吉林大学学报(工学版) ›› 2025, Vol. 55 ›› Issue (3): 857-865.doi: 10.13229/j.cnki.jdxbgxb.20240044
基于CAN总线数据的车载网络入侵检测系统
- 长春大学 计算机科学技术学院,长春 130022
In⁃vehicle network intrusion detection system based on CAN bus data
Yin-fei DAI( ),Xiu-zhen ZHOU,Yu-bao LIU(
),Xiu-zhen ZHOU,Yu-bao LIU( ),Zhi-yuan LIU
),Zhi-yuan LIU
- School of Computer Science and Technology,Changchun University,Changchun 130022,China
摘要:
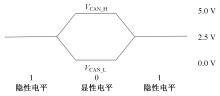
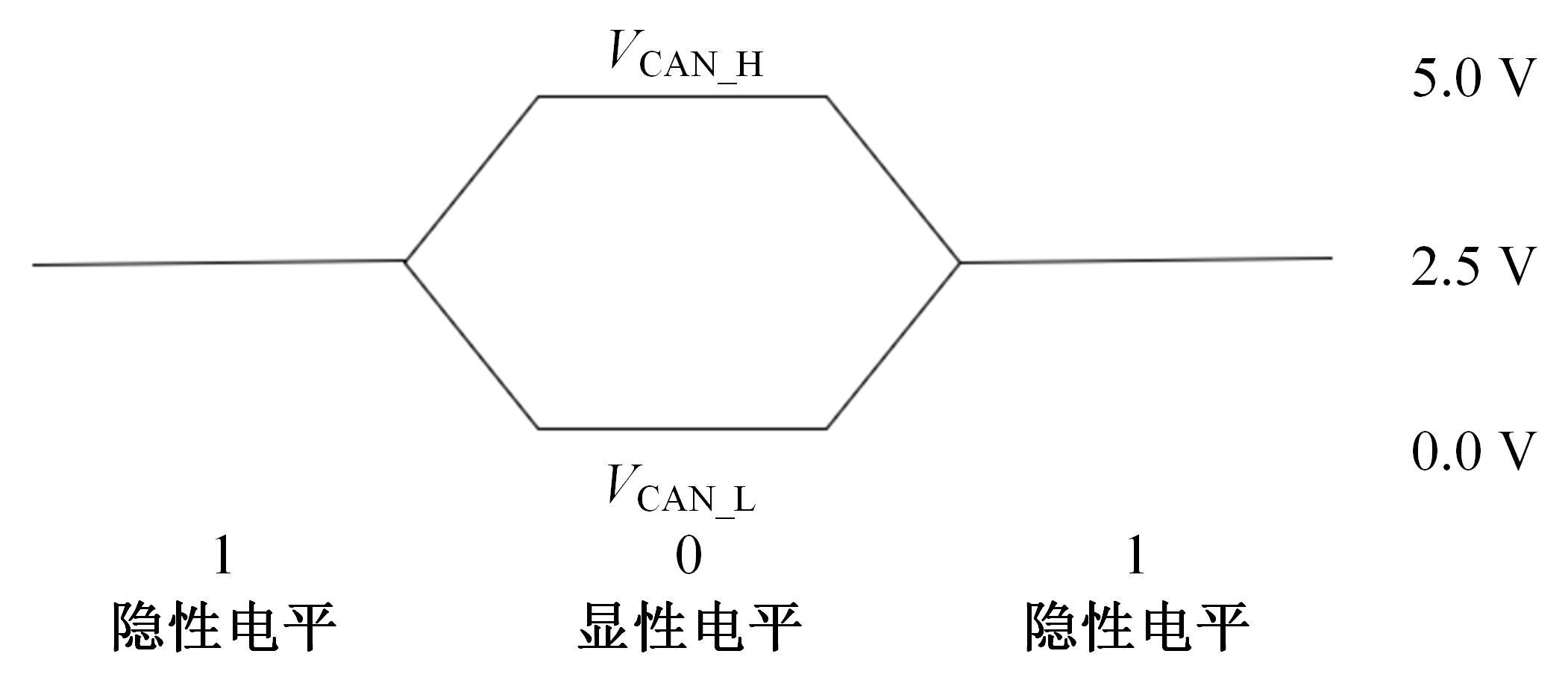
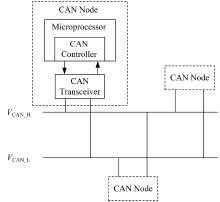
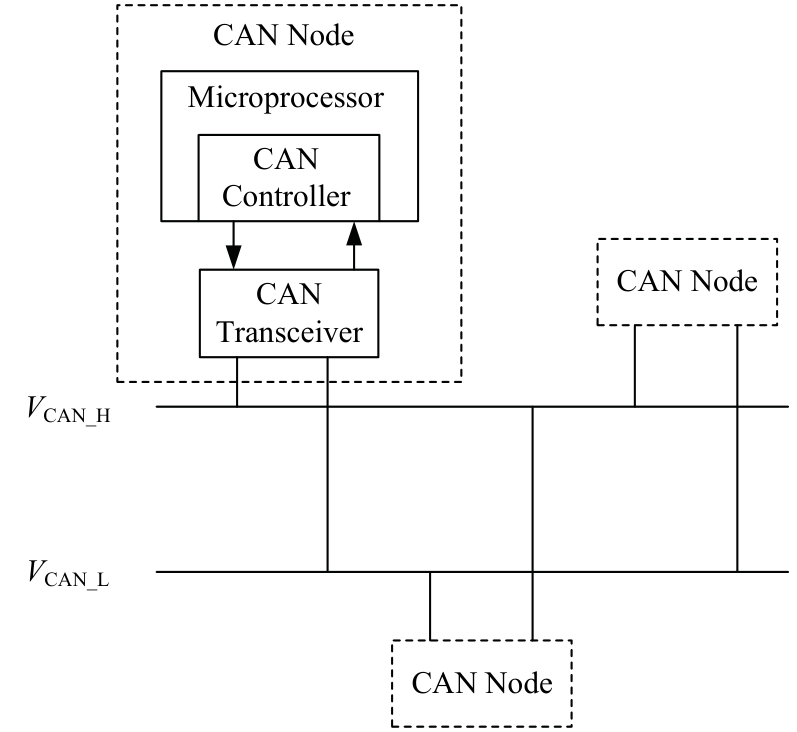
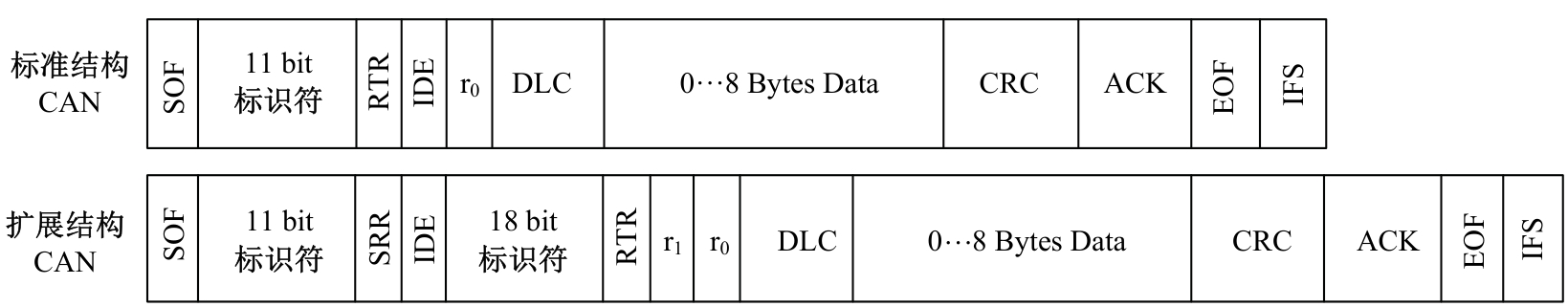
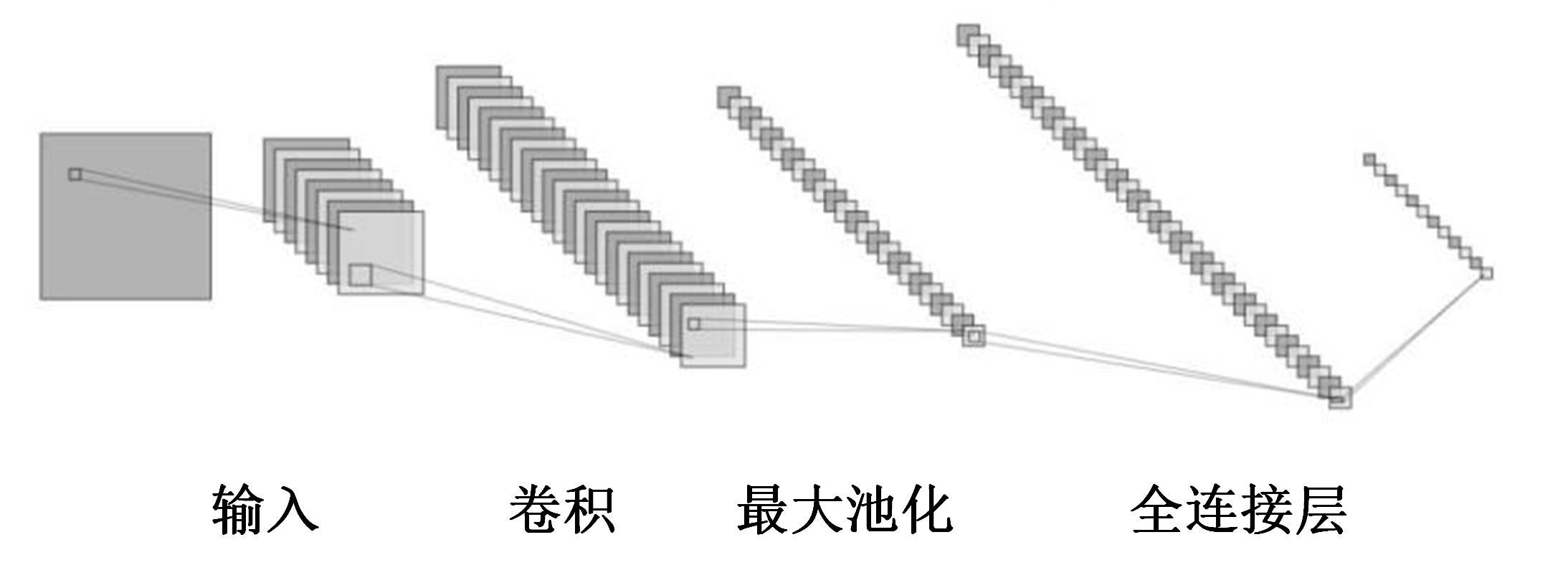
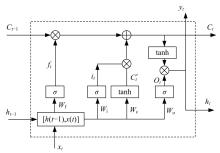
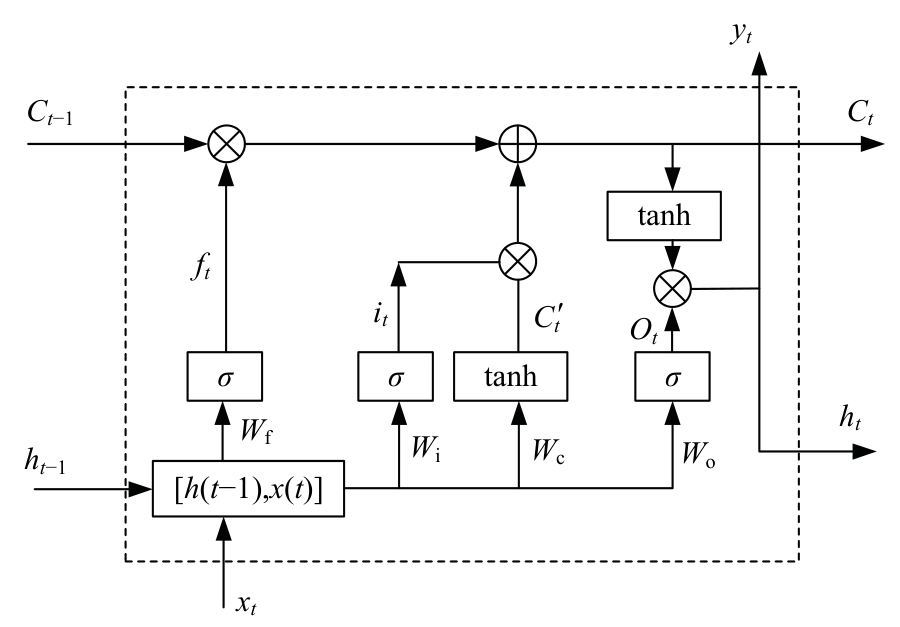
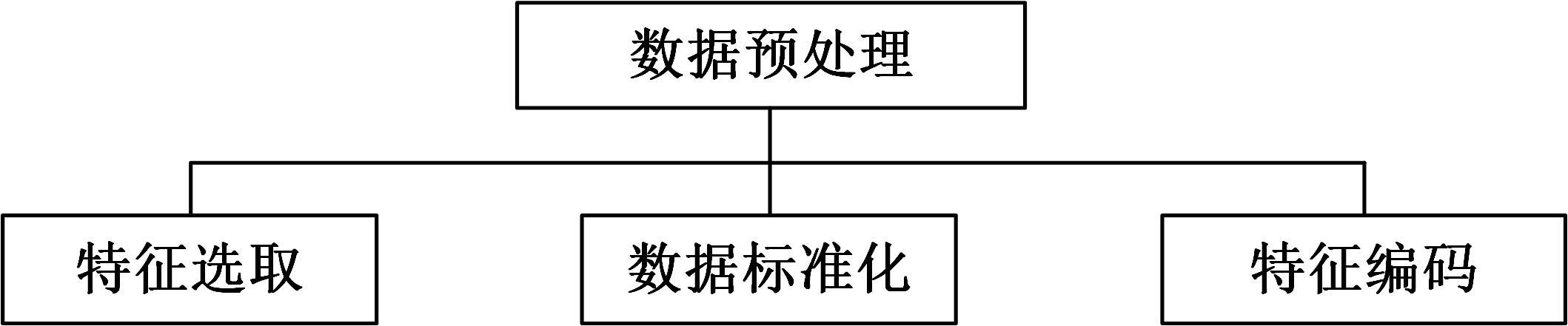
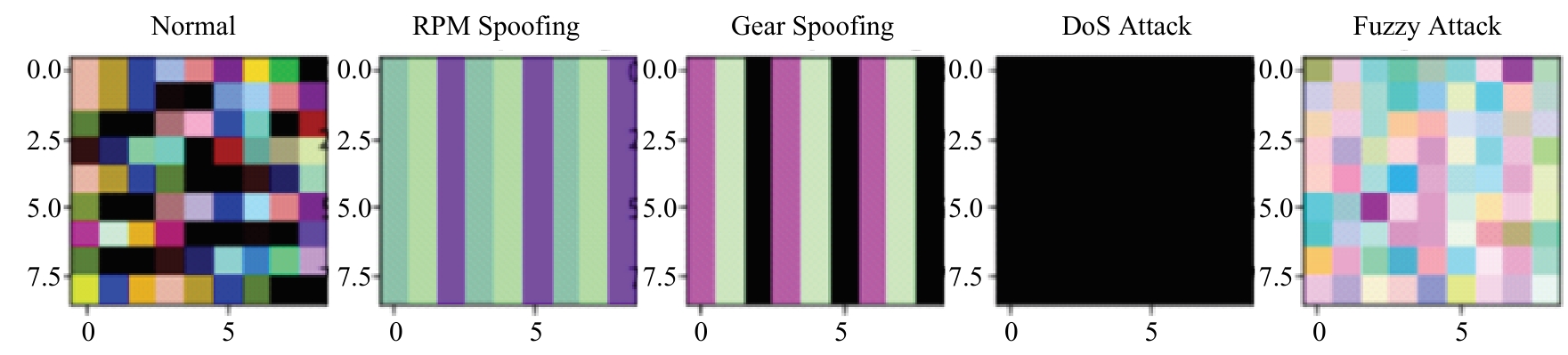
