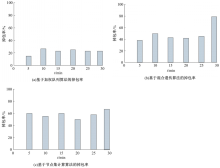
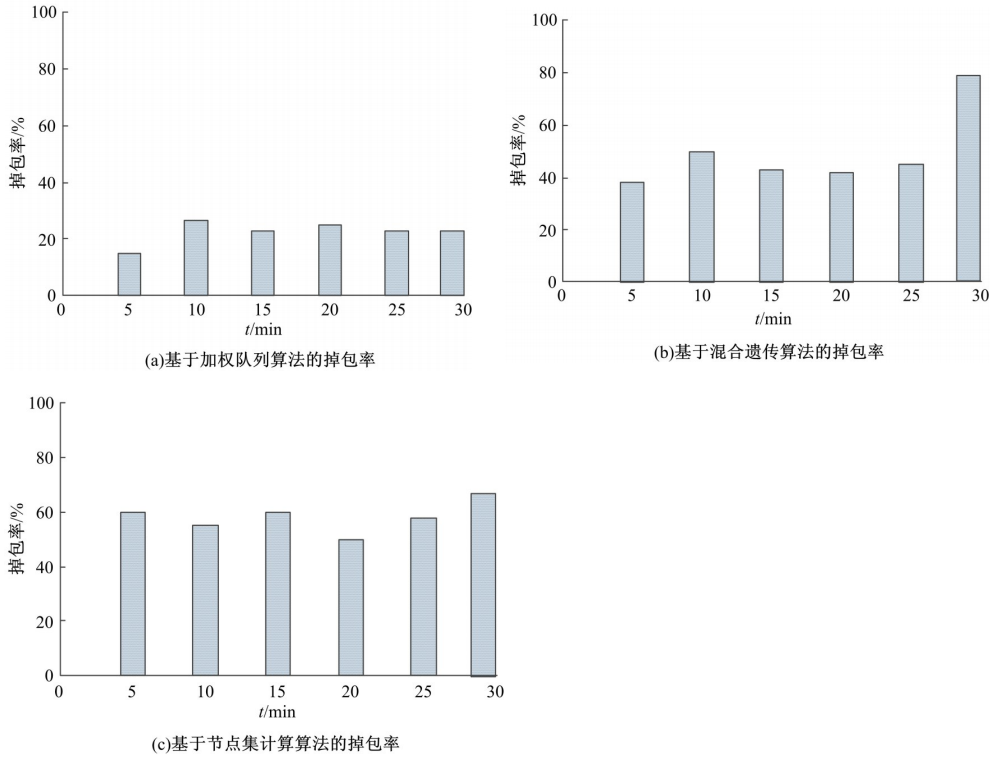
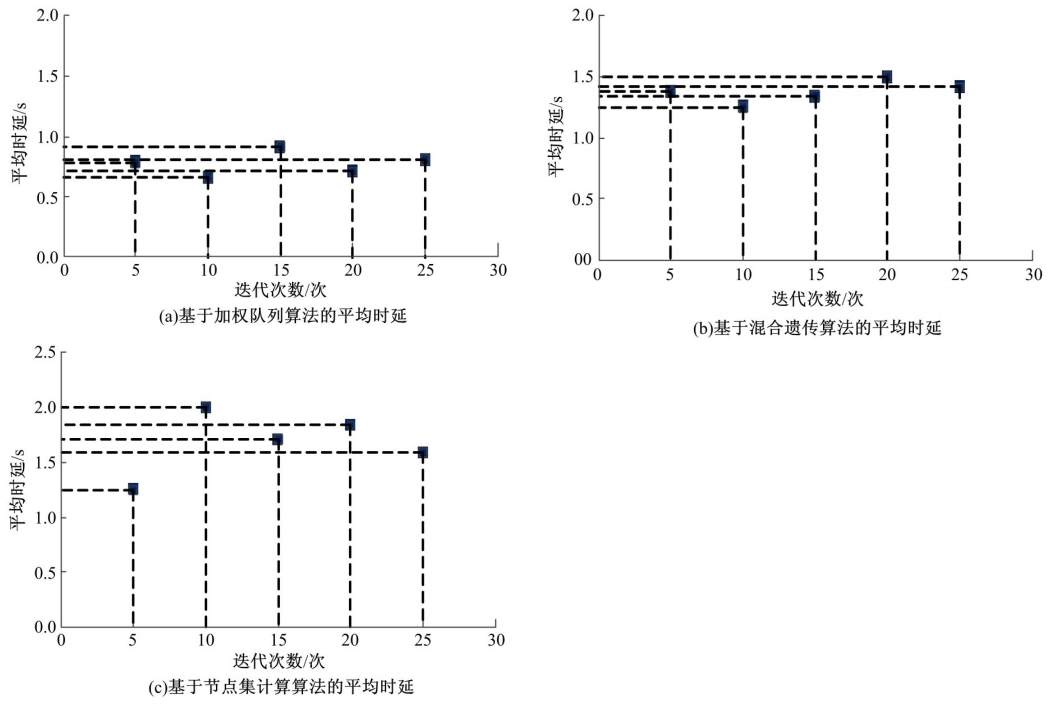
Journal of Jilin University(Engineering and Technology Edition) ›› 2021, Vol. 51 ›› Issue (4): 1470-1475.doi: 10.13229/j.cnki.jdxbgxb20200339
Cross-platform inter-process communication scheduling algorithm based on weighted queue
- School of Computer Science and Engineering,University of Electronic Science and Technology of China,Chengdu 611731,China
CLC Number:
- TP393
| 1 | 刘欣. 云计算通信网络信息下载均衡调度优化研究[J]. 计算机仿真, 2016, 33(10):162-165. |
| Liu Xin. Cloud computing communication network information download balanced scheduling optimization research[J]. Computer Simulation, 2016, 33(10):162-165. | |
| 2 | 段新宇, 韩杏玲, 吴宣利. LTE系统中基于缓存信息的非实时业务调度算法[J]. 哈尔滨工业大学学报, 2016, 48(11):142-146, 154. |
| Duan Xin-yu, Han Xing-ling, Wu Xuan-li. Non-real-time buffer information based scheduling algorithm in LTE system[J]. Journal of Harbin Institute of Technology, 2016, 48(11):142-146, 154. | |
| 3 | 吕朋蓬, 赵晋泉, 李端超, 等. 基于信息物理系统的孤岛微网实时调度的一致性协同算法[J]. 中国电机工程学报, 2016, 36(6):1471-1480. |
| Lv Peng-peng, Zhao Jin-quan, Li Duan-chao, et al. A consensus-based collaborative algorithm for real time dispatch of island microgrid in cyber physical system[J]. Proceedings of the CSEE, 2016, 36(6):1471-1480. | |
| 4 | 罗玉春, 王毅, 戴则梅, 等. 基于多调度控制中心的分解协调状态估计[J]. 电网技术, 2016, 40(5):1516-1521. |
| Luo Yu-chun, Wang Yi, Dai Ze-mei, et al. Decomposition and coordination state estimation for multi dispatching and control centers[J]. Power System Technology, 2016, 40(5):1516-1521. | |
| 5 | 李炳乾, 王勇, 谭小虎, 等. 基于混合遗传算法的TTE静态调度表生成设计[J]. 电子技术应用, 2016, 42(10):96-99, 103. |
| Li Bing-qian, Wang Yong, Tan Xiao-hu, et al. Hybrid-GA based static schedule generation for time-triggered Ethernet[J]. Application of Electronic Technique, 2016, 42(10):96-99, 103. | |
| 6 | 朱洁, 李雯睿, 王江平, 等. 基于节点集计算能力差异的Hadoop自适应任务调度算法[J]. 计算机应用, 2016, 36(4):918-922. |
| Zhu Jie, Li Wen-rui, Wang Jiang-ping, et al. Hadoop adaptive task scheduling algorithm based on computation capacity difference between node sets[J]. Journal of Computer Applications, 2016, 36(4):918-922. | |
