吉林大学学报(工学版) ›› 2025, Vol. 55 ›› Issue (5): 1497-1515.doi: 10.13229/j.cnki.jdxbgxb.20240381
基于深度学习的图像信息隐藏方法综述
- 1.大连民族大学 机电工程学院,辽宁 大连 116600
2.北京航空航天大学 网络空间安全学院,北京 100191
Review on image information hiding methods based on deep learning
Ru-bo ZHANG1( ),Shi-qi CHANG1,Tian-yi ZHANG2(
),Shi-qi CHANG1,Tian-yi ZHANG2( )
)
- 1.College of Mechanical & Electronic Engineering,Dalian Minzu University,Dalian 116600,China
2.School of Cyber Science and Technology,Beihang University,Beijing 100191,China
摘要:
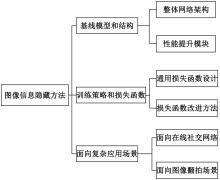
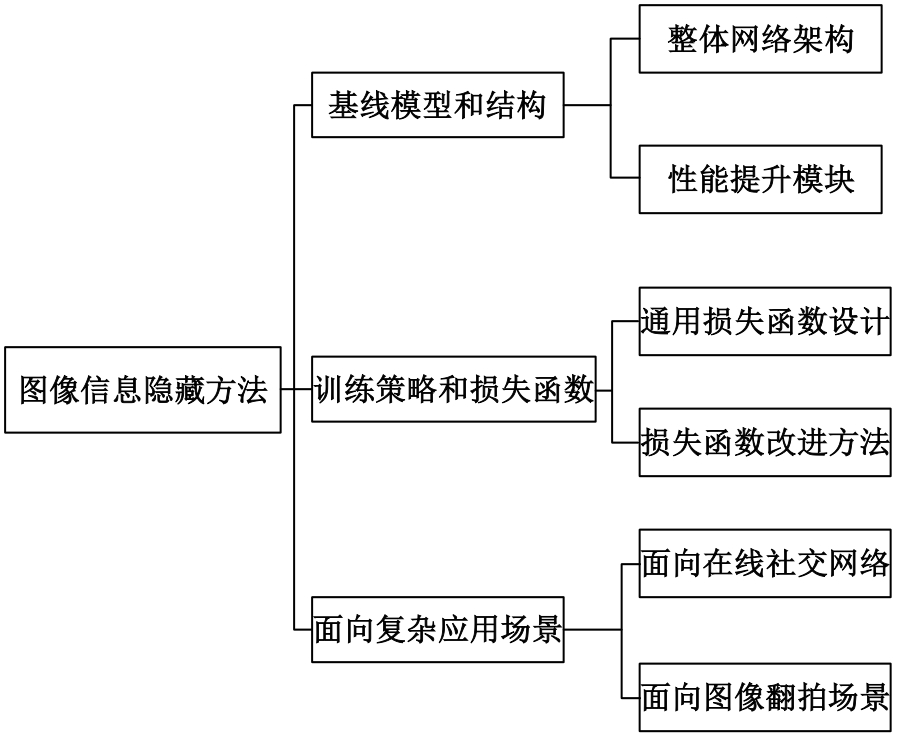
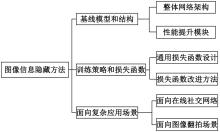
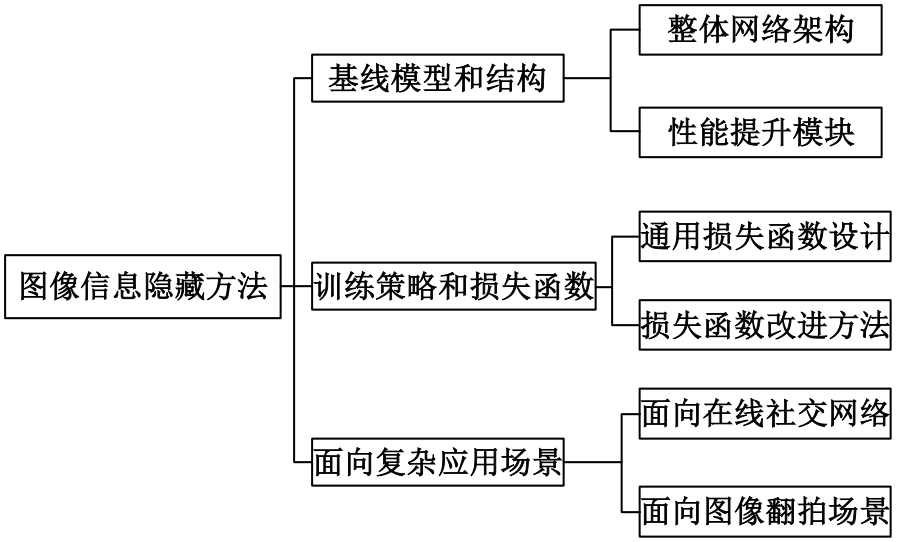
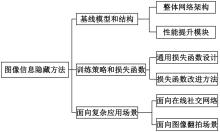
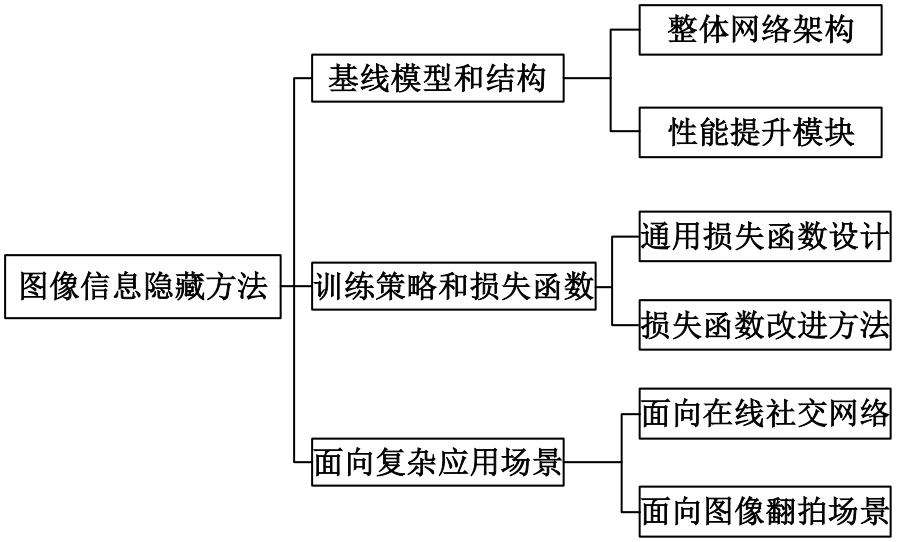
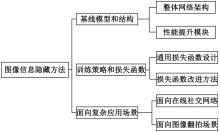
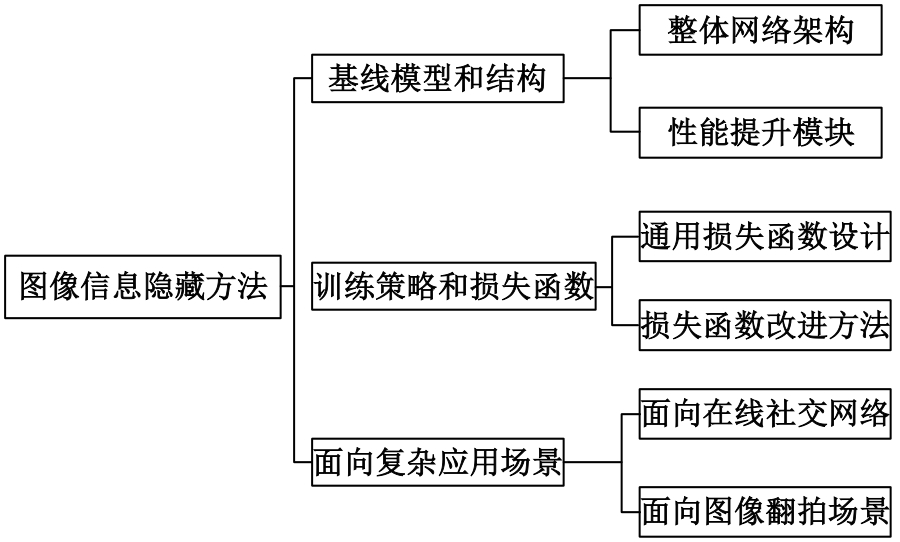
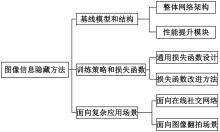
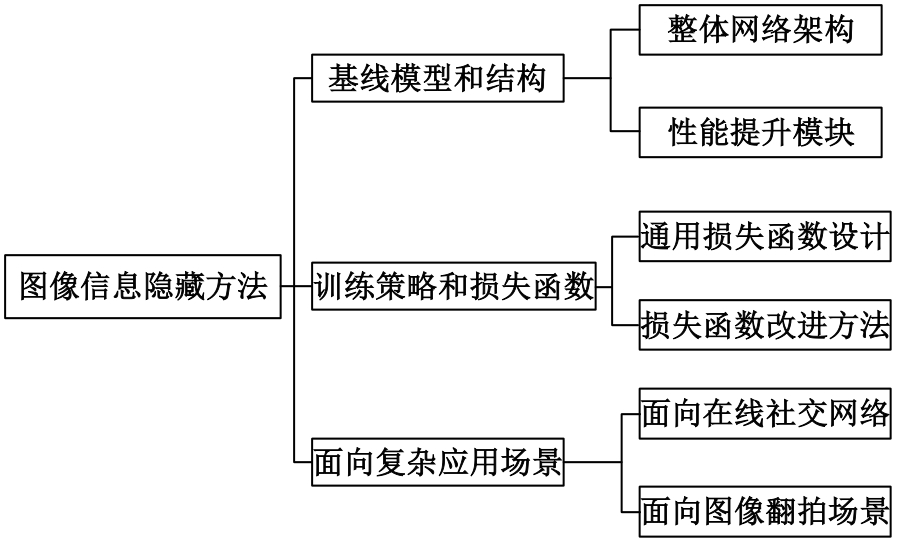
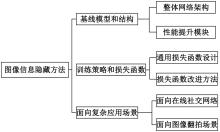
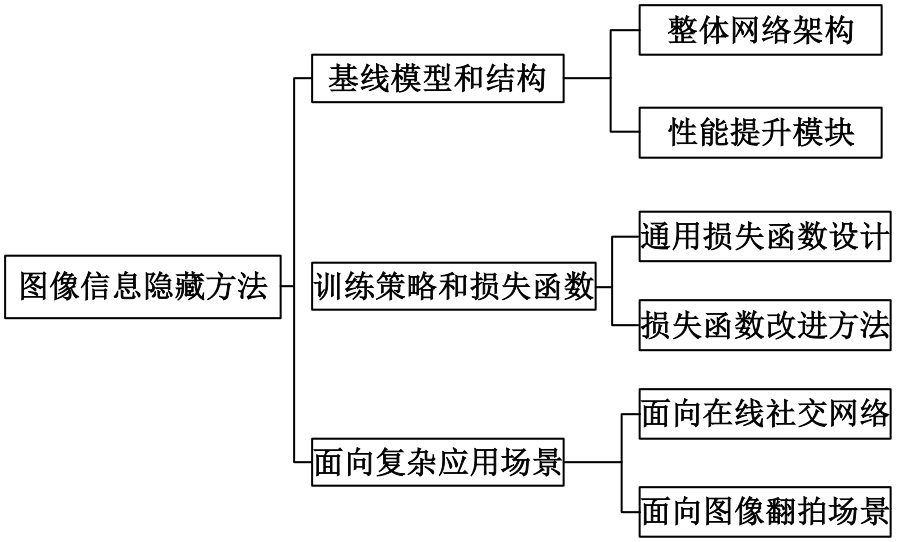
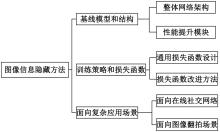
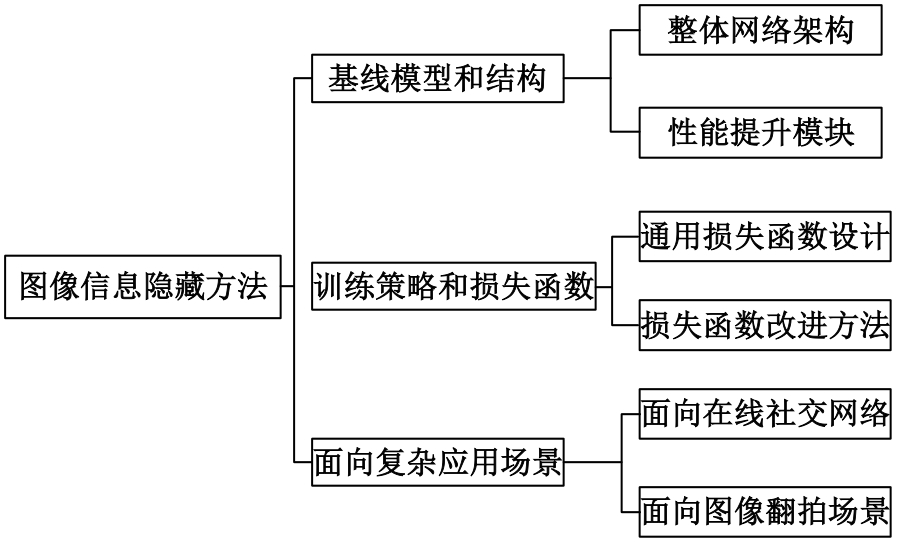
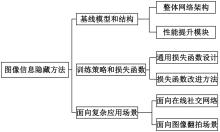
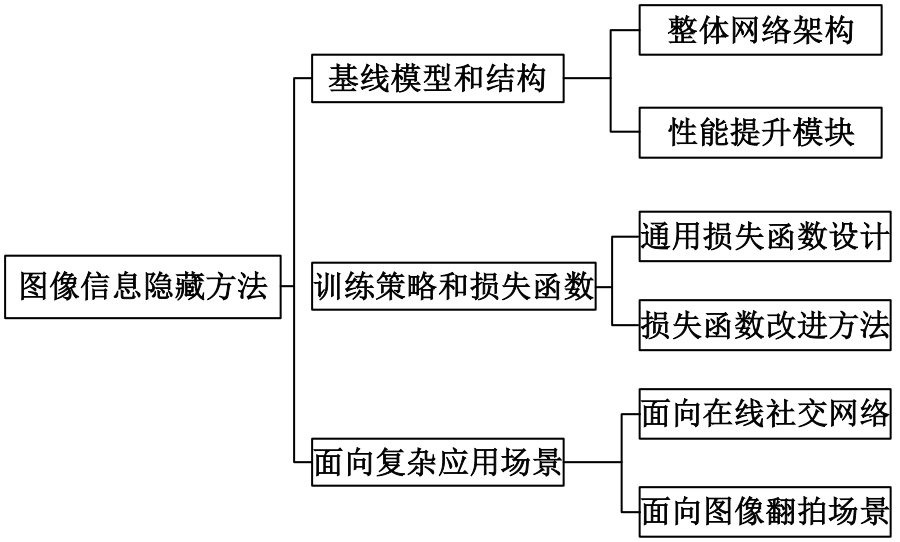
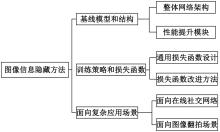
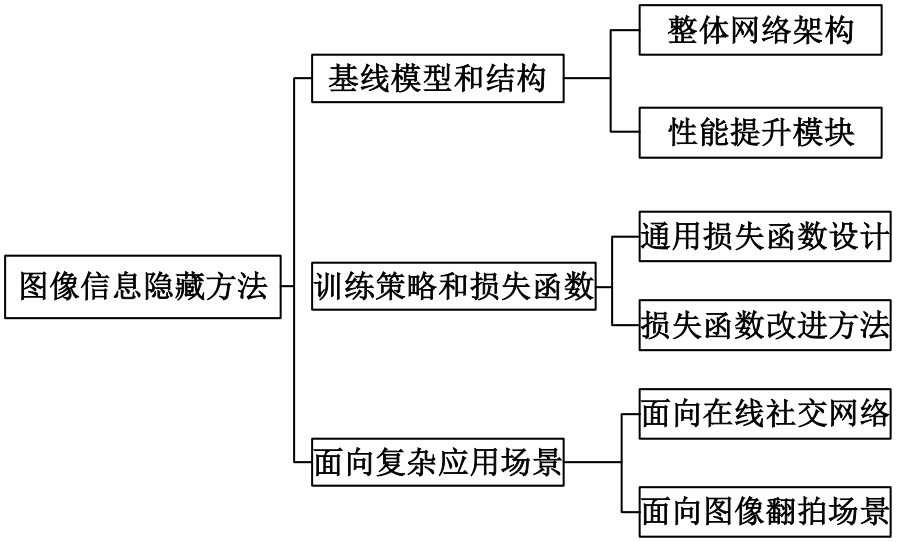
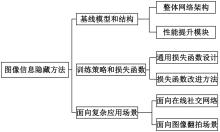
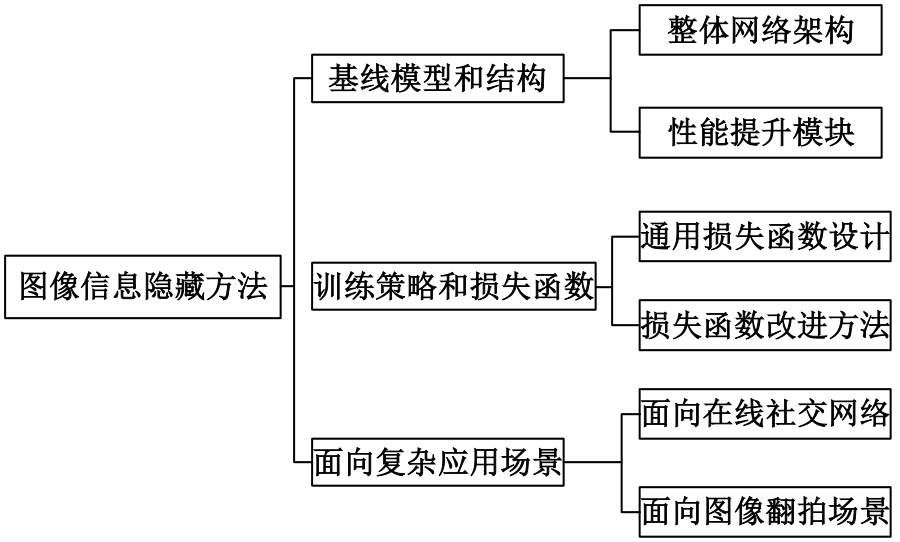
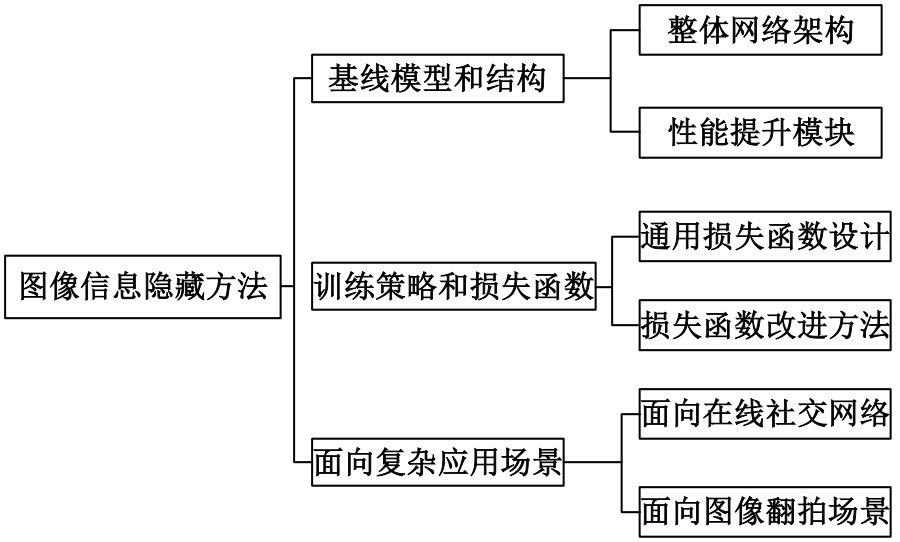
基于图像的信息隐藏技术可以实现将信息隐蔽地藏于图像内容中,从而在图片的传输过程中实现保密通信、版权认证等信息安全保护行为,是目前信息安全领域研究的热点之一。本文首先论述了基于深度学习的图像信息隐藏方法的重难点问题;其次,从结构特点、训练特点和应用特点3个角度对基于深度学习的图像隐写方法进行归纳;再次,介绍了领域相关主要数据集和评估指标;然后,总结了图像信息隐藏技术的应用情况;最后,讨论了图像信息隐藏技术的研究方向,为该领域的进一步发展提供见解和建议。
中图分类号:
- TP309.7
| [1] | 张卫明, 王宏霞, 李斌, 等. 多媒体隐写研究进展[J]. 中国图象图形学报, 2022, 27(6): 1918-1943. |
| Zhang Wei-ming, Wang Hong-xia, Li Bin, et al. Overview of steganography on multimedia[J]. Journal of Image and Graphics, 2022, 27(6): 1918-1943. | |
| [2] | Subramanian N, Elharrouss O, Almaadeed S, et al. Image steganography: a review of the recent advances[J]. IEEE Access, 2021, 9: 23409-23423. |
| [3] | Tsai P, Hu Y C, Yeh H L. Reversible image hiding scheme using predictive coding and histogram shifting[J]. Signal Processing, 2009, 89(6): 1129-1143. |
| [4] | Pan F, Li J, Yang X. Image steganography method based on PVD and modulus function[C]∥2011 International Conference on Electronics, Communications and Control (ICECC), Ningbo, China, 2011: 282-284. |
| [5] | 孙曦, 张卫明, 俞能海, 等. 基于空域图像变换参数扰动的隐写术[J]. 通信学报, 2017, 38(10): 166-174. |
| Sun Xi, Zhang Wei-ming, Yu Neng-hai, et al. Steganography based on parameters' disturbance of spatial image transform[J]. Journal on Communications, 2017, 38 (10): 166-174. | |
