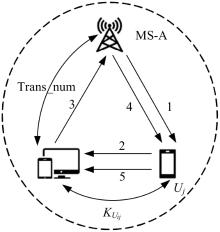
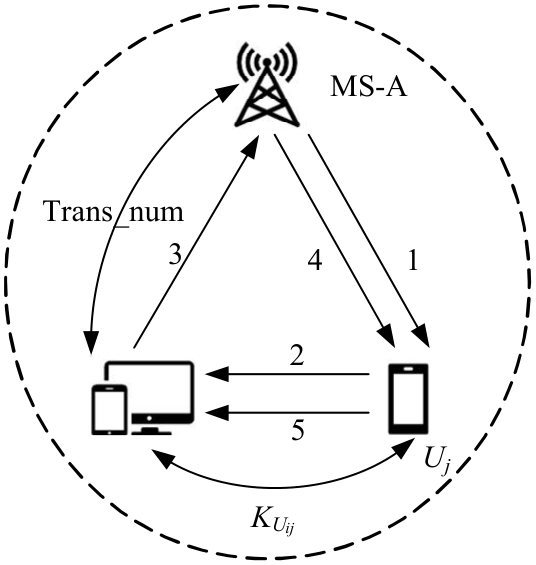
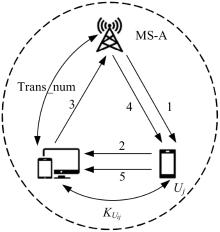
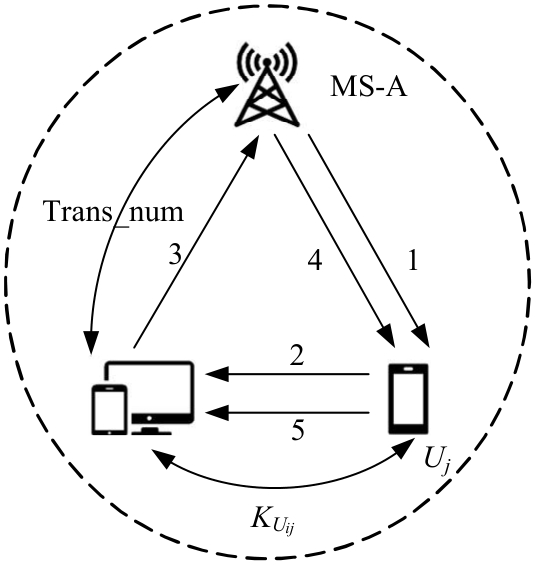
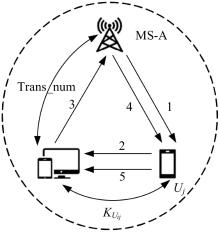
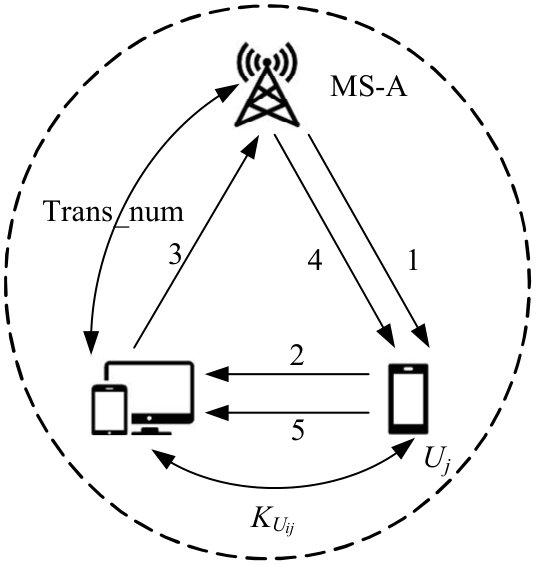
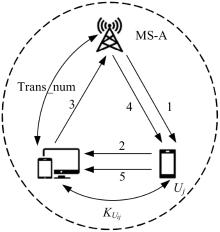
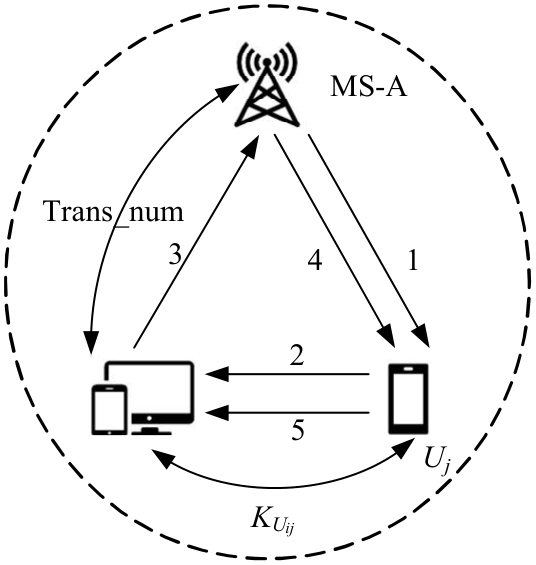
吉林大学学报(工学版) ›› 2025, Vol. 55 ›› Issue (3): 1050-1060.doi: 10.13229/j.cnki.jdxbgxb.20230618
• 计算机科学与技术 • 上一篇
移动边缘计算场景中的动态身份认证协议
- 兰州交通大学 电子与信息工程学院,兰州 730070
Dynamic authentication protocol for mobile edge computing scenarios
Shu-xu ZHAO( ),Zhi-chao SUN,Xiao-long WANG
),Zhi-chao SUN,Xiao-long WANG
- School of Electronic and Information Engineering,Lanzhou Jiaotong University,Lanzhou 730070,China
摘要:
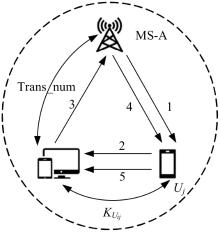
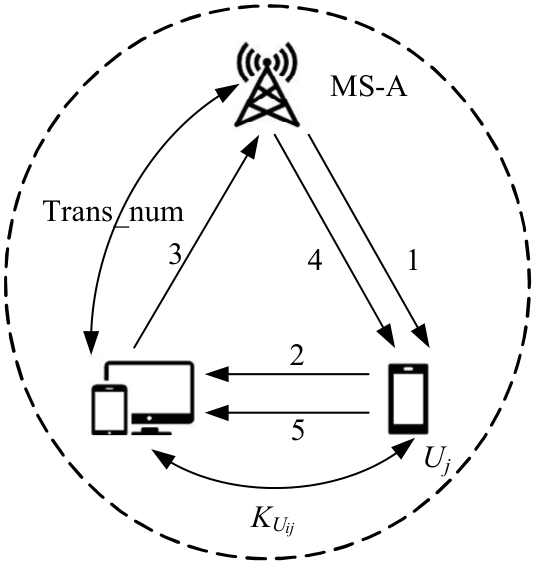
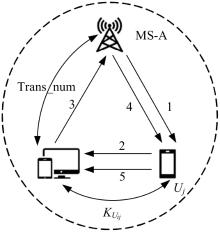
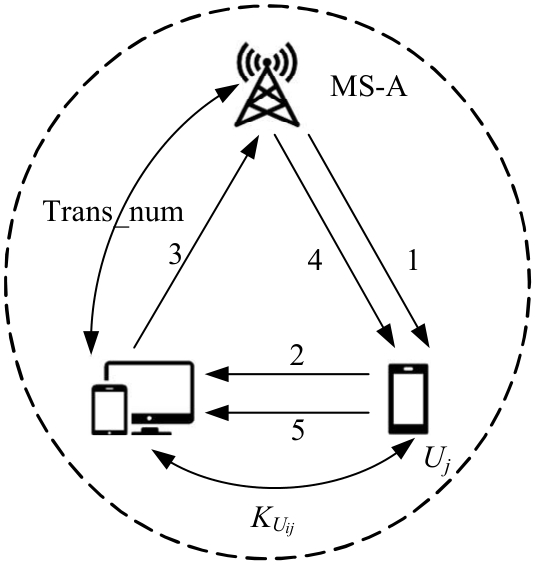
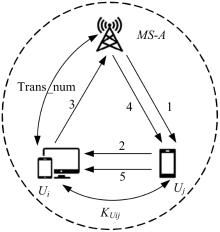
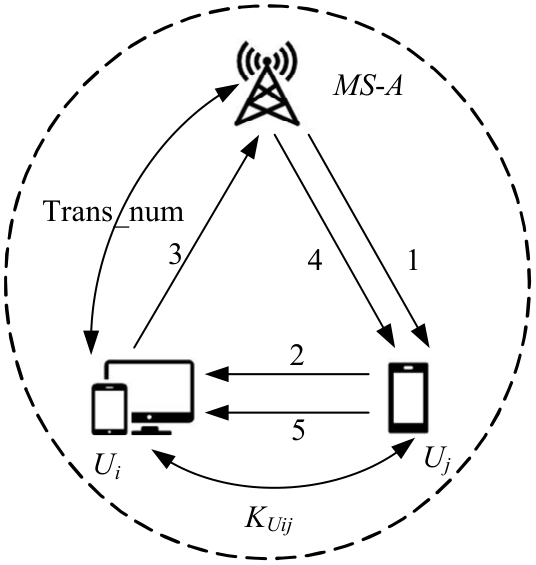
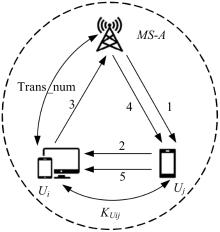
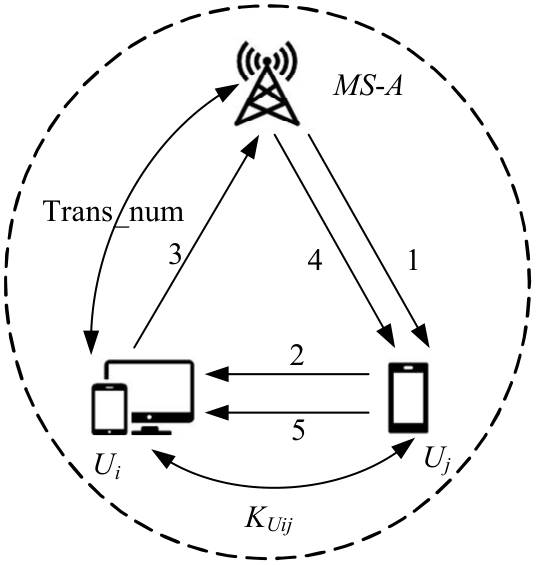
针对移动边缘计算中移动用户跨域身份认证问题,本文提出了一种由3种安全认证模型构成的动态身份认证框架,该框架提供了安全高效的身份认证。基于该认证框架,设计了基于椭圆曲线加密系统的轻量化身份认证协议——以边缘为中心的安全认证协议。该协议确保了移动用户的匿名性、不可追踪性,以及其与边缘服务器之间的相互认证。安全性分析和性能评估表明:本协议在计算成本和通信成本两方面都具有较大的性能优势,更加适合于移动场景。
中图分类号:
- TP309
| 1 | 施巍松, 孙辉, 曹杰, 等. 边缘计算: 万物互联时代新型计算模型[J]. 计算机研究与发展, 2017, 54(5): 907-924. |
| Shi Wei-song, Sun Hui, Cao Jie, et al. Edge computing—an emerging computing model for the internet of everything era [J]. Journal of Computer Research and Development, 2017, 54(5): 907-924. | |
| 2 | Shi W, Cao J, Zhang Q, et al. Edge computing: vision and challenges[J]. IEEE Internet of Things Journal, 2016, 3(5): 637-646. |
