吉林大学学报(工学版) ›› 2020, Vol. 50 ›› Issue (1): 255-261.doi: 10.13229/j.cnki.jdxbgxb20181286
基于GSPN的Ad⁃hoc网络性能和安全平衡
邓钧忆1( ),刘衍珩1,2,冯时1,赵荣村3,王健1,2(
),刘衍珩1,2,冯时1,赵荣村3,王健1,2( )
)
- 1. 吉林大学 计算机科学与技术学院,长春 130012
2. 吉林大学 符号计算与知识工程教育部重点实验室,长春 130012
3. 百度国际科技(深圳)有限公司,广东 深圳 518000
GSPN⁃based model to evaluate the performance and securi tytradeoff in Ad-hoc network
Jun-yi DENG1( ),Yan-heng LIU1,2,Shi FENG1,Rong-cun ZHAO3,Jian WANG1,2(
),Yan-heng LIU1,2,Shi FENG1,Rong-cun ZHAO3,Jian WANG1,2( )
)
- 1. College of Computer Science and Technology, Jilin University,Changchun 130012, China
2. Key Laboratory of Symbolic Computation and Knowledge Engineering of Ministry of Education, Jilin University, Changchun 130012, China
3. Baidu International Technology (Shenzhen) Co. Ltd. , Shenzhen 518000, China
摘要:
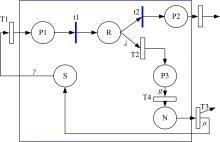
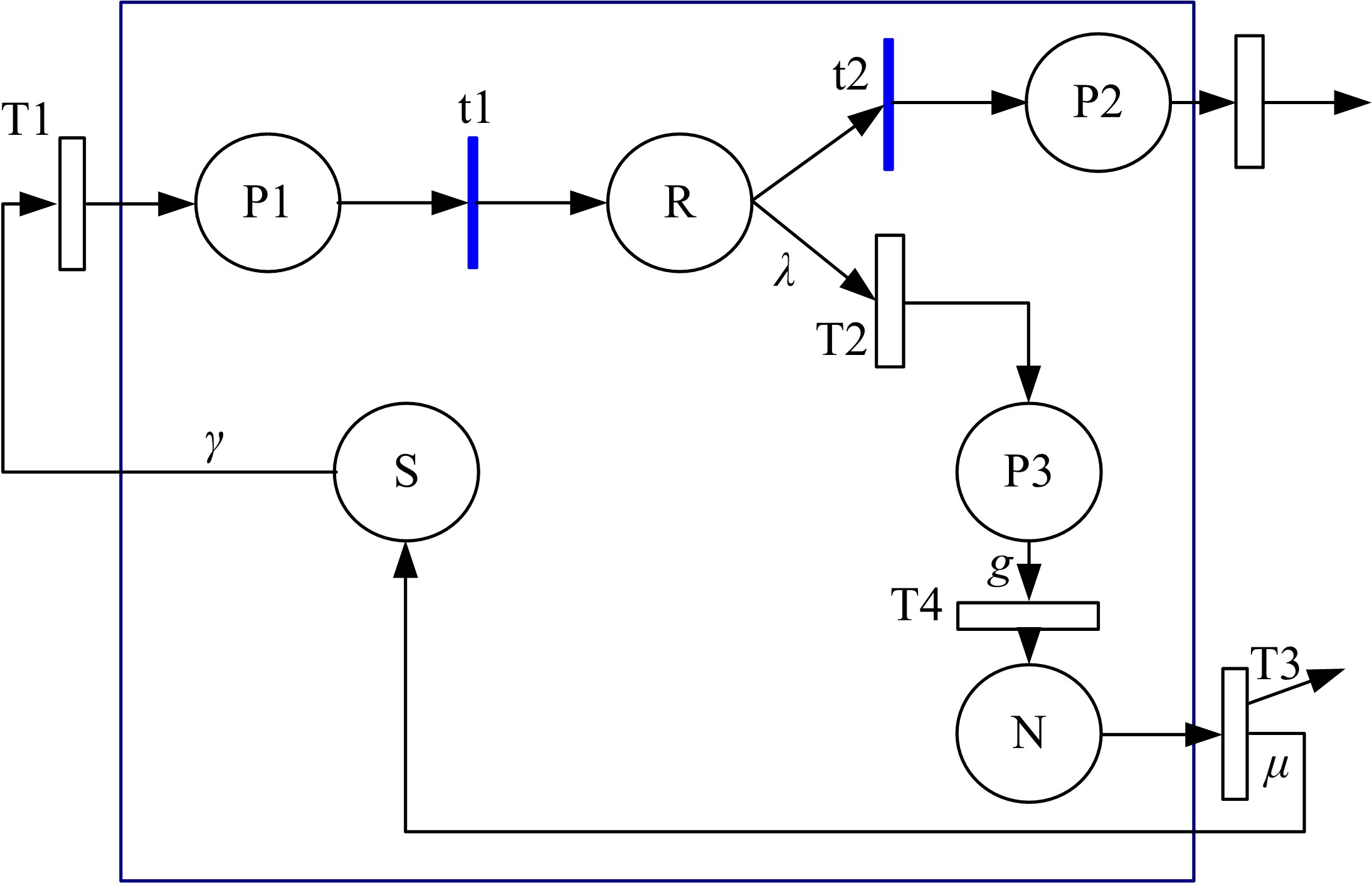