| [6] | Rustad S, Syukur A, Andono P N. Inverted LSB image steganography using adaptive pattern to improve imperceptibility[J]. Journal of King Saud University-Computer and Information Sciences, 2022, 34(6): 3559-3568. |
| [7] | Fazli S, Moeini M. A robust image watermarking method based on DWT, DCT, and SVD using a new technique for correction of main geometric attacks[J]. Optik-International Journal for Light and Electron Optics, 2016, 127(2): 964-972. |
| [8] | Abadi R Y, Moallem P. Robust and optimum color image watermarking method based on a combination of DWT and DCT[J]. Optik, 2022, 261: No.169146. |
| [9] | 赵瑶瑶, 李万社. 基于离散小波变换和离散余弦变换的彩色图像水印算法[J].应用数学进展, 2021, 10: No.1096. |
| Zhao Yao-yao, Li Wan-she. Color image watermarking algorithm based on discrete wavelet transform and discrete cosine transform[J]. Advances in Applied Mathematics, 2021,10: No.1096. | |
| [19] | Wang R Z, Lin C F, Lin J C. Image hiding by optimal LSB substitution and genetic algorithm[J]. Pattern Recognition, 2001, 34(3): 671-683. |
| [11] | Fridrich J, Goljan M, Du R. Detecting LSB steganography in color, and gray-scale images[J]. IEEE Multimedia, 2001, 8(4): 22-28. |
| [12] | Mandal P C, Mukherjee I, Paul G, et al. Digital image steganography: a literature survey[J]. Information Sciences, 2022, 609: 1451-1488. |
| [13] | Chhikara S, Kumar R. Information theoretic steganalysis of processed image LSB steganography[J]. Multimedia Tools and Applications, 2023, 82(9): 13595-13615. |
| [14] | 付章杰, 李恩露, 程旭, 等. 基于深度学习的图像隐写研究进展[J]. 计算机研究与发展, 2021, 58(3): 548-568. |
| Fu Zhang-jie, Li En-lu, Cheng Xu, et al. Recent advances in image steganography based on deep learning[J]. Journal of Computer Research and Development, 2021, 58(3): 548-568. | |
| [15] | Ehrlich M, Davis L, Lim S N, et al. Analyzing and mitigating jpeg compression defects in deep learning[C]∥Proceedings of the IEEE/CVF International Conference on Computer Vision, Montreal, Canada, 2021: 2357-2367. |
| [16] | Khayam S A. The discrete cosine transform (DCT): theory and application[J]. Journal of Michigan State University, 2003, 114(1): 1-31. |
| [17] | Poyueh P Y, Lin H J. A DWT based approach for image steganography[J]. International Journal of Applied Science and Engineering, 2006, 4(3): 275-290. |
| [18] | Ruanaidh J, Dowling W J, Boland F M. Phase watermarking of digital images[J]. Proceedings of 3rd IEEE International Conference on Image Processing, 1996, 3: 239-242. |
| [19] | Li Y. Research and application of deep learning in image recognition[C]∥2022 IEEE 2nd International Conference on Power, Electronics and Computer Applications (ICPECA), Shenyang, China, 2022: 994-999. |
