吉林大学学报(工学版) ›› 2021, Vol. 51 ›› Issue (4): 1364-1369.doi: 10.13229/j.cnki.jdxbgxb20200955
• 计算机科学与技术 • 上一篇
基于标签分类的云数据完整性验证审计方案
- 1.长春理工大学 计算机科学技术学院,长春 130022
2.长春汽车工业高等专科学校 信息技术学院,长春 130013
3.长春理工大学 信息化中心,长春 130022
Cloud storage integrity verification audit scheme based on label classification
Chun-bo WANG1,2( ),Xiao-qiang DI1,3(
),Xiao-qiang DI1,3( )
)
- 1.College of Computer Science and Technology,Changchun University of Science and Technology,Changchun 130022,China
2.School of Information Technology,Changchun Automobile Industry Institute,Changchun 130013,China
3.Information Center,Changchun University of Science and Technology,Changchun 130022,China
摘要:
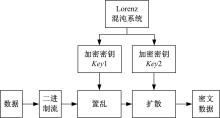
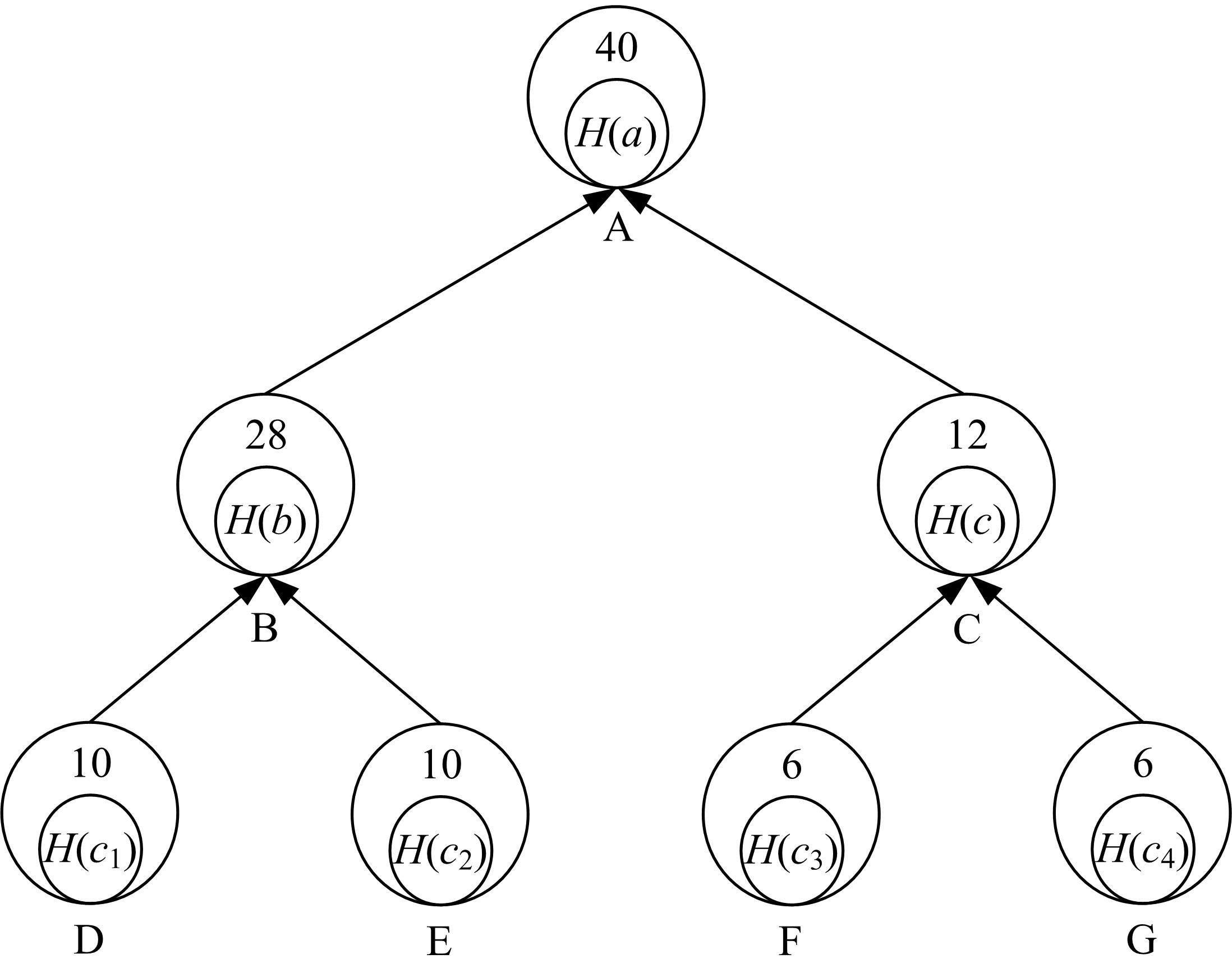
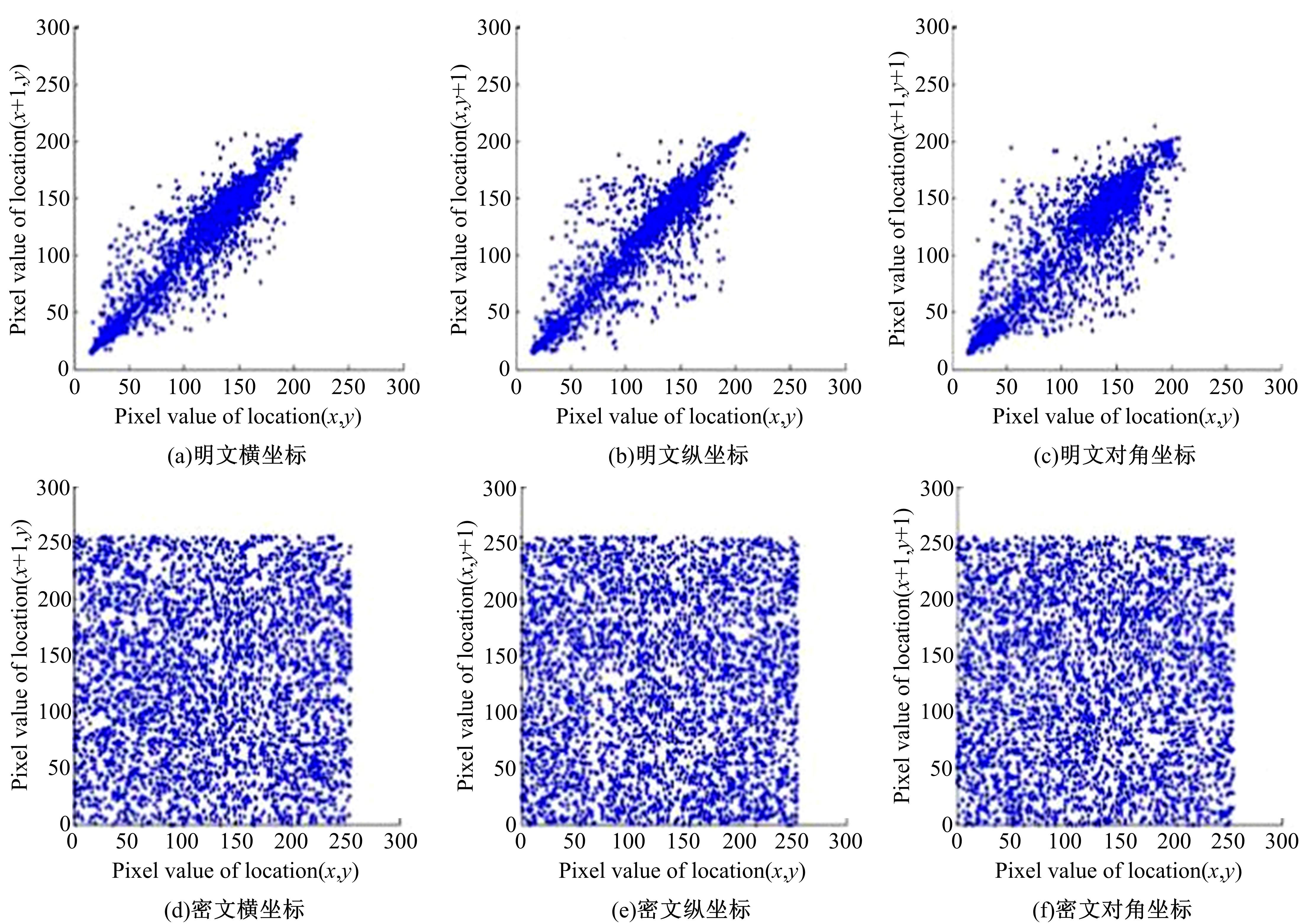
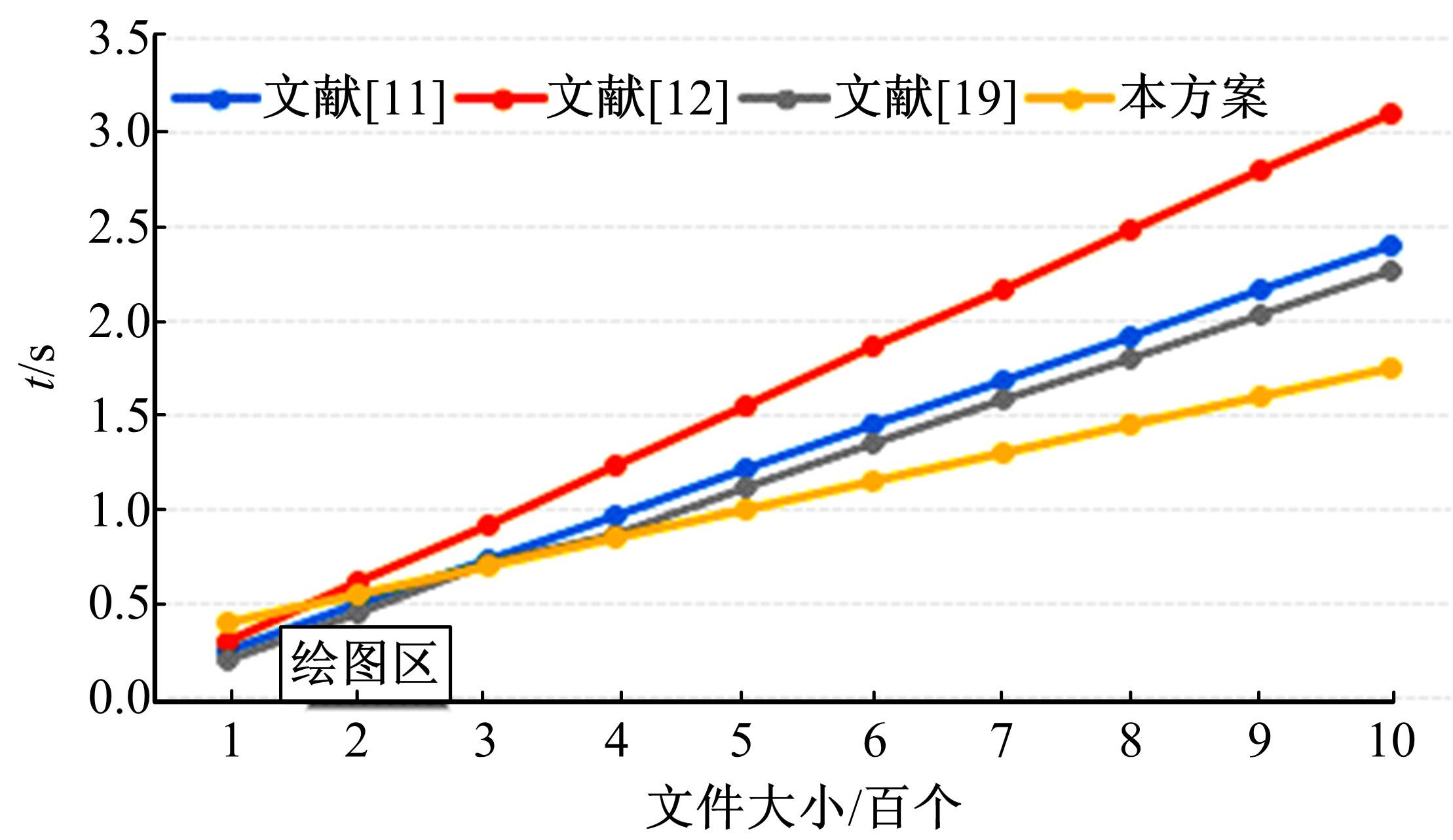
随着云存储技术的发展,更多用户为了降低成本将数据存储到云服务器,但同时也失去了数据控制权,导致无法确保云存储数据的完整性和安全性。针对上述问题,提出一种基于快速标签查询的安全数据完整性审计方案。首先,利用混沌系统对云存储数据进行加密,以保证数据机密性。然后,利用数据块的哈希值作为标签对数据块分类。将Merkle哈希树(MHT)每个叶节点对应一个标签,每个标签对应多个数据块,提高了数据查询索引速度。本方案满足了云数据存储完整性审计方案的安全性要求,还降低了审计过程的通信开销。实验结果表明,本方案安全有效。
中图分类号:
- TP309
