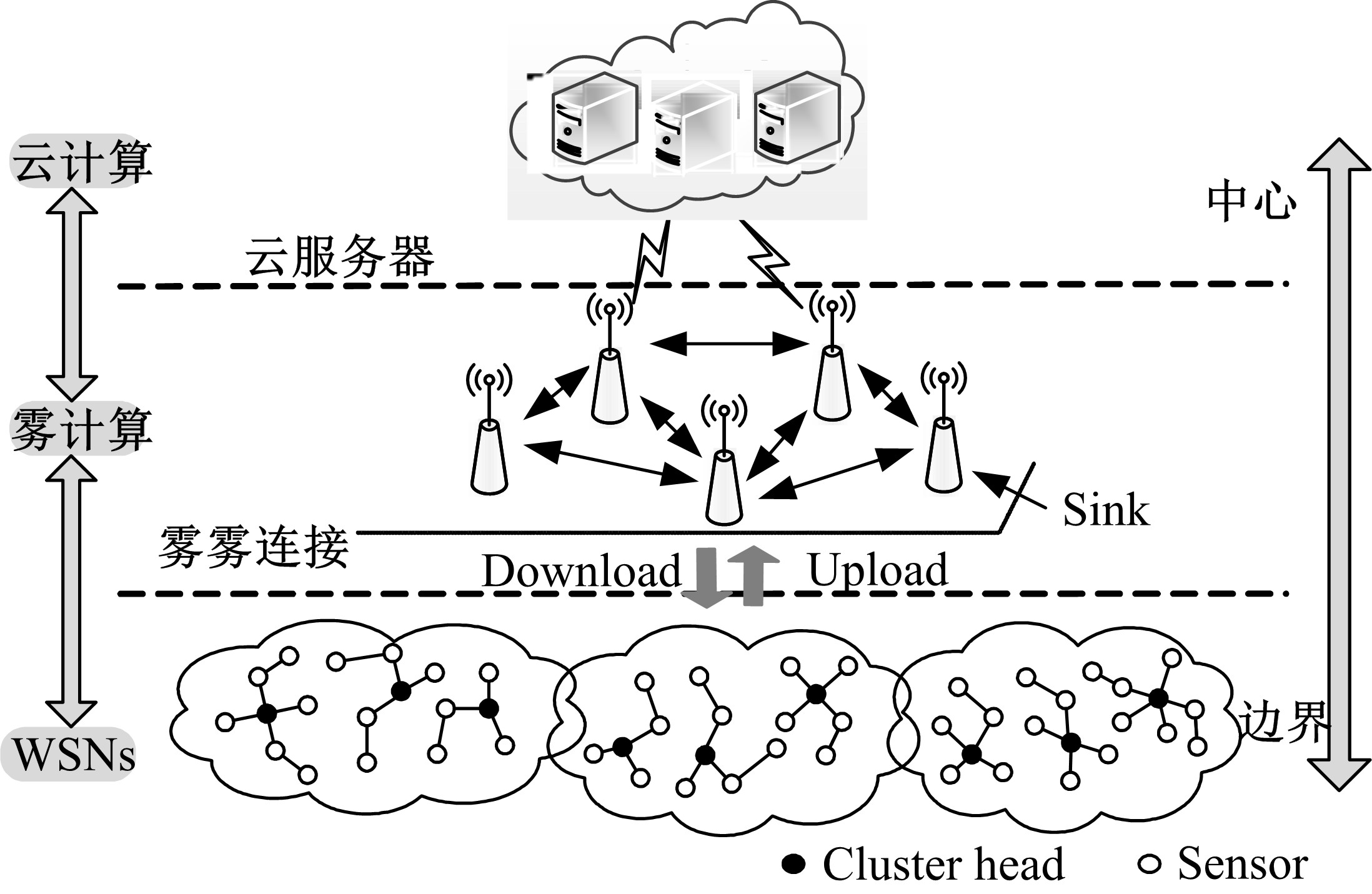
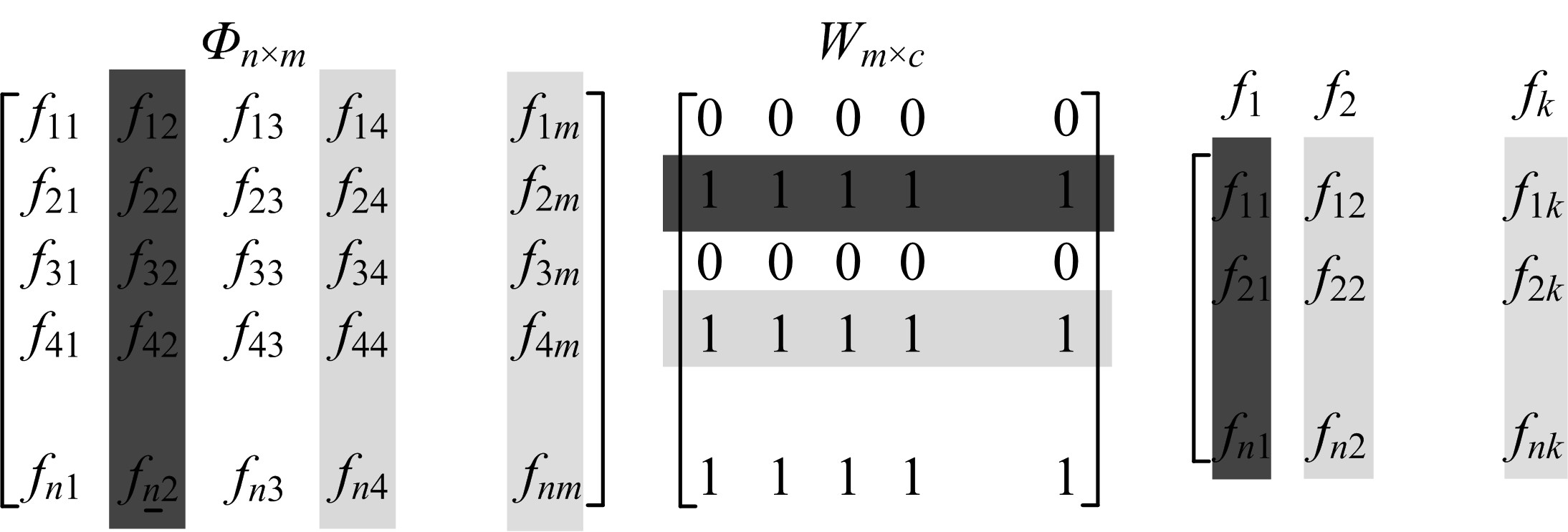
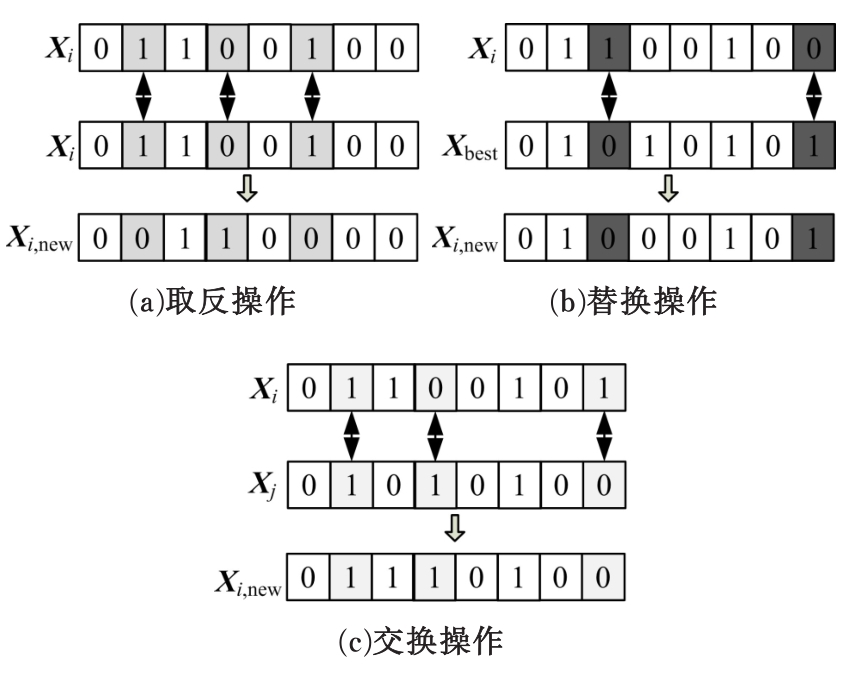
Journal of Jilin University(Engineering and Technology Edition) ›› 2020, Vol. 50 ›› Issue (2): 692-702.doi: 10.13229/j.cnki.jdxbgxb20181170
Sensor cloud intrusion detection based on discrete optimization algorithm and machine learning
Zhou-zhou LIU1,2( ),Wen-xiao YIN3,Qian-yun ZHANG1,Han PENG2
),Wen-xiao YIN3,Qian-yun ZHANG1,Han PENG2
- 1.School of Computer Science, Xi′an Aeronautical University, Xi′an, 710077, China
2.School of Information Science and Engineering, Hebei North University, Zhangjiakou,075000, China
3.School of Computer Science, Northwestern Polytechnical University, Xi′an, 710072, China
CLC Number:
- TP393
| 1 | 曾建电, 王田, 贾维嘉, 等. 传感云研究综述[J]. 计算机研究与发展, 2017, 54( 5): 925- 939. |
| Zeng Jian-dian, Wang Tian, Jia Wei-jia, et al. A survey on sensor-cloud[J]. Journal of Computer Research and Development, 2017, 54( 5): 925- 939. | |
| 2 | 应时彦, 汤顺. 基于节点位置动态变化的无线传感网络路由协议[J]. 吉林大学学报: 工学版, 2011, 41( 增刊1): 309- 313. |
| Ying Shi-yan, Tang Shun. Routing protocol of wsn in terms of dynamic changes of node location[J]. Journal of Jilin University (Engineering and Technology Edition), 2011, 41( Sup.1): 309- 313. | |
| 3 | Yuriyama M, Kushida T. Sensor-cloud infrastructure physical sensor management with virtualized sensors on cloud computing[C]∥ Proc of the 13th International Conference On Network-Based Information Systems. Washington, DC: IEEE Computer Society, 2010: 1- 8. |
| 4 | Madria S, Kumar V, Dalvi R. Sensor cloud: a cloud of virtual sensors[J]. IEEE Software, 2014, 31( 2): 70- 77. |
| 5 | Wang T, Bhuiyan M Z, Wang G J, et al. Big data reduction for smart city’s critical infrastructural health monitoring[J]. IEEE Communications Magazine, 2018, 56( 3): 128- 133. |
| 6 | Elhag S, Fernandez A, Bawakid A, et al. On the combination of genetic fuzzy systems and pair-wise learning for improving detection rates on intrusion detection systems[J]. Expert Systems with Applications, 2015, 42( 1): 193- 202. |