| [20] | 徐涛, 马克, 刘才华. 基于深度学习的行人多目标跟踪方法[J]. 吉林大学学报: 工学版, 2021, 51(1): 27-38. |
| Xu Tao, Ma Ke, Liu Cai-hua. Multi object pedestrian tracking based on deep learning[J]. Journal of Jilin University (Engineering and Technology Edition), 2021, 51(1): 27-38. | |
| [21] | Lopez M M, Kalita J. Deep learning applied to NLP[J/OL]. [2024-04-01]. |
| [22] | Zhang Z, Geiger J, Pohjalainen J, et al. Deep learning for environmentally robust speech recognition: an overview of recent developments[J]. ACM Transactions on Intelligent Systems and Technology (TIST), 2018, 9(5): 1-28. |
| [23] | 黄立威, 江碧涛, 吕守业, 等. 基于深度学习的推荐系统研究综述[J]. 计算机学报, 2018, 41(7): 1619-1647. |
| Huang Li-wei, Jiang Bi-tao, Shou-ye Lyu, et al. Survey on deep learning based recommender systems[J]. Chinese Journal of Computers, 2018, 41(7): 1619-1647. | |
| [24] | Heaton J B, Polson N G, Witte J H. Deep learning for finance: deep portfolios[J]. Applied Stochastic Models in Business and Industry, 2017, 33(1): 3-12. |
| [25] | 沈权猷, 张小波, 李文豪, 等. U-Net在肺结节分割中的应用进展[J]. 计算机应用, 2023, 43(): 250-257. |
| Shen Quan-you, Zhang Xiao-bo, Li Wen-hao, et al. Progress of U-Net applications to lung nodule segmentation[J]. Journal of Computer Applications, 2023,43(Sup.1): 250-257. | |
| [26] | Alom M Z, Yakopcic C, Hasan M, et al. Recurrent residual U-Net for medical image segmentation[J]. Journal of Medical Imaging, 2019, 6(1): No.014006. |
| [27] | 付章杰, 王帆, 孙星明, 等. 基于深度学习的图像隐写方法研究[J]. 计算机学报, 2020, 43(9): 1656-1672. |
| Fu Zhang-jie, Wang Fan, Sun Xing-ming, et al. Research on steganography of digital images based on deep learning[J]. Chinese Journal of Computers, 2020,43(9): 1656-1672. | |
| [28] | 张茹, 刘建毅, 刘功申, 等. 数字内容安全[M]. 北京: 北京邮电大学出版社, 2017. |
| [29] | Sara U, Akter M, Uddin M S. Image quality assessment through FSIM, SSIM, MSE and PSNR—a comparative study[J]. Journal of Computer and Communications, 2019, 7(3): 8-18. |
| [30] | Xu G, Wu H Z, Shi Y Q. Structural design of convolutional neural networks for steganalysis[J]. IEEE Signal Processing Letters, 2016, 23(5): 708-712. |
| [31] | Geng L, Zhang W, Chen H, et al. Real-time attacks on robust watermarking tools in the wild by CNN[J]. Journal of Real-Time Image Processing, 2020, 17: 631-641. |
| [32] | Wei P, Zhu Z, Luo G, et al. Breaking robust data hiding in online social networks[J]. IEEE Signal Processing Letters, 2022, 29: 2682-2686. |
| [33] | Chaumont M. Deep Learning in Steganography and Steganalysis[M]. New York: Academic Press, 2020. |
| [34] | 夏道勋, 王林娜, 宋允飞, 等. 深度神经网络模型数字水印技术研究进展综述[J]. 科学技术与工程, 2023, 23(5): 1799-1811. |
