吉林大学学报(工学版) ›› 2020, Vol. 50 ›› Issue (2): 692-702.doi: 10.13229/j.cnki.jdxbgxb20181170
• 计算机科学与技术 • 上一篇
基于离散优化算法和机器学习的传感云入侵检测
- 1.西安航空学院 计算机学院, 西安 710077
2.西北工业大学 计算机学院, 西安 710072
3.河北北方学院 信息科学与工程学院,河北 张家口 075000
Sensor cloud intrusion detection based on discrete optimization algorithm and machine learning
Zhou-zhou LIU1,2( ),Wen-xiao YIN3,Qian-yun ZHANG1,Han PENG2
),Wen-xiao YIN3,Qian-yun ZHANG1,Han PENG2
- 1.School of Computer Science, Xi′an Aeronautical University, Xi′an, 710077, China
2.School of Information Science and Engineering, Hebei North University, Zhangjiakou,075000, China
3.School of Computer Science, Northwestern Polytechnical University, Xi′an, 710072, China
摘要:
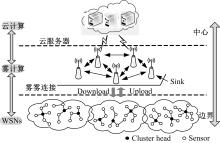
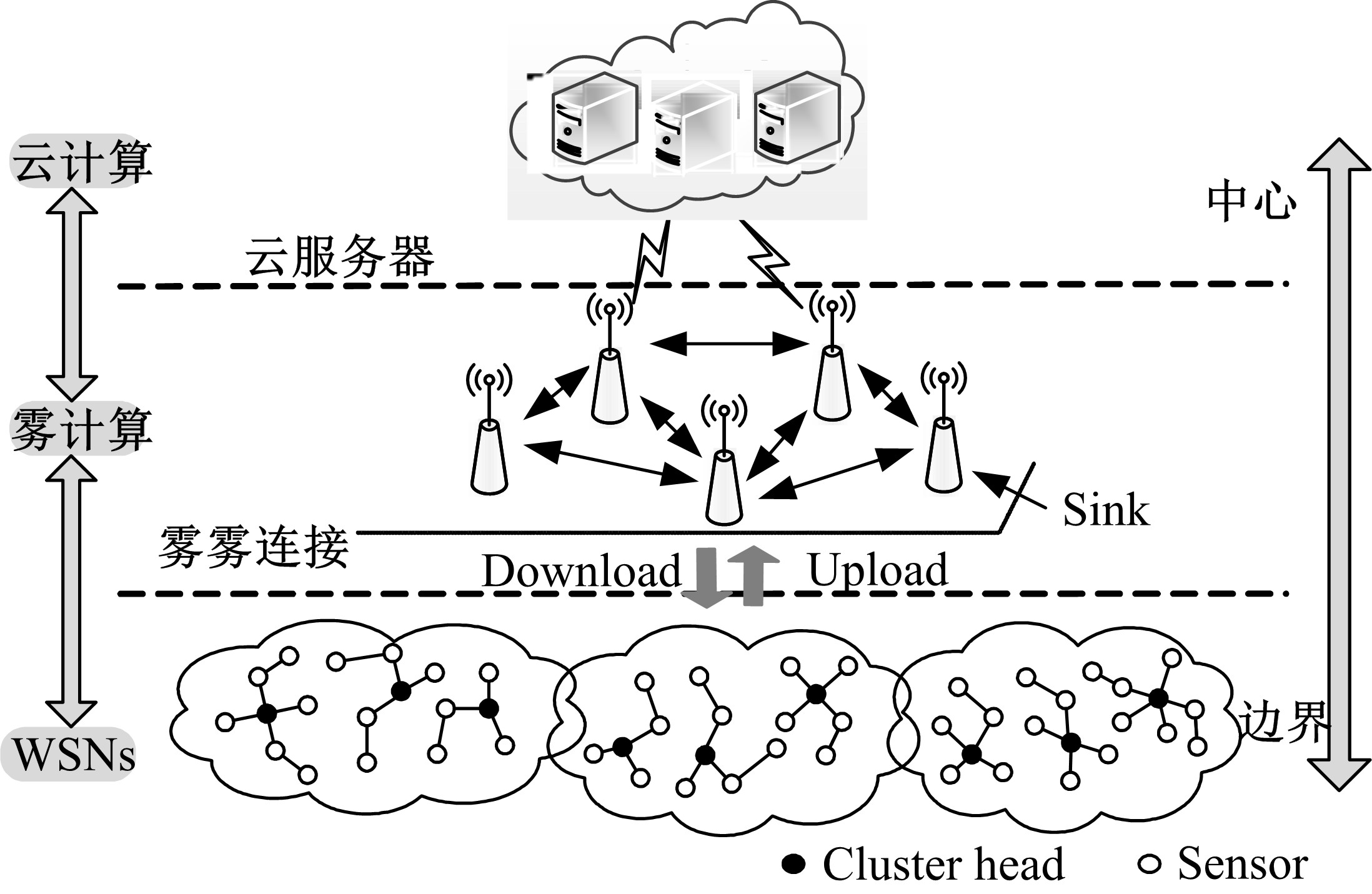
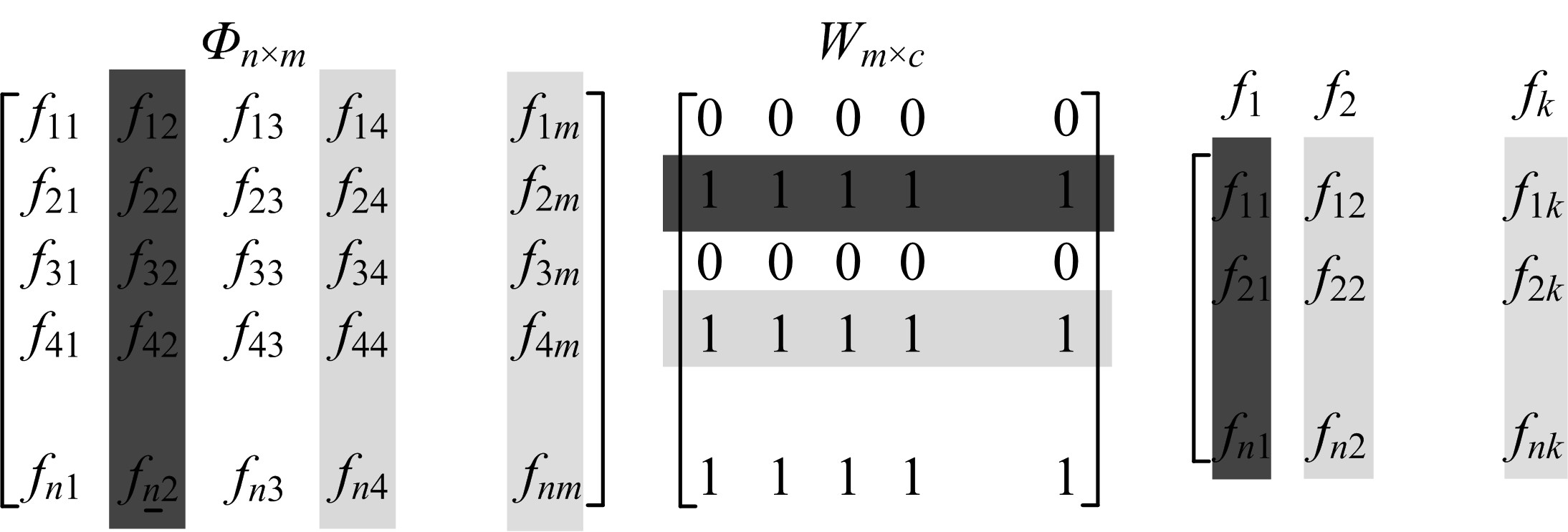
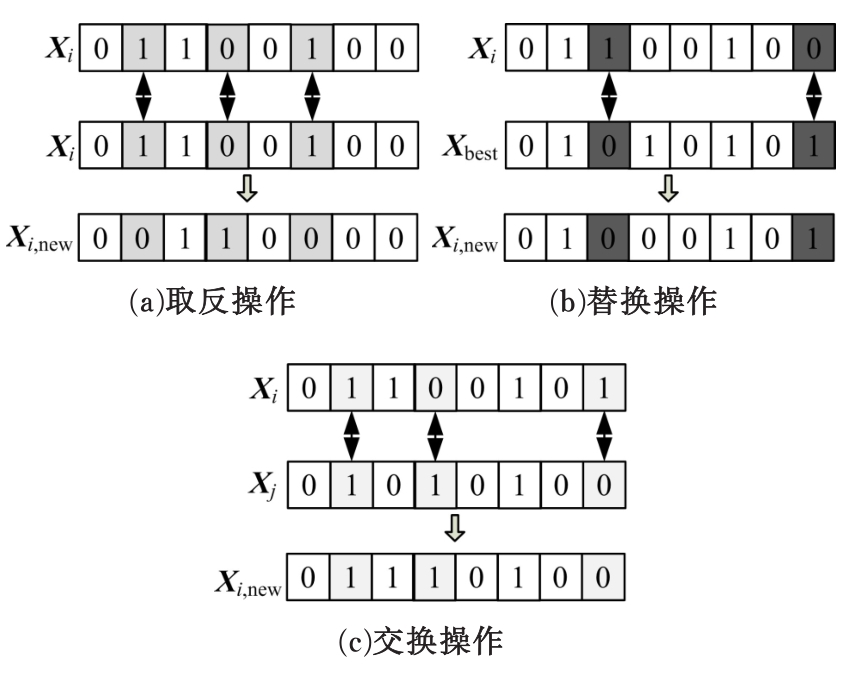
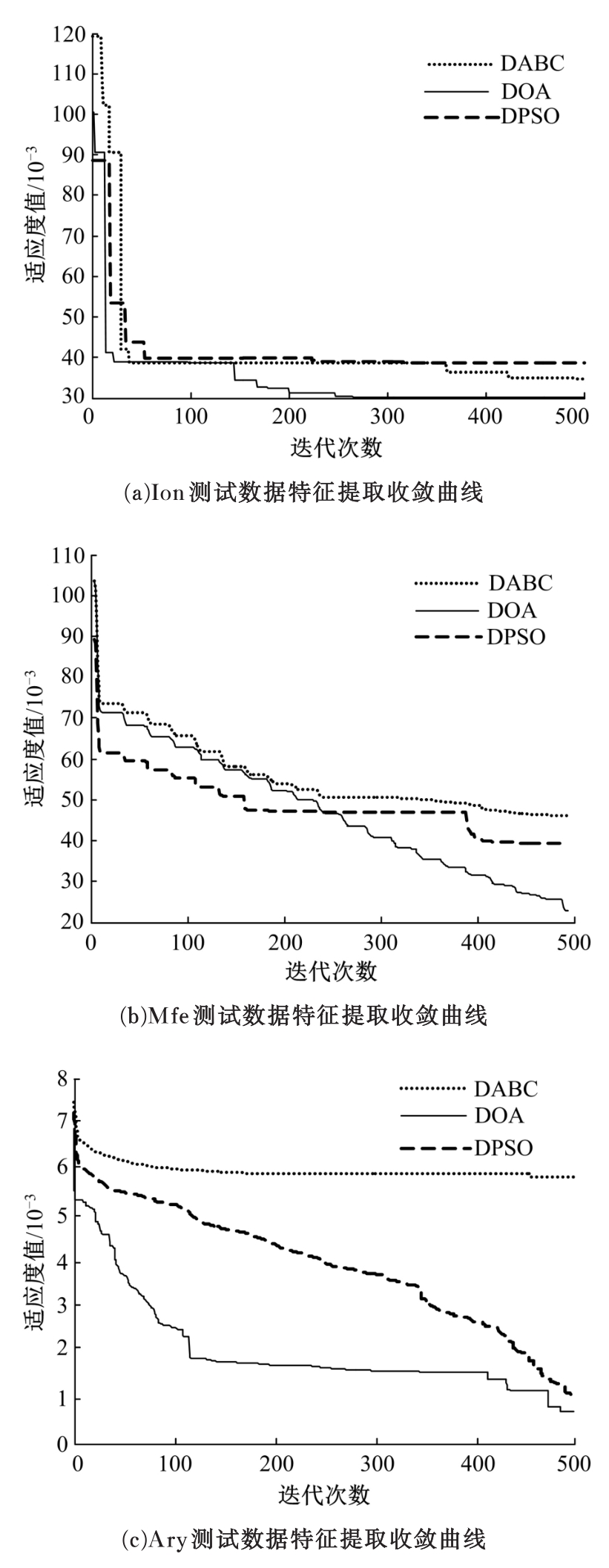
针对传感云的大规模高维度数据和多变性入侵行为,在雾计算模式下提出了一种基于并行离散优化特征提取和机器学习方法特性的传感云入侵检测算法。首先,为有效降低数据维度和提高特征提取过程的鲁棒性,在定义最优特征评价指标的基础上构建并行离散优化特征提取框架,理论分析表明:该指标能最大限度去除特征冗余度和保持原始数据多样性。其次,设计了具有普遍意义的离散优化算法(DOA),结合工程优化问题特点给出DOA实现流程,并证明了DOA具有全局收敛性,在此基础上使用DOA对特征提取框架进行求解,通过并行特征子集筛选过程实现了最佳特征组合提取。最后,利用最佳特征子集和机器学习中的分布模糊聚类技术对传感云入侵行为进行检测,通过引入智能迭代进化思想和自适应聚类策略,在有效避免模糊聚类算法易陷入局部最优缺陷的同时实现了聚类个数自动划分。实验结果表明:该入侵检测算法能有效给出入侵检测结果,而且相比于其他检测算法,该算法异常检测成功率和漏检率明显改善,且具有较强抗噪能力。
中图分类号:
- TP393