| 1 | Lu X, Pan Z, Xian H. An integrity verification scheme of cloud storage for internet-of-things mobile terminal devices[J]. Computers and Security, 2020, 92: No.101686. |
| 2 | Bawa Garg N S, Kumar N. An efficient data integrity auditing protocol for cloud computing[J]. Future Generation Computer Systems, 2020, 109: 306-316. |
| 3 | Zhu H, Yuan Y, Chen Y, et al. A secure and efficient data integrity verification scheme for cloud-IoT based on short signature[J]. IEEE Access, 2019, 7: 90036-90044. |
| 4 | Tang X, Qi Y, Huang Y. Reputation audit in multi-cloud storage through integrity verification and data dynamics[C]∥IEEE International Conference on Cloud Computing, San Francisco, USA, 2017: 624-631. |
| 5 | Gajendra B P, Singh V K, Sujeet M. Achieving cloud security using third party auditor, MD5 and identity-based encryption[C]∥International Conference on Computing, Greater Noida, India, 2016: 1304-1309. |
| 6 | 秦志光,王士雨,赵洋,等. 云存储服务的动态数据完整性审计方案[J]. 计算机研究与发展,2015,52(10): 2192-2199. |
| Qin Zhi-guang,Wang Shi-yu,Zhao Yang, et al. An auditing protocol for data storage in cloud computing with data dynamics[J]. Journal of Computer Research and Development, 2015, 52(10): 2192-2199. | |