| Xia Dao-xun, Wang Lin-na, Song Yun-fei, et al. Review of deep neural network digital watermarking technology[J]. Science Technology and Engineering, 2023, 23(5): 1799-1811. | |
| [35] | Denis R, Madhubala P. Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare systems[J]. Multimedia Tools and Applications, 2021, 80: 21165-21202. |
| [36] | Jiang X H. Digital watermarking and its application in image copyright protection[C]∥2010 International Conference on Intelligent Computation Technology and Automation, Changsha, China, 2010: 114-117. |
| [37] | Megías D, Mazurczyk W, Kuribayashi M. Data hiding and its applications: digital watermarking and steganography[J]. Applied Sciences, 2021, 11(22): No.10928. |
| [38] | 赵洁, 邹天宇, 黄展鹏, 等. 基于手写数字水印的医学图像版权保护研究[J]. 医疗卫生装备, 2016, 37(6): 36-38. |
| Zhao Jie, Zou Tian-yu, Huang Zhan-peng, et al. Research on copyright protection of medical images based on handwritten digital watermarking[J]. Chinese Medical Equipment Journal, 2016, 37(6): 36-38. | |
| [39] | 周娜, 成茗, 贾孟霖, 等. 基于缩略图加密和分布式存储的医学图像隐私保护[J]. 计算机应用, 2023, 43(10): 3149-3155. |
| Zhou Na, Cheng Ming, Jia Meng-lin, et al. Medical image privacy protection based on thumbnail encryption and distributed storage[J]. Journal of Computer Applications, 2023, 43(10): 3149-3155. | |
| [40] | 刘佳, 柯彦, 雷雨, 等. 生成对抗网络在图像隐写中的应用[J]. 武汉大学学报: 理学版, 2019, 65(2): 139-152. |
| Liu Jia, Ke Yan, Lei Yu, et al. Application of generative adversarial networks in image steganography[J]. Journal of Wuhan University (Science Edition), 2019, 65 (2): 139-152. | |
| [41] | Zhang K A, Cuesta I A, Xu L, et al. SteganoGAN: high capacity image steganography with GANs[J/OL].[2024-04-01]. |
| [42] | Singh B, Sharma P K, Huddedar S A, et al. StegGAN: hiding image within image using conditional generative adversarial networks[J]. Multimedia Tools and Applications, 2022, 81(28): 40511-40533. |
| [43] | Wang Z, Gao N, Wang X, et al. SSteGAN: self-learning steganography based on generative adversarial networks[C]∥Neural Information Processing: 25th International Conference, Siem Reap, Cambodia, 2018: 253-264. |
| [44] | Zhu J, Kaplan R, Johnson J, et al. Hidden: hiding data with deep networks[C]∥Proceedings of the European conference on computer vision (ECCV), Munich, Germany, 2018: 657-672. |
| [45] | Sun W, Zhou J, Li Y, et al. Robust high-capacity watermarking over online social network shared images[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2020, 31(3): 1208-1221. |
| [46] | Luo X, Zhan R, Chang H, et al. Distortion agnostic deep watermarking[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Seattle, USA, 2020: 13548-13557. |
