吉林大学学报(工学版) ›› 2023, Vol. 53 ›› Issue (11): 3229-3237.doi: 10.13229/j.cnki.jdxbgxb.20221027
基于联邦学习和自注意力的工业物联网入侵检测
- 沈阳化工大学 计算机科学与技术学院,沈阳 110142
Intrusion detection for industrial internet of things based on federated learning and self-attention
Jun WANG( ),Hua-lin WANG,Bo-wen HUANG,Qiang FU,Jun LIU(
),Hua-lin WANG,Bo-wen HUANG,Qiang FU,Jun LIU( )
)
- College of Computer Science and Technology,Shenyang University of Chemical Technology,Shenyang 110142,China
摘要:
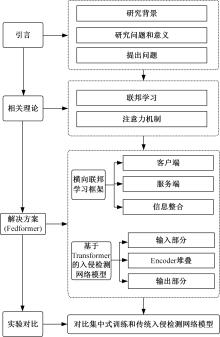
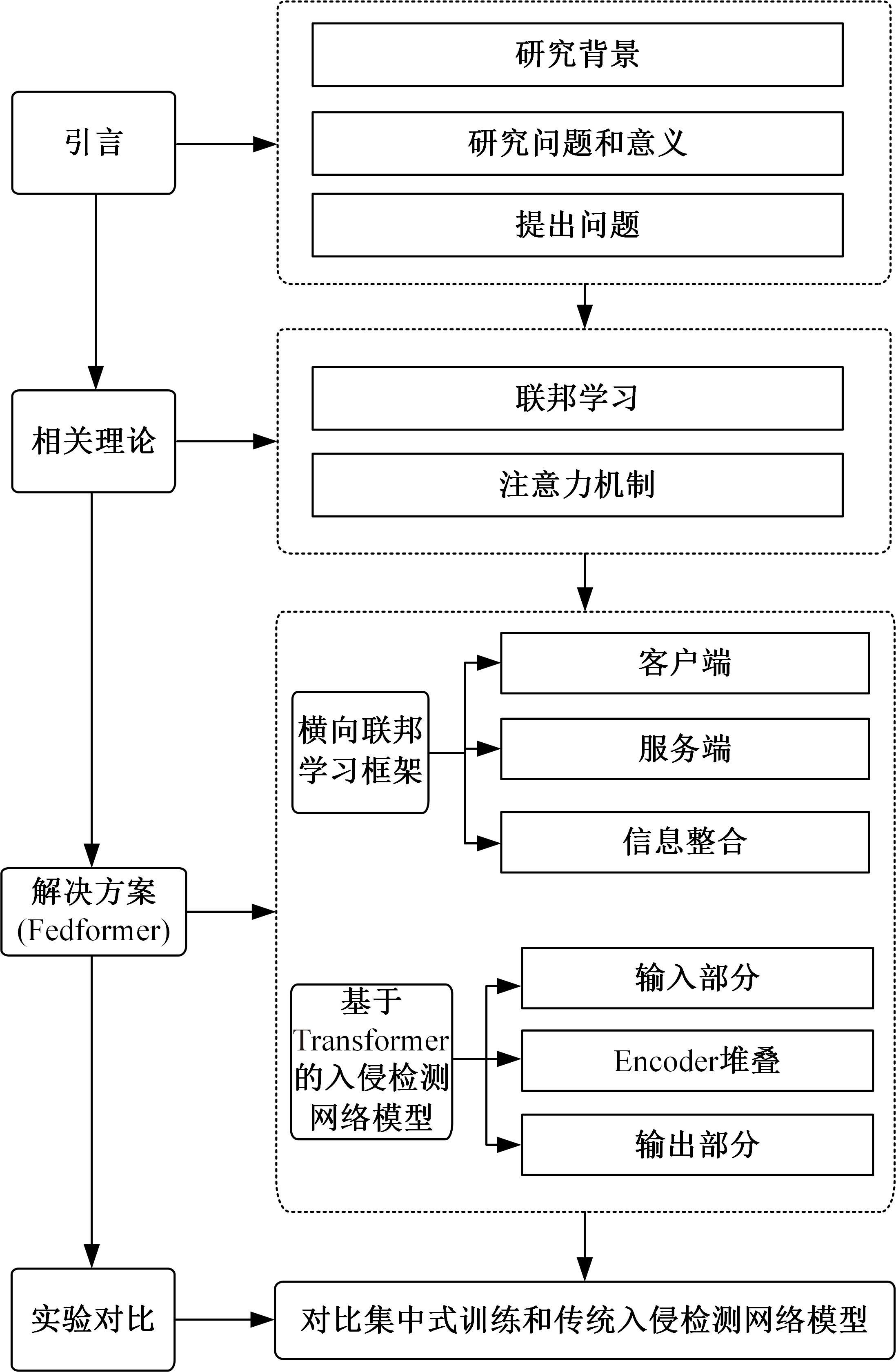
