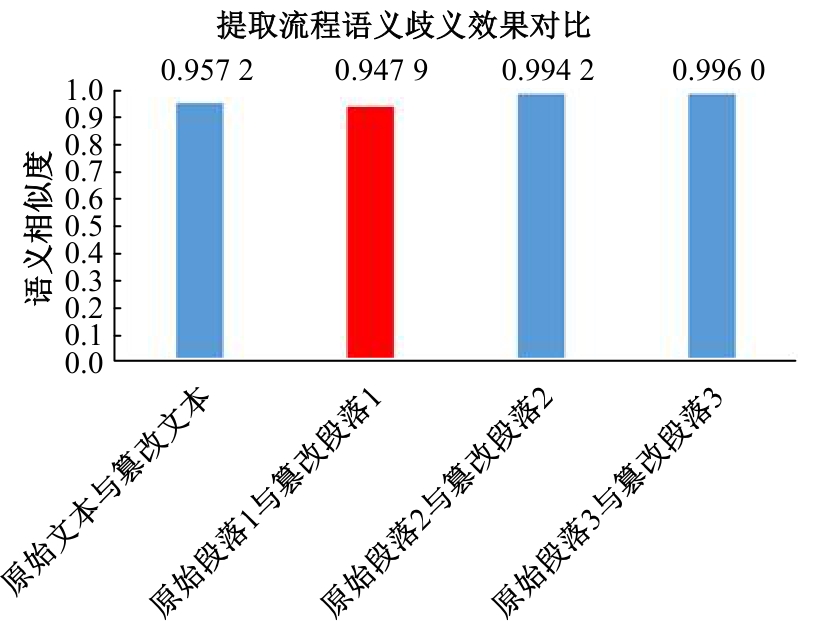
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (11): 3715-3726.doi: 10.13229/j.cnki.jdxbgxb.20240248
Chinese text watermarking algorithm based on chaotic AES and synonym expansion
Shu-ming LI1( ),Bing-nan LI1,Chao YANG2,3
),Bing-nan LI1,Chao YANG2,3
- 1.College of Computer and Information Engineering,Hubei Normal University,Huangshi 435002,China
2.College of Computer,Hubei University,Wuhan 430062,China
3.Hubei Key Laboratory of Big Data Intelligent Analysis and Industry Applications,Hubei University,Wuhan 430062,China
CLC Number:
- TP391
| [1] | 朱强强. 基于汉字笔画微变形的文本隐写方法研究[D]. 杭州: 杭州电子科技大学网络与信息安全学院,2024. |
| Zhu Qiang-qiang. Research on text steganography based on chinese character stroke fine-tuning[D]. Hangzhou: College of Network and Information Security, Hangzhou Dianzi University, 2024. | |
| [2] | 黄瑶, 潘丽丽, 熊思宇, 等. 基于生成对抗网络与多头注意力的文本隐写术[J]. 计算机工程与科学,2023, 45(10): 1789-1796. |
| Huang Yao, Pan Li-li, Xiong Si-yu, et al. Text steganography based on generative adversarial networks and multi-head attention[J]. Journal of Computer Engineering & Science, 2023, 45(10): 1789-1796. | |
| [3] | 费文斌, 唐向宏, 王静, 等. 基于预测误差扩展的可逆文本水印算法[J]. 中文信息学报, 2015, 29(1):133-138. |
