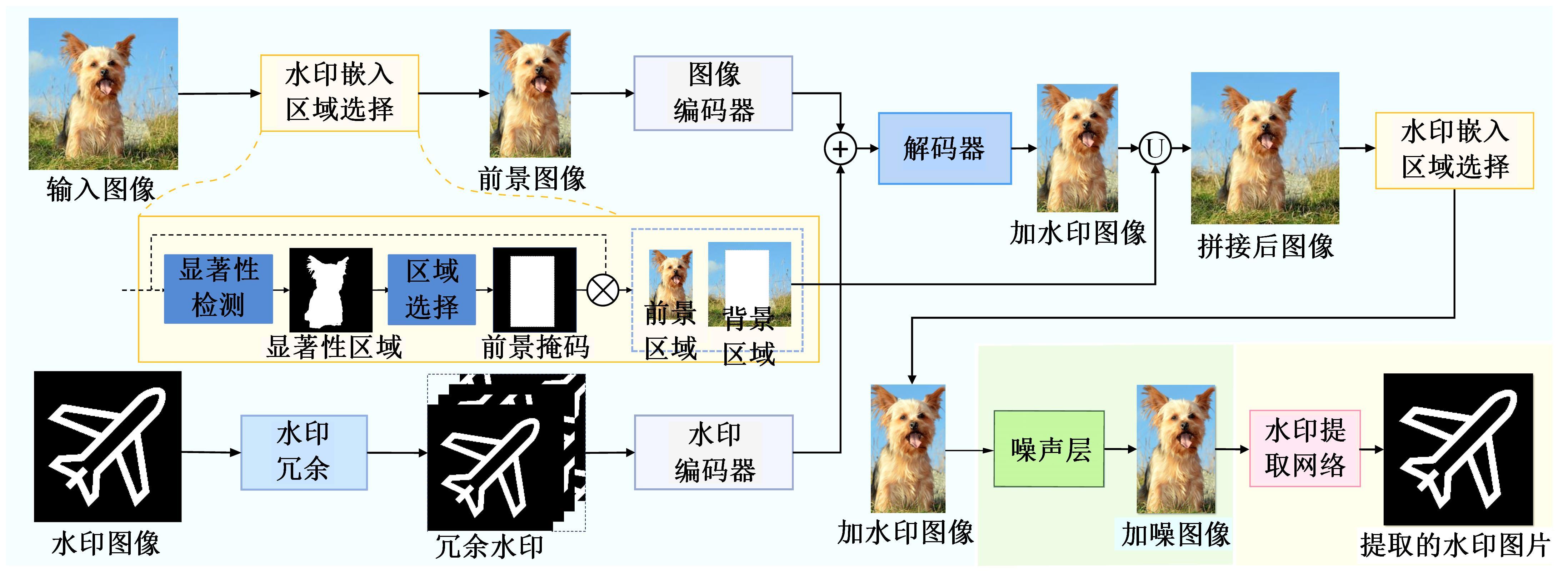
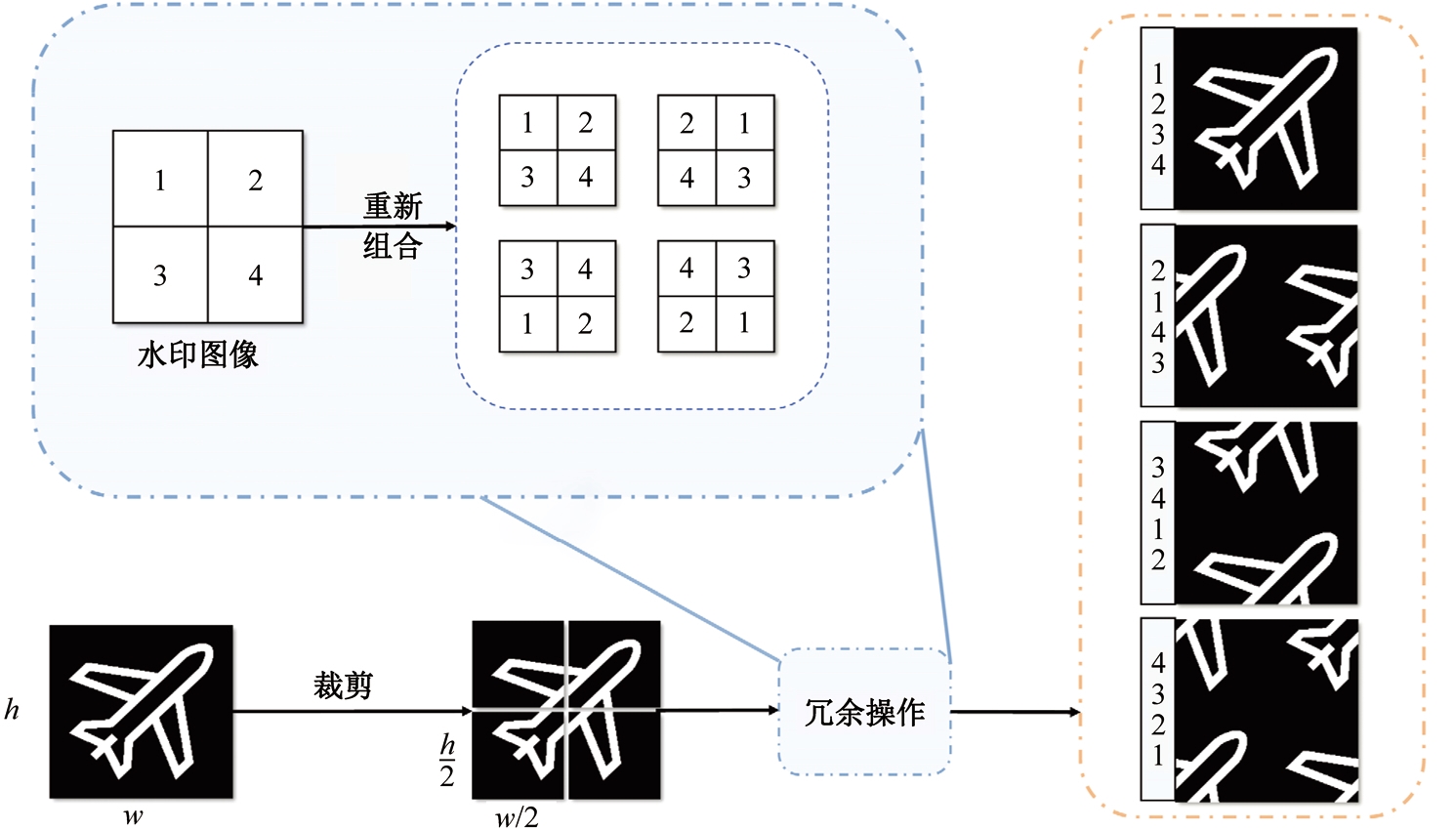
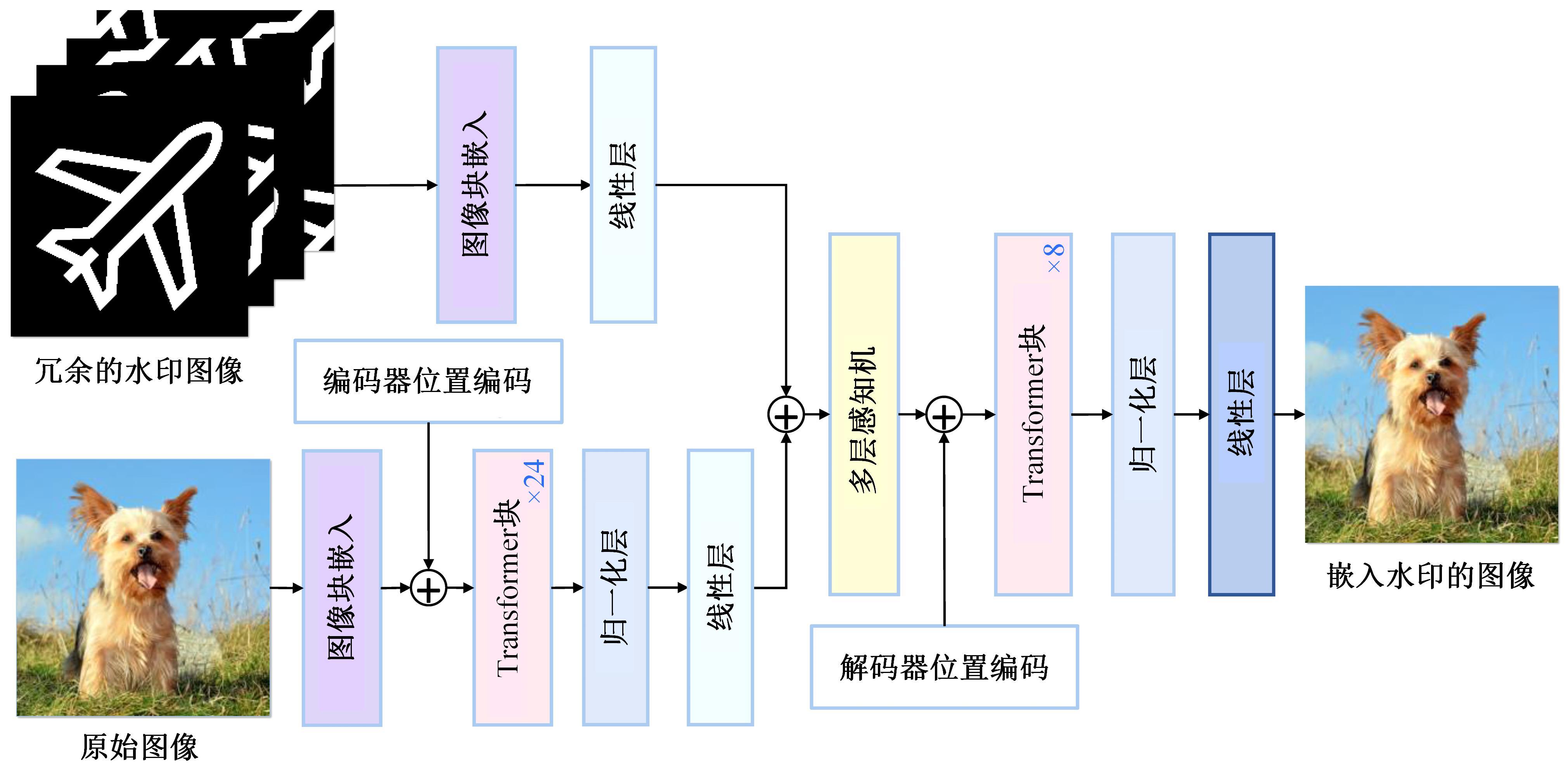
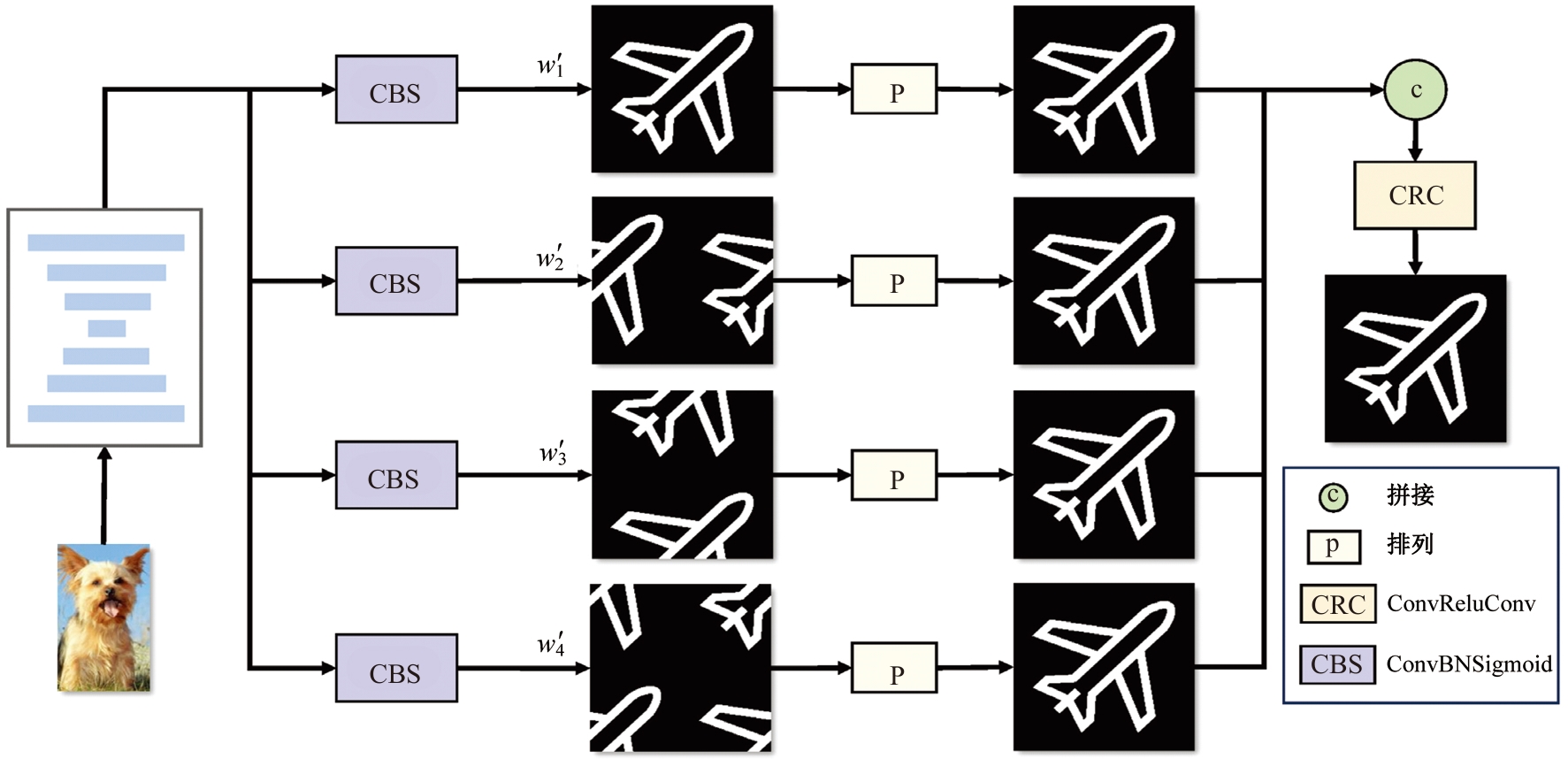
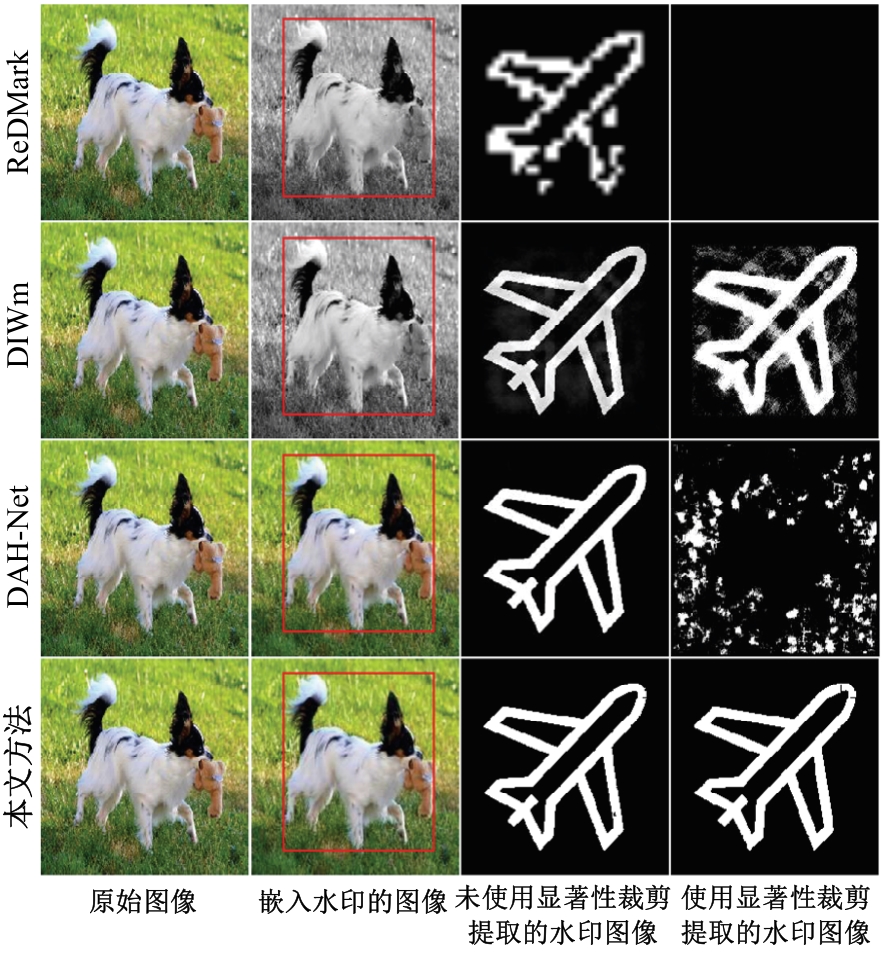
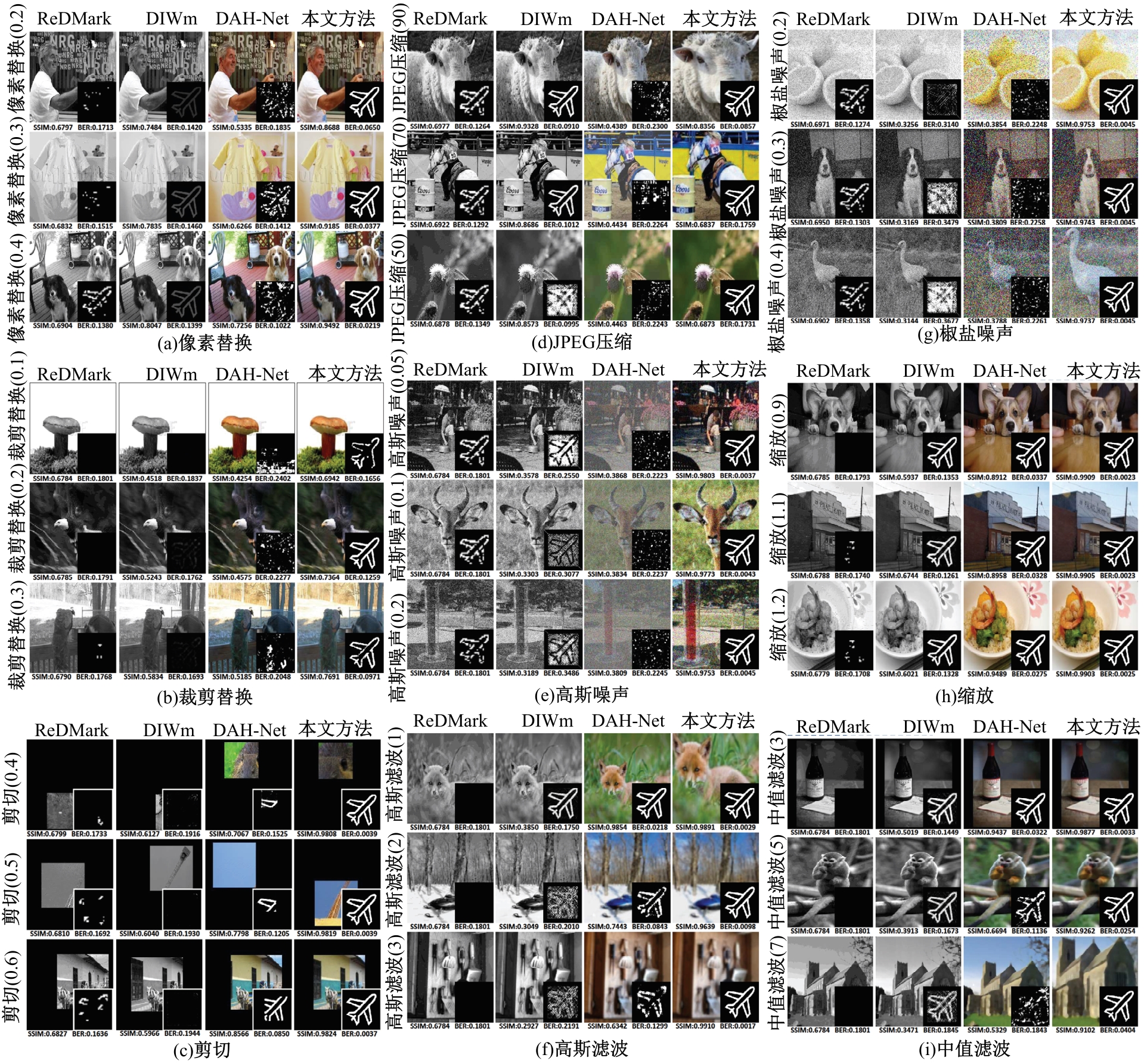
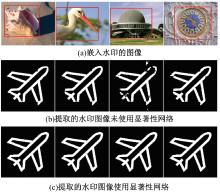
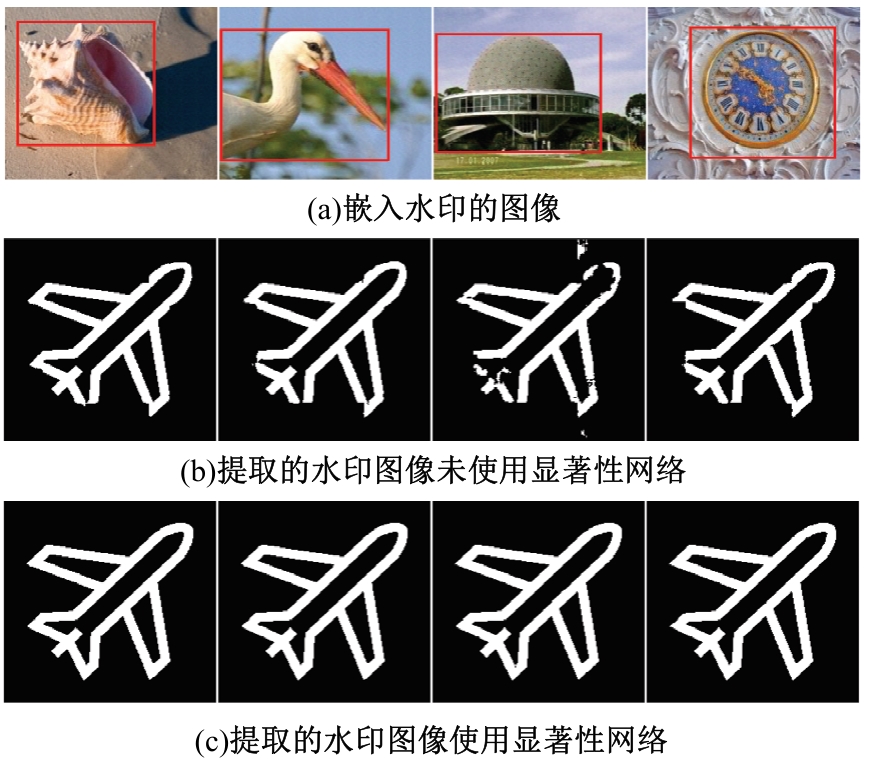
Journal of Jilin University(Engineering and Technology Edition) ›› 2025, Vol. 55 ›› Issue (12): 4000-4009.doi: 10.13229/j.cnki.jdxbgxb.20240301
Anti⁃cropping digital image watermarking based on saliency detection
Rui HUANG1( ),Ruo-xue YU1,Wei FAN1(
),Ruo-xue YU1,Wei FAN1( ),Yan XING2,Zi-yin CHEN3
),Yan XING2,Zi-yin CHEN3
- 1.School of Computer and Artificial Intelligence,Civil Aviation University of China,Tianjin 300300,China
2.School of Safety Science and Engineering,Civil Aviation University of China,Tianjin 300300,China
3.College of Electronic Information and Automation,Civil Aviation University of China,Tianjin 300300,China
CLC Number:
- TP309
| [1] | Van Schyndel R G, Tirkel A Z, Osborne C F. A digital watermark[C]∥Proceedings of 1st International Conference on Image Processing,Austin, USA, 1994: 86-90. |