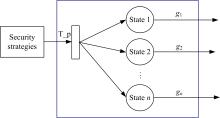
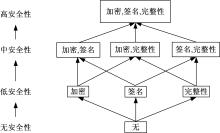
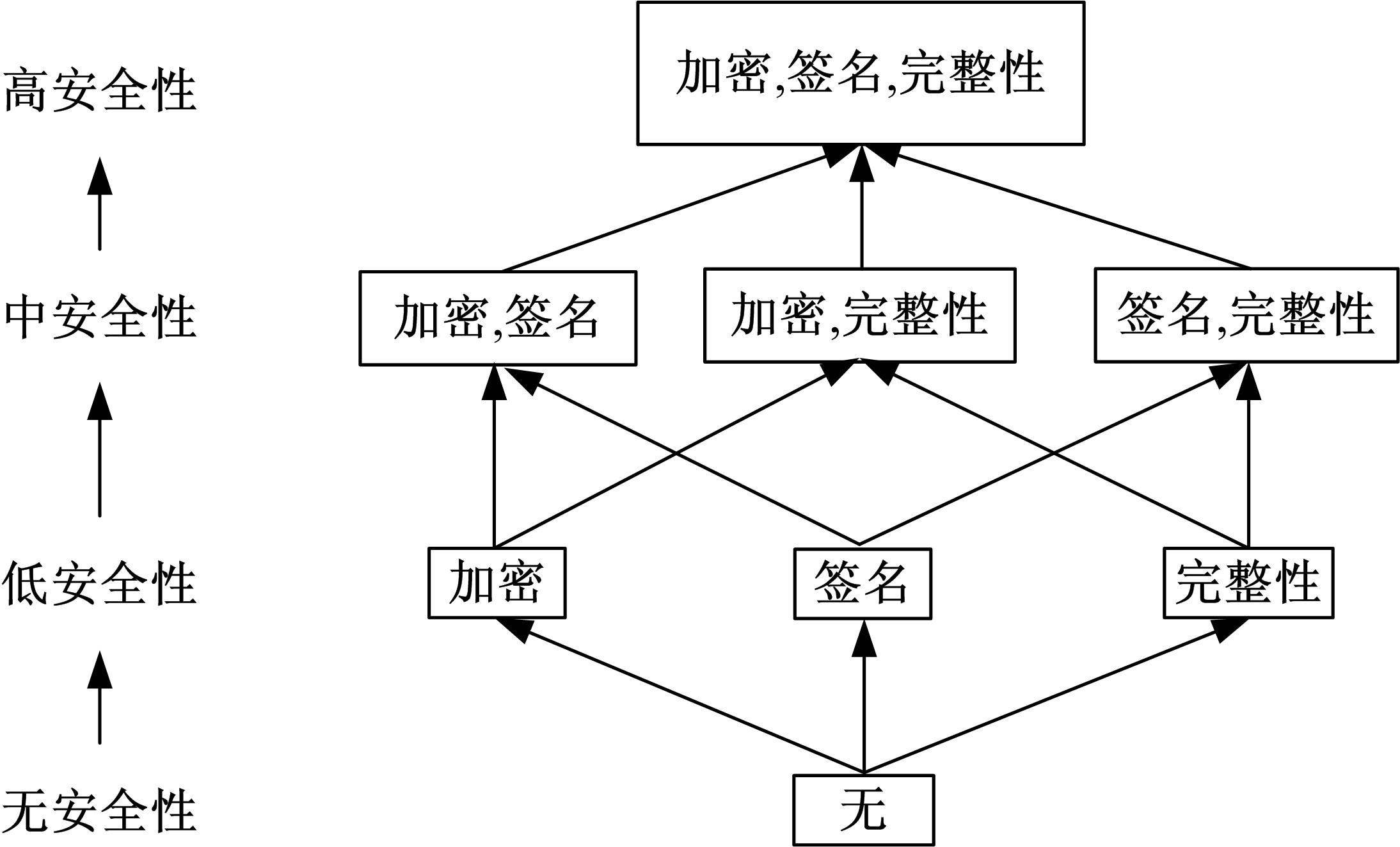
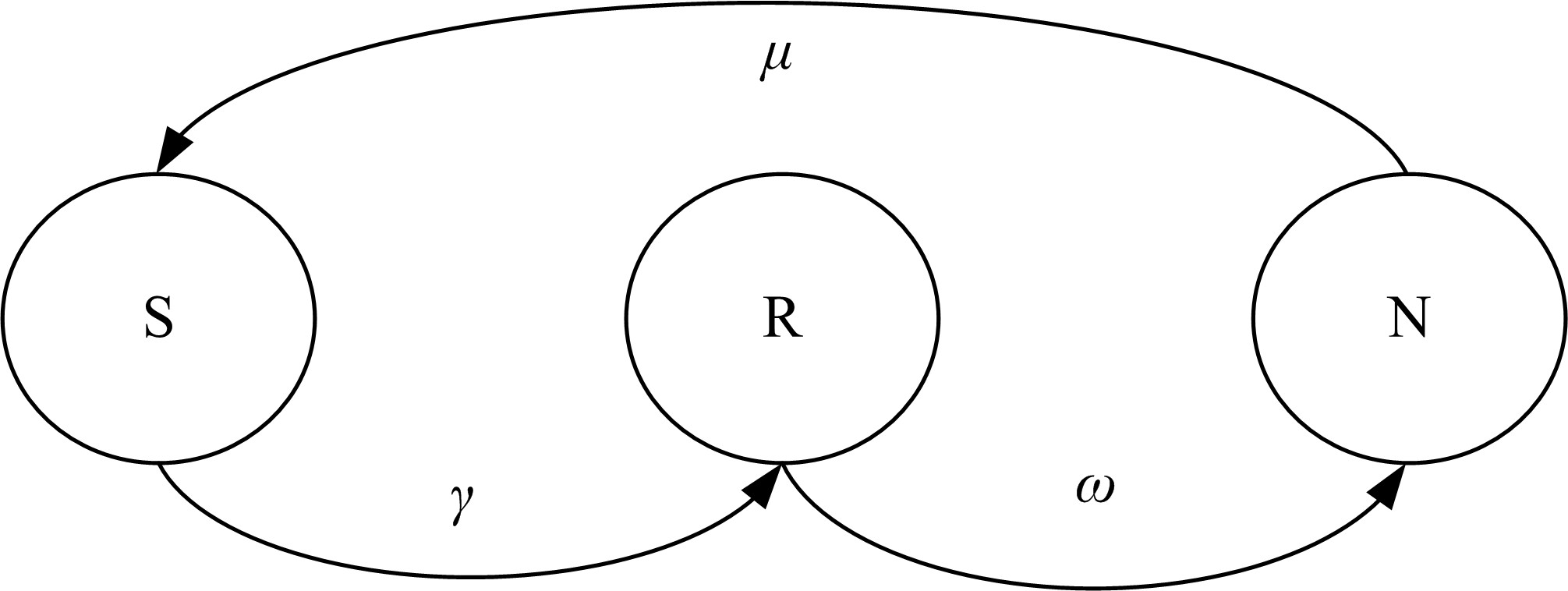
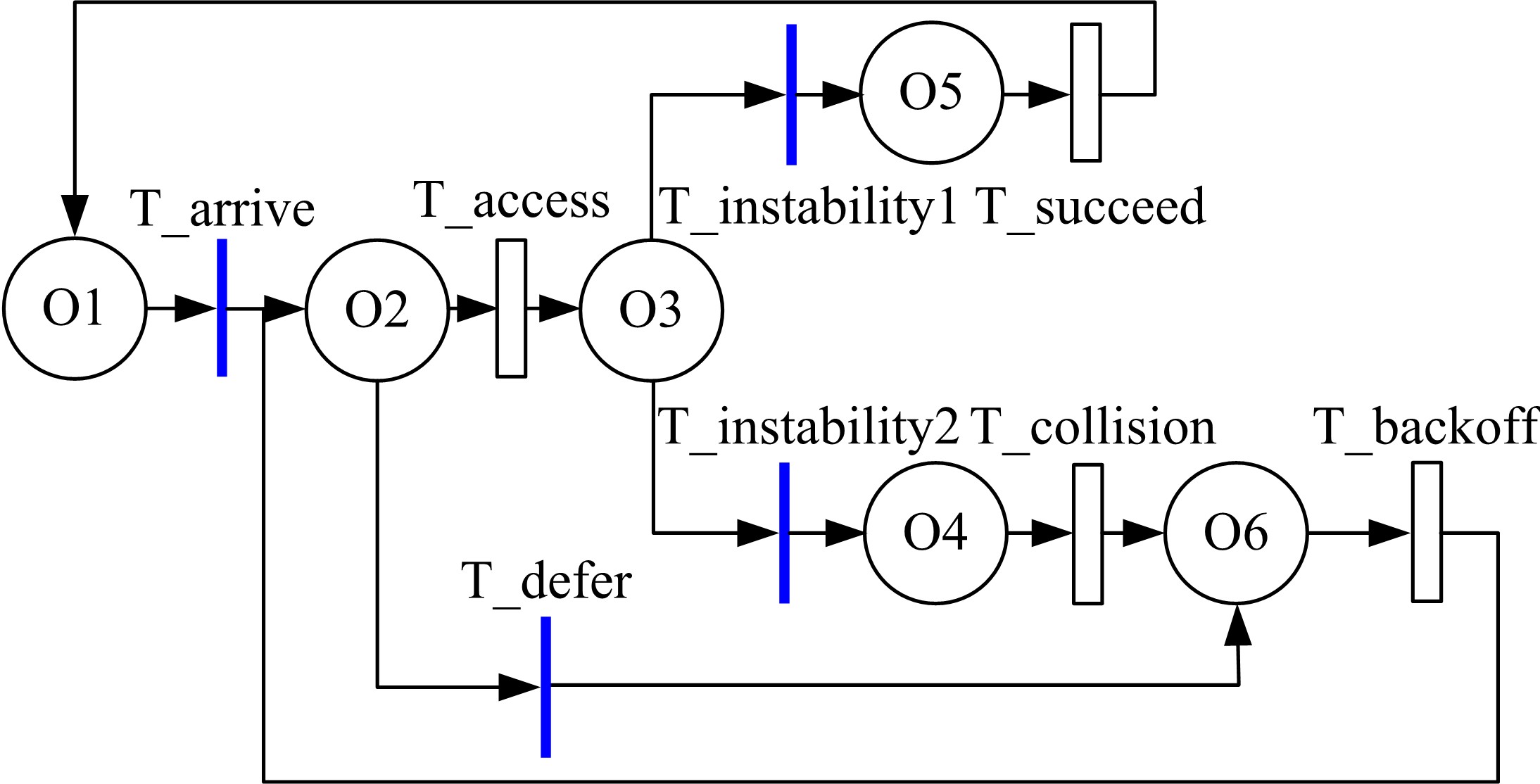
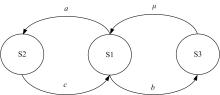
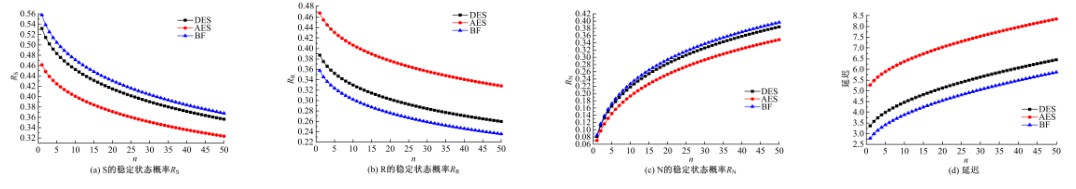
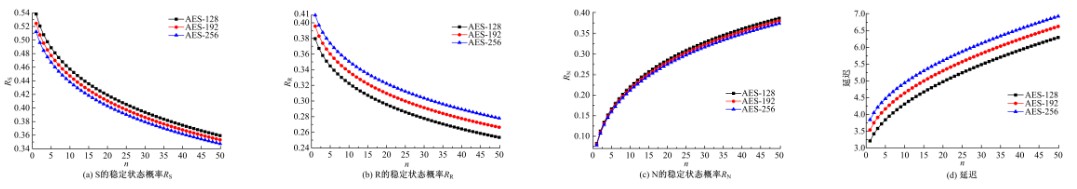
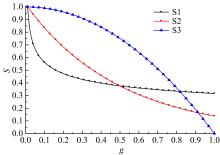
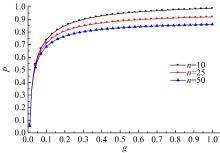
关于Ad-hoc网络研究中性能与安全的平衡问题有很多优化方案,但一直缺乏统一的量化标准来比较性能和收益,为此,提出了一种可以广泛使用的方法来评估Ad-hoc网络中性能和安全平衡。首先,采用GSPN构建节点内和节点间的数据传输模型;然后,运用Petri网抽象和精化;最后,结合连续时间马尔可夫链CTMC计算性能、安全和收益。通过这种方式,可将不同策略纳入统一的评估框架中,根据不同环境和需求选择最优均衡解,并在数据加密算法、密钥大小和策略选择上进行了仿真,为该模型利于网络资源的利用提供了理论依据和数据支持。
中图分类号:
- TP393
| 1 | Al-Sultan Saif , Al-Doori Moath M , Al-Bayatti Ali H , et al . A comprehensive survey on vehicular Ad Hoc network[J]. Journal of Network & Computer Applications, 2014, 37(1): 380-392. |
