吉林大学学报(工学版) ›› 2021, Vol. 51 ›› Issue (6): 2198-2206.doi: 10.13229/j.cnki.jdxbgxb20210475
• 计算机科学与技术 • 上一篇
面向云端系统的可伸缩群体远程对外证明方法
- 1.浙江工商大学 杭州商学院,杭州 311500
2.中国人民大学 信息学院,北京 100872
3.浙江大学 计算机科学与技术学院,杭州 310013
Scalable collective remote attestation towards cloud system
He-qing SONG1( ),Li-qiang YOU1,Yuan SONG2,Zhang-ye WANG3(
),Li-qiang YOU1,Yuan SONG2,Zhang-ye WANG3( )
)
- 1.Hangzhou College of Commerce,Zhejiang Gongshang University,Hangzhou 311500,China
2.School of Information,Renmin University,Beijing 100872,China
3.College of Computer Science and Technology,Zhejiang University,Hangzhou 310013,China
摘要:
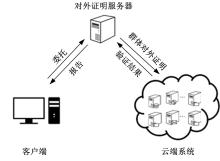
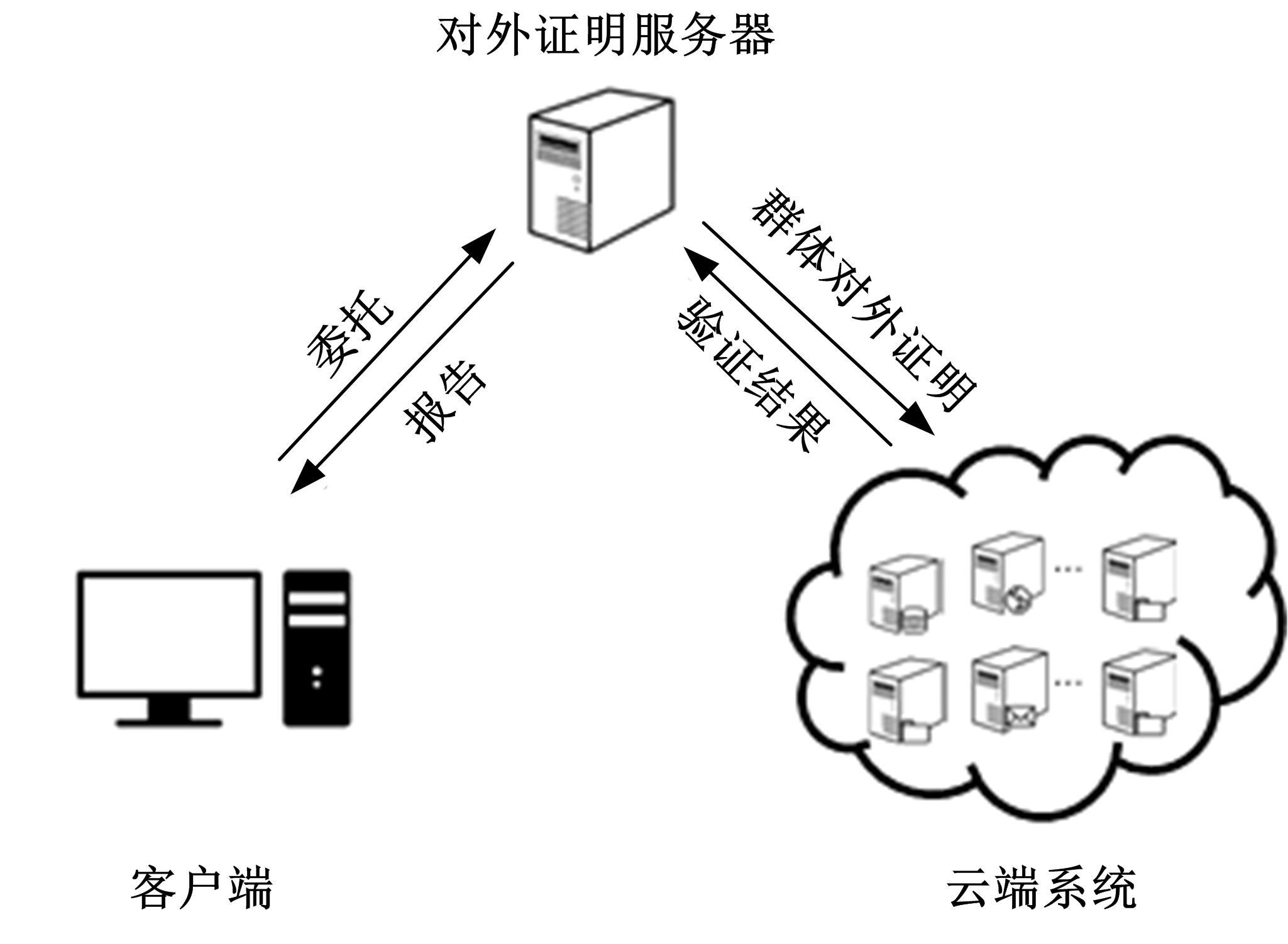
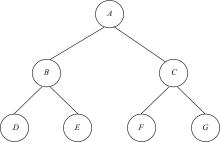
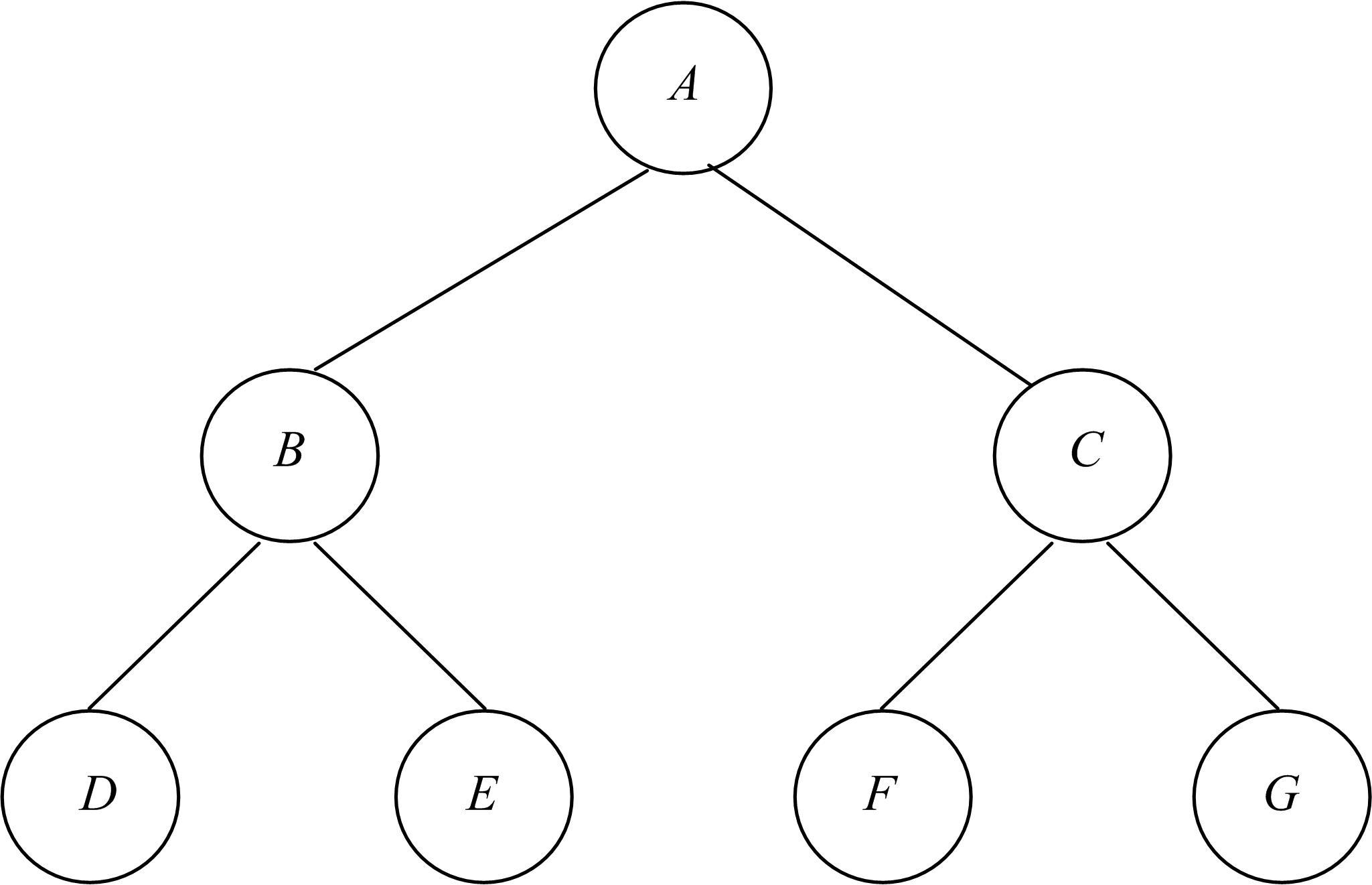
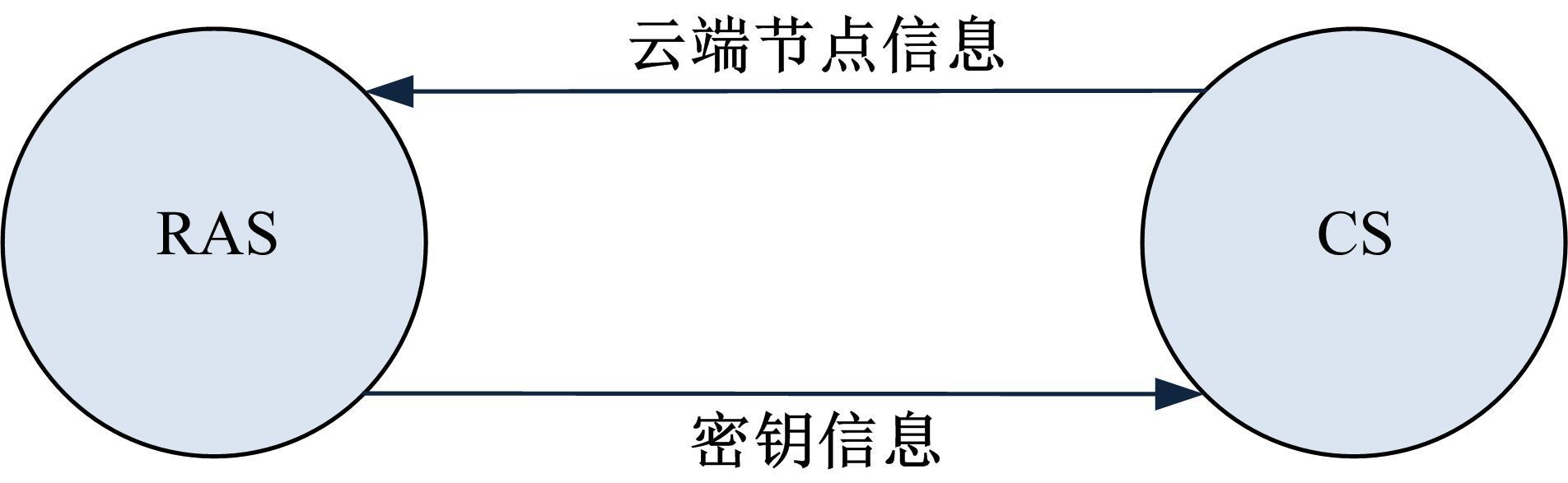
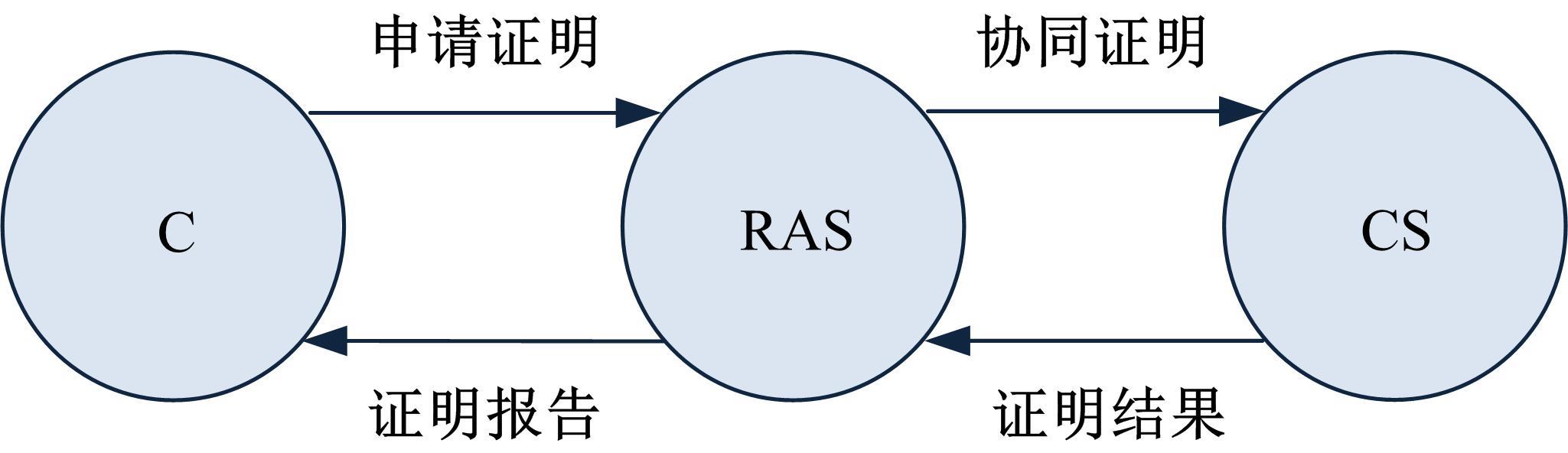
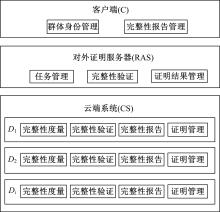