| Fei Wen-bin, Tang Xiang-hong, Wang Jing, et al. Reversible text watermarking algorithm based on prediction error expansion[J]. Journal of Chinese Information Processing, 2015, 29(1): 133-138. | |
| [4] | Xiang L Y, Wu W S, Li X, et al. A linguistic steganography based on word indexing compression and candidate selection[J]. Multimedia Tools and Applications, 2018, 77(21): 28969-28989. |
| [5] | 姚晔, 刘书辉, 王慧, 等. 基于字符扰动变形和字库替换的鲁棒中文文本水印[J]. 密码学报, 2023, 10(4): 769-785. |
| Lao Ye, Liu Shu-hui, Wang Hui, et al. Robust chinese text watermarking method based on chinese character glyph perturbation and font replacing[J]. Journal of Cryptologic Research, 2023, 10(4): 769-785. | |
| [6] | 张娜, 张琨, 张先国, 等. 基于主题词与信息熵编码的文本零水印算法[J]. 计算机与数字工程, 2021, 49(8): 1612-1618. |
| Zhang Na, Zhang Kun, Zhang Xian-guo, et al. Text zero-watermarking algorithm based on keywords and information entropy encoding[J]. Journal of Computer & Digital Engineering, 2021, 49(8): 1612-1618. | |
| [7] | Zheng X Y, Wu H Z. Autoregressive linguistic steganography based on BERT and consistency coding[J]. Security and Communication Networks, 2022: 1-11. |
| [8] | Yu L, Lu Y L, Yan X H, et al. MTS-Stega: linguistic steganography based on multi-time-step[J]. Entropy, 2022, 24(5): 585. |
