吉林大学学报(工学版) ›› 2023, Vol. 53 ›› Issue (11): 3260-3267.doi: 10.13229/j.cnki.jdxbgxb.20220402
结合融合特征与特征映射的空域图像隐写分析
罗维薇1( ),刘少伟1,张冰涛1,李萌1,刘海銮2(
),刘少伟1,张冰涛1,李萌1,刘海銮2( ),樊凌雁2
),樊凌雁2
- 1.兰州交通大学 电子与信息工程学院,兰州 730070
2.杭州电子科技大学 微电子研究院,杭州 310018
Steganalysis of spatial image combining fusion features and feature mapping
Wei-wei LUO1( ),Shao-wei LIU1,Bing-tao ZHANG1,Meng LI1,Hai-luan LIU2(
),Shao-wei LIU1,Bing-tao ZHANG1,Meng LI1,Hai-luan LIU2( ),Ling-yan FAN2
),Ling-yan FAN2
- 1.School of Electronic and Information Engineering,Lanzhou Jiaotong University,Lanzhou 730070,China
2.Microelectronics Research Institute,Hangzhou Dianzi University,Hangzhou 310018,China
摘要:
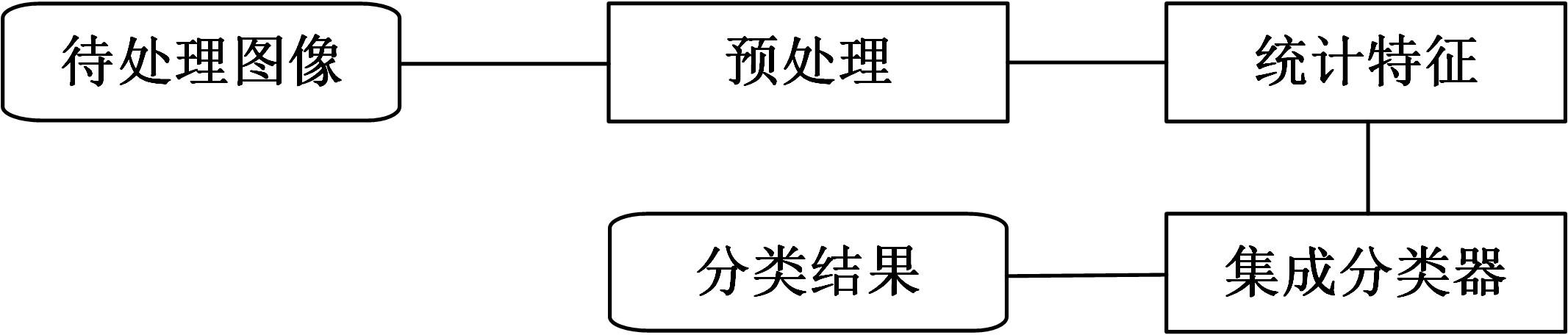
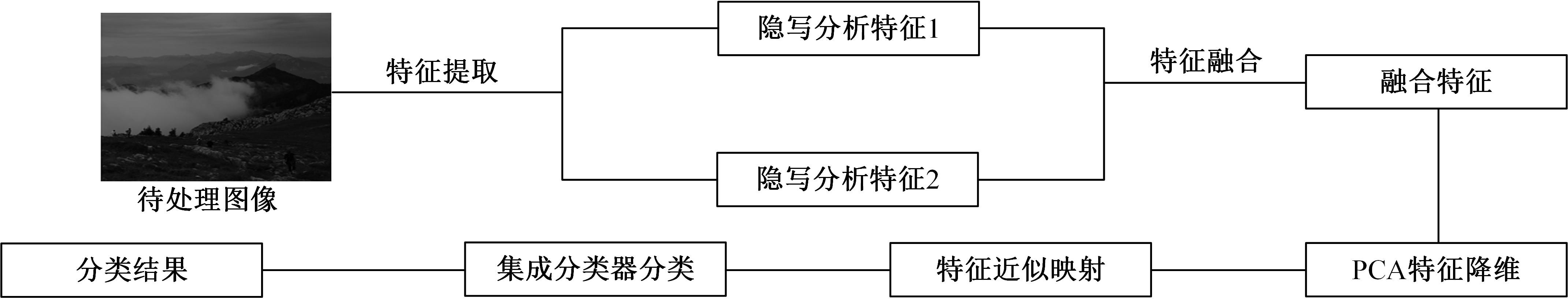
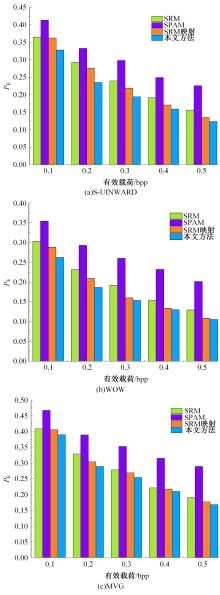
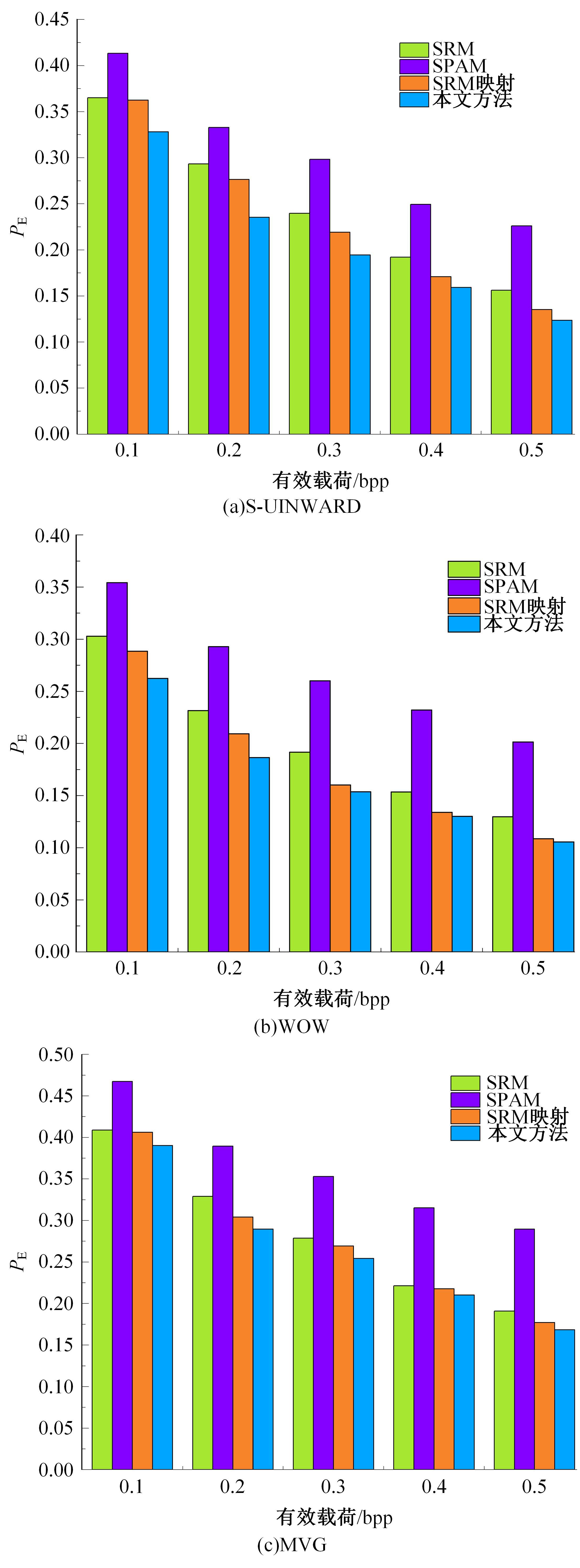
为了更好地捕获隐写术对图像统计特征的改变,提高对隐写图像的检测率并解决特征映射问题,提出结合融合特征与特征映射的隐写分析方法,提取融合特征,更全面地捕获隐写算法对载体图像统计特征的扰动。同时,提出结合PCA的特征映射,以解决图像数小于特征维数时不能直接投影的问题。然后,对融合特征进行结合PCA的近似映射,用于隐写分析。实验证明:该方法有效地提升了对隐写图像的检测率。
中图分类号:
- TP309
| 1 | Xiang S J, Luo X R. Reversible data hiding in encrypted image based on homomorphic public key cryptosystem[J]. Journal of Software, 2016, 27(6): 1592-1601. |
| 2 | Li Y F, Ding L P, Wu J Z, et al. Survey on key issues in networks covert channel[J]. Journal of Software, 2019, 30(8): 2470-2490. |
| 3 | 栗风永. 数字图像高维特征隐写分析及安全隐写[D]. 上海: 上海大学通信学院, 2014. |
| Su Feng-yong. Steganalysis with high dimensional features and secure steganography in digital image[D]. Shangai: School of Communication, Shanghai University, 2014. | |
| 4 | 陈君夫, 付章杰, 张卫明, 等. 基于深度学习的图像隐写分析综述 [J]. 软件学报, 2021, 32(2): 551-578. |
