吉林大学学报(工学版) ›› 2021, Vol. 51 ›› Issue (6): 2253-2258.doi: 10.13229/j.cnki.jdxbgxb20200814
• 通信与控制工程 • 上一篇
基于被动分簇算法的即时通信网络协议漏洞检测
- 1.山西大同大学 计算机与网络工程学院,山西 大同 037009
2.山西大同大学 数学与统计学院,山西 大同 037009
Vulnerability detection of instant messaging network protocol based on passive clustering algorithm
Jie ZHANG1( ),Wen JING1,Fu CHEN2
),Wen JING1,Fu CHEN2
- 1.School of Computer and Network Engineering,Shanxi Datong University,Datong 037009,China
2.School of Mathematics and Statistics,Shanxi Datong University,Datong 037009,China.
摘要:
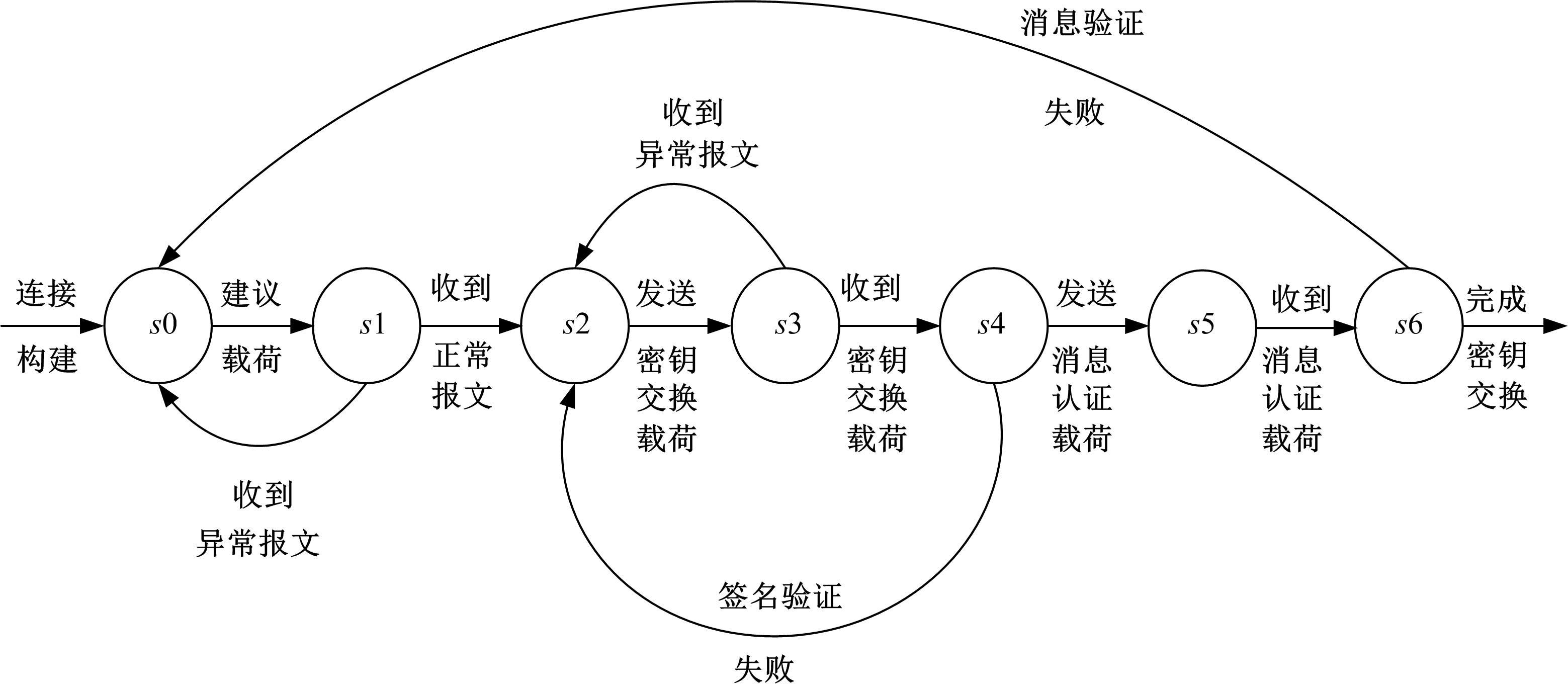
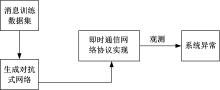
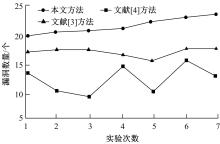
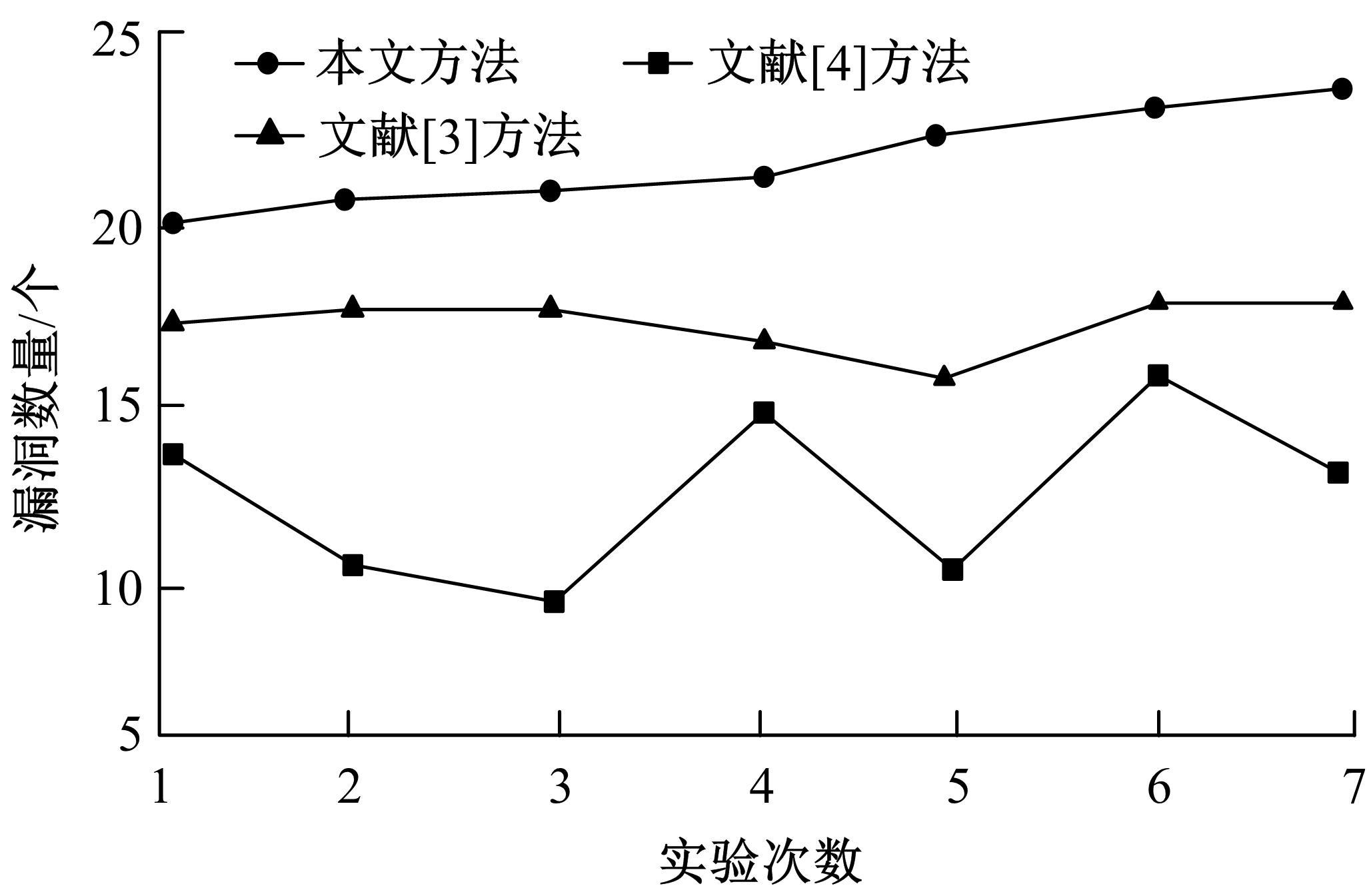
为有效挖掘出网络协议漏洞,防止恶意攻击者泄露协议机密信息,维护协议运行环境安全,提出了一种基于被动分簇算法的即时通信网络协议漏洞检测方法。该方法使用被动分簇算法中先声明者优先机制挑选簇首,按照网络健壮性和能源有效性间的均衡原则明确网关节点;对待检测协议实施形式化定义,获得协议工作详细流程;采用AFL模糊检测工具对协议的正、负样本过采样,得到完整样本集合;将前向反馈网络和支持向量机分别当作生成对抗式网络中的生成模型与判别模型,利用拉格朗日算法得到检测用例数据,将其代入协议系统内完成漏洞检测。仿真结果证明,所提方法具有极高的漏洞检测精度与效率,能有效确保网络协议运行安全性。
中图分类号:
- TP357
| 1 | 冯文博, 洪征, 吴礼发,等. 网络协议识别技术综述[J]. 计算机应用, 2019, 39(12):3604-3614. |
| Feng Wen-bo, Hong Zheng, Wu Li-fa, et al. Overview of network protocol identification technology [J]. Computer Applications, 2019, 39 (12): 3604-3614. | |
| 2 | Atilgan C, Nasibov E N. A space efficient minimum spanning tree approach to the fuzzy Joint points clustering algorithm[J]. IEEE Transactions on Fuzzy Systems, 2019, 27(6):1317-1322. |
| 3 | 邓兆琨, 陆余良, 黄钊, 等. 基于程序建模的网络程序漏洞检测技术[J]. 北京航空航天大学学报, 2019, 45(4):796-803. |
| Deng Zhao-kun, Lu Yu-liang, Huang Zhao, et al. Network program vulnerability detection technology based on program modeling[J]. Journal of Beijing University of Aeronautics and Astronautics, 2019, 45(4):796-803. | |