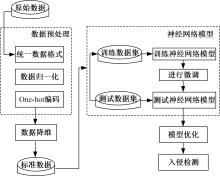
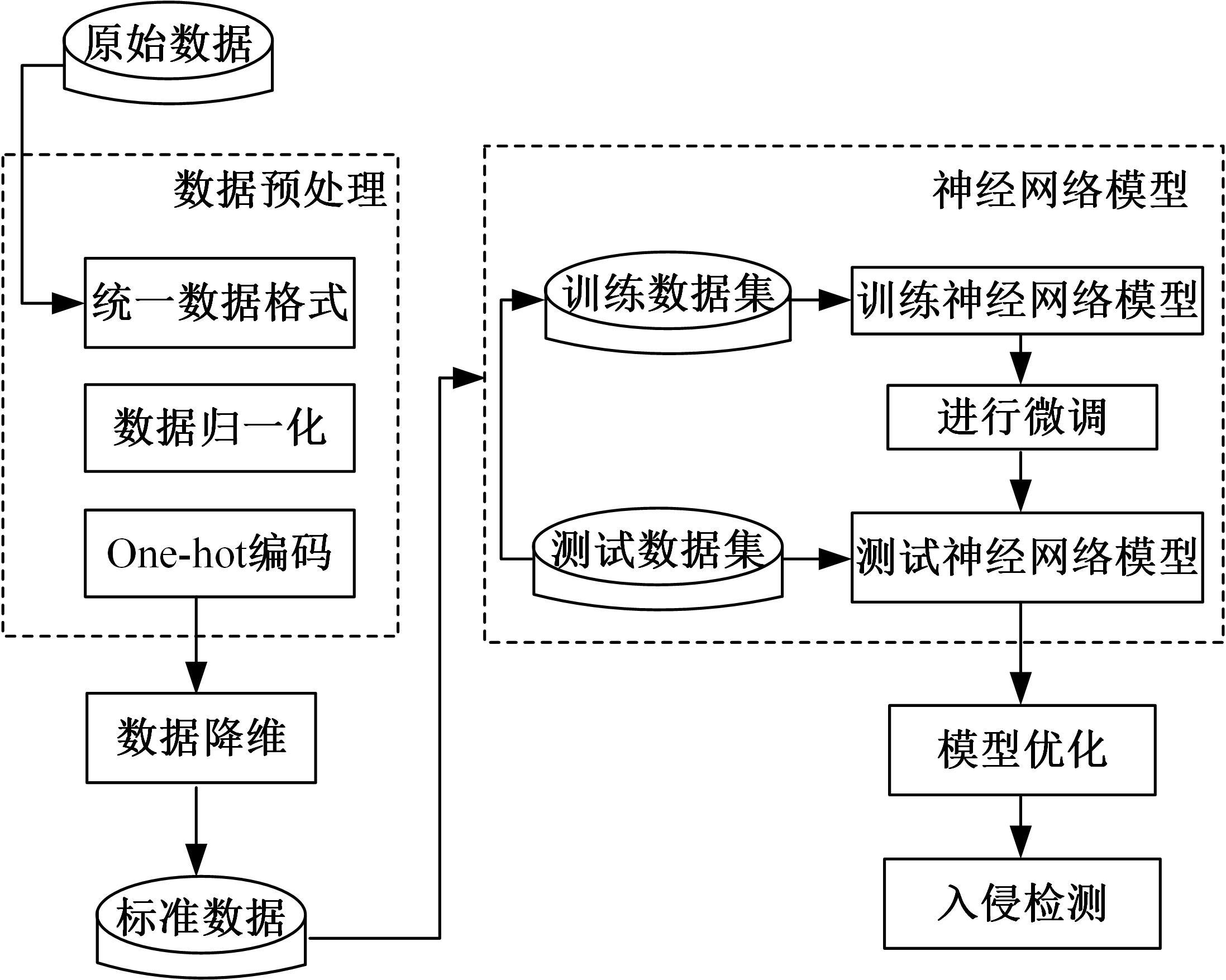
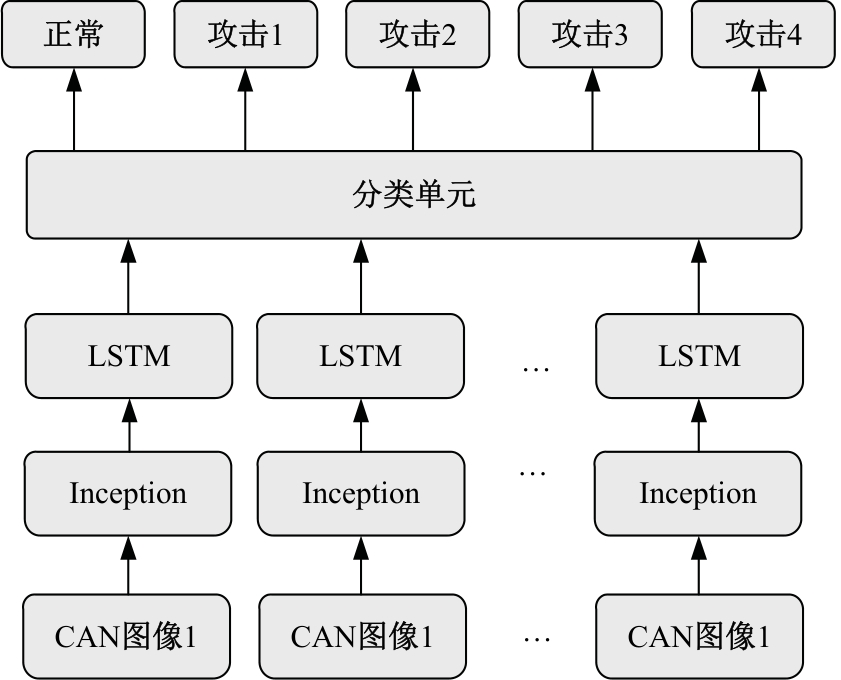
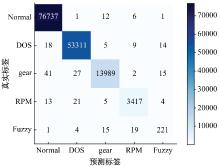
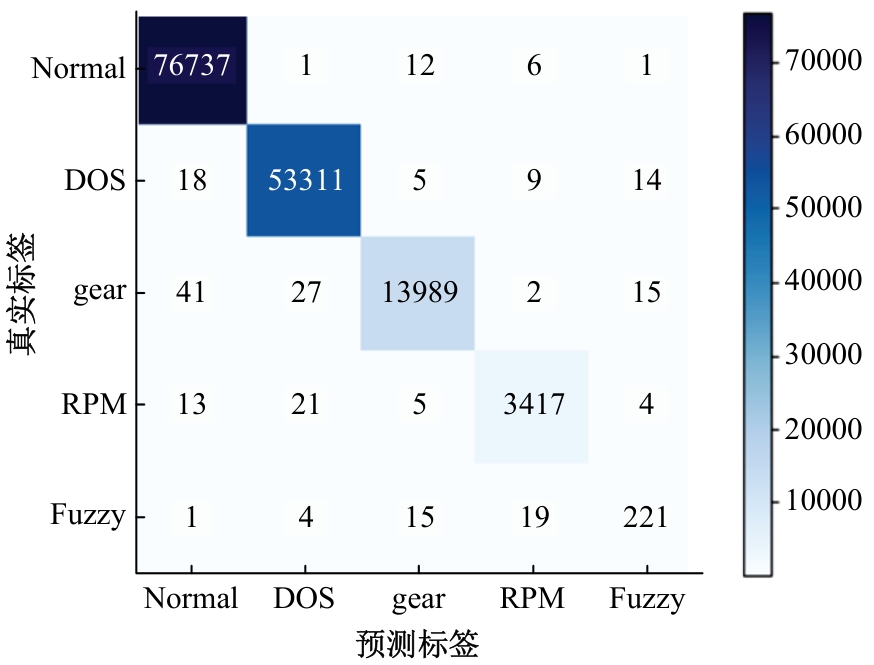
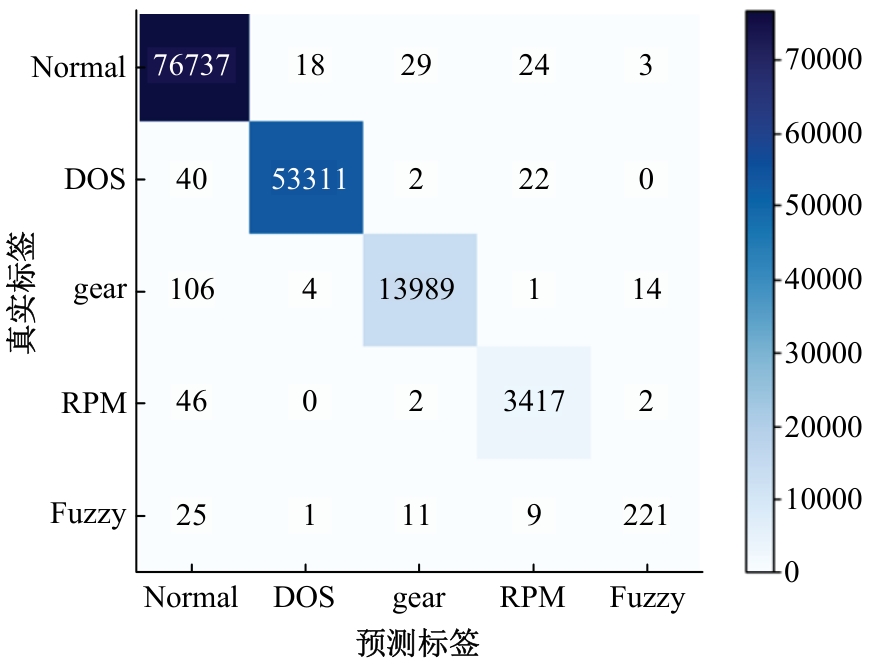
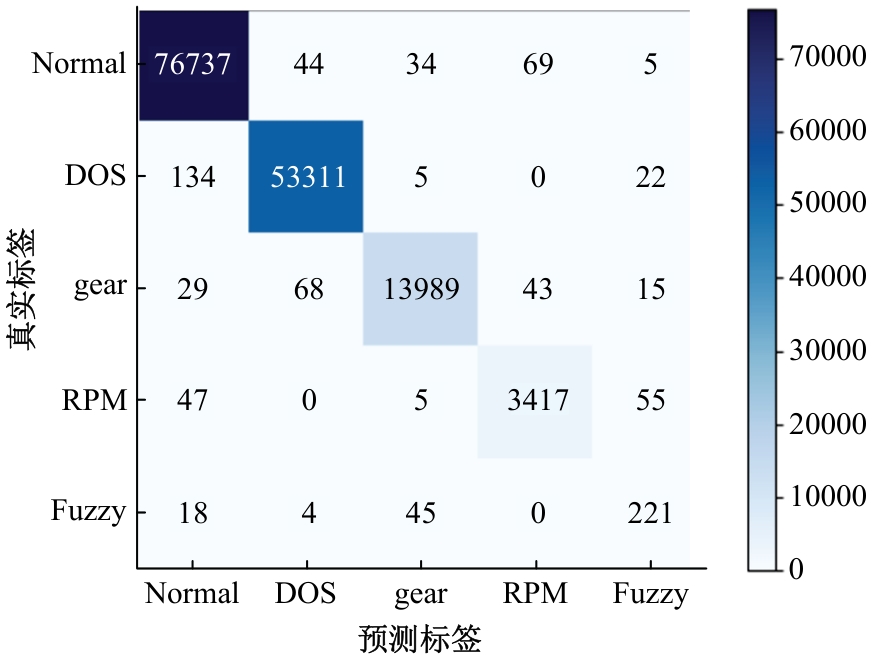
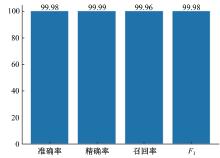
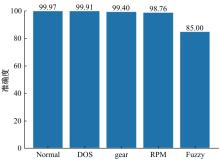
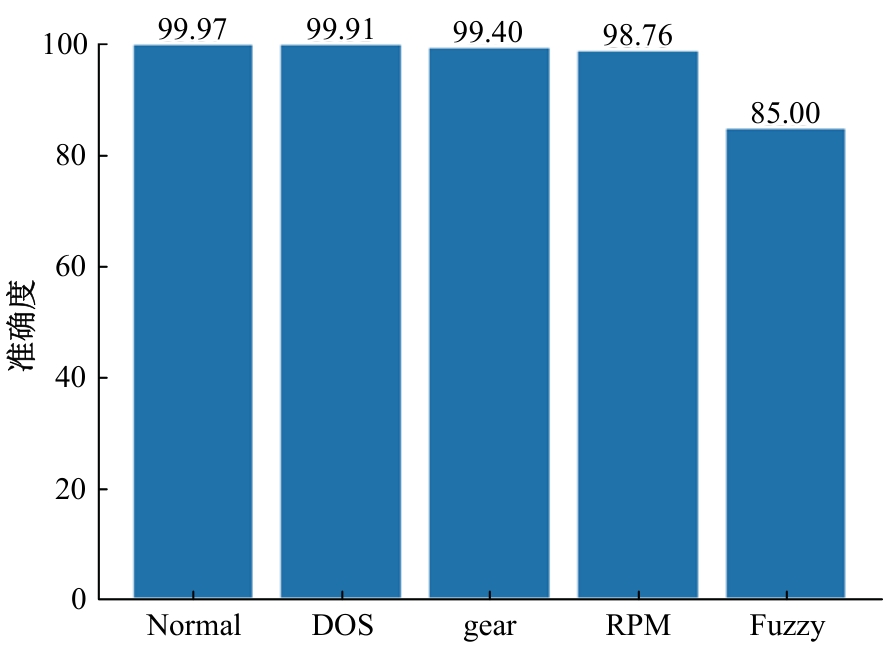
提出了一种基于控制器局域网(CAN)总线数据的新型车载网络入侵检测方法——IncepNet方法。首先,选取一个真实的汽车黑客攻击数据集(Car-hacking dataset),对其进行数据预处理,使用图像处理方法将该数据集中的时间序列数据按照一定规则重新组织,转换为适合作为卷积神经网络输入的图片数据。其次,优化现有的残差网络(Inception-ResNet),并在其后添加了具有多批次归一化功能的长短期记忆神经网络(LSTM)层和丢弃层(Dropout)。最后,使用包括识别率、准确率、F1分数(F1-score)和误报次数(FAR)在内的混淆矩阵,证明本文模型具有卓越的准确性和可靠性。研究结果表明:本文模型具有低误报率、高检测准确率和高检测率,其效率明显优于以往基于其他机器学习的检测方法。
中图分类号:
- TP393