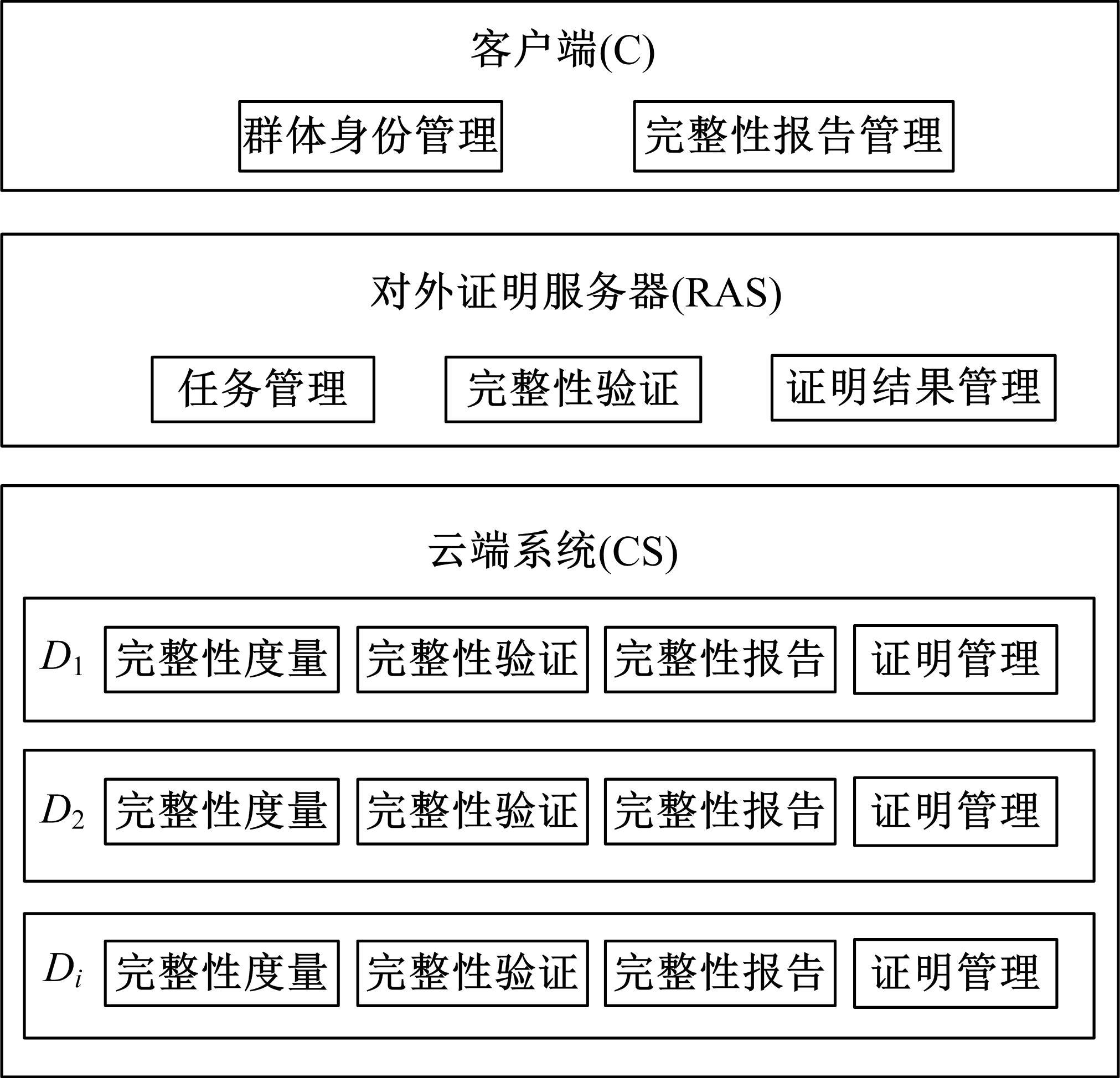
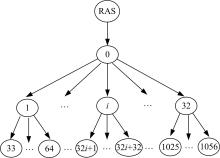
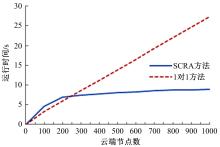
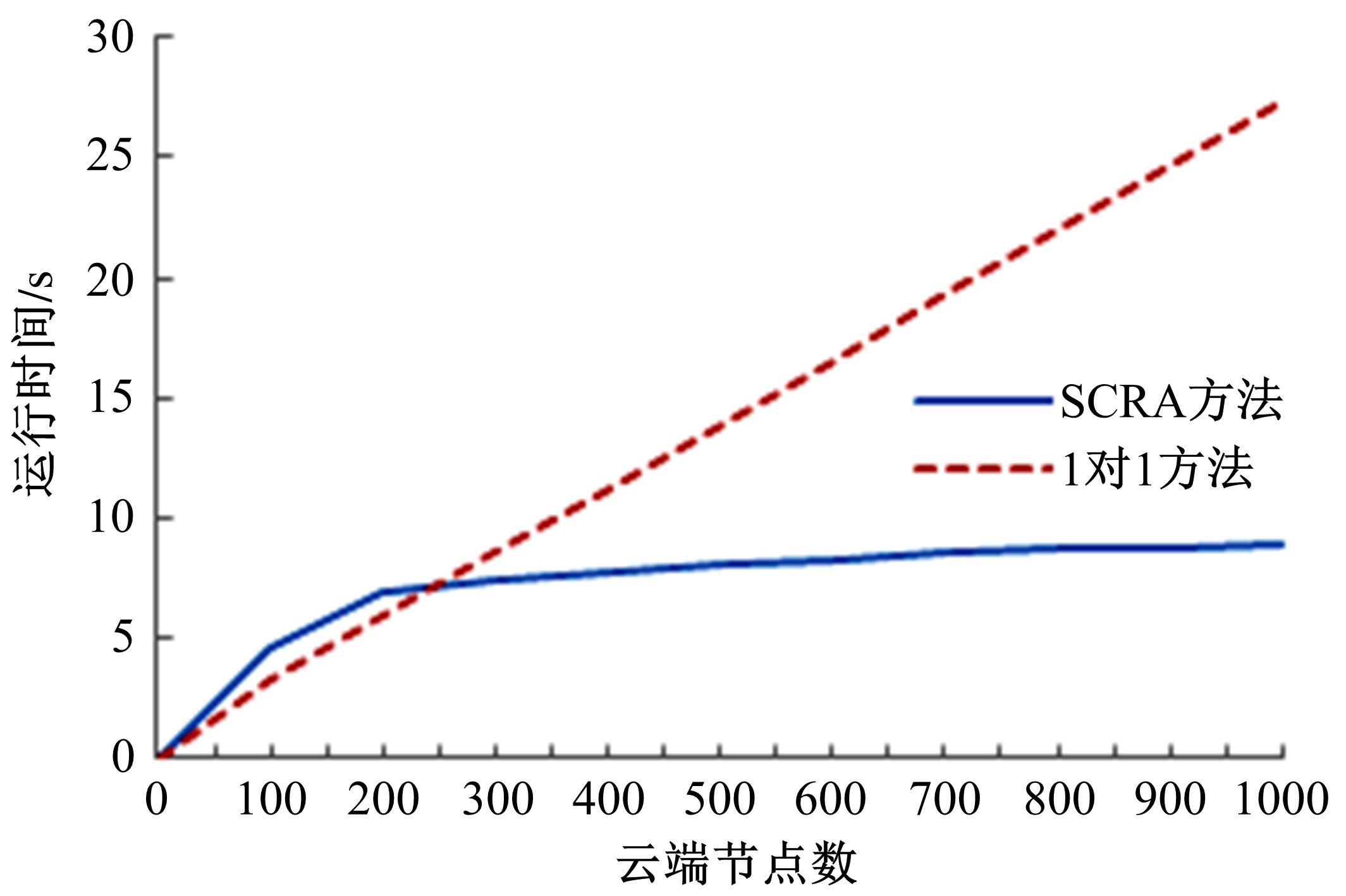
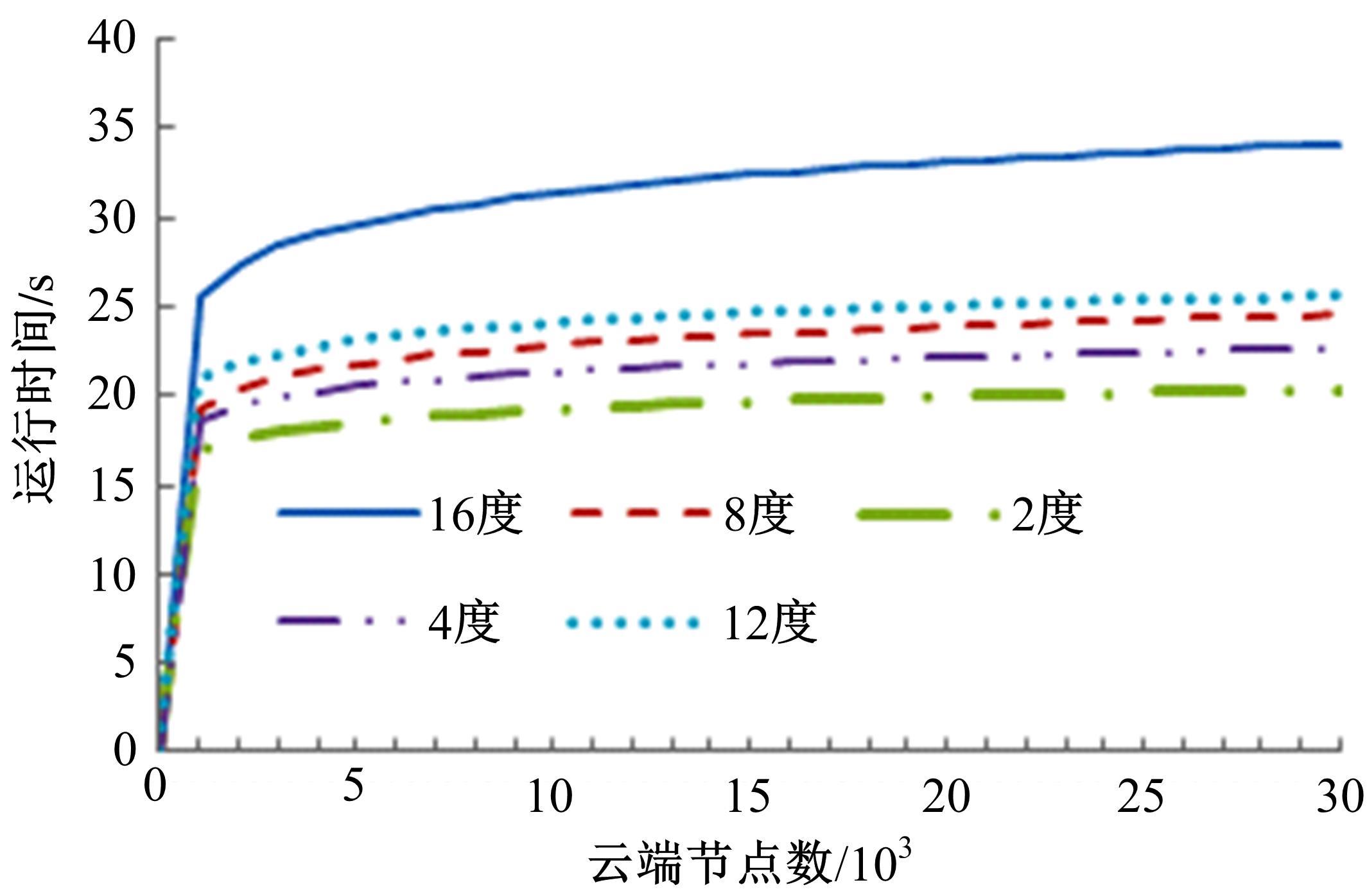
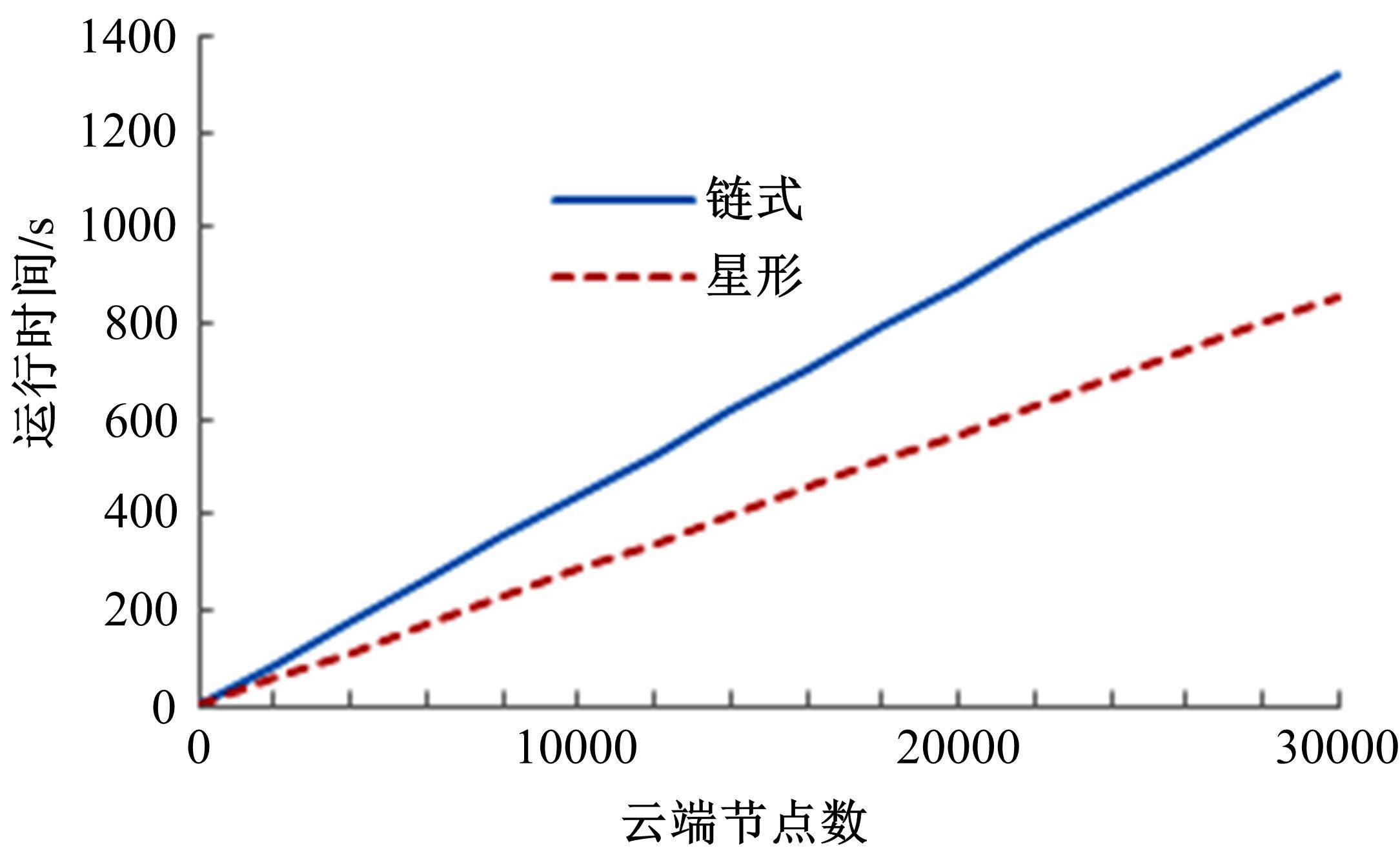
为真实地掌握大规模云端系统的完整性状态,同时保障可伸缩性和高效性的需求,本文提出了一种面向云端系统的群体对外证明方法,提出用对外证明关系树结构确定云端节点间的协作关系,协同收集、验证云端系统各节点的完整性状态。采用基于身份的聚合签名技术,快速检验证明结果的有效性。实验结果表明,本文方法与现有的云端系统对外证明方法相比,在可伸缩性方面具有较好的表现,能在19.9 s内有效证明3万个节点组成的云端系统的完整性状态。
中图分类号:
- TP399
| 1 | Common vulnerabilities and exposures. CVE-ID: CVE-2021-31929[DB/OL].[2021-04-30]. |
| 2 | Common vulnerabilities and exposures. CVE-ID: CVE-2020-8933[DB/OL].[2020-02-12]. |
| 3 | Gao Xing, Steenkamer B, Gu Zhong-shu, et al. A study on the security implications of information leakages in container clouds[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(1): 174-191. |