| [47] | Zhang H, Wang H, Cao Y, et al. Robust data hiding using inverse gradient attention[J/OL]. [2024-04-01]. |
| [48] | Rahim R, Nadeem S. End-to-end trained CNN encoder-decoder networks for image steganography[C]∥Proceedings of the European Conference on Computer Vision (ECCV) Workshops, Munich, Germany, 2018: 723-729. |
| [49] | Kishore V, Chen X, Wang Y, et al. Fixed neural network steganography: train the images, not the network[C]∥International Conference on Learning Representations, Vienna, Austria, 2021: 1-10. |
| [50] | Dinh L, Krueger D, Bengio Y. Nice: non-linear independent components estimation[J/OL]. [2024-04-01]. |
| [51] | Ardizzone L, Kruse J, Wirkert S, et al. Analyzing inverse problems with invertible neural networks[J/OL]. [2024-04-01]. |
| [52] | Dinh L, Sohl D J, Bengio S. Density estimation using real NVP[C]∥ICLR 2017-Conference Track Proceedings, Toulon, France, 2019: No.160508803. |
| [53] | Jing J, Deng X, Xu M, et al. HiNet: deep image hiding by invertible network[C]∥Proceedings of the IEEE/CVF International Conference on Computer Vision, Montreal, Canada, 2021: 4733-4742. |
| [54] | Lu S P, Wang R, Zhong T, et al. Large-capacity image steganography based on invertible neural networks[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Nashville, USA, 2021: 10816-10825. |
| [55] | Xu Y, Mou C, Hu Y, et al. Robust invertible image steganography[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, USA, 2022: 7875-7884. |
| [56] | Guan Z, Jing J, Deng X, et al. DeepMIH: deep invertible network for multiple image hiding[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2022, 45(1): 372-390. |
| [57] | Yang H, Xu Y, Liu X, et al. PRIS: practical robust invertible network for image steganography[J/OL]. [2024-04-01]. |
| [58] | Mou C, Xu Y, Song J, et al. Large-capacity and flexible video steganography via invertible neural network[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, Canada, 2023: 22606-22615. |
| [59] | Bui T, Agarwal S, Yu N, et al. Rosteals: robust steganography using autoencoder latent space[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, Canada, 2023: 933-942. |
| [60] | Liu Y, Guo M, Zhang J, et al. A novel two-stage separable deep learning framework for practical blind watermarking[C]∥Proceedings of the 27th ACM International Conference on Multimedia,Nice, France, 2019: 1509-1517. |
| [61] | Yu C. Attention based data hiding with generative adversarial networks[J]. Proceedings of the AAAI Conference on Artificial Intelligence, 2020, 34(1): 1120-1128. |