| 1 | 曾建电, 王田, 贾维嘉, 等. 传感云研究综述[J]. 计算机研究与发展, 2017, 54( 5): 925- 939. |
| Zeng Jian-dian, Wang Tian, Jia Wei-jia, et al. A survey on sensor-cloud[J]. Journal of Computer Research and Development, 2017, 54( 5): 925- 939. | |
| 2 | 应时彦, 汤顺. 基于节点位置动态变化的无线传感网络路由协议[J]. 吉林大学学报: 工学版, 2011, 41( 增刊1): 309- 313. |
| Ying Shi-yan, Tang Shun. Routing protocol of wsn in terms of dynamic changes of node location[J]. Journal of Jilin University (Engineering and Technology Edition), 2011, 41( Sup.1): 309- 313. | |
| 3 | Yuriyama M, Kushida T. Sensor-cloud infrastructure physical sensor management with virtualized sensors on cloud computing[C]∥ Proc of the 13th International Conference On Network-Based Information Systems. Washington, DC: IEEE Computer Society, 2010: 1- 8. |
| 4 | Madria S, Kumar V, Dalvi R. Sensor cloud: a cloud of virtual sensors[J]. IEEE Software, 2014, 31( 2): 70- 77. |
| 5 | Wang T, Bhuiyan M Z, Wang G J, et al. Big data reduction for smart city’s critical infrastructural health monitoring[J]. IEEE Communications Magazine, 2018, 56( 3): 128- 133. |
| 6 | Elhag S, Fernandez A, Bawakid A, et al. On the combination of genetic fuzzy systems and pair-wise learning for improving detection rates on intrusion detection systems[J]. Expert Systems with Applications, 2015, 42( 1): 193- 202. |
| 7 | Qing Y L, Information Technology Co, LTD. YeeLink[EB/OL].[ 2018-11-26]. |