| 4 | Patel S, Persiano G, Yeo K, et al. Mitigating leakage in secure cloud-hosted data structures: volume-hiding for multi-maps via hashing[C]∥Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019:79-93. |
| 5 | Bacis E, Paraboschi S, Foresti S, et al. Securing resources in decentralized cloud storage[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 286-298. |
| 6 | Cojocar L, Kim J, Patel M, et al. Are we susceptible to rowhammer? An end-to-end methodology for cloud providers[C]∥2020 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 2020: 712-728. |
| 7 | Ali T, Ismail R, Musa S, et al. Design and implementation of an attestation protocol for measured dynamic behavior[J]. The Journal of Supercomputing, 2018, 74(11): 5746-5773. |
| 8 | Weng Chu-liang, Liu Qian, Li Ken-li, et al. CloudMon: monitoring virtual machines in clouds[J]. IEEE Transactions on Computers, 2016, 65(12): 3787-3793. |
| 9 | Stephen A, Benedict S, Kumar R P A, et al. Monitoring IaaS using various cloud monitors[J]. Cluster Computing, 2019, 22(1): 12459-12471. |
| 10 | 何欣枫, 田俊峰, 刘凡鸣. 可信云平台技术综述[J]. 通信学报, 2019, 40(2): 154-163. |
| He Xin-feng, Tian Jun-feng, Liu Fan-ming. Survey on trusted cloud platform technology[J]. Journal on Communications, 2019, 40(2): 154-163. | |
| 11 | 冯登国, 刘敬彬, 秦宇, 等. 创新发展中的可信计算理论与技术[J].中国科学: 信息科学, 2020, 50(8): 1127-1147. |
| Feng Deng-guo, Liu Jing-bin, Qin Yu, et al. Trusted computing theory and technology in innovation-driven development[J]. Scientia Sinica(Informationis), 2020, 50(8): 1127-1147. | |
| 12 | Santos N, Gummadi K P, Rodrigues R, et al. Towards trusted cloud computing[C]∥IEEE International Conference on Cloud Computing Technology and Science, San Diego, CA, USA, 2009: 1-5. |
| 13 | Sen P, Saha P, Khatua S. A distributed approach towards trusted cloud computing platform[C]∥2015 Applications and Innovations in Mobile Computing (AIMoC), Kolkata, India, 2015: 146-151. |
