吉林大学学报(工学版) ›› 2023, Vol. 53 ›› Issue (10): 2897-2908.doi: 10.13229/j.cnki.jdxbgxb.20211336
面向SaaS隐私保护的自适应访问控制方法
- 1.南京工程学院 计算机工程学院,南京 211167
2.南京航空航天大学 计算机科学与技术学院,南京 210016
Adaptive access control method for SaaS privacy protection
Da-juan FAN1,2( ),Zhi-qiu HUANG2,Yan CAO2
),Zhi-qiu HUANG2,Yan CAO2
- 1.School of Computer Engineering,Nanjing Institute of Technology,Nanjing 211167,China
2.College of Computer Science and Technology,Nanjing University of Aeronautics and Astronautics,Nanjing 210016,China
摘要:
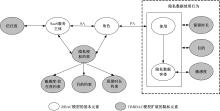
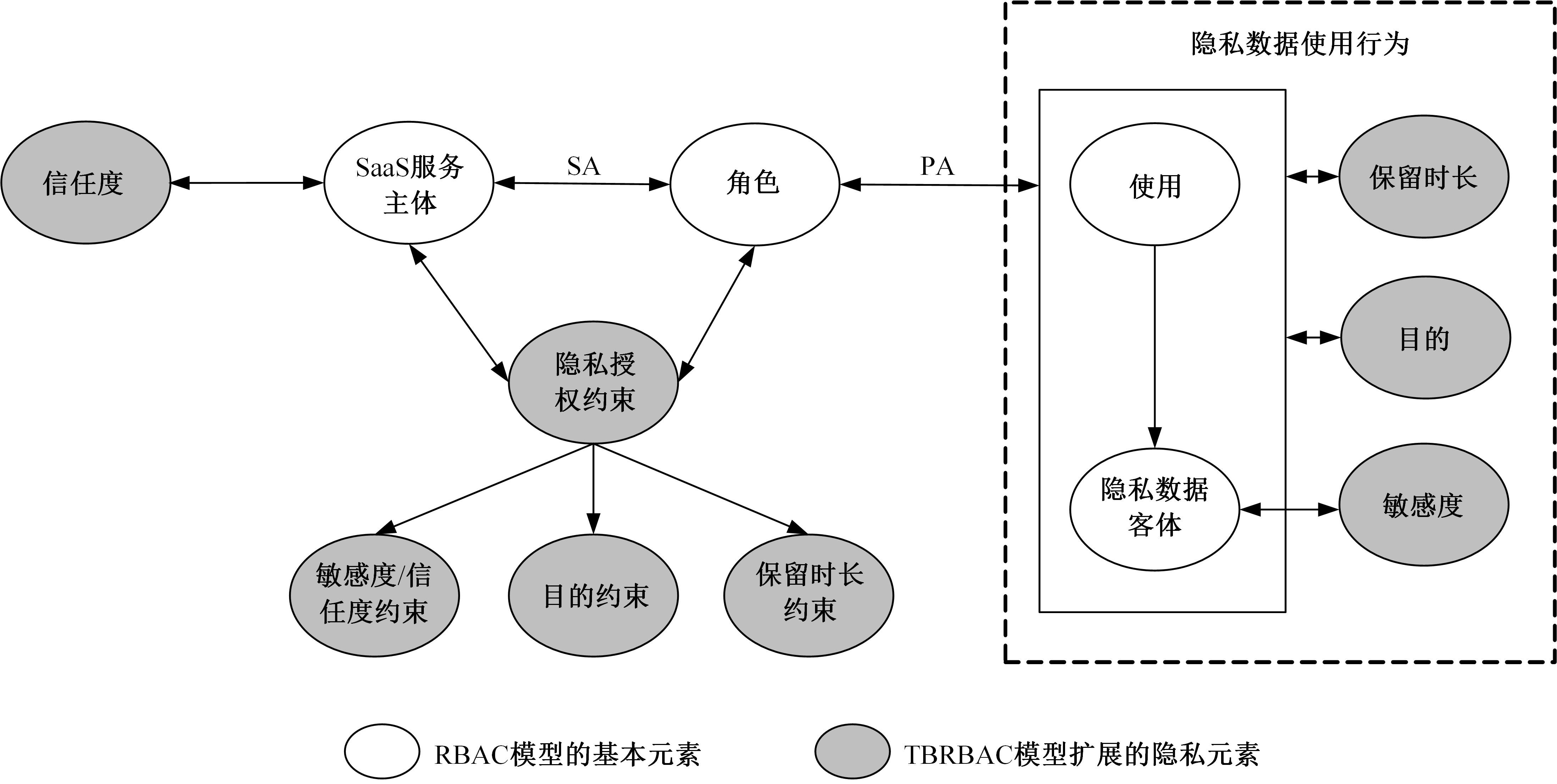
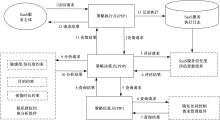
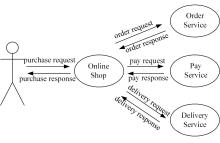
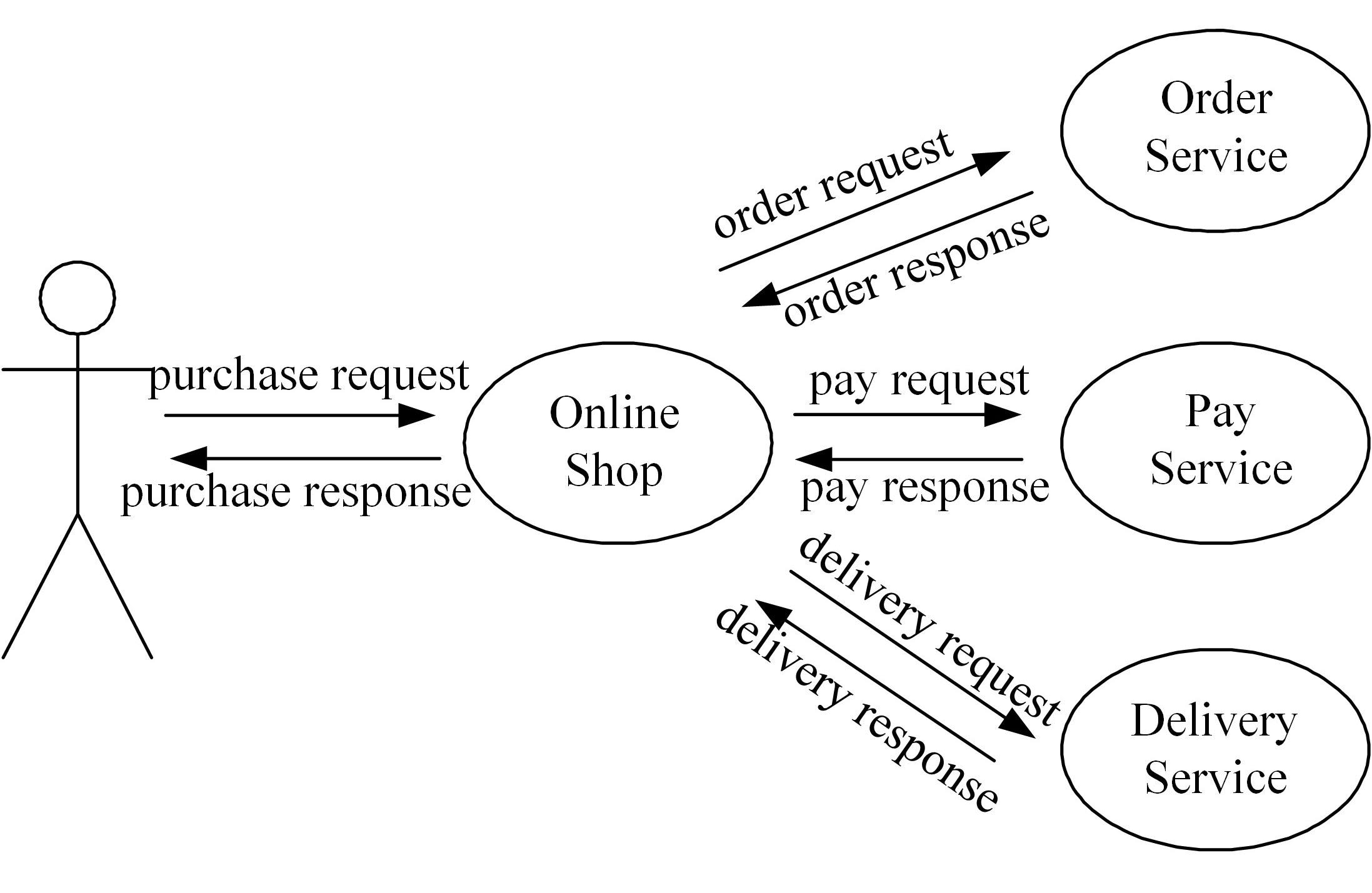
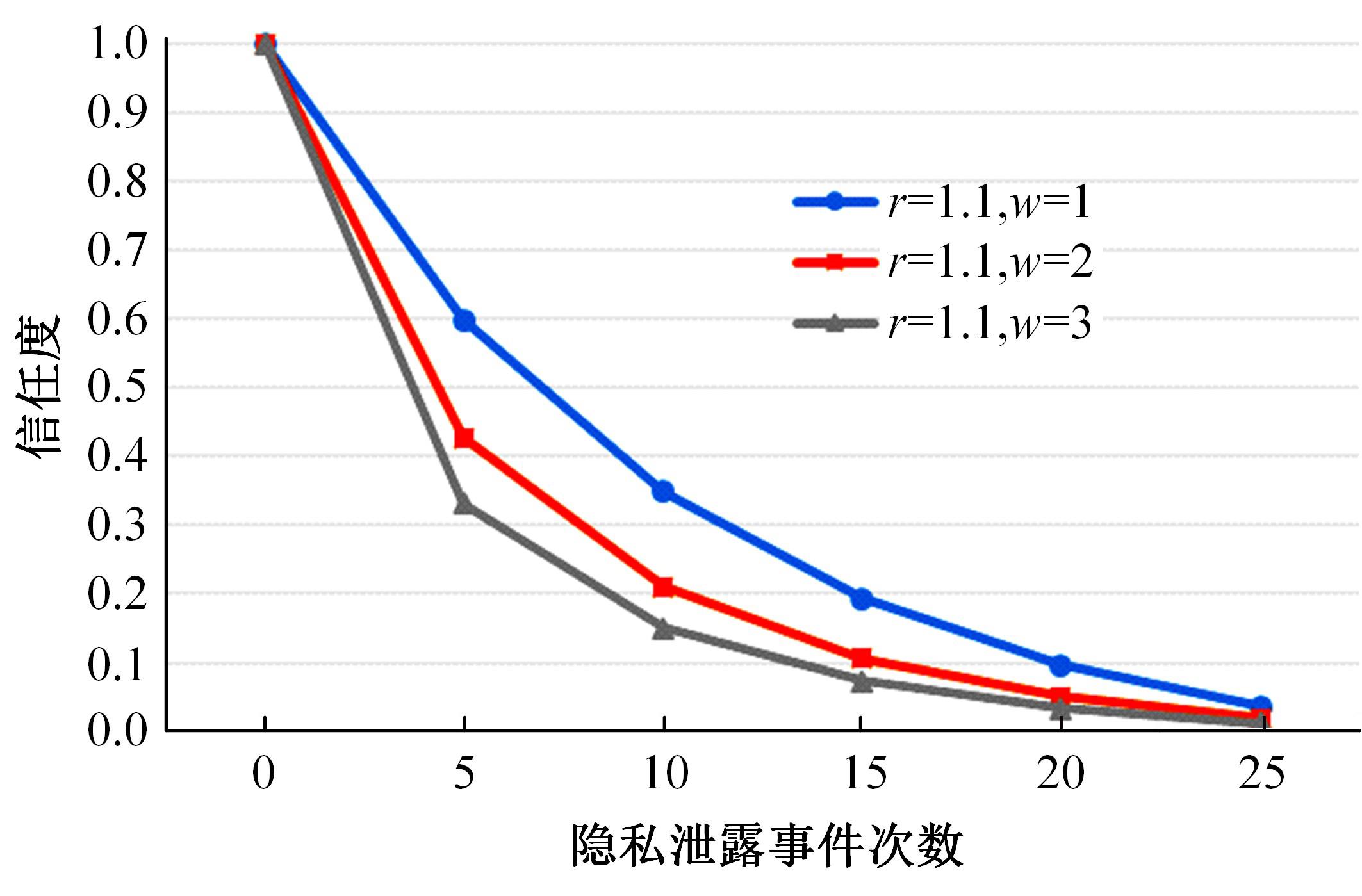