| 4 | 李佳莉, 陈永乐, 李志, 等. 基于协议状态图遍历的RTSP协议漏洞挖掘[J]. 计算机科学, 2018, 45(9):178-183. |
| Li Jia-li, Chen Yong-le, Li Zhi, et al. RTSP protocol vulnerability mining based on traversal of protocol state graph [J]. Computer Science, 2018, 45 (9): 178-183. | |
| 5 | Huang C, Molisch A F, Geng Y A, et al. Trajectory-Joint clustering algorithm for time-varying channel modeling[J]. IEEE Transactions on Vehicular Technology, 2020, 69(1):1041-1045. |
| 6 | 丁旭, 黄成, 吴晓蓓,等. 基于压缩感知的传感器网络中概率负载均衡的数据路由协议[J]. 控制与决策, 2018, 33(06):1041-1047. |
| Ding Xu, Huang Cheng, Wu Xiao-bei, et al. Data routing protocol for probabilistic load balancing in sensor networks based on compressed sensing [J]. Control and Decision, 2018, 33 (06): 1041-1047 | |
| 7 | Tan B, Elnaggar R, Fung J M, et al. Towards hardware-based IP vulnerability detection and post-deployment patching in systems-on-chip[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2020, PP(99):1-1. |
| 8 | 夏之阳, 易平, 杨涛. 基于神经网络与代码相似性的静态漏洞检测[J]. 计算机工程, 2019, 45(12):141-146. |
| Xia Zhi-yang, Yi Ping, Yang Tao. Static vulnerability detection based on neural network and code similarity [J]. Computer Engineering, 2019, 45 (12): 141-146. | |
| 9 | Nancy P, Muthurajkumar S, Ganapathy S, et al. Intrusion detection using dynamic feature selection and fuzzy temporal decision tree classification for wireless sensor networks[J]. IET Communications, 2020, 14(5):888-895. |
| 10 | 苏彬, 马丽梅, 崔宝江. 适用于传感器采集网络的轻量级安全通信协议[J]. 计算机工程与设计, 2018, 39(5): 1262-1268. |
| Su Bin, Ma Li-mei, Cui Bao-jiang. Lightweight secure communication protocol for sensor acquisition networks [J]. Computer engineering and design, 2018, 39 (5): 1262-1268. | |