| 2 | Deepak, Kumar R , Rishi R . Routing and security analysis in vehicular ad-hoc networks(VANETs)[C]∥IEEE International Conference on Power Electronics Intelligent Control and Energy Systems (ICPEICES),Delhi, India, 2017. |
| 3 | Qiu T , Chen N , Li K , et al . Heterogeneous ad hoc networks: architectures, advances and challenges[J]. Ad Hoc Networks, 2016, 55: 143-152. |
| 4 | Wolter K , Reinecke P . Performance and security tradeoff[C]∥LNCS 6154, 2010:135-167. |
| 5 | Zhao Y , Thomas N . Efficient solutions of a PEPA model of a key distribution centre[J]. Performance Evaluation, 2010, 67(8): 740-756. |
| 6 | Aldini A . Trade-off between performance and security[R]∥Foundations of Security Analysis and Design (FOSAD), Bertinoro, Italy, 2011. |
| 7 | Kumar N , Chilamkurti N . Collaborative trust aware intelligent intrusion detection in VANETs[J]. Computers & Electrical Engineering, 2014, 40(6): 1981-1996. |
| 8 | Liu Z C , Xiong L , Peng T , et al . A realistic distributed conditional privacy-preserving authentication scheme for vehicular Ad⁃hoc networks[J]. IEEE Access, 2018, 6: 26307-26317 |
| 9 | Marsan M A , Balbo G , Conte G , et al . Modelling with generalized stochastic petri nets[J]. ACM Sigmetrics Performance Evaluation Review, 1998, 26(2): 2. |
| 10 | Huaizhou Y , Zengzhi L I . Web service composition and performance analysis based on GSPN[J]. Computer Engineering, 2009, 35(22): 1-3. |
| 11 | Shi Z S , Wang C F , Zheng P , et al . An energy consumption prediction model based on GSPN for wireless sensor networks[C]∥International Conference on Computational & Information Sciences, Chengdu, China, 2011. |
| 12 | Zhao X , Malasse O , Buchheit G . Verification of safety integrity level of high demand system based on Stochastic Petri Nets and Monte Carlo simulation[J]. Reliability Engineering & System Safety, 2019, 184: 258-265. |