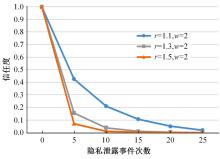
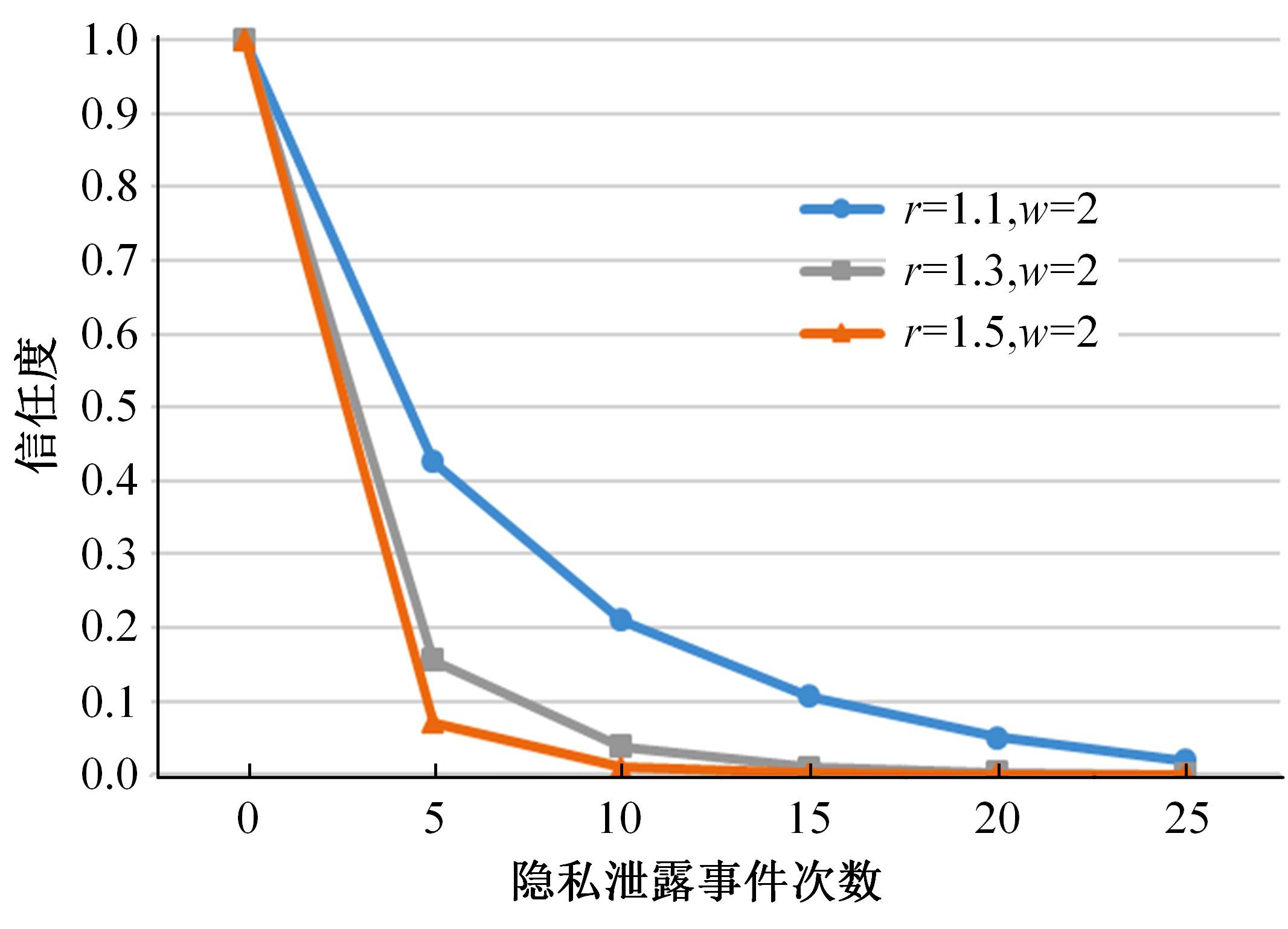
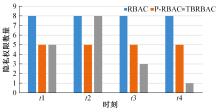
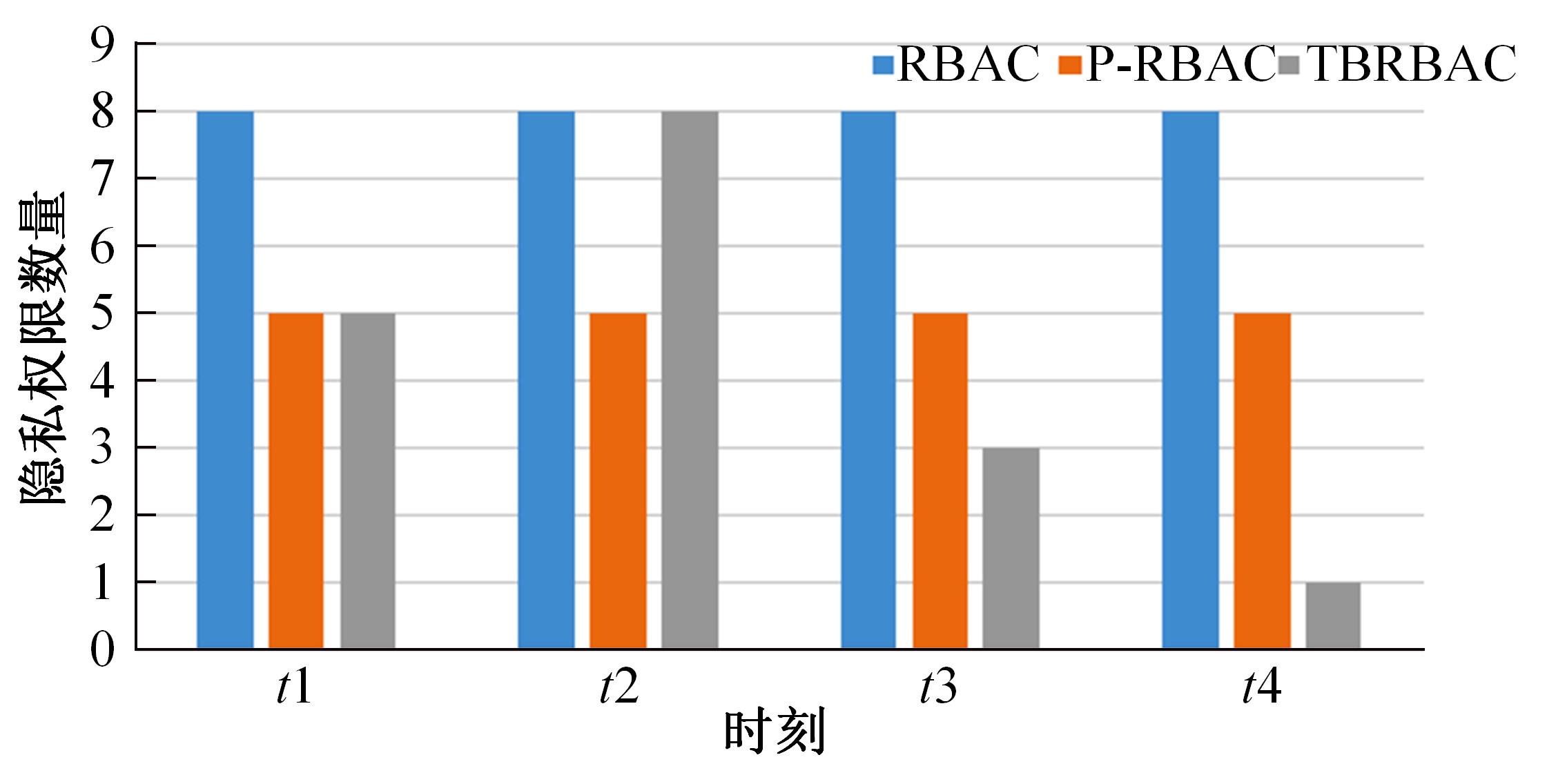
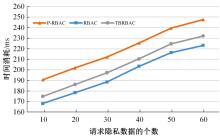
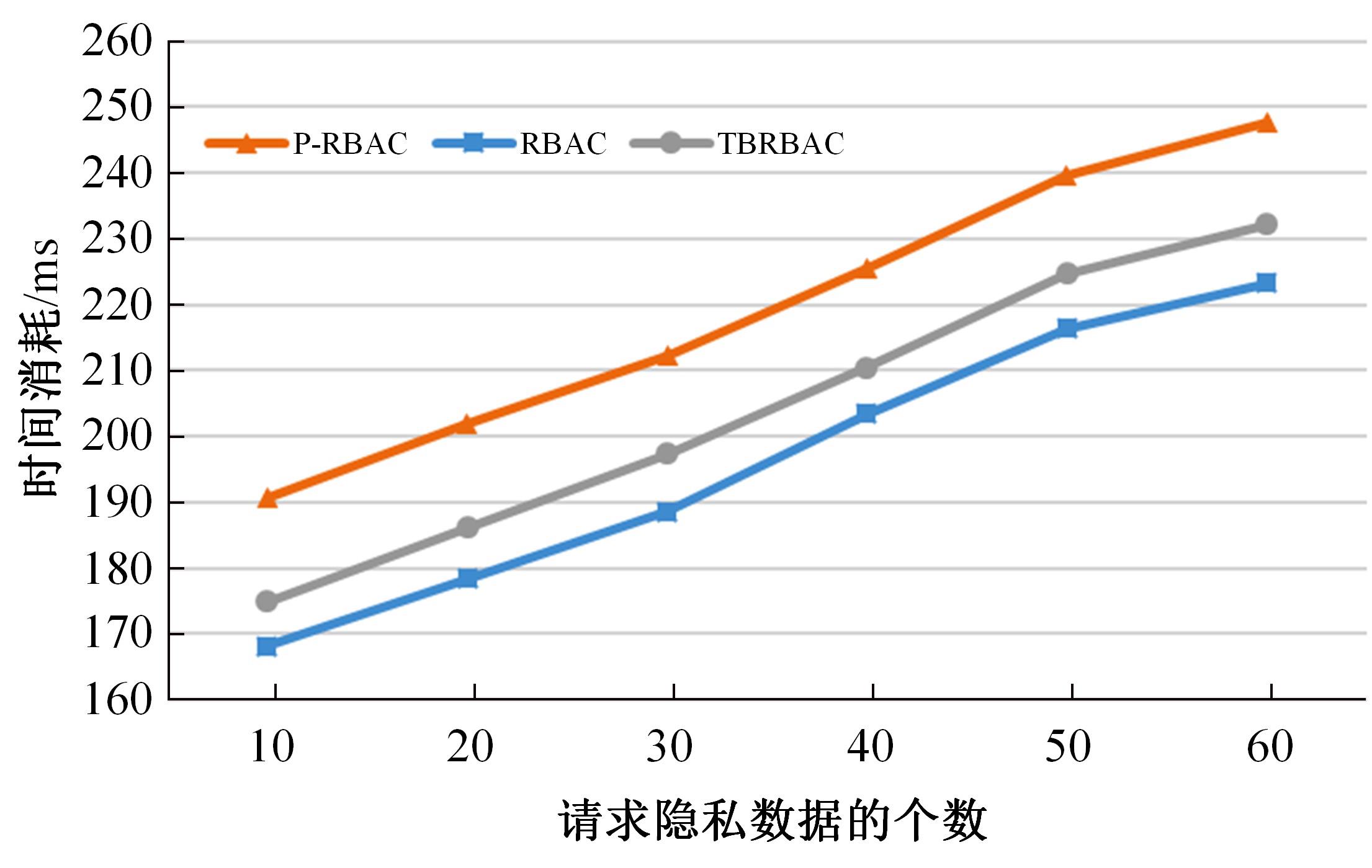
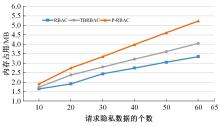
针对现有访问控制方法未针对云计算隐私保护特征且缺少动态隐私授权机制,无法在运行过程中自适应保护隐私数据的不足,通过对基于角色的访问控制(RBAC)模型进行信任度和隐私使用行为扩展,提出了一种面向云计算SaaS层隐私保护的访问控制模型TBRBAC。在此基础上,提出了一种SaaS服务信任度评估和动态更新机制,给出了基于TBRBAC(Trust and Behavior based RBAC)模型的自适应隐私访问控制系统的体系结构、执行流程以及授权分析算法,讨论了自适应访问控制流程的合理性,并通过实例分析和实验验证说明了本文方法的可行性和有效性。该方法能够实现运行时动态隐私授权及细粒度的隐私访问控制,增强了云计算环境下隐私数据的安全保护。
中图分类号:
- TP311
| 1 | Stephanie V, Chamikara M, Khalil I, et al. Privacy-preserving location data stream clustering on mobile edge computing and cloud[J]. Information Systems, 2021, 10(2): 17-28. |