| 7 | 齐平, 王福成, 王必晴, 等. 云计算环境下基于可靠性感知的任务调度算法[J]. 计算机工程与科学, 2018, 40(11):1925-1935. |
| Qi Ping, Wang Fu-cheng, Wang Bi-qing, et al. A reliability aware task scheduling algorithm for cloud computing[J]. Computer Engineering and Science, 2018, 40(11):1925-1935. | |
| 8 | 曾斌, 姚路, 胡炜, 等. 考虑不确定因素影响的保障任务调度算法[J]. 系统工程与电子技术, 2016, 38(3):595-601. |
| Zeng Bin, Yao Lu, Hu Wei, et al. Scheduling algorithm for maintenance tasks under uncertainty[J]. Systems Engineering and Electronics, 2016, 38(3):595-601. | |
| 9 | 彭浩, 韩江洪, 魏振春, 等. 副版本优先级可提升的全局容错调度算法[J]. 计算机研究与发展, 2016, 53(2):354-361. |
| Peng Hao, Han Jiang-hong, Wei Zhen-chun, et al. Fault tolerant global scheduling with backup priority promotion[J]. Journal of Computer Research and Development, 2016, 53(2):354-361. | |
| 10 | 钱晓军, 范冬萍, 吉根林. 物联网环境下实时任务传输的分簇调度算法[J]. 计算机科学, 2016, 43(11):176-179, 189. |
| Qian Xiao-jun, Fan Dong-ping, Ji Gen-lin. Cluster scheduling algorithm for real time tasks transmission in Internet of Things[J]. Computer Science, 2016, 43(11):176-179, 189. |
| [1] | Shu-tao SHEN,Zha-xi NIMA. Double chaos identifiable tampering image encryption method based on blockchain technology [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1055-1059. |
| [2] | Zhen-peng LIU,Shao-song REN,Ming LI,Xin-peng WANG,Xiao-fei LI. Software defines dynamic traffic scheduling scheme for network data center [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1040-1047. |
| [3] | Xiao-hui LI,Chao-yang CHEN,Hua-wei YI,Bo LI. Large scale network traffic prediction based on cloud computing and big data analysis [J]. Journal of Jilin University(Engineering and Technology Edition), 2021, 51(3): 1034-1039. |
| [4] | Zhou-zhou LIU,Wen-xiao YIN,Qian-yun ZHANG,Han PENG. Sensor cloud intrusion detection based on discrete optimization algorithm and machine learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(2): 692-702. |
| [5] | Shun-fu JIN,Xiu-chen QIE,Hai-xing WU,Zhan-qiang HUO. Clustered virtual machine allocation strategy in cloud computing based on new type of sleep-mode and performance optimization [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 237-246. |