| 7 | Wang Qian, Wang Cong, Ren Kui, et al. Enabling public auditability and data dynamics for storage security in cloud computing[J]. IEEE Transactions on Parallel and Distributed Systems, 2010, 22(5): 847-859. |
| 8 | Chen F, Zhang T, Chen J, et al. Cloud storage integrity checking: going from theory to practice[C]∥Proceedings of the 4th ACM International Workshop on Security in Cloud Computing, New York, USA, 2016: 24-28. |
| 9 | 刘绍翰,高天行,黄志球. 一种简化的AVL树的实现方法[J]. 三峡大学学报:自然科学版, 2011, 33(1):85-87, 106. |
| Liu Shao-han, Gao Tian-xing, Huang Zhi-qiu. A development of AVL tree: HAVL tree[J]. Journal of China Three Gorges University (Natural Sciences), 2011, 33(1):85-87, 106. | |
| 10 | Xu G, Han S, Bai Y, et al. Data tag replacement algorithm for data integrity verification in cloud storage[J]. Computers & Security, 2021, 103: 102205. |
| 11 | Arockiam L, Monikandan S. Efficient cloud storage confidentiality to ensure data security[C]∥International Conference on Computer Communication and Informatics, Coimbatore, India, 2014: 1-5. |
| 12 | 王正飞. 云中数据正确性和完整性的高效验证[J]. 计算机工程与科学,2012,34(4):167-170. |