| 13 | Ma X , Chen X . Saturation Performance of IEEE 802.11 broadcast networks[J]. IEEE Communications Letters, 2007, 11(8): 686-688. |
| 14 | Ma X , Chen X . Performance Analysis of IEEE 802.11 broadcast scheme in Ad Hoc wireless LANs[J]. IEEE Transactions on Vehicular Technology, 2008, 57(6): 3757-3768. |
| 15 | Al Tamimi A K . Performance analysis of data encryption algorithms[DB/OL].[2018-10-13]. https:∥ |
| [1] | 陈蔓,钟勇,李振东. 隐低秩结合低秩表示的多聚焦图像融合[J]. 吉林大学学报(工学版), 2020, 50(1): 297-305. |
| [2] | 张笑东,夏筱筠,吕海峰,公绪超,廉梦佳. 大数据网络并行计算环境中生理数据流动态负载均衡[J]. 吉林大学学报(工学版), 2020, 50(1): 247-254. |
| [3] | 王晓辉,吴禄慎,陈华伟. 基于法向量距离分类的散乱点云数据去噪[J]. 吉林大学学报(工学版), 2020, 50(1): 278-288. |
| [4] | 王铁君,王维兰. 基于本体的唐卡图像标注方法[J]. 吉林大学学报(工学版), 2020, 50(1): 289-296. |
| [5] | 李雄飞,王婧,张小利,范铁虎. 基于SVM和窗口梯度的多焦距图像融合方法[J]. 吉林大学学报(工学版), 2020, 50(1): 227-236. |