| [2] | Ko H J, Huang C T, Horng G, et al. Robust and blind image watermarking in DCT domain using inter-block coefficient correlation[J]. Information Sciences, 2020, 517: 128-147. |
| [3] | Cedillo-Hernandez M, Cedillo-Hernandez A, Garcia-Ugalde F J. Improving dft-based image watermarking using particle swarm optimization algorithm[J]. Mathematics, 2021, 9(15): No. 1795. |
| [4] | Giri K J, Quadri S M K, Bashir R, et al. DWT based color image watermarking: a review[J]. Multimedia Tools and Applications, 2020, 79: 32881-32895. |
| [5] | Assini I, Badri A, Safi K, et al. A robust hybrid watermarking technique for securing medical image[J]. International Journal of Intelligent Engineering and Systems, 2018, 11(3): 169-176. |
| [6] | 李喜艳, 周夏冰, 刘征. 基于高容量强鲁棒的图像水印算法[J]. 吉林大学学报: 工学版, 2022, 52(1): 174-179. |
| Li Xi-yan, Zhou Xia-bing, Liu Zheng. High-capacity and robust image watermarking algorithm[J]. Journal of Jilin University (Engineering and Technology Edition), 2022, 52(1): 174-179. | |
| [7] | Hsu C S, Tu S F. Enhancing the robustness of image watermarking against cropping attacks with dual watermarks[J]. Multimedia Tools and Applications, 2020, 79(17/18): 11297-11323. |
| [8] | Liu J, Huang J, Luo Y, et al. An optimized image watermarking method based on HD and SVD in DWT domain[J]. IEEE Access, 2019, 7: 80849-80860. |
| [9] | Zhu J, Kaplan R, Johnson J, et al. Hidden: hiding data with deep networks[C]∥Proceedings of the European Conference on Computer Vision (ECCV),Munich, Germany, 2018: 657-672. |
| [10] | Lu J, Ni J, Su W, et al. Wavelet-based CNN for robust and high-capacity image watermarking[C]∥IEEE International Conference on Multimedia and Expo (ICME), Taipei, China, 2022: 1-6. |
| [11] | Liu Y, Guo M, Zhang J, et al. A novel two-stage separable deep learning framework for practical blind watermarking[C]∥Proceedings of the 27th ACM International Conference on Multimedia,Nice, France,2019: 1509-1517. |
| [12] | Zhang L, Lu Y, Li J, et al. Deep adaptive hiding network for image hiding using attentive frequency extraction and gradual depth extraction[J]. Neural Computing and Applications, 2023, 35(15): 10909-10927. |