| [9] | 金家立. 基于自动选择编码方式的文本信息隐藏技术研究[D]. 沈阳: 沈阳工业大学信息科学与工程学院,2023. |
| Jin Jia-li. Research on text information hiding technology based on automatic selection encoding[D]. Shenyang: School of Information Science and Engineering, Shenyang University of Technology,2023. | |
| [10] | Reimers N, Gurevych I. Sentence-bert: sentence embeddings using siamese bert-networks[J]. Arxiv Preprint, 2019, 8: 190810084. |
| [11] | Wang X Y, Feng D G, Lai X J, et al. Collisions for hash functions MD 4, MD5, HAVAL-128 and RIPEMD[J/OL]. IACR Cryptology eprint Archive, [2004-08-17]. |
| [12] | Klima V. Tunnels in hash functions: MD5 collisions within a minute[J/OL].IACR Cryptol. ePrint Arch, [2006-04-17]. |
| [13] | Stevens M. Attacks on hash functions and applications[D]. Leiden: Mathematical institute faculty, science Leiden University, 2012. |
| [14] | Rønjom S, Bardeh N G, Helleseth T. Yoyo tricks with AES[C]∥Advances in Cryptology-ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 2017: 217-243. |
| [15] | Bardeh N G, Rønjom S. The exchange attack: how to distinguish six rounds of AES with chosen plaintexts[C]∥International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 2019: 347-370. |