| 1 | Miller C, Valasek C. Remote exploitation of an unaltered passenger vehicle[J]. Black Hat USA, 2015, 2015(S91): 1-91. |
| 2 | Javed A R, Ur Rehman S, Khan M U, et al. CANintelliIDS: detecting in-vehicle intrusion attacks on a controller area network using CNN and attention-based GRU[J]. IEEE Transactions on Network Science and Engineering, 2021, 8(2): 1456-1466. |
| 3 | Kim S H, Seo S H, Kim J H, et al. A gateway system for an automotive system: LIN, CAN, and FlexRay[C]∥6th IEEE International Conference on Industrial Informatics, Foshan, China, 2008: 967-972. |
| 4 | Farsi M, Ratcliff K, Barbosa M. An overview of controller area network[J]. Computing & Control Engineering Journal, 1999, 10(3): 113-120. |
| 5 | 朱鹏程, 涂江健, 招志才, 等. 车联网威胁分析和入侵检测关键技术[J]. 自动化博览, 2022,39(1):88-93. |
| Zhu Peng-cheng, Tu Jiang-jian, Zhao Zhi-cai, et al. Key technologies for threat analysis and intrusion detection in telematics[J]. Automation Expo, 2022, 39(1): 88-93. | |
| 6 | Checkoway S, McCoy D, Kantor B, et al. Comprehensive experimental analyses of automotive attack surfaces[C]∥20th USENIX Security Symposium,San Francisco,USA, 2011: 99-114. |
| 7 | Xu Z, Wang Z. Feature selection-based intrusion detection system for internet of vehicles[J]. IEEE Transactions on Intelligent Transportation Systems,2021,22(1): 1-11. |
| 8 | Song Y, Du J, Chen X, et al. Anomaly detection algorithm based on improved one-class support vector machine[J]. Journal of Ambient Intelligence and Humanized Computing,2019, 10(1): 219-228. |