| 2 | Iyengar R, Zoom Fung B., the video conferencing app everyone is using, faces questions over privacy[EB/OL]. [2020-04-01]. . |
| 3 | Sun P. Research on adaptive relationship between trust and privacy in cloud service[J]. IEEE Access, 2021, 9: 43214-43227. |
| 4 | 彭焕峰, 黄志球, 范大娟, 等. 面向服务组合的用户隐私需求规约与验证方法[J]. 软件学报, 2016, 27(8): 1948-1963. |
| Peng Huan-feng, Huang Zhi-qiu, Fan Da-juan, et al. Specification and verification of user privacy requirements for web service composition[J]. Journal of Software, 2016, 27(8): 1948-1963. | |
| 5 | Ding W, Hu R, Yan Z, et al. An extended framework of privacy-preserving computation with flexible access control[J]. IEEE Transactions on Network and Service Management, 2020, 17(2): 918-930. |
| 6 | Qun N, Bertino I E, Lobo J, et al. Privacy-aware role-based access control[J]. ACM Transactions on Information & System Security, 2010, 13(3): 1-31. |
| 7 | Wang H, Sun L L, Bertino E. Building access control policy model for privacy preserving and testing policy conflicting problems[J]. Journal of Computer & System Sciences, 2014, 80(8): 1493-1503. |
| 8 | Omoronyia I. Privacy engineering in dynamic settings[C]∥Proc of IEEE/ACM International Conference on Software Engineering Companion, Washington, USA, 2017: 297-299. |
| 9 | Sun P. Research on cloud computing service based on trust access control[J]. International Journal of Engineering Business Management, 2020, 12: 1-13. |
| 10 | 余波, 台宪青, 马治杰. 云计算环境下基于属性和信任的RBAC模型研究[J]. 计算机工程与应用, 2020, 56(9): 84-92. |