| 3 | 谢人超, 廉晓飞, 贾庆民, 等. 移动边缘计算卸载技术综述[J]. 通信学报, 2018, 39(11): 138-155. |
| Xie Ren-chao, Lian Xiao-fei, Jia Qing-min, et al. Survey on computation offloading in mobile edge computing[J]. Journal on Communications, 2018, 39(11): 138-155. | |
| 4 | Hu Y C, Patel M, Sabella D, et al. Mobile edge computing—a key technology towards 5G[J]. ETSI White Paper, 2015, 11(11): 1-16. |
| 5 | Dinh H T, Lee C, Niyato D, et al. A survey of mobile cloud computing: architecture, applications, and approaches[J]. Wireless Communications and Mobile Computing, 2013, 13(18): 1587-1611. |
| 6 | Cau E, Corici M, Bellavista P, et al. Efficient exploitation of mobile edge computing for virtualized 5G in EPC architectures[C]∥4th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 2016: 100-109. |
| 7 | Jararweh Y, Doulat A, AlQudah O, et al. The future of mobile cloud computing: integrating cloudlets and mobile edge computing[C]∥23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 2016: 1-5. |
| 8 | Barbarossa S, Sardellitti S, Di Lorenzo P. Communicating while computing: distributed mobile cloud computing over 5G heterogeneous networks[J]. IEEE Signal Processing Magazine, 2014, 31(6): 45-55. |
| 9 | Hassan N, Yau K L A, Wu C. Edge computing in 5G: a review[J]. IEEE Access, 2019, 7: 127276-127289. |
| 10 | 朱思峰, 赵明阳, 柴争义. 边缘计算场景中基于粒子群优化算法的计算卸载[J]. 吉林大学学报: 工学版, 2022, 52(11): 2698-2705. |
| Zhu Si-feng, Zhao Ming-yang, Chai Zheng-yi. Computing offloading scheme based on particle swarm optimization algorithm in edge computing scene[J]. Journal of Jilin University (Engineering and Technology Edition), 2022, 52(11): 2698-2705. | |