| [16] | Dunkelman O, Keller N, Ronen E, et al. The retracing boomerang attack[C]∥Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 2020: 280-309. |
| [17] | Bardeh N G, Rijmen V. New key recovery attack on reduced-round AES[J]. Cryptology ePrint Archive, 2022(2): 43-62. |
| [1] | Xiu-hui WANG,Yong-bo XU. Chinese named entity recognition algorithm with soft attention mask embedding [J]. Journal of Jilin University(Engineering and Technology Edition), 2026, 56(1): 231-238. |
| [2] | Fei SHAN,Hui LI,Hao SUN,Shi-gang NIE,Zhong-hu SHEN. Pavement distress identification method based on improved simAM-YOLOv8 [J]. Journal of Jilin University(Engineering and Technology Edition), 2026, 56(1): 219-230. |
| [3] | Hai-peng CHEN,Hong-xin LIU,Hui KANG,Xue-jie LIU. Image manipulation localization method based on boundary uncertainty learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(12): 4063-4071. |
| [4] | Hong ZHAO,Yu-xuan MA,Fu-rong SONG. Image adversarial examples generation based on Diff⁃AdvGAN [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(12): 4052-4062. |
| [5] | Ping FENG,Zi-qian YANG,Ren-jie WANG,Shi-yu FENG,Hang WU,Yu SUN. Entity relationship extraction method based on span and semantic features [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(12): 4045-4051. |