| 7 | Qing Y L, Information Technology Co, LTD. YeeLink[EB/OL].[ 2018-11-26]. |
| 8 | 杜晔, 张亚丹, 黎妹红, 等. 基于改进FastICA算法的入侵检测样本数据优化方法[J]. 通信学报, 2016, 37( 1): 42- 48. |
| Du Ye, Zhang Ya-dan, Li Mei-hong, et al. Improved FastICA algorithm for data optimization processing in intrusion detection[J]. Journal on Communicaitons, 2016, 37( 1): 42- 48. | |
| 9 | Zhao Z, Wang L, Liu H, et al. On similarity preserving feature selection[J]. IEEE Trans on Knowledge and Data Engineering, 2013, 25( 3): 619- 632. |
| 10 | 王珺, 卫金茂, 张璐. 基于保留分类信息的多任务特征学习算法[J]. 计算机研究与发展, 2017, 54( 3): 537- 548. |
| Wang Jun, Wei Jin-mao, Zhang Lu. Multi-task feature learning algorithm based on preserving classification information[J]. Journal of Computer Research and Development, 2017, 54( 3): 537- 548. | |
| 11 | 孙广路, 宋智超, 刘金来, 等. 基于最大信息系数和近似马尔科夫毯的特征选择方法[J]. 自动化学报, 2017, 43( 5): 795- 805. |
| Sun Guang-lu, Song Zhi-chao, Liu Jin-lai, et al. Feature selection method based on maximum information coefficient and approximate Markov blanket[J]. Acta Automatica Sinica, 2017, 43( 5): 795- 805. | |
| 12 | 仇利克, 郭忠文, 刘青, 等. 基于冗余分析的特征选择算法[J]. 北京邮电大学学报, 2017, 40( 1): 36- 41. |
| Qiu Li-ke, Guo Zhong-wen, Liu Qing, et al. Feature selection algorithm based on redundancy analysis[J]. Journal of Beijing University of Posts and Telecommunications, 2017, 40( 1): 36- 41. | |
| 13 | 唐成华, 六鹏程, 汤申生, 等. 基于特征选择的模糊聚类异常行为检测[J]. 计算机研究与发展, 2015, 52( 3): 718- 728. |
| Tang Cheng-hua, Liu Peng-cheng, Tang Shen-sheng, et al. Anomaly intrusion behavior detection based on fuzzy clustering and features selection[J]. Journal of Computer Research and Development, 2015, 52( 3): 718- 728. | |
| 14 | Nayak J, Naik B, Kanungo D P, et al. A hybrid elicit teaching learning based optimization with fuzzy C-means(ETLBO-FCM) algorithm for data clustering [J]. Ain Shams Engineering Journal, 2018, 9( 3): 379- 393. |
