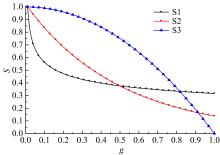
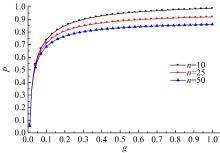
Journal of Jilin University(Engineering and Technology Edition) ›› 2020, Vol. 50 ›› Issue (1): 255-261.doi: 10.13229/j.cnki.jdxbgxb20181286
Previous Articles Next Articles
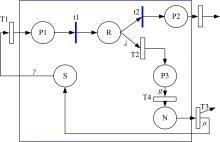
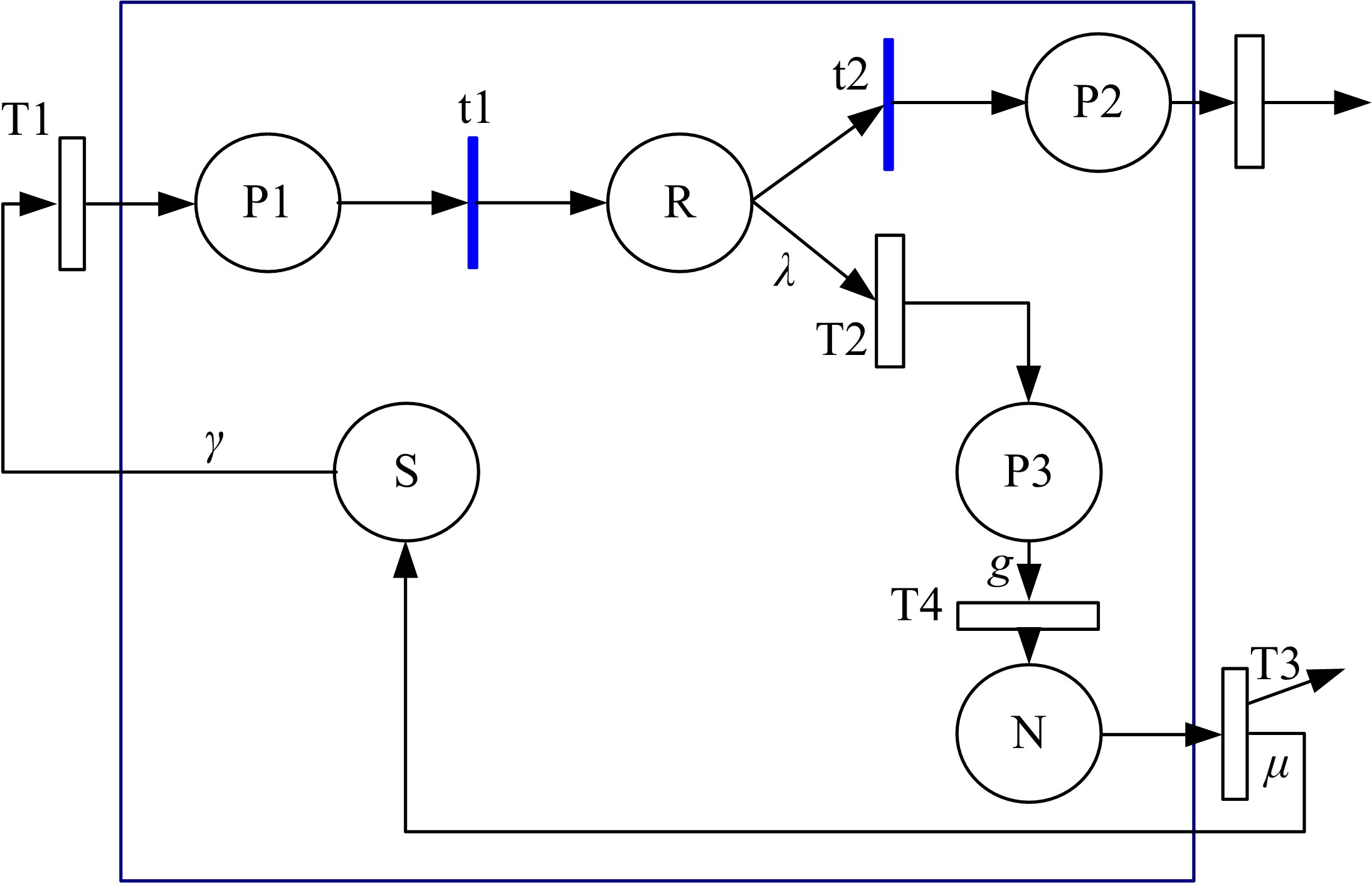
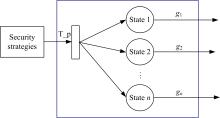
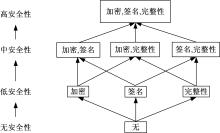
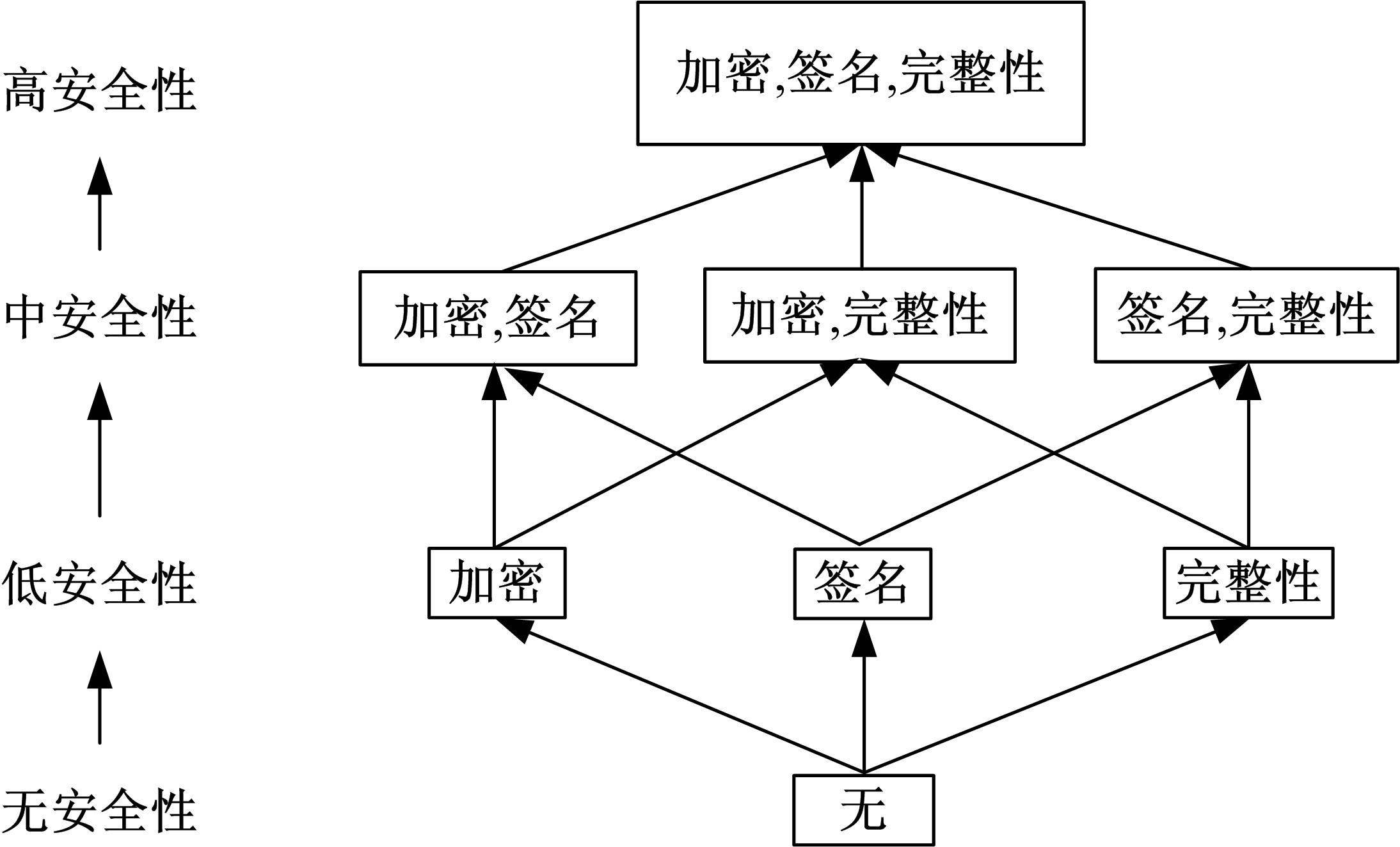
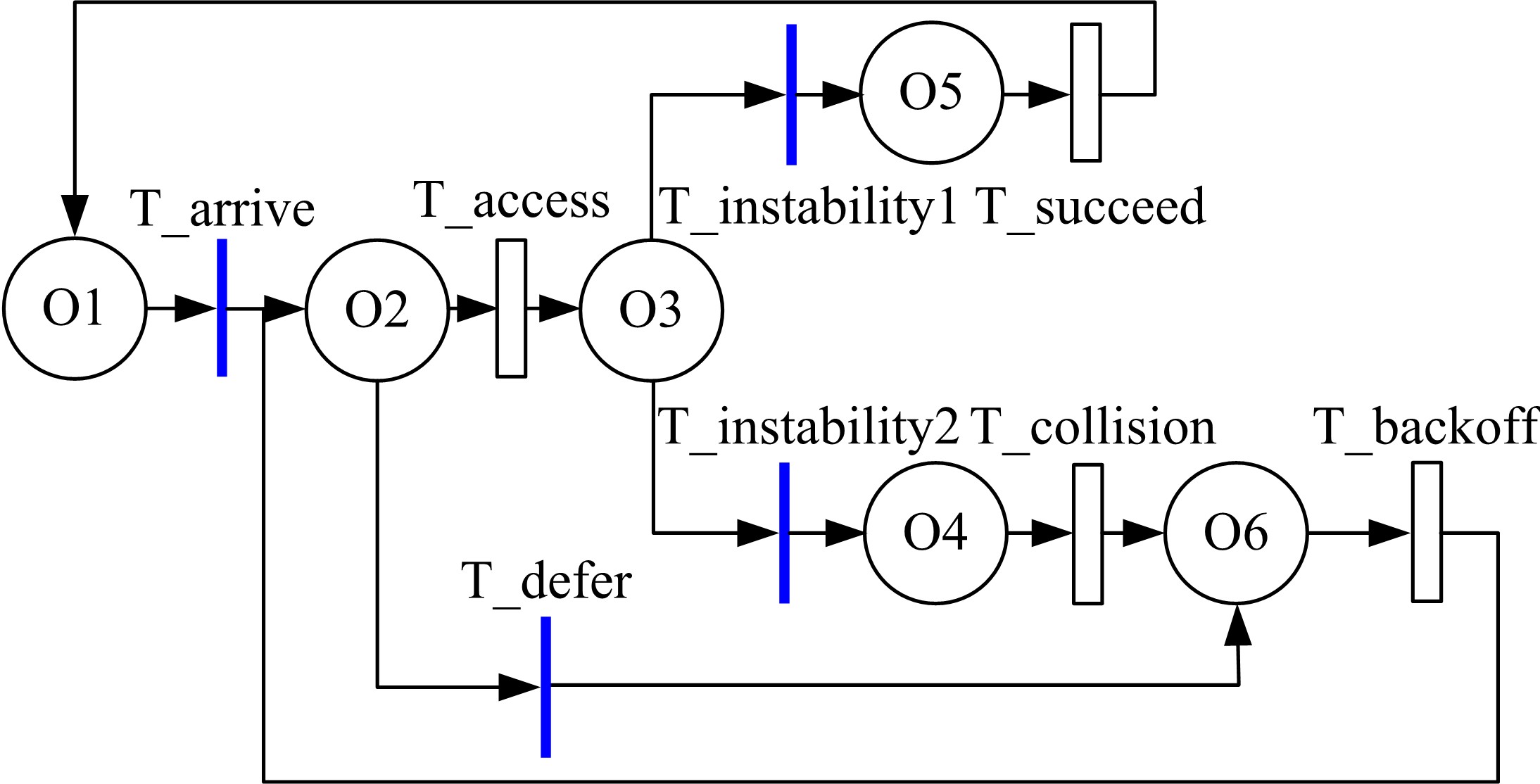
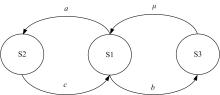
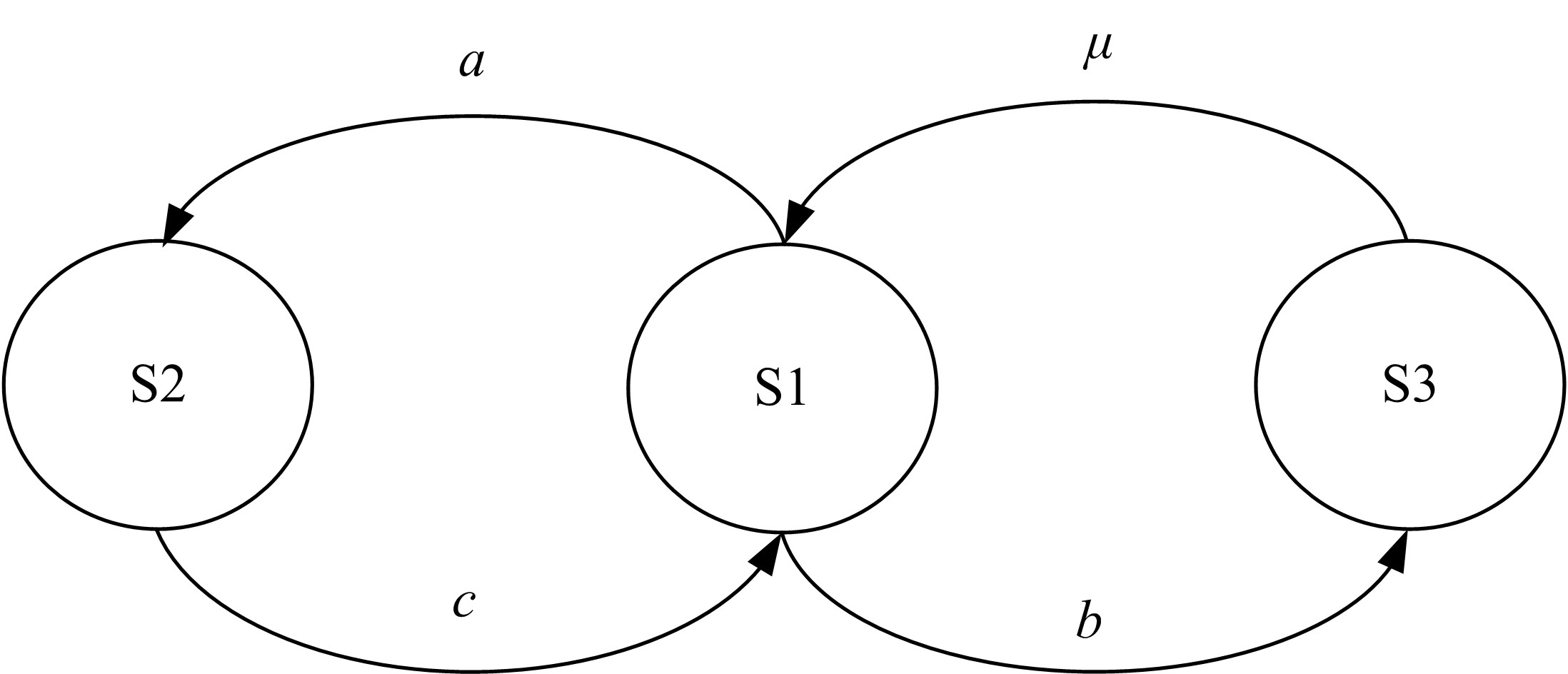
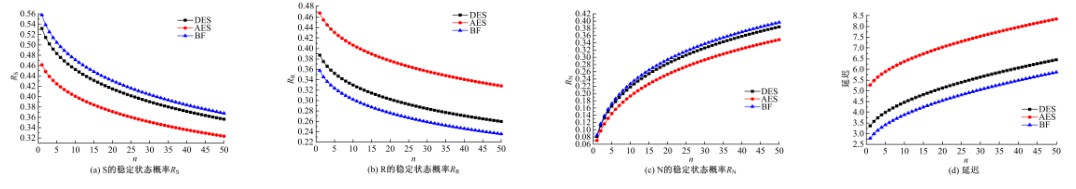
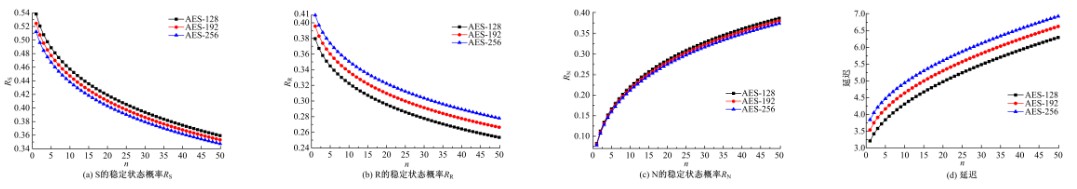
GSPN⁃based model to evaluate the performance and securi tytradeoff in Ad-hoc network
Jun-yi DENG1( ),Yan-heng LIU1,2,Shi FENG1,Rong-cun ZHAO3,Jian WANG1,2(
),Yan-heng LIU1,2,Shi FENG1,Rong-cun ZHAO3,Jian WANG1,2( )
)
- 1. College of Computer Science and Technology, Jilin University,Changchun 130012, China
2. Key Laboratory of Symbolic Computation and Knowledge Engineering of Ministry of Education, Jilin University, Changchun 130012, China