| [62] | Tan J, Liao X, Liu J, et al. Channel attention image steganography with generative adversarial networks[J]. IEEE Transactions on Network Science and Engineering, 2021, 9(2): 888-903. |
| [63] | Cui J, Zhang P, Li S, et al. Multitask identity-aware image steganography via minimax optimization[J]. IEEE Transactions on Image Processing, 2021, 30: 8567-8579. |
| [64] | Tancik M, Mildenhall B, Ng R. Stegastamp: invisible hyperlinks in physical photographs[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition,Seattle, USA, 2020: 2117-2126. |
| [65] | Wei P, Li S, Zhang X, et al. Generative steganography network[C]∥Proceedings of the 30th ACM International Conference on Multimedia, New York, USA, 2022: 1621-1629. |
| [66] | Liu X, Ma Z, Ma J, et al. Image disentanglement autoencoder for steganography without embedding[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, USA, 2022: 2303-2312. |
| [67] | You Z, Ying Q, Li S, et al. Image generation network for covert transmission in online social network[C]∥Proceedings of the 30th ACM International Conference on Multimedia, New York, USA, 2022: 2834-2842. |
| [68] | Hu D, Detone D, Malisiewicz T. Deep charuco: dark charuco marker pose estimation[C]∥Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Long Beach, USA, 2019: 8436-8444. |
| [69] | Deng J, Dong W, Socher R, et al. Imagenet: a large-scale hierarchical image database[C]∥IEEE Conference on Computer Vision and Pattern Recognition, Miami, USA, 2009: 248-255. |
| [70] | Zhang C, Benz P, Karjauv A, et al. Udh: universal deep hiding for steganography, watermarking, and light field messaging[J]. Advances in Neural Information Processing Systems, 2020, 33: 10223-10234. |
| [71] | Lin T Y, Maire M, Belongie S, et al. Microsoft coco: common objects in context[C]∥Computer Vision-ECCV 2014: 13th European Conference, Zurich, Switzerland, 2014: 740-755. |
| [72] | Eirikur A, Radu T. NTIRE 2017 challenge on single image super-resolution: dataset and study[C]∥Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Honolulu, USA, 2017: 126-135. |
| [73] | Liu Z, Luo P, Wang X, et al. Deep learning face attributes in the wild[C]∥Proceedings of the IEEE International Conference on Computer Vision, Santiago, Chile, 2015: 3730-3738. |
| [74] | Bas P, Filler T, Pevný T. Break our steganographic system: the ins and outs of organizing boss[C]∥International Workshop on Information Hiding, Berlin, Germany, 2011: 59-70. |
| [75] | Deng L. The mnist database of handwritten digit images for machine learning research best of the web [J]. IEEE Signal Processing Magazine, 2012, 29(6): 141-142. |