| 15 | Ma A, Zhong Y F, Zhang L P. Adaptive multiplicative meme-tic fuzzy clustering algorithm for remote sensing imagery[J]. IEEE Trans on Geoscience and Remote Sensing, 2015, 53( 8): 4202- 4217. |
| 16 | 刘洲洲, 王福豹. 改进的离散混合蛙跳算法压缩感知信号重构及应用[J]. 吉林大学学报: 工学版, 2016, 46( 4): 1261- 1268. |
| Liu Zhou-zhou, Wang Fu-bao. Improvement of discrete shuffled frog-leaping algorithm and application in compressed sensing reconstruction[J]. Journal of Jilin University (Engineering and Technology Edition), 2016, 46( 4): 1261- 1268. | |
| 17 | 刘洲洲, 彭寒. 基于节点可靠度的无线传感器网络拓扑控制算法[J]. 吉林大学学报: 工学版, 2018, 48( 2): 571- 577. |
| Liu Zhou-zhou, Peng Han. Topology control algorithm based on node reliability in WSN[J]. Journal of Jilin University (Engineering and Technology Edition), 2018, 48( 2): 571- 577. | |
| 18 | 吴丽云, 李生林, 甘旭升, 等. 基于PLS特征提取的网络异常入侵检测CVM模型[J]. 控制与决策, 2017, 32( 4): 755- 758. |
| Wu Li-yun, Li Sheng-lin, Gan Xu-sheng, et al. Network anomaly intrusion detection CVM model based on PLS feature extraction[J]. Control and Decision, 2017, 32( 4): 755- 758. |
| [1] | Man CHEN,Yong ZHONG,Zhen-dong LI. Multi-focus image fusion based on latent low⁃rank representation combining low⁃rank representation [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 297-305. |
| [2] | Shun-fu JIN,Xiu-chen QIE,Hai-xing WU,Zhan-qiang HUO. Clustered virtual machine allocation strategy in cloud computing based on new type of sleep-mode and performance optimization [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 237-246. |
| [3] | Xiao-dong ZHANG,Xiao-jun XIA,Hai-feng LYU,Xu-chao GONG,Meng-jia LIAN. Dynamic load balancing of physiological data flow in big data network parallel computing environment [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 247-254. |
| [4] | Xiao-hui WANG,Lu-shen WU,Hua-wei CHEN. Denoising of scattered point cloud data based on normal vector distance classification [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 278-288. |
| [5] | Jun-yi DENG,Yan-heng LIU,Shi FENG,Rong-cun ZHAO,Jian WANG. GSPN⁃based model to evaluate the performance and securi tytradeoff in Ad-hoc network [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 255-261. |