| [6] | 王洪雁,邱贺磊,郑佳,裴炳南. 光照变化下基于低秩稀疏表示的视觉跟踪方法[J]. 吉林大学学报(工学版), 2020, 50(1): 268-277. |
| [7] | 车翔玖,刘华罗,邵庆彬. 基于Fast RCNN改进的布匹瑕疵识别算法[J]. 吉林大学学报(工学版), 2019, 49(6): 2038-2044. |
| [8] | 周炳海,吴琼. 考虑工具和空间约束的机器人装配线平衡优化[J]. 吉林大学学报(工学版), 2019, 49(6): 2069-2075. |
| [9] | 赵宏伟,王鹏,范丽丽,胡黄水,刘萍萍. 相似性保持实例检索方法[J]. 吉林大学学报(工学版), 2019, 49(6): 2045-2050. |
| [10] | 沈军,周晓,吉祖勤. 服务动态扩展网络及其结点系统模型的实现[J]. 吉林大学学报(工学版), 2019, 49(6): 2058-2068. |
| [11] | 周柚,杨森,李大琳,吴春国,王岩,王康平. 基于现场可编程门电路的人脸检测识别加速平台[J]. 吉林大学学报(工学版), 2019, 49(6): 2051-2057. |
| [12] | 李宾,周旭,梅芳,潘帅宁. 基于K-means和矩阵分解的位置推荐算法[J]. 吉林大学学报(工学版), 2019, 49(5): 1653-1660. |
| [13] | 李雄飞,宋璐,张小利. 基于协同经验小波变换的遥感图像融合[J]. 吉林大学学报(工学版), 2019, 49(4): 1307-1319. |
| [14] | 刘元宁,刘帅,朱晓冬,霍光,丁通,张阔,姜雪,郭书君,张齐贤. 基于决策粒子群优化与稳定纹理的虹膜二次识别[J]. 吉林大学学报(工学版), 2019, 49(4): 1329-1338. |
| [15] | 李宾,申国君,孙庚,郑婷婷. 改进的鸡群优化算法[J]. 吉林大学学报(工学版), 2019, 49(4): 1339-1344. |
|
||