| [6] | Yan YANG,Wang-liang SHEN. Multi⁃scale detail enhancement and layered noise suppression algorithm for image dehazing [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(12): 4010-4023. |
| [7] | Tian-min DENG,Peng-fei XIE,Yang YU,Yue-tian CHEN. Method of lane detection based on adaptive fusion of double branch features [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(12): 3840-3851. |
| [8] | Xiao-Dong CAI,Ye-yang HUANG,Li-fang DONG. Semantic similarity model based on augmented positives and interlayer negatives [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(11): 3705-3714. |
| [9] | Yu-dong CAO,Xin-lin LIAO,Xin CHEN,Xu JIA. Vision object detection model with deep active learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(11): 3697-3704. |
| [10] | Rui-feng ZHANG,Fang-zhao GUO,Qiang LI. Chest X-ray images classification based on multi-scale attention information multiplexing network [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(11): 3686-3696. |
| [11] | Hong-bin WANG,Hao-dong TANG,Yan-tuan XIAN,Bo LIU,Xin-liang GU. Knowledge graph alignment based on entity reliable path and semantic aggregates [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(11): 3673-3685. |
| [12] | Lai-wei JIANG,Ce WANG,Hong-yu YANG. Review of multi-object tracking based on deep learning [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(11): 3429-3445. |
| [13] | Lin LIN,Yu-xin CHEN,Wei-zhi NAI. Adaptive real⁃time gesture classification algorithm based on gesture frame sequence extraction [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(9): 3042-3048. |
| [14] | Yan PIAO,Ji-yuan KANG. RAUGAN:infrared image colorization method based on cycle generative adversarial networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(8): 2722-2731. |
| [15] | Pei-ming SUN,Zhe WANG. Optimization method of party affairs activity scheduling based on directional differential evolution algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(8): 2761-2770. |
|
||
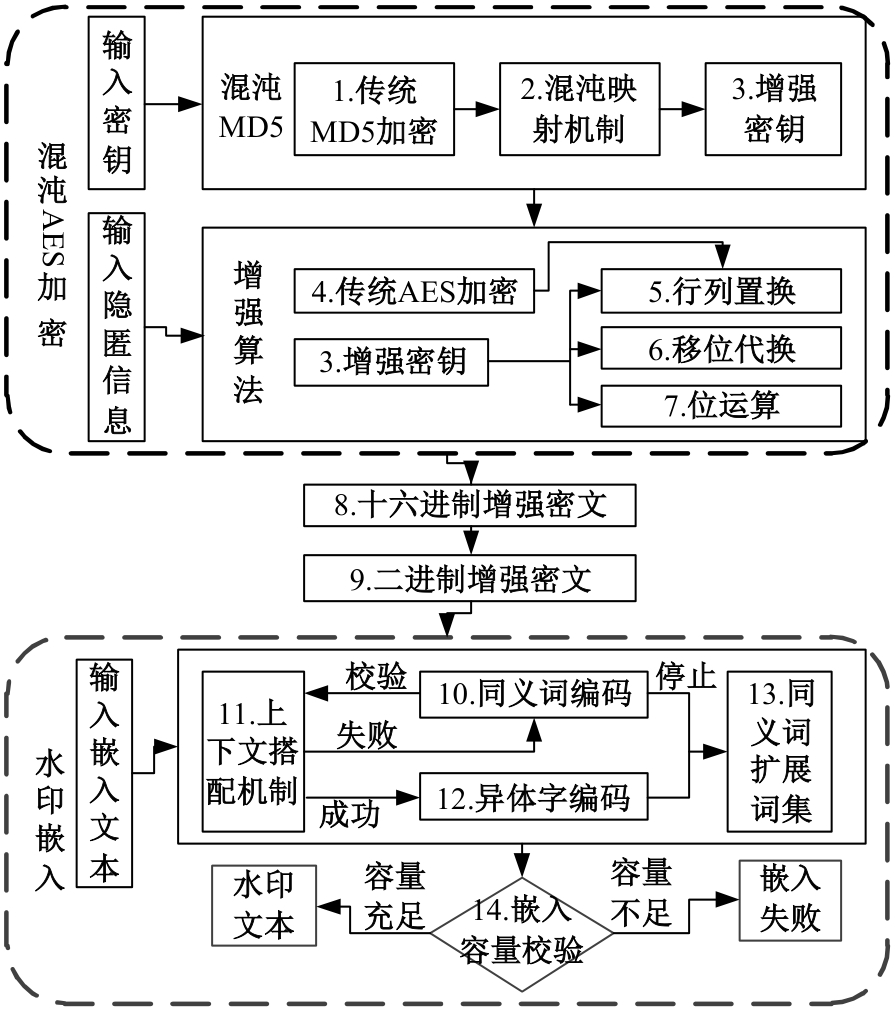
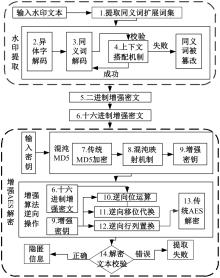
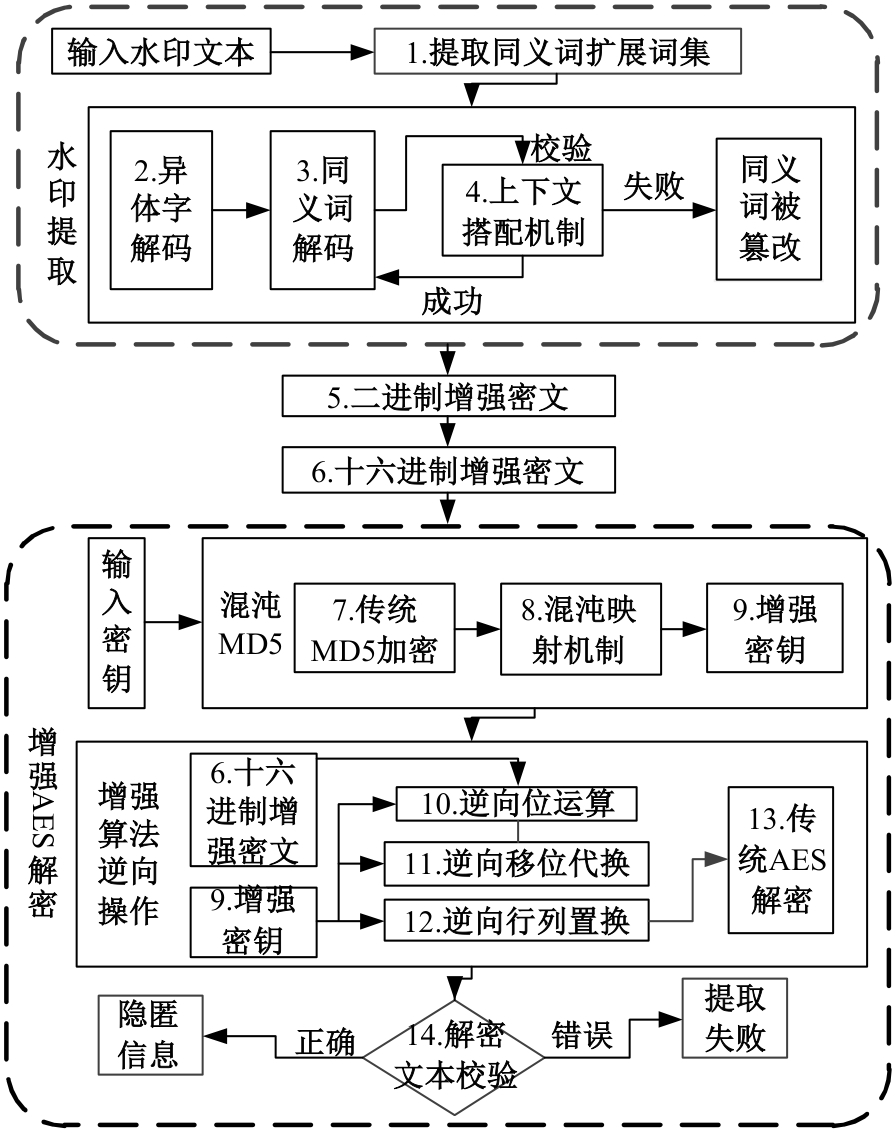
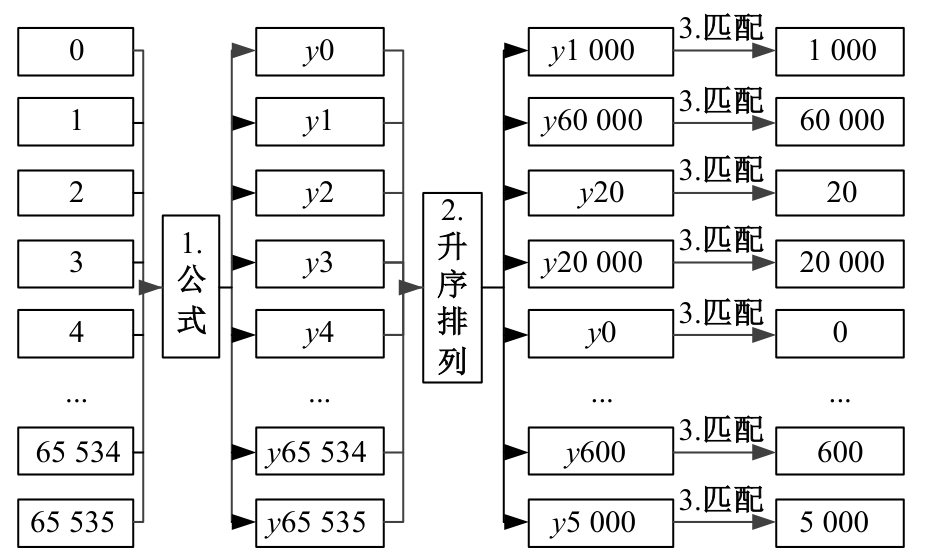
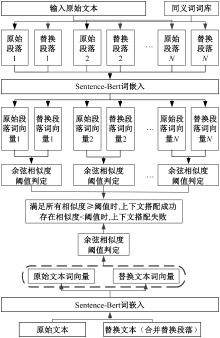
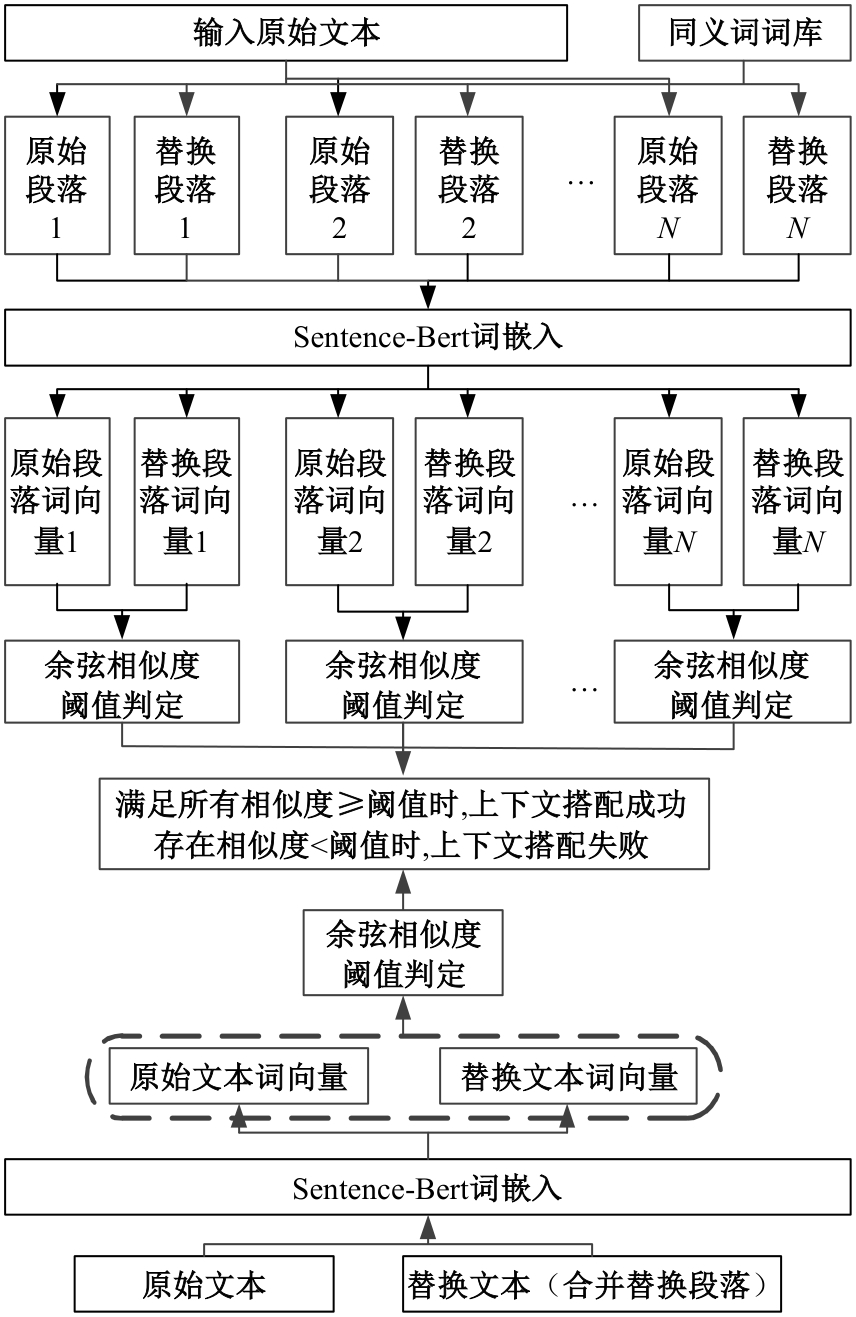




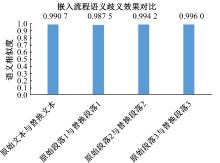
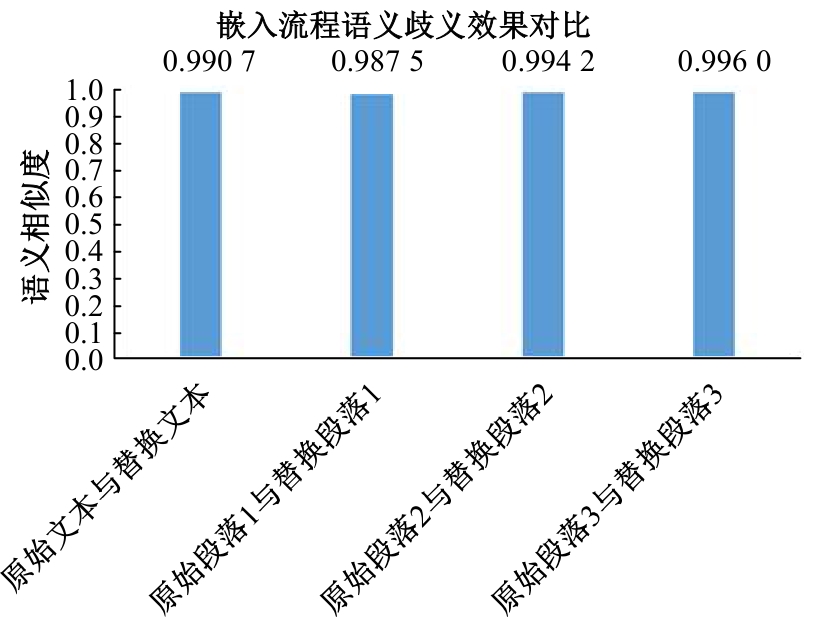
 :1,出—岀:1
:1,出—岀:1