3. Baidu International Technology (Shenzhen) Co. Ltd. , Shenzhen 518000, China
CLC Number:
- TP393
| 1 | Al-Sultan Saif , Al-Doori Moath M , Al-Bayatti Ali H , et al . A comprehensive survey on vehicular Ad Hoc network[J]. Journal of Network & Computer Applications, 2014, 37(1): 380-392. |
| 2 | Deepak, Kumar R , Rishi R . Routing and security analysis in vehicular ad-hoc networks(VANETs)[C]∥IEEE International Conference on Power Electronics Intelligent Control and Energy Systems (ICPEICES),Delhi, India, 2017. |
| 3 | Qiu T , Chen N , Li K , et al . Heterogeneous ad hoc networks: architectures, advances and challenges[J]. Ad Hoc Networks, 2016, 55: 143-152. |
| 4 | Wolter K , Reinecke P . Performance and security tradeoff[C]∥LNCS 6154, 2010:135-167. |
| 5 | Zhao Y , Thomas N . Efficient solutions of a PEPA model of a key distribution centre[J]. Performance Evaluation, 2010, 67(8): 740-756. |
| 6 | Aldini A . Trade-off between performance and security[R]∥Foundations of Security Analysis and Design (FOSAD), Bertinoro, Italy, 2011. |