| Wang Zheng-fei. An efficient verification for outsourced data based on subtree[J]. Computer Engineering & Science, 2012,34(4): 167-170. | |
| 13 | Man Z, Li J, Di X Q, et al. An image segmentation encryption algorithm based on hybrid chaotic system[J]. IEEE Access, 2019, 7: 103047-103058. |
| 14 | Deepa N, Pandiaraja P. Hybrid context aware recommendation system for E-health care by merkle hash tree from cloud using evolutionary algorithm[J]. Soft Computing, 2019, 24: 1-13. |
| 15 | Li Q. Research on E-commerce user information encryption technology based on merkle hash tree[C]∥ International Conference on Robots & Intelligent System (ICRIS), Haikou, China, 2019: 365-369. |
| 16 | Wang X Y, Feng L, Li R, et al. A fast image encryption algorithm based on non-adjacent dynamically coupled map lattice model[J]. Nonlinear Dynamics, 2019, 95(1): 1-28. |
| 17 | Wang X Y, Li Z M. A color image encryption algorithm based on Hopfield chaotic neural network[J]. Optics and Lasers in Engineering, 2019, 115: 107-118. |
| 18 | Nardo L G, Nepomuceno E G, Garcia J A, et al. Image encryption using finite-precision error[J]. Chaos, Solitons & Fractals, 2019, 123: 69-78. |