| 11 | Wang X L, Dang J W, Zhao S X, et al. Coalition structure generation in edge computing environment with multitasking concurrency[J]. IEEE Internet of Things Journal, 2023, 10(5): 4324-4338. |
| 12 | 张开元, 桂小林, 任德旺, 等. 移动边缘网络中计算迁移与内容缓存研究综述[J]. 软件学报, 2019, 30(8): 2491-2516. |
| Zhang Kai-yuan, Gui Xiao-lin, Ren De-wang, et al. Survey on computation offloading and content caching in mobile edge networks[J]. Journal of Software, 2019, 30(8): 2491-2516. | |
| 13 | Ranaweera P, Jurcut A D, Liyanage M. Survey on multi-access edge computing security and privacy[J]. IEEE Communications Surveys & Tutorials, 2021, 23(2): 1078-1124. |
| 14 | Irshad A, Chaudhry S A, Alomari O A, et al. A novel pairing-free lightweight authentication protocol for mobile cloud computing framework[J]. IEEE Systems Journal, 2021, 15(3): 3664-3672. |
| 15 | Amanlou S, Hasan M K, Bakar K A A. Lightweight and secure authentication scheme for IoT network based on publish-subscribe fog computing model[J]. Computer Networks, 2021, 199: No.108465. |
| 16 | Chatterjee U, Ray S, Khan M K, et al. An ECC-based lightweight remote user authentication and key management scheme for IoT communication in context of fog computing[J]. Computing, 2022, 104(6): 1359-1395. |
| 17 | Wang C, Huang R, Shen J, et al. A novel lightweight authentication protocol for emergency vehicle avoidance in VANETs[J]. IEEE Internet of Things Journal, 2021, 8(18): 14248-14257. |
| 18 | Rawat G S, Singh K, Arshad N I, et al. A lightweight authentication scheme with privacy preservation for vehicular networks[J]. Computers and Electrical Engineering, 2022, 100: No.108016. |