| 11 | Zhao Z N, Wang J, Guo H W. Analysis of vulnerability propagation for the all-optical network based on Bio-PEPA[J]. Wireless Networks, 2019, 25(6):3513-3529. |
| 12 | Nunes P, Medeiros I, Fonseca J, et al. An empirical study on combining diverse static analysis tools for web security vulnerabilities based on development scenarios[J]. Computing, 2019, 101(2):161-185. |
| 13 | 荆琛, 傅晓彤, 董伟,等. 基于Q-学习算法的有状态网络协议模糊测试方法研究[J]. 电子技术应用, 2020, 46(4):49-52, 56. |
| Jing Chen, Fu Xiao-tong, Dong Wei, et al. Research on fuzzy testing method of stateful network protocol based on Q-learning algorithm[J]. Electronic Technology Application, 2020, 46 (4): 49-52, 56. | |
| 14 | He F, Zhang B. A protocol of potential advantage in the low frequency range to gravitational wave detection with space based optical atomic clocks[J]. The European Physical Journal D, 2020, 74(5):1-6. |
| 15 | 张志华. 基于渗透测试的网络安全漏洞实时侦测技术[J]. 科学技术与工程, 2018, 18(20):297-302. |
| Zhang Zhi-hua, Real time detection technology of network security vulnerability based on penetration test [J]. Science, technology and engineering, 2018, 18(20): 297-302. | |
| 16 | Kim J, Cho K, Kim Y K, et al. Study on peak misdetection recovery of key exchange protocol using heartbeat[J]. Journal of supercomputing, 2019, 75(6):3288-3301. |
| 17 | 王培超, 周鋆, 朱承, 等. 基于贝叶斯网络的XSS攻击检测方法[J]. 中国科学技术大学学报, 2019, 49(2):166-172. |
| Wang Pei-chao, Zhou Yun, Zhu Cheng, et al. XSS attack detection method based on Bayesian networks [J]. Journal of China University of Science and Technology, 2019, 49 (2): 166-172. | |
| 18 | Han Y, Seed D, Wang C, et al. Delay-aware application protocol for internet of things[J]. IEEE Network, 2018 (1):1-8. |