| [13] | Marchesotti L, Cifarelli C, Csurka G. A framework for visual saliency detection with applications to image thumbnailing[C]∥IEEE 12th International Conference on Computer Vision, Kyoto, Japan, 2009: 2232-2239. |
| [14] | 刘洋, 毛克明. 基于自适应反馈机制的小差异化图像纹理特征信息数据检索[J]. 江苏大学学报: 自然科学版, 2025, 46(1): 73-81. |
| Liu yang, mao Ke-ming. Retrieval of texture feature information data for small differentiated images based on adaptive feedback mechanism[J]. Journal of Jiangsu University(Natural Science Edition), 2025, 46(1): 73-81. | |
| [15] | Tu Y, Niu L, Zhao W, et al. Image cropping with composition and saliency aware aesthetic score map[C]∥Proceedings of the AAAI Conference on Artificial Intelligence, New York, USA,2020: 12104-12111. |
| [16] | Thahab A T, Shahadi H I. Robust image watermarking against crop and rotation attacks for public communication networks[C]∥Third Scientific Conference of Electrical Engineering,Baghdad, Iraq, 2018: 105-110. |
| [17] | Jia Z, Fang H, Zhang W. Mbrs: enhancing robustness of dnn-based watermarking by mini-batch of real and simulated jpeg compression[C]∥Proceedings of the 29th ACM International Conference on Multimedia, Chengdu, China, 2021: 41-49. |
| [18] | Ding J, Cao Y, Shi C. CropDefender: deep watermark which is more convenient to train and more robust against cropping[J/OL].[2024-03-05]. |
| [19] | Tancik M, Mildenhall B, Ng R. Stegastamp: invisible hyperlinks in physical photographs[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Seattle, USA,2020: 2117-2126. |
| [20] | Ahmadi M, Norouzi A, Karimi N, et al. ReDMark: framework for residual diffusion watermarking based on deep networks[J]. Expert Systems with Applications, 2020, 146: No.113157. |
| [21] | Liu J J, Hou Q, Cheng M M, et al. A simple pooling-based design for real-time salient object detection[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition,Long Beach, USA, 2019: 3912-3921. |
| [22] | Deng J, Dong W, Socher R, et al. ImageNet: a large-scale hierarchical image database[C]∥IEEE Conference on Computer Vision and Pattern Recognition, Miami, USA, 2009: 248-255. |