| 19 | Tsai J L, Lo N W. A privacy-aware authentication scheme for distributed mobile cloud computing services[J]. IEEE Systems Journal, 2015, 9(3): 805-815. |
| 20 | Irshad A, Sher M, Ahmad H F, et al. An improved multi-server authentication scheme for distributed mobile cloud computing services[J]. KSII Transactions on Internet and Information Systems (TIIS), 2016, 10(12): 5529-5552. |
| 21 | Kaur K, Garg S, Kaddoum G, et al. A lightweight and privacy-preserving authentication protocol for mobile edge computing[C]∥IEEE Global Communications Conference (GLOBECOM), Waikoloa, USA, 2019: 1-6. |
| 22 | Jia X, He D, Kumar N, et al. A provably secure and efficient identity-based anonymous authentication scheme for mobile edge computing[J]. IEEE Systems Journal, 2020, 14(1): 560-571. |
| 23 | Li Y, Cheng Q, Liu X, et al. A secure anonymous identity-based scheme in new authentication architecture for mobile edge computing[J]. IEEE Systems Journal, 2021, 15(1): 935-946. |
| 24 | 薛建彬, 白子梅. 边缘计算中移动终端安全高效认证协议[J]. 北京邮电大学学报, 2021, 44(1): 110-116. |
| Xue Jian-bin, Bai Zi-mei. Security and efficient authentication scheme for mobile edge computing[J]. Journal of Beijing University of Posts and Telecommunications, 2021, 44(1): 110-116. | |
| 25 | 余宜诚, 胡亮, 迟令,等. 一种单服务器环境下的匿名认证协议[J]. 吉林大学学报: 工学版, 2021, 51(2): 659-666. |
| Yu Yi-cheng, Hu Liang, Chi Ling, et al. An anonymous authentication protocol for single⁃server architectures[J]. Journal of Jilin University (Engineering and Technology Edition), 2021, 51(2): 659-666. | |
| 26 | Mao Y, You C, Zhang J, et al. A survey on mobile edge computing: the communication perspective[J]. IEEE Communications Surveys & Tutorials, 2017, 19(4): 2322-2358. |