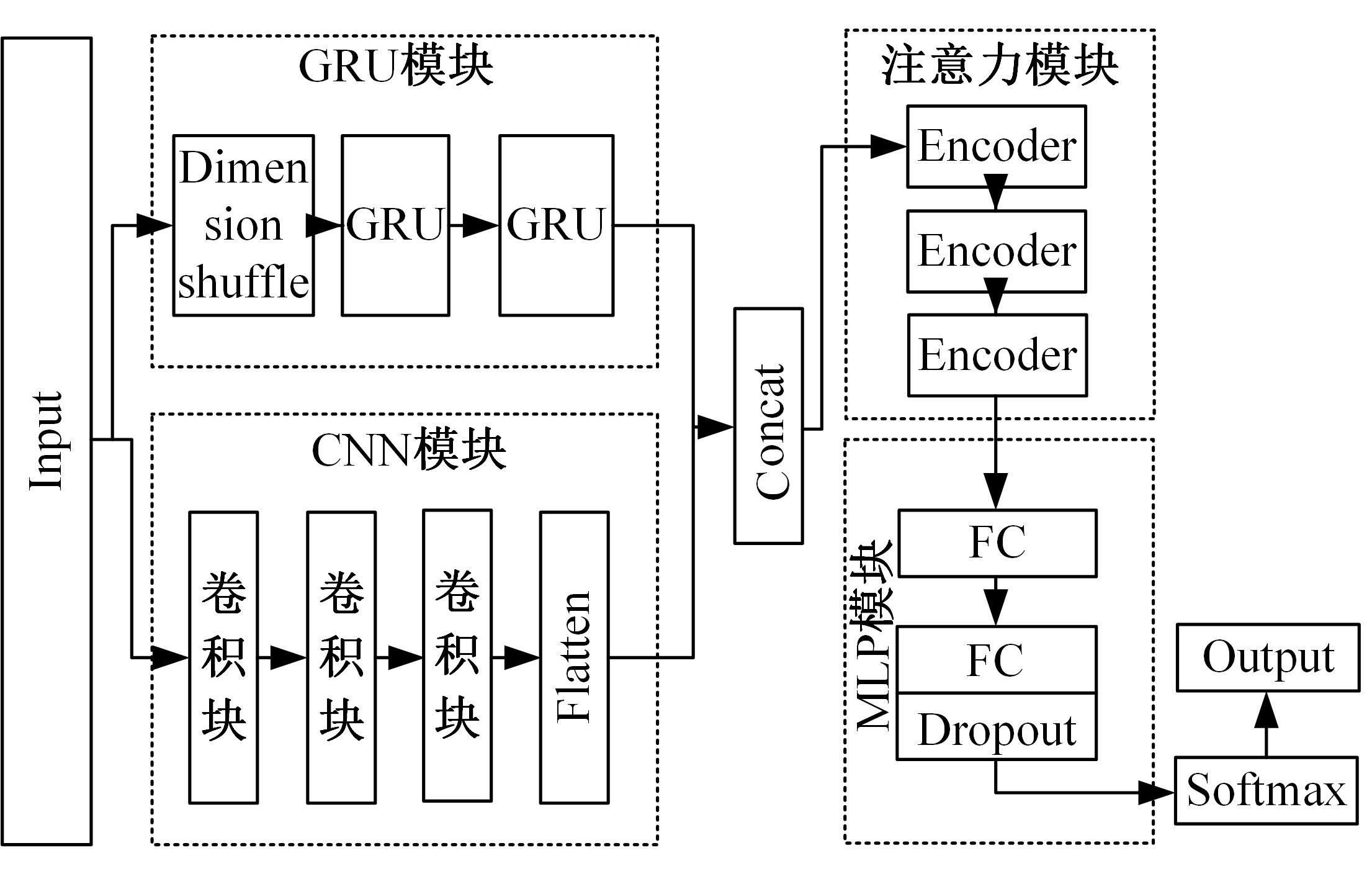
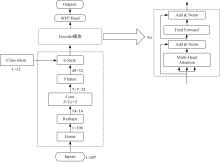
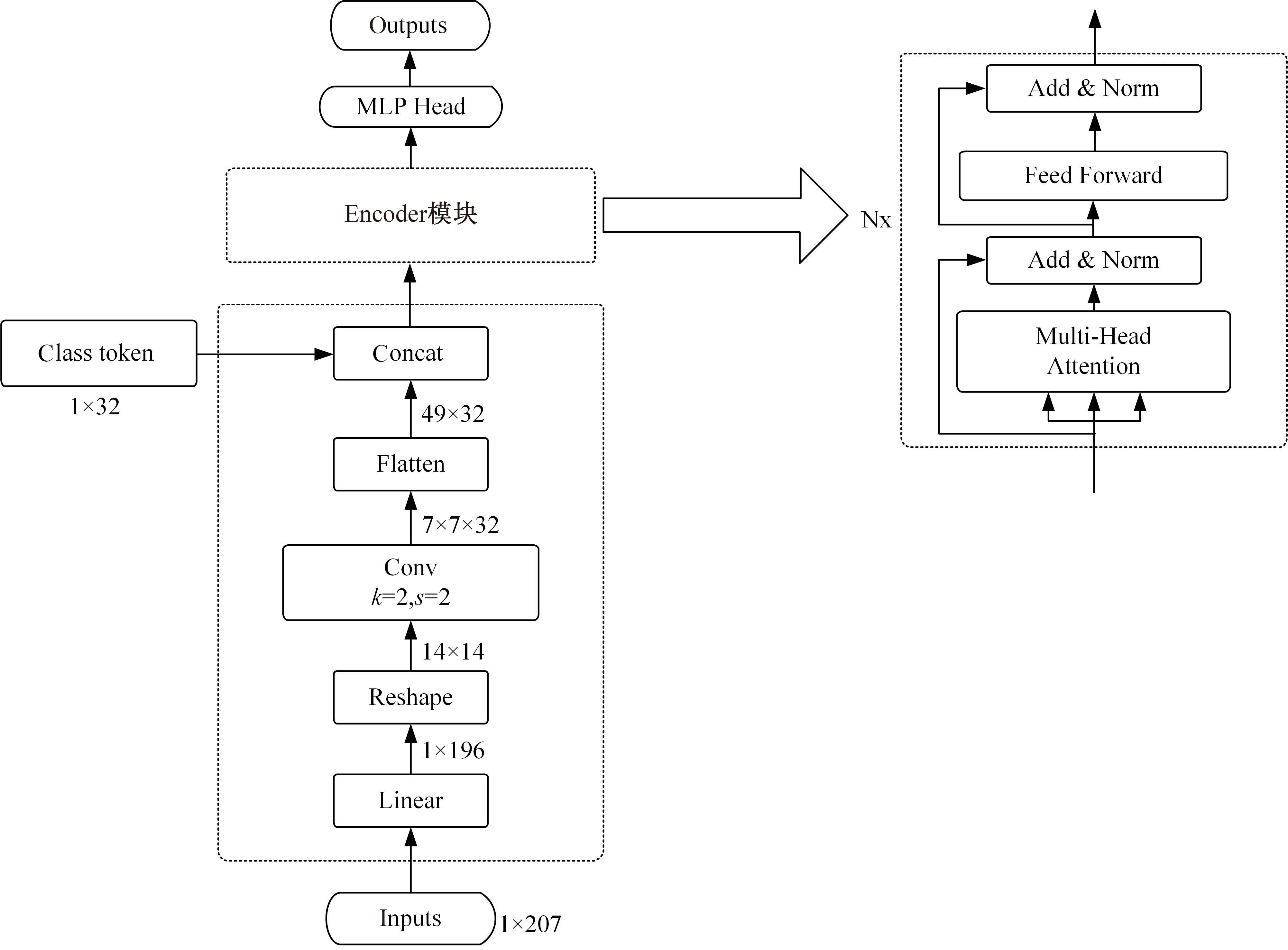
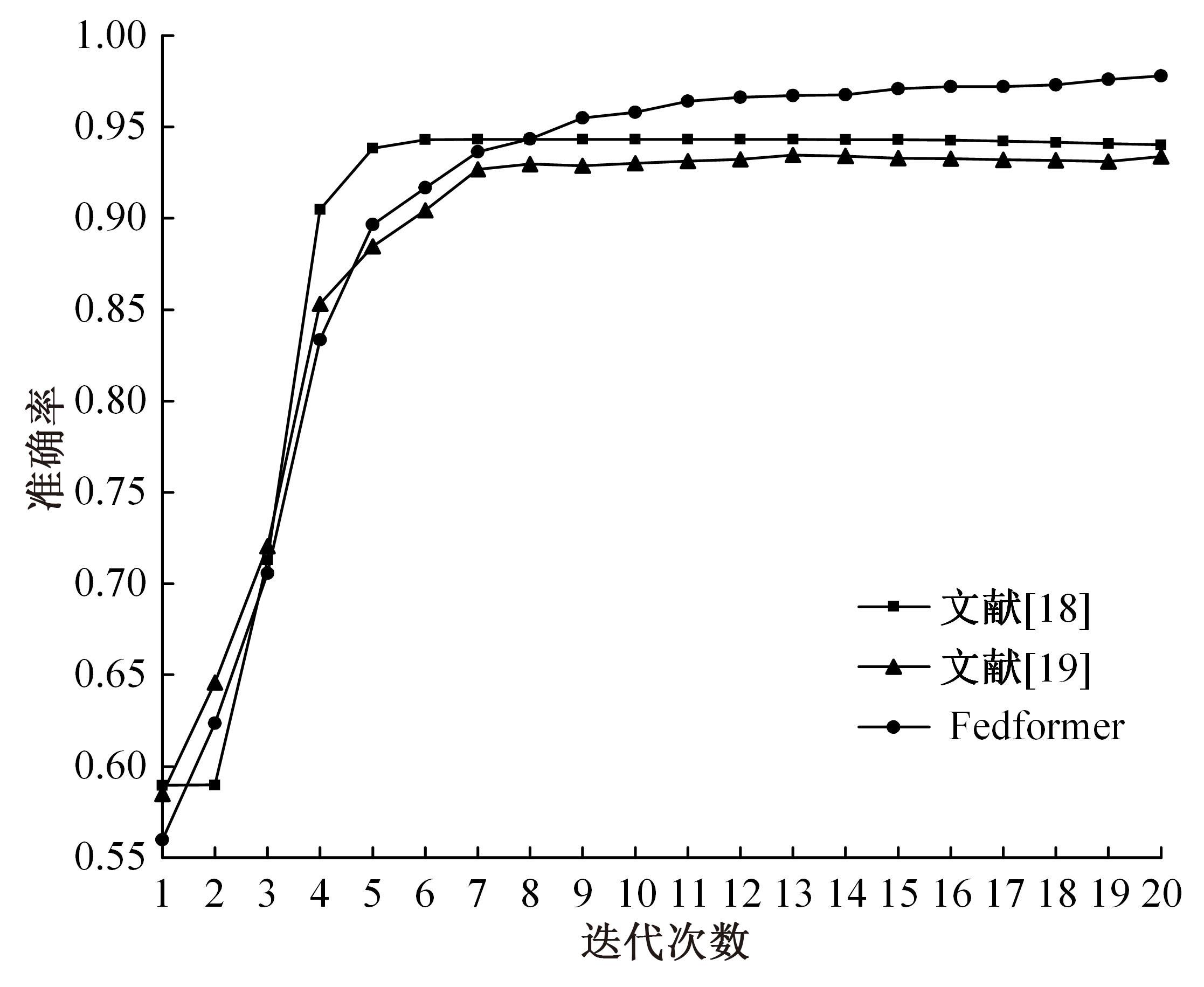