| Yu Bo, Tai Xian-qing, Ma Zhi-jie. Study on attribute and trust-based RBAC model in cloud computing[J]. Computer Engineering and Applications, 2020, 56(9): 84-92. | |
| 11 | Kolter J, Netter M, Pernul G. Visualizing past personal data disclosures[C]∥Proceedings of IEEE International Conference on Availability, Reliability, and Security, Krakow, Poland, 2010: 131-139. |
| 12 | Jiang J X, Huang Z Q, Ma W W, et al. Using information flow analysis to detect implicit information leaks for web service composition[J]. Frontiers of Information Technology & Electronic Engineering, 2018, 19(4): 494-502. |
| 13 | Pitsiladis G V, Stefaneas P. Implementation of privacy calculus and its type checking in Maude[C]∥Proc of the 8th International Symposium on Leveraging Applications of Formal Methods, Verification and Validation, Limassol, Cyprus, 2018: 477-493. |
| 14 | Costante E, Paci F, Zannone N. Privacy-aware web service composition and ranking[C]∥Proc of the 20th IEEE International Conference on Web Services, Salt Lake City, USA, 2013: 131-138. |
| 15 | Ke C B, Xiao F, Huang Z Q . et al. Ontology-based privacy data chain disclosure discovery method for big data[J]. IEEE Transactions on Services Computing,2022,15(1): 59-68. |
| 16 | Accorsi R, Lehmann A, Lohmann N. Information leak detection in business process models[J]. Theory, Application, and Tool Support: Information Systems, 2015, 47: 244-257. |
| 17 | Ding H F, Peng C G, Tian Y L, et al. Privacy risk adaptive access control model via evolutionary game[J]. Journal on Communications, 2019, 40(12): 9-20. |