| 14 | Asokan N, Brasser F, Ibrahim A, et al. SEDA: scalable embedded device attestation[C]∥Computer and Communications Security, Denver, USA, 2015: 964-975. |
| 15 | Sailer R, Zhang X L, Jaeger T, et al. Design and implementation of a TCG-based integrity measurement architecture[J/OL].[2021-04-27]. |
| 16 | Xing Bin, Han Zhen, Chang Xiao-lin, et al. OB-IMA: out-of-the-box integrity measurement approach for guest virtual machines[J]. Concurrency and Computation: Practice and Experience, 2015, 27(5): 1092-1109. |
| 17 | Zheng Wei, Wu Ying, Wu Xiao-xue, et al. A survey of intel SGX and its applications[J]. Frontiers of Computer Science, 2021, 15(3): 186-200. |
| 18 | Hua Zhi-chao, Gu Jin-yu, Xia Yu-bin, et al. vTZ: virtualizing ARM trustZone[C]∥The Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 2017: 541-556. |
| 19 | Wang Juan, Hong Zhi, Zhang Yu-han, et al. Enabling security-enhanced attestation with intel sgx for remote terminal and IoT[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2018, 37(1): 88-96. |
| 20 | Arnautov S, Trach B, Gregor F, et al. Scone: secure linux containers with intel SGX[C]∥The 12th USENIX Symposium on Operating Systems Design and Implementation, Savannah, GA, USA, 2016: 689-703. |
| 21 | Baumann A, Peinado M, Hunt G C. Shielding applications from an untrusted cloud with haven[J]. ACM Transactions on Computer Systems, 2015, 33(3): 1-26. |
| 22 | 陈璐, 柯文彬, 张立强, 等. 云计算环境下基于系统依赖图的远程证明方案[J]. 武汉大学学报:理学版, 2020, 66(4): 401-408. |
| Chen Lu, Ke Wen-bin, Zhang Li-qiang, et al. A remote attestation scheme based on system dependence graph in cloud computing environment[J]. Journal of Wuhan University(Natural Science Edition), 2020, 66(4): 401-408. | |
| 23 | 荣星, 沈昌祥, 江荣, 等. 基于双层非平衡散列树的云平台远程验证方案[J]. 通信学报, 2017, 38(9): 31-38. |