| [1] | Qing-lin AI,Yuan-xiao LIU,Jia-hao YANG. Small target swmantic segmentation method based MFF-STDC network in complex outdoor environments [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(8): 2681-2692. |
| [2] | Yu-fei ZHANG,Li-min WANG,Jian-ping ZHAO,Zhi-yao JIA,Ming-yang LI. Robot inverse kinematics solution based on center selection battle royale optimization algorithm [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(8): 2703-2710. |
| [3] | Yan PIAO,Ji-yuan KANG. RAUGAN:infrared image colorization method based on cycle generative adversarial networks [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(8): 2722-2731. |
| [4] | Qiong-xin LIU,Tian-tian WANG,Ya-nan WANG. Non-dominated sorted particle swarm genetic algorithm to solve vehicle location routing problems [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(7): 2464-2474. |
| [5] | Xiang-jiu CHE,Liang LI. Graph similarity measurement algorithm combining global and local fine-grained features [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(7): 2365-2371. |
| [6] | Wen-hui LI,Chen YANG. Few-shot remote sensing image classification based on contrastive learning text perception [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(7): 2393-2401. |
| [7] | Shan-na ZHUANG,Jun-shuai WANG,Jing BAI,Jing-jin DU,Zheng-you WANG. Video-based person re-identification based on three-dimensional convolution and self-attention mechanism [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(7): 2409-2417. |
| [8] | Hai-peng CHEN,Shi-bo ZHANG,Ying-da LYU. Multi⁃scale context⁃aware and boundary⁃guided image manipulation detection method [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(6): 2114-2121. |
| [9] | Jian WANG,Chen-wei JIA. Trajectory prediction model for intelligent connected vehicle [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(6): 1963-1972. |
| [10] | Feng-feng ZHOU,Zhe GUO,Yu-si FAN. Feature representation algorithm for imbalanced classification of multi⁃omics cancer data [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(6): 2089-2096. |
| [11] | Xiang-jiu CHE,Yu-peng SUN. Graph node classification algorithm based on similarity random walk aggregation [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(6): 2069-2075. |
| [12] | Ping-ping LIU,Wen-li SHANG,Xiao-yu XIE,Xiao-kang YANG. Unbalanced image classification algorithm based on fine⁃grained analysis [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(6): 2122-2130. |
| [13] | You-wei WANG,Ao LIU,Li-zhou FENG. New method for text sentiment classification based on knowledge distillation and comment time [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1664-1674. |
| [14] | Hong-wei ZHAO,Ming-zhu ZHOU,Ping-ping LIU,Qiu-zhan ZHOU. Medical image segmentation based on confident learning and collaborative training [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1675-1681. |
| [15] | Zi-hao SHEN,Yong-sheng GAO,Hui WANG,Pei-qian LIU,Kun LIU. Deep deterministic policy gradient caching method for privacy protection in Internet of Vehicles [J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(5): 1638-1647. |
|
||