| Chen Jun-fu, Fu Zhang-jie, Zhang Wei-ming, et al. Review of image steganalysis based on deep learning[J]. Journal of Software, 2021,32(2): 551-578. | |
| 5 | Westfld A, Pfitzmanna A. Attacks on steganographic systems[C]∥Proceedings of the Third International Workshop on Information Hiding, Berlin, Germany, 1999: 61-76. |
| 6 | Ker A D. Steganalysis of LSB matching in grayscale images[J]. IEEE Signal Processing Letters, 2005, 12(6): 441-444. |
| 7 | Pevny T, Bas P, Fridrich J. Steganalysis by subtractive pixel adjacency matrix[J]. IEEE Transactions on information Forensics and Security, 2010, 5(2): 215-224. |
| 8 | Fridrich J, Kodovsky J. Rich models for steganalysis of digital images [J]. IEEE Transactions on Information Forensics and Security, 2012, 7(3): 868-882. |
| 9 | Holub V, Fridrich J. Random projections of residuals for digital image steganalysis[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(12): 1996-2006. |
| 10 | Denemark T, Sedighi V, Holub V, et al. Selection-channel-aware rich model for steganalysis of digital images[C]∥Proceedings of the 2014 IEEE International Workshop on Information Forensics and Security, Atlanta, USA, 2014: 48-53. |
| 11 | Denemark T, Fridrich J, Comesaña-alfaro P. Improving selection-channel-aware steganalysis features [J]. Electronic Imaging, 2016(8): 1-8. |
| 12 | Chang C C, Lin C J. LIBSVM: a library for support vector machines [J]. ACM Transactions on Intelligent Systems and Technology, 2011, 2(3): 1-27. |
| 13 | Kodovsky J, Fridrich J, Holub V. Ensemble classifiers for steganalysis of digital media[J]. IEEE Transactions on Information Forensics and Security, 2011, 7(2): 432-444. |