| [6] | Jun-yi DENG,Yan-heng LIU,Shi FENG,Rong-cun ZHAO,Jian WANG. GSPN⁃based model to evaluate the performance and securi tytradeoff in Ad-hoc network [J]. Journal of Jilin University(Engineering and Technology Edition), 2020, 50(1): 255-261. |
| [7] | En-ze LIU,Wen-fu WU. Monochrome fruit growth detection internet architecture based oncomprehensive indicator quality evaluation algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2019-2026. |
| [8] | Jun SHEN,Xiao ZHOU,Zu-qin JI. Implementation of service dynamic extended network and its node system model [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(6): 2058-2068. |
| [9] | Bin-bin YU,Liang HU,Ling CHI. Digital signature scheme against internal and external attack for wireless sensor networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(5): 1676-1681. |
| [10] | Kun XIAO. Formal verification method for cryptographic software security based on Hoare logic [J]. Journal of Jilin University(Engineering and Technology Edition), 2019, 49(4): 1301-1306. |
| [11] | JIN Shun-fu,WANG Bao-shuai,HAO Shan-shan,JIA Xiao-guang,HUO Zhan-qiang. Synchronous sleeping based energy saving strategy of reservation virtual machines in cloud data centers and its performance research [J]. Journal of Jilin University(Engineering and Technology Edition), 2018, 48(6): 1859-1866. |
| [12] | ZHAO Dong,SUN Ming-yu,ZHU Jin-long,YU Fan-hua,LIU Guang-jie,CHEN Hui-ling. Improved moth-flame optimization method based on combination of particle swarm optimization and simplex method [J]. Journal of Jilin University(Engineering and Technology Edition), 2018, 48(6): 1867-1872. |
| [13] | FU Wen-bo, ZHANG Jie, CHEN Yong-le. Network topology discovery algorithm against routing spoofing attack in Internet of things [J]. 吉林大学学报(工学版), 2018, 48(4): 1231-1236. |
| [14] | HUANG Hui, FENG Xi-an, WEI Yan, XU Chi, CHEN Hui-ling. An intelligent system based on enhanced kernel extreme learning machine for choosing the second major [J]. 吉林大学学报(工学版), 2018, 48(4): 1224-1230. |
| [15] | CAI Zhen-nao, LYU Xin-en, CHEN Hui-ling. Prediction model of somatization disorder based on an oppositional bacterial foraging optimization based support vector machine [J]. 吉林大学学报(工学版), 2018, 48(3): 936-942. |
|
||