| [76] | Setiadi D R I M. PSNR vs SSIM: imperceptibility quality assessment for image steganography[J]. Multimedia Tools and Applications, 2021, 80(6): 8423-8444. |
| [77] | Zhang R, Isola P, Efros A A, et al. The unreasonable effectiveness of deep features as a perceptual metric[C]∥Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Salt Lake City, USA, 2018: 586-595. |
| [78] | Zhang L, Zhang L, Mou X, et al. FSIM: a feature similarity index for image quality assessment[J]. IEEE Transactions on Image Processing, 2011, 20(8): 2378-2386. |
| [79] | 杨榆, 雷敏. 信息隐藏与数字水印[M]. 北京: 北京邮电大学出版社, 2017. |
| [80] | Pandey B K, Pandey D, Wairya S, et al. Application of integrated steganography and image compressing techniques for confidential information transmission[J]. Cyber Security and Network Security, 2022, 3: 169-191. |
| [81] | Morkel T. Image Steganography Applications for Secure Communication[M]. Pretoria: University of Pretoria (South Africa), 2012. |
| [82] | Pandey D, Wairya S, Mahdawi R S, et al. Secret data transmission using advanced steganography and image compression[J]. International Journal of Nonlinear Analysis and Applications, 2021, 12: 1243-1257. |
| [83] | 张雪锋. 信息安全概论[M]. 北京: 人民邮电出版社, 2014. |
| [84] | 郑钢, 胡东辉, 戈辉, 等. 生成对抗网络驱动的图像隐写与水印模型[J]. 中国图象图形学报, 2021, 26(10): 2485-2502. |
| Zheng Gang, Hu Dong-hui, Ge Hui, et al. End-to-end image steganography and watermarking driven by generative adversarial networks[J]. Chinese Journal of Image and Graphics, 2021, 26(10): 2485-2502. | |
| [85] | 吴汉舟, 张杰, 李越, 等. 人工智能模型水印研究进展[J]. 中国图象图形学报, 2023, 28(6): 1792-1810. |
| Wu Han-zhou, Zhang Jie, Li Yue, et al. Research progress of artificial intelligence model watermarking[J]. Journal of Image and Graphics, 2023, 28(6): 1792-1810. | |
| [86] | 郑秋梅, 刘楠, 王风华. 基于复杂攻击的脆弱水印图像完整性认证算法[J]. 计算机科学, 2020, 47(10): 332-338. |
| Zheng Qiu-mei, Liu Nan, Wang Feng-hua. Complex attack based fragile watermarking for image integrity authentication algorithm[J]. Computer Science, 2020, 47(10): 332-338. | |
| [87] | 张文芳. 远程会诊中的医疗数据水印算法研究[D]. 南京: 南京信息工程大学计算机学院, 2023. |
| Zhang Wen-Fang. Research on medical data watermarking algorithm in remote consultation[D]. Nanjing: School of Computer Science, Nanjing University of Information Engineering, 2023. | |
| [88] | Zeng C, Liu J, Li J, et al. Multi-watermarking algorithm for medical image based on KAZE-DCT[J]. Journal of Ambient Intelligence and Humanized Computing, 2022, 15: 1735-1743. |
| [89] | 刘泳彬, 徐涛, 苏锐豪, 等. 基于数字水印的医学图像信息隐藏系统[J]. 现代计算机, 2019(20): 42-45. |