| 9 | Wu S, Xu J, Wang Y,et al. Anomaly detection algorithm based on improved spectral clustering[J]. Journal of Ambient Intelligence and Humanized Computing,2022, 13(1): 513-521. |
| 10 | 丁宝星. 基于人工智能的网络入侵检测与防御研究[J]. 中国信息化, 2023(11): 76-78. |
| Ding Bao-xing. Research on network intrusion detection and defense based on artificial intelligence[J]. China Informatization, 2023(11):76-78. | |
| 11 | 陈力, 王海江, 吴凯. 基于卷积神经网络的车载网络入侵检测方法[J].浙江科技学院学报, 2021, 33(1):59-66, 84. |
| Chen Li, Wang Hai-jiang, Wu Kai. Intrusion detection method for in-vehicle networks based on convolutional neural networks[J]. Journal of Zhejiang Institute of Science and Technology, 2021, 33(1):59-66, 84. | |
| 12 | Zhang J, Wu Z C, Li F, et al. A deep learning framework for driving behavior identification on in-vehicle CAN-BUS sensor data[J]. Sensors, 2019, 19(6): 1356. |
| 13 | Chung J, Gulcehre C, Cho K H, et al. Empirical evaluation of gated recurrent neural networks on sequence modeling[J/OL]. [2024-01-05]. |
| 14 | 关宇昕, 冀浩杰, 崔哲, 等. 智能网联汽车车载CAN网络入侵检测方法综述[J]. 汽车工程, 2023,45(6): 922-935. |
| Guan Yu-xin, Ji Hao-jie, Cui Zhe, et al. A review of intrusion detection methods for in-vehicle CAN networks in smart connected vehicles[J]. Automotive Engineering,2023, 45(6): 922-935. | |
| 15 | Sun H, Chen M, Weng J, et al. Anomaly detection for in-vehicle network using CNN-LSTM with attention mechanism[J]. IEEE Transactions on Vehicular Technology, 2021, 70(10): 10880-10893. |
| 16 | Seo E, Song H M, Kim H K. GIDS: GAN based intrusion detection system for in-vehicle network[C]∥16th Annual Conference on Privacy, Security and Trust (PST),Waterloo, Canada,2018: 1-6. |