| 18 | Amardeep K, Amandeep V. An abstract model for adaptive access control in cloud computing[C]∥Proc of International Conference on Recent Advancement on Computer and Communication, Andhra Pradesh, India, 2018: 269-277. |
| [1] | 张刘,曾庆铭,赵寰宇,范国伟. 基于Lyapunov理论的卫星大挠性太阳能帆板分布式自适应振动抑制控制方法[J]. 吉林大学学报(工学版), 2023, 53(9): 2676-2685. |
| [2] | 于雅静,郭健,王荣浩,秦伟,宋明武,向峥嵘. 基于状态观测器的多四旋翼无人机时变编队控制[J]. 吉林大学学报(工学版), 2023, 53(3): 871-882. |
| [3] | 樊敏,宋世军. 基于多源大数据分析的图像特征智能识别模型[J]. 吉林大学学报(工学版), 2023, 53(2): 555-561. |
| [4] | 吴剑,许斌. 基于CEEMDAN理论的堆积层滑坡位移区间预测模型及仿真[J]. 吉林大学学报(工学版), 2023, 53(2): 562-568. |
| [5] | 马敏,胡大伟,舒兰,马壮林. 城市轨道交通网络韧性评估及恢复策略[J]. 吉林大学学报(工学版), 2023, 53(2): 396-404. |
| [6] | 白丽丽,姜封国,周玉明,曾枭. 基于改进鲸鱼算法的结构可靠性优化设计[J]. 吉林大学学报(工学版), 2023, 53(11): 3160-3165. |