| Rong Xing, Shen Chang-xiang, Jiang Rong, et al. Remote attestation scheme for cloud platform based on double-layer unbalanced hash tree[J]. Journal on Communications, 2017, 38(9): 31-38. | |
| 24 | Ruan An-bang, Martin A. Repcloud: attesting to cloud service dependency[J]. IEEE Transactions on Services Computing, 2016, 10(5): 675-688. |
| 25 | Shim K. An ID-based aggregate signature scheme with constant pairing computations[J]. Journal of Systems and Software, 2010, 83(10): 1873-1880. |
| [1] | 董延华,刘靓葳,赵靖华,李亮,解方喜. 基于BPNN在线学习预测模型的扭矩实时跟踪控制[J]. 吉林大学学报(工学版), 2021, 51(4): 1405-1413. |
| [2] | 魏晓辉,汤钫宇,李洪亮. 地理分布数据中心的工作流经济高效资源分配[J]. 吉林大学学报(工学版), 2021, 51(4): 1349-1357. |
| [3] | 魏晓辉,周长宝,沈笑先,刘圆圆,童群超. 机器学习加速CALYPSO结构预测的可行性[J]. 吉林大学学报(工学版), 2021, 51(2): 667-676. |
| [4] | 陈蔓,钟勇,李振东. 隐低秩结合低秩表示的多聚焦图像融合[J]. 吉林大学学报(工学版), 2020, 50(1): 297-305. |
| [5] | 张笑东,夏筱筠,吕海峰,公绪超,廉梦佳. 大数据网络并行计算环境中生理数据流动态负载均衡[J]. 吉林大学学报(工学版), 2020, 50(1): 247-254. |