| 8 | 杜晔, 张亚丹, 黎妹红, 等. 基于改进FastICA算法的入侵检测样本数据优化方法[J]. 通信学报, 2016, 37( 1): 42- 48. |
| Du Ye, Zhang Ya-dan, Li Mei-hong, et al. Improved FastICA algorithm for data optimization processing in intrusion detection[J]. Journal on Communicaitons, 2016, 37( 1): 42- 48. | |
| 9 | Zhao Z, Wang L, Liu H, et al. On similarity preserving feature selection[J]. IEEE Trans on Knowledge and Data Engineering, 2013, 25( 3): 619- 632. |
| 10 | 王珺, 卫金茂, 张璐. 基于保留分类信息的多任务特征学习算法[J]. 计算机研究与发展, 2017, 54( 3): 537- 548. |
| Wang Jun, Wei Jin-mao, Zhang Lu. Multi-task feature learning algorithm based on preserving classification information[J]. Journal of Computer Research and Development, 2017, 54( 3): 537- 548. | |
| 11 | 孙广路, 宋智超, 刘金来, 等. 基于最大信息系数和近似马尔科夫毯的特征选择方法[J]. 自动化学报, 2017, 43( 5): 795- 805. |
| Sun Guang-lu, Song Zhi-chao, Liu Jin-lai, et al. Feature selection method based on maximum information coefficient and approximate Markov blanket[J]. Acta Automatica Sinica, 2017, 43( 5): 795- 805. | |
| 12 | 仇利克, 郭忠文, 刘青, 等. 基于冗余分析的特征选择算法[J]. 北京邮电大学学报, 2017, 40( 1): 36- 41. |
| Qiu Li-ke, Guo Zhong-wen, Liu Qing, et al. Feature selection algorithm based on redundancy analysis[J]. Journal of Beijing University of Posts and Telecommunications, 2017, 40( 1): 36- 41. | |
| 13 | 唐成华, 六鹏程, 汤申生, 等. 基于特征选择的模糊聚类异常行为检测[J]. 计算机研究与发展, 2015, 52( 3): 718- 728. |