| 14 | Cogranne R, Sedighi V, Fridrich J, et al. Is ensemble classifier needed for steganalysis in high-dimensional feature spaces?[C]∥Proceedings of the 2015 IEEE International Workshop on Information Forensics and Security, Rome, Italy, 2015: 1-6. |
| 15 | Boroumand M, Fridrich J. Applications of explicit non-linear feature maps in steganalysis[J]. IEEE Transactions on Information Forensics and Security, 2017, 13(4): 823-833. |
| 16 | 邓利芳, 党建武, 王阳萍, 等. 结合混合核特征映射的空域图像隐写分析[J]. 计算机工程与应用, 2021, 57(9): 118-125. |
| Deng Li-fang, Dang Jian-wu, Wang Yang-ping, et al. Steganalysis of spatial image based on hybrid kernel feature mapping[J]. Computer Engineering and Applications, 2021, 57(9): 118-125. | |
| 17 | 刘富, 宗宇轩, 康冰, 等, 基于优化纹理特征的手背静脉识别系统 [J]. 吉林大学学报: 工学版, 2018, 48(6): 1844-1850. |
| Liu Fu, Zong Yu-xuan, Kang Bing, et al. Dorsal hand vein recognition system based on optimized texture features[J]. Journal of Jilin University (Engineering and Technology Edition), 2018, 48(6): 1844-1850. | |
| 18 | Huang D S, Jiang F W, Li K P, et al. Scaled PCA: a new approach to dimension reduction[J/OL]. [2022-04-02]. |
| 19 | 刘云, 刘富, 侯涛, 等. 优化核参数的模糊C均值聚类算法[J]. 吉林大学学报: 工学版, 2016, 46(1): 246-251. |
| Liu Yun, Liu Fu, Hou Tao, et al. Kernel-based fuzzy C-means clustering method based on parameter optimization[J]. Journal of Jilin University(Engineering and Technology Edition), 2016, 46(1): 246-251. | |
| 20 | Denemark T, Fridrich J, Holub V. Further study on the security of S-UNIWARD[J]. Media Watermarking, Security, and Forensics, 2014, 9028: 902805. |
| 21 | Holub V, Fridrich J. Designing steganographic distortion using directional filters[C]∥ IEEE International Workshop on Information Forensicsand Security, Adeje, Spain, 2012: 234-239. |