| 27 | Tran T X, Hajisami A, Pandey P, et al. Collaborative mobile edge computing in 5G networks: new paradigms, scenarios, and challenges[J]. IEEE Communications Magazine, 2017, 55(4): 54-61. |
| 28 | Burrows M, Abadi M, Needham R. A logic of authentication[J]. ACM Transactions on Computer Systems (TOCS), 1990, 8(1): 18-36. |
| [1] | 魏晓辉,王晨洋,吴旗,郑新阳,于洪梅,岳恒山. 面向脉动阵列神经网络加速器的软错误近似容错设计[J]. 吉林大学学报(工学版), 2024, 54(6): 1746-1755. |
| [2] | 李丽娜,魏晓辉,郝琳琳,王兴旺,王储. 大规模流数据处理中代价有效的弹性资源分配策略[J]. 吉林大学学报(工学版), 2020, 50(5): 1832-1843. |
| [3] | 吴昊天,郭锐锋,彭阿珍,王品. 一种考虑可靠性的常带宽服务器低功耗调度算法[J]. 吉林大学学报(工学版), 2020, 50(5): 1802-1808. |
| [4] | 于斌斌,胡亮,迟令. 可抵抗内外部攻击的无线传感器网络数字签名方案[J]. 吉林大学学报(工学版), 2019, 49(5): 1676-1681. |
| [5] | 肖堃. 基于Hoare逻辑的密码软件安全性形式化验证方法[J]. 吉林大学学报(工学版), 2019, 49(4): 1301-1306. |
| [6] | 余宜诚, 胡亮, 迟令, 初剑峰. 一种改进的适用于多服务器架构的匿名认证协议[J]. 吉林大学学报(工学版), 2018, 48(5): 1586-1592. |
| [7] | 董坚峰, 张玉峰, 戴志强. 改进的基于狄利克雷混合模型的推荐算法[J]. 吉林大学学报(工学版), 2018, 48(2): 596-604. |
| [8] | 赵博, 秦贵和, 赵永哲, 杨文迪. 基于半陷门单向函数的公钥密码[J]. 吉林大学学报(工学版), 2018, 48(1): 259-267. |
| [9] | 刘磊, 刘利娟, 吴新维, 张鹏. 基于ECPMR的编译器测试方法[J]. 吉林大学学报(工学版), 2017, 47(4): 1262-1267. |
| [10] | 董立岩, 王越群, 贺嘉楠, 孙铭会, 李永丽. 基于时间衰减的协同过滤推荐算法[J]. 吉林大学学报(工学版), 2017, 47(4): 1268-1272. |
| [11] | 于斌斌, 武欣雨, 初剑峰, 胡亮. 基于群密钥协商的无线传感器网络签名协议[J]. 吉林大学学报(工学版), 2017, 47(3): 924-929. |
| [12] | 邓昌义, 郭锐锋, 张忆文, 王鸿亮. 基于平衡因子的动态偶发任务低功耗调度算法[J]. 吉林大学学报(工学版), 2017, 47(2): 591-600. |
| [13] | 郝娉婷, 胡亮, 姜婧妍, 车喜龙. 基于多管理节点的乐观锁协议[J]. 吉林大学学报(工学版), 2017, 47(1): 227-234. |
| [14] | 魏晓辉, 刘智亮, 庄园, 李洪亮, 李翔. 支持大规模流数据在线处理的自适应检查点机制[J]. 吉林大学学报(工学版), 2017, 47(1): 199-207. |
| [15] | 魏晓辉, 李翔, 李洪亮, 李聪, 庄园, 于洪梅. 支持大规模流数据处理的弹性在线MapReduce模型及拓扑协议[J]. 吉林大学学报(工学版), 2016, 46(4): 1222-1231. |
|
||