| Tang Cheng-hua, Liu Peng-cheng, Tang Shen-sheng, et al. Anomaly intrusion behavior detection based on fuzzy clustering and features selection[J]. Journal of Computer Research and Development, 2015, 52( 3): 718- 728. | |
| 14 | Nayak J, Naik B, Kanungo D P, et al. A hybrid elicit teaching learning based optimization with fuzzy C-means(ETLBO-FCM) algorithm for data clustering [J]. Ain Shams Engineering Journal, 2018, 9( 3): 379- 393. |
| 15 | Ma A, Zhong Y F, Zhang L P. Adaptive multiplicative meme-tic fuzzy clustering algorithm for remote sensing imagery[J]. IEEE Trans on Geoscience and Remote Sensing, 2015, 53( 8): 4202- 4217. |
| 16 | 刘洲洲, 王福豹. 改进的离散混合蛙跳算法压缩感知信号重构及应用[J]. 吉林大学学报: 工学版, 2016, 46( 4): 1261- 1268. |
| Liu Zhou-zhou, Wang Fu-bao. Improvement of discrete shuffled frog-leaping algorithm and application in compressed sensing reconstruction[J]. Journal of Jilin University (Engineering and Technology Edition), 2016, 46( 4): 1261- 1268. | |
| 17 | 刘洲洲, 彭寒. 基于节点可靠度的无线传感器网络拓扑控制算法[J]. 吉林大学学报: 工学版, 2018, 48( 2): 571- 577. |
| Liu Zhou-zhou, Peng Han. Topology control algorithm based on node reliability in WSN[J]. Journal of Jilin University (Engineering and Technology Edition), 2018, 48( 2): 571- 577. | |
| 18 | 吴丽云, 李生林, 甘旭升, 等. 基于PLS特征提取的网络异常入侵检测CVM模型[J]. 控制与决策, 2017, 32( 4): 755- 758. |
| Wu Li-yun, Li Sheng-lin, Gan Xu-sheng, et al. Network anomaly intrusion detection CVM model based on PLS feature extraction[J]. Control and Decision, 2017, 32( 4): 755- 758. |