| [6] | Tie-jun WANG,Wei-lan WANG. Thangka image annotation based on ontology [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 289-296. |
| [7] | Xiong-fei LI,Jing WANG,Xiao-li ZHANG,Tie-hu FAN. Multi-focus image fusion based on support vector machines and window gradient [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 227-236. |
| [8] | Hong-yan WANG,He-lei QIU,Jia ZHENG,Bing-nan PEI. Visual tracking method based on low⁃rank sparse representation under illumination change [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 268-277. |
| [9] | Xiang-jiu CHE,Hua-luo LIU,Qing-bin SHAO. Fabric defect recognition algorithm based onimproved Fast RCNN [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2038-2044. |
| [10] | Bing-hai ZHOU,Qiong WU. Balancing and optimization of robotic assemble lines withtool and space constraint [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2069-2075. |
| [11] | You ZHOU,Sen YANG,Da-lin LI,Chun-guo WU,Yan WANG,Kang-ping WANG. Acceleration platform for face detection and recognition based on field⁃programmable gate array [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2051-2057. |
| [12] | Hong-wei ZHAO,Peng WANG,Li-li FAN,Huang-shui HU,Ping-ping LIU. Similarity retention instance retrieval method [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2045-2050. |
| [13] | Jun SHEN,Xiao ZHOU,Zu-qin JI. Implementation of service dynamic extended network and its node system model [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2058-2068. |
| [14] | Bin LI,Xu ZHOU,Fang MEI,Shuai-ning PAN. Location recommendation algorithm based on K-means and matrix factorization [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(5): 1653-1660. |
| [15] | Bin LI,Guo⁃jun SHEN,Geng SUN,Ting⁃ting ZHENG. Improved chicken swarm optimization algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(4): 1339-1344. |
|
||