| Liu Yong-bin, Xu Tao, Su Rui-hao, et al. A medical image information hiding system based on digital watermarking[J]. Modern Computer, 2019(20): 42-45. | |
| [90] | Anand A, Singh A K. Watermarking techniques for medical data authentication: a survey[J]. Multimedia Tools and Applications, 2021, 80: 30165-30197. |
| [91] | Karakus S, Avci E. A new image steganography method with optimum pixel similarity for data hiding in medical images[J]. Medical Hypotheses, 2020, 139: No.109691. |
| [92] | Priyadharshini A, Umamaheswari R, Jayapandian N, et al. Securing medical images using encryption and LSB steganography[C]∥International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT), Bhilai, India, 2021: 1-5. |
| [93] | Balu S, Babu C N K, Amudha K. Secure and efficient data transmission by video steganography in medical imaging system[J]. Cluster Computing, 2019, 22(Sup.2): 4057-4063. |
| [94] | 卢臻. AI换脸骗局频现 人工智能出圈后如何监管? [N]. 通信信息报, 2023-06-14. |
| Lu Zhen. How to supervise after AI face changing scam occurs frequently? [N]. Journal of Communication Information, 2023-06-14. | |
| [95] | 魏哲哲. “AI换脸”, 便利背后有风险[N]. 人民日报, 2023-12-04. |
| Wei Zhe-zhe. "AI changing faces", convenience behind the risk [N]. People's Daily, 2023-12-04. |
| [1] | 李健,刘欢,李艳秋,王海瑞,关路,廖昌义. 基于THGS算法优化ResNet-18模型的图像识别[J]. 吉林大学学报(工学版), 2025, 55(5): 1629-1637. |
| [2] | 文斌,丁弈夫,杨超,沈艳军,李辉. 基于自选择架构网络的交通标志分类算法[J]. 吉林大学学报(工学版), 2025, 55(5): 1705-1713. |
| [3] | 薛雅丽,俞潼安,崔闪,周李尊. 基于级联嵌套U-Net的红外小目标检测[J]. 吉林大学学报(工学版), 2025, 55(5): 1714-1721. |
| [4] | 李振江,万利,周世睿,陶楚青,魏巍. 基于时空Transformer网络的隧道交通运行风险动态辨识方法[J]. 吉林大学学报(工学版), 2025, 55(4): 1336-1345. |
| [5] | 聂为之,尹斐,苏毅珊. 任务驱动下成像声呐水下目标识别方法综述[J]. 吉林大学学报(工学版), 2025, 55(4): 1163-1175. |
| [6] | 单泽彪,薛泓垚,刘小松,姚瑞广,陈广秋. Alpha稳定分布噪声下基于近似l0范数稀疏重构的波达方向估计[J]. 吉林大学学报(工学版), 2025, 55(3): 1093-1102. |
| [7] | 赵孟雪,车翔玖,徐欢,刘全乐. 基于先验知识优化的医学图像候选区域生成方法[J]. 吉林大学学报(工学版), 2025, 55(2): 722-730. |
| [8] | 刘元宁,臧子楠,张浩,刘震. 基于深度学习的核糖核酸二级结构预测方法[J]. 吉林大学学报(工学版), 2025, 55(1): 297-306. |
| [9] | 徐慧智,蒋时森,王秀青,陈爽. 基于深度学习的车载图像车辆目标检测和测距[J]. 吉林大学学报(工学版), 2025, 55(1): 185-197. |
| [10] | 李路,宋均琦,朱明,谭鹤群,周玉凡,孙超奇,周铖钰. 基于RGHS图像增强和改进YOLOv5网络的黄颡鱼目标提取[J]. 吉林大学学报(工学版), 2024, 54(9): 2638-2645. |
| [11] | 张磊,焦晶,李勃昕,周延杰. 融合机器学习和深度学习的大容量半结构化数据抽取算法[J]. 吉林大学学报(工学版), 2024, 54(9): 2631-2637. |
| [12] | 乔百友,武彤,杨璐,蒋有文. 一种基于BiGRU和胶囊网络的文本情感分析方法[J]. 吉林大学学报(工学版), 2024, 54(7): 2026-2037. |
| [13] | 郭昕刚,何颖晨,程超. 抗噪声的分步式图像超分辨率重构算法[J]. 吉林大学学报(工学版), 2024, 54(7): 2063-2071. |
| [14] | 张丽平,刘斌毓,李松,郝忠孝. 基于稀疏多头自注意力的轨迹kNN查询方法[J]. 吉林大学学报(工学版), 2024, 54(6): 1756-1766. |
| [15] | 孙铭会,薛浩,金玉波,曲卫东,秦贵和. 联合时空注意力的视频显著性预测[J]. 吉林大学学报(工学版), 2024, 54(6): 1767-1776. |
|