| 19 | Wang C, Wang Q, Ren K, et al. Privacy-preserving public auditing for data storage security in cloud computing[C]∥Proceedings of IEEE INFOCOM, San Diego, USA, 2010: 1-9. |
| 20 | Fan Y,Lin X,Tan G, et al. One secure data integrity verification scheme for cloud storage[J]. Future Generation Computer Systems, 2019, 96: 376-385. |
| [1] | 钱榕,张茹,张克君,金鑫,葛诗靓,江晟. 融合全局和局部特征的胶囊图神经网络[J]. 吉林大学学报(工学版), 2021, 51(3): 1048-1054. |
| [2] | 周炳海,吴琼. 基于多目标的机器人装配线平衡算法[J]. 吉林大学学报(工学版), 2021, 51(2): 720-727. |
| [3] | 许骞艺,秦贵和,孙铭会,孟诚训. 基于改进的ResNeSt驾驶员头部状态分类算法[J]. 吉林大学学报(工学版), 2021, 51(2): 704-711. |
| [4] | 宋元,周丹媛,石文昌. 增强OpenStack Swift云存储系统安全功能的方法[J]. 吉林大学学报(工学版), 2021, 51(1): 314-322. |
| [5] | 车翔玖,董有政. 基于多尺度信息融合的图像识别改进算法[J]. 吉林大学学报(工学版), 2020, 50(5): 1747-1754. |
| [6] | 胡冠宇, 乔佩利. 基于云群的高维差分进化算法及其在网络安全态势预测上的应用[J]. 吉林大学学报(工学版), 2016, 46(2): 568-577. |
| [7] | 贺秦禄1, 李战怀1, 王乐晓1, 王瑞2. 云存储系统聚合带宽测试技术[J]. 吉林大学学报(工学版), 2014, 44(4): 1104-1111. |
| [8] | 佟金, 王亚辉, 樊雪梅, 张书军, 陈东辉. 生鲜农产品冷链物流状态监控信息系统[J]. 吉林大学学报(工学版), 2013, 43(06): 1707-1711. |
| [9] | 聂雄丁, 韩德志, 毕坤. 云计算数据安全[J]. 吉林大学学报(工学版), 2012, 42(增刊1): 332-336. |
|
||