| [7] | 武狄,何鸣. 基于机器视觉的视频SAR运动目标检测方法[J]. 吉林大学学报(工学版), 2023, 53(11): 3214-3220. |
| [8] | 陈永刚,许继业,王海涌,熊文祥. 基于自适应神经模糊网络的转辙机故障诊断方法[J]. 吉林大学学报(工学版), 2023, 53(11): 3274-3280. |
| [9] | 杜睿山,陈雨欣,孟令东. 可信云计算平台多源大数据时间序列调度算法[J]. 吉林大学学报(工学版), 2023, 53(11): 3194-3200. |
| [10] | 董立岩,梁伟业,王越群,李永丽. 基于会话的结合全局潜在信息的图神经网络推荐模型[J]. 吉林大学学报(工学版), 2023, 53(10): 2964-2972. |
| [11] | 秦严严,杨晓庆,王昊. 智能网联混合交通流CO2排放影响及改善方法[J]. 吉林大学学报(工学版), 2023, 53(1): 150-158. |
| [12] | 李永明,裴小轩,伊曙东. 混合动力汽车动力电池自适应神经网络优化控制[J]. 吉林大学学报(工学版), 2022, 52(9): 2063-2068. |
| [13] | 张冲,胡云峰,宫洵,孙耀. 燃料电池阴极流量无模型自适应滑模控制器设计[J]. 吉林大学学报(工学版), 2022, 52(9): 2085-2095. |
| [14] | 刘岩,丁天威,王宇鹏,都京,赵洪辉. 基于自适应控制的燃料电池发动机热管理策略[J]. 吉林大学学报(工学版), 2022, 52(9): 2168-2174. |
| [15] | 王克勇,鲍大同,周苏. 基于数据驱动的车用燃料电池故障在线自适应诊断算法[J]. 吉林大学学报(工学版), 2022, 52(9): 2107-2118. |
|
||