| [6] | 赵宏伟, 刘宇琦, 董立岩, 王玉, 刘陪. 智能交通混合动态路径优化算法[J]. 吉林大学学报(工学版), 2018, 48(4): 1214-1223. |
| [7] | 张浩, 占萌苹, 郭刘香, 李誌, 刘元宁, 张春鹤, 常浩武, 王志强. 基于高通量数据的人体外源性植物miRNA跨界调控建模[J]. 吉林大学学报(工学版), 2018, 48(4): 1206-1213. |
| [8] | 曹婧华, 孔繁森, 冉彦中. 面向服务推荐的QoS成列协同排序算法[J]. 吉林大学学报(工学版), 2018, 48(1): 274-280. |
| [9] | 梁士利, 柴宗谦, 张玲, 吴颜生, 曹春雷. 基于偏X型细胞自动机的图像加密方法[J]. 吉林大学学报(工学版), 2017, 47(5): 1653-1660. |
| [10] | 林冬梅, 张爱华, 沈蓉, 王平, 杨力铭, 陈晓雷. 双目视觉脉搏测量系统中的相机同步采集方法[J]. 吉林大学学报(工学版), 2015, 45(6): 1999-2006. |
| [11] | 康冰, 刘富, 魏祺韡. 基于光谱融合的掌纹精细纹路提取[J]. 吉林大学学报(工学版), 2015, 45(4): 1274-1280. |
| [12] | 刘富,张潇,侯涛,刘云. 基于粗糙集的基因信号属性约简[J]. 吉林大学学报(工学版), 2015, 45(2): 624-629. |
| [13] | 刘元宁,艾露露,段云娜,李誌,田明尧,张浩. 基于局部结构交互的RNA假结预测[J]. 吉林大学学报(工学版), 2015, 45(2): 613-618. |
| [14] | 刘元宁, 徐宝林, 张浩, 陈竟博, 韩烨, 禹剑龙. 基于siRNA-mRNA结合热力学特征的高效siRNA筛选[J]. 吉林大学学报(工学版), 2014, 44(01): 191-195. |
| [15] | 吴佳楠, 周春光, 夏雪飞, 刘桂霞, 沈薇, 周柚. 基于简单统计排名模型的差异表达基因识别[J]. 吉林大学学报(工学版), 2013, 43(04): 1059-1063. |
|
||