| 19 | 许力, 李光辉. 基于信任机制的无线传感器网络多协议层入侵检测方法[J]. 传感技术学报, 2019, 32(5):101-110. |
| Xu Li, Li Guang-hui. Multi protocol layer intrusion detection method for wireless sensor networks based on trust mechanism [J]. Journal of sensing technology, 2019, 32 (5): 101-110. | |
| 20 | Wei X, Gao S, Huang T, et al. Complex network-based cascading faults graph for the analysis of transmission network vulnerability[J]. IEEE Transactions on Industrial Informatics, 2019, 15(3):1265-1276. |
| [1] | 董丽丽,杨丹,张翔. 基于深度学习的大规模语义文本重叠区域检索[J]. 吉林大学学报(工学版), 2021, 51(5): 1817-1822. |
| [2] | 金立生,郭柏苍,王芳荣,石健. 基于改进YOLOv3的车辆前方动态多目标检测算法[J]. 吉林大学学报(工学版), 2021, 51(4): 1427-1436. |
| [3] | 兰凤崇,李继文,陈吉清. 面向动态场景复合深度学习与并行计算的DG-SLAM算法[J]. 吉林大学学报(工学版), 2021, 51(4): 1437-1446. |
| [4] | 李锦青,周健,底晓强. 基于循环生成对抗网络的学习型光学图像加密方案[J]. 吉林大学学报(工学版), 2021, 51(3): 1060-1066. |
| [5] | 袁哲明,袁鸿杰,言雨璇,李钎,刘双清,谭泗桥. 基于深度学习的轻量化田间昆虫识别及分类模型[J]. 吉林大学学报(工学版), 2021, 51(3): 1131-1139. |
| [6] | 彭博,张媛媛,王玉婷,唐聚,谢济铭. 基于自动编码机-分类器的视频交通状态自动识别[J]. 吉林大学学报(工学版), 2021, 51(3): 886-892. |
| [7] | 宋震,李俊良,刘贵强. 基于深度学习和限幅模糊的变转速液压动力源恒流量预测方法[J]. 吉林大学学报(工学版), 2021, 51(3): 1106-1110. |
| [8] | 赵宏伟,刘晓涵,张媛,范丽丽,龙曼丽,臧雪柏. 基于关键点注意力和通道注意力的服装分类算法[J]. 吉林大学学报(工学版), 2020, 50(5): 1765-1770. |
| [9] | 谌华,郭伟,闫敬文,卓文浩,吴良斌. 基于深度学习的SAR图像道路识别新方法[J]. 吉林大学学报(工学版), 2020, 50(5): 1778-1787. |
| [10] | 郜峰利,陶敏,李雪妍,何昕,杨帆,王卓,宋俊峰,佟丹. 基于深度学习的CT影像脑卒中精准分割[J]. 吉林大学学报(工学版), 2020, 50(2): 678-684. |
| [11] | 徐谦,李颖,王刚. 基于深度学习的行人和车辆检测[J]. 吉林大学学报(工学版), 2019, 49(5): 1661-1667. |
| [12] | 郭立民,陈鑫,陈涛. 基于AlexNet模型的雷达信号调制类型识别[J]. 吉林大学学报(工学版), 2019, 49(3): 1000-1008. |
| [13] | 李抵非, 田地, 胡雄伟. 基于分布式内存计算的深度学习方法[J]. 吉林大学学报(工学版), 2015, 45(3): 921-925. |
|
||