| 17 | Ergen T, Kozat S S. Unsupervised anomaly detection with LSTM neural networks[J]. IEEE transactions on Neural Networks and Learning Systems, 2019, 31(8): 3127-3141. |
| 18 | Song H M, Kim H K. Can network intrusion datasets[EB/OL].[2024-01-06]. |
| [1] | 丁海兰,祁坤钰. 基于TextRank算法和相似度的中文文本主题句自动提取[J]. 吉林大学学报(工学版), 2025, 55(3): 1001-1008. |
| [2] | 王娜,崔月磊,李杨,王子从. 基于小波包对数能量图的滚动轴承故障诊断方法[J]. 吉林大学学报(工学版), 2025, 55(2): 494-502. |
| [3] | 车翔玖,武宇宁,刘全乐. 基于因果特征学习的有权同构图分类算法[J]. 吉林大学学报(工学版), 2025, 55(2): 681-686. |
| [4] | 蔡晓东,周青松,张言言,雪韵. 基于动静态和关系特征全局捕获的社交推荐模型[J]. 吉林大学学报(工学版), 2025, 55(2): 700-708. |
| [5] | 胡宏宇,张争光,曲优,蔡沐雨,高菲,高镇海. 基于双分支和可变形卷积网络的驾驶员行为识别方法[J]. 吉林大学学报(工学版), 2025, 55(1): 93-104. |
| [6] | 汪豪,赵彬,刘国华. 基于时间和运动增强的视频动作识别[J]. 吉林大学学报(工学版), 2025, 55(1): 339-346. |