| 7 | Kumar N , Chilamkurti N . Collaborative trust aware intelligent intrusion detection in VANETs[J]. Computers & Electrical Engineering, 2014, 40(6): 1981-1996. |
| 8 | Liu Z C , Xiong L , Peng T , et al . A realistic distributed conditional privacy-preserving authentication scheme for vehicular Ad⁃hoc networks[J]. IEEE Access, 2018, 6: 26307-26317 |
| 9 | Marsan M A , Balbo G , Conte G , et al . Modelling with generalized stochastic petri nets[J]. ACM Sigmetrics Performance Evaluation Review, 1998, 26(2): 2. |
| 10 | Huaizhou Y , Zengzhi L I . Web service composition and performance analysis based on GSPN[J]. Computer Engineering, 2009, 35(22): 1-3. |
| 11 | Shi Z S , Wang C F , Zheng P , et al . An energy consumption prediction model based on GSPN for wireless sensor networks[C]∥International Conference on Computational & Information Sciences, Chengdu, China, 2011. |
| 12 | Zhao X , Malasse O , Buchheit G . Verification of safety integrity level of high demand system based on Stochastic Petri Nets and Monte Carlo simulation[J]. Reliability Engineering & System Safety, 2019, 184: 258-265. |
| 13 | Ma X , Chen X . Saturation Performance of IEEE 802.11 broadcast networks[J]. IEEE Communications Letters, 2007, 11(8): 686-688. |