| 22 | Sedighi V, Fridrich J, Cogranne R. Content-adaptive pentary steganography using the multivariate generalized Gaussian cover model[J]. Media Watermarking, Security, and Forensics, 2015, 9409: 94090H. |
| [1] | 刘培勇,董洁,谢罗峰,朱杨洋,殷国富. 基于多支路卷积神经网络的磁瓦表面缺陷检测算法[J]. 吉林大学学报(工学版), 2023, 53(5): 1449-1457. |
| [2] | 欧阳宁,李祖锋,林乐平. 基于多层次空⁃谱融合网络的高光谱图像分类[J]. 吉林大学学报(工学版), 2022, 52(10): 2438-2446. |
| [3] | 潘晓英,魏德,赵逸喆. 基于Mask R⁃CNN和上下文卷积神经网络的肺结节检测[J]. 吉林大学学报(工学版), 2022, 52(10): 2419-2427. |
| [4] | 周大可,张超,杨欣. 基于多尺度特征融合及双重注意力机制的自监督三维人脸重建[J]. 吉林大学学报(工学版), 2022, 52(10): 2428-2437. |
| [5] | 赵宏伟,霍东升,王洁,李晓宁. 基于显著性检测的害虫图像分类[J]. 吉林大学学报(工学版), 2021, 51(6): 2174-2181. |
| [6] | 谌华,郭伟,闫敬文,卓文浩,吴良斌. 基于深度学习的SAR图像道路识别新方法[J]. 吉林大学学报(工学版), 2020, 50(5): 1778-1787. |
| [7] | 倪涛,刘海强,王林林,邹少元,张红彦,黄玲涛. 基于双向长短期记忆模型的起重机智能操控方法[J]. 吉林大学学报(工学版), 2020, 50(2): 445-453. |
| [8] | 王生生, 郭湑, 张家晨, 王光耀, 赵欣. 基于全局与局部形状特征融合的形状识别算法[J]. 吉林大学学报(工学版), 2016, 46(5): 1627-1632. |
| [9] | 张浩, 刘海明, 吴春国, 张艳梅, 赵天明, 李寿涛. 基于多特征融合的绿色通道车辆检测判定[J]. 吉林大学学报(工学版), 2016, 46(1): 271-276. |
| [10] | 杨欣,刘加,周鹏宇,周大可. 基于多特征融合的粒子滤波自适应目标跟踪算法[J]. 吉林大学学报(工学版), 2015, 45(2): 533-539. |
| [11] | 吴迪, 曹洁. 智能环境下基于核相关权重鉴别分析算法的多特征融合人脸识别[J]. 吉林大学学报(工学版), 2013, 43(02): 439-443. |
| [12] | 王新颖, 刘钢, 谷方明, 肖巍. 三维模型检索中的语义与形状异构特征融合[J]. 吉林大学学报(工学版), 2012, 42(增刊1): 359-363. |
| [13] | 邢笑雪, 刘富, 马冬梅, 翟微微, 王芳荣. 基于机器视觉的软体纤维丝集束智能计数系统[J]. , 2012, 42(05): 1267-1272. |
| [14] | 曲智国, 王平, 高颖慧, 王鹏, 沈振康, 李江. 基于同化核分割相同值区域特征融合的边缘检测 [J]. , 2012, (03): 759-765. |
| [15] | 陈绵书, 付平, 李勇, 张慧. 基于范围相似分最小化的图像特征融合[J]. 吉林大学学报(工学版), 2010, 40(增刊): 365-0368. |
|