| [7] | 曲广雷,闫宗伟,郑木莲,刘红,袁月明. 基于神经网络与回归分析的多孔混凝土性能预测[J]. 吉林大学学报(工学版), 2025, 55(1): 269-282. |
| [8] | 张磊,焦晶,李勃昕,周延杰. 融合机器学习和深度学习的大容量半结构化数据抽取算法[J]. 吉林大学学报(工学版), 2024, 54(9): 2631-2637. |
| [9] | 商蕾,杨萍,杨祥国,潘建欣,杨军,张梦如. 基于APSO-BP-PID控制的质子交换膜燃料电池热管理系统温度控制[J]. 吉林大学学报(工学版), 2024, 54(9): 2401-2413. |
| [10] | 杨军,韩鹏飞. 采用神经网络架构搜索的高分辨率遥感影像目标检测[J]. 吉林大学学报(工学版), 2024, 54(9): 2646-2657. |
| [11] | 特木尔朝鲁朝鲁,张亚萍. 基于卷积神经网络的无线传感器网络链路异常检测算法[J]. 吉林大学学报(工学版), 2024, 54(8): 2295-2300. |
| [12] | 朱圣杰,王宣,徐芳,彭佳琦,王远超. 机载广域遥感图像的尺度归一化目标检测方法[J]. 吉林大学学报(工学版), 2024, 54(8): 2329-2337. |
| [13] | 赵宏伟,武鸿,马克,李海. 基于知识蒸馏的图像分类框架[J]. 吉林大学学报(工学版), 2024, 54(8): 2307-2312. |
| [14] | 张锦洲,姬世青,谭创. 融合卷积神经网络和双边滤波的相贯线焊缝提取算法[J]. 吉林大学学报(工学版), 2024, 54(8): 2313-2318. |
| [15] | 朱国庆,刘显成,田从祥. 基于长短期记忆网络的公共建筑短期能耗预测模型[J]. 吉林大学学报(工学版), 2024, 54(7): 2009-2014. |
|
||