| [1] | 陈蔓,钟勇,李振东. 隐低秩结合低秩表示的多聚焦图像融合[J]. 吉林大学学报(工学版), 2020, 50(1): 297-305. |
| [2] | 金顺福,郄修尘,武海星,霍占强. 基于新型休眠模式的云虚拟机分簇调度策略及性能优化[J]. 吉林大学学报(工学版), 2020, 50(1): 237-246. |
| [3] | 张笑东,夏筱筠,吕海峰,公绪超,廉梦佳. 大数据网络并行计算环境中生理数据流动态负载均衡[J]. 吉林大学学报(工学版), 2020, 50(1): 247-254. |
| [4] | 王晓辉,吴禄慎,陈华伟. 基于法向量距离分类的散乱点云数据去噪[J]. 吉林大学学报(工学版), 2020, 50(1): 278-288. |
| [5] | 邓钧忆,刘衍珩,冯时,赵荣村,王健. 基于GSPN的Ad⁃hoc网络性能和安全平衡[J]. 吉林大学学报(工学版), 2020, 50(1): 255-261. |
| [6] | 王铁君,王维兰. 基于本体的唐卡图像标注方法[J]. 吉林大学学报(工学版), 2020, 50(1): 289-296. |
| [7] | 李雄飞,王婧,张小利,范铁虎. 基于SVM和窗口梯度的多焦距图像融合方法[J]. 吉林大学学报(工学版), 2020, 50(1): 227-236. |
| [8] | 王洪雁,邱贺磊,郑佳,裴炳南. 光照变化下基于低秩稀疏表示的视觉跟踪方法[J]. 吉林大学学报(工学版), 2020, 50(1): 268-277. |
| [9] | 车翔玖,刘华罗,邵庆彬. 基于Fast RCNN改进的布匹瑕疵识别算法[J]. 吉林大学学报(工学版), 2019, 49(6): 2038-2044. |
| [10] | 周炳海,吴琼. 考虑工具和空间约束的机器人装配线平衡优化[J]. 吉林大学学报(工学版), 2019, 49(6): 2069-2075. |
| [11] | 周柚,杨森,李大琳,吴春国,王岩,王康平. 基于现场可编程门电路的人脸检测识别加速平台[J]. 吉林大学学报(工学版), 2019, 49(6): 2051-2057. |
| [12] | 赵宏伟,王鹏,范丽丽,胡黄水,刘萍萍. 相似性保持实例检索方法[J]. 吉林大学学报(工学版), 2019, 49(6): 2045-2050. |
| [13] | 沈军,周晓,吉祖勤. 服务动态扩展网络及其结点系统模型的实现[J]. 吉林大学学报(工学版), 2019, 49(6): 2058-2068. |
| [14] | 李宾,周旭,梅芳,潘帅宁. 基于K-means和矩阵分解的位置推荐算法[J]. 吉林大学学报(工学版), 2019, 49(5): 1653-1660. |
| [15] | 李宾,申国君,孙庚,郑婷婷. 改进的鸡群优化算法[J]. 吉林大学学报(工学版), 2019, 49(4): 1339-1344. |
|
||