| 14 | Ma X , Chen X . Performance Analysis of IEEE 802.11 broadcast scheme in Ad Hoc wireless LANs[J]. IEEE Transactions on Vehicular Technology, 2008, 57(6): 3757-3768. |
| 15 | Al Tamimi A K . Performance analysis of data encryption algorithms[DB/OL].[2018-10-13]. https:∥ |
| [1] | Man CHEN,Yong ZHONG,Zhen-dong LI. Multi-focus image fusion based on latent low⁃rank representation combining low⁃rank representation [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 297-305. |
| [2] | Xiao-dong ZHANG,Xiao-jun XIA,Hai-feng LYU,Xu-chao GONG,Meng-jia LIAN. Dynamic load balancing of physiological data flow in big data network parallel computing environment [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 247-254. |
| [3] | Xiao-hui WANG,Lu-shen WU,Hua-wei CHEN. Denoising of scattered point cloud data based on normal vector distance classification [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 278-288. |
| [4] | Tie-jun WANG,Wei-lan WANG. Thangka image annotation based on ontology [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 289-296. |
| [5] | Xiong-fei LI,Jing WANG,Xiao-li ZHANG,Tie-hu FAN. Multi-focus image fusion based on support vector machines and window gradient [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 227-236. |
| [6] | Hong-yan WANG,He-lei QIU,Jia ZHENG,Bing-nan PEI. Visual tracking method based on low⁃rank sparse representation under illumination change [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 268-277. |
| [7] | Xiang-jiu CHE,Hua-luo LIU,Qing-bin SHAO. Fabric defect recognition algorithm based onimproved Fast RCNN [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2038-2044. |
| [8] | Bing-hai ZHOU,Qiong WU. Balancing and optimization of robotic assemble lines withtool and space constraint [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2069-2075. |
| [9] | Hong-wei ZHAO,Peng WANG,Li-li FAN,Huang-shui HU,Ping-ping LIU. Similarity retention instance retrieval method [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2045-2050. |
| [10] | Jun SHEN,Xiao ZHOU,Zu-qin JI. Implementation of service dynamic extended network and its node system model [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2058-2068. |
| [11] | You ZHOU,Sen YANG,Da-lin LI,Chun-guo WU,Yan WANG,Kang-ping WANG. Acceleration platform for face detection and recognition based on field⁃programmable gate array [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2051-2057. |
| [12] | Bin LI,Xu ZHOU,Fang MEI,Shuai-ning PAN. Location recommendation algorithm based on K-means and matrix factorization [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(5): 1653-1660. |
| [13] | Xiong-fei LI,Lu SONG,Xiao-li ZHANG. Remote sensing image fusion based on cooperative empirical wavelet transform [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(4): 1307-1319. |
| [14] | Yuan-ning LIU,Shuai LIU,Xiao-dong ZHU,Guang HUO,Tong DING,Kuo ZHANG,Xue JIANG,Shu-jun GUO,Qi-xian ZHANG. Iris secondary recognition based on decision particle swarm optimization and stable texture [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(4): 1329-1338. |
| [15] | Bin LI,Guo⁃jun SHEN,Geng SUN,Ting⁃ting ZHENG. Improved chicken swarm optimization algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(4): 1339-1344. |
|
||