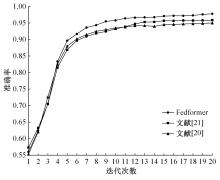
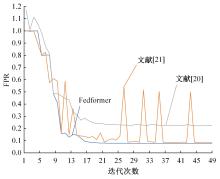
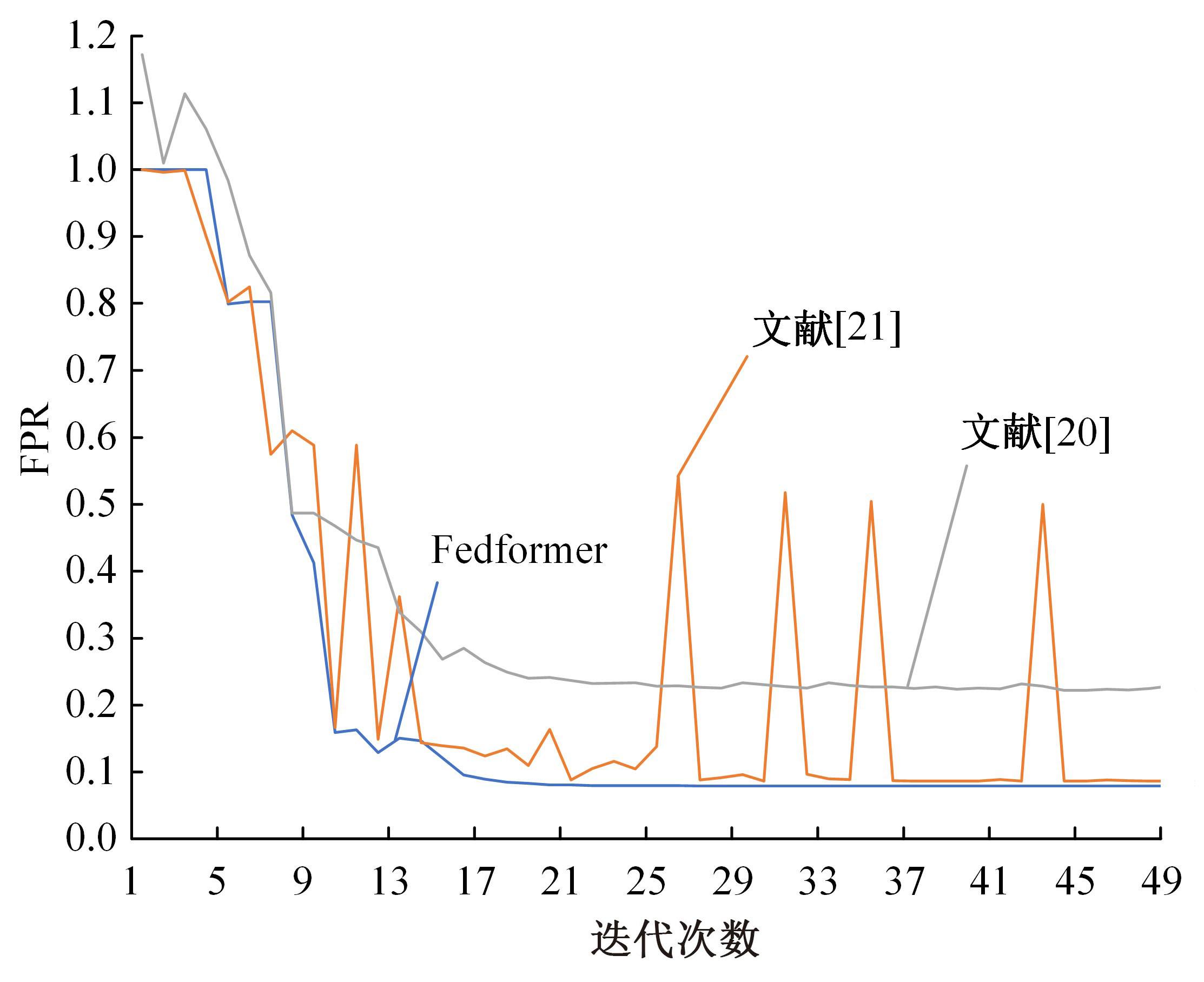
为解决工业物联网网络拓扑结构相对固定、特征低维、数据分布不均衡且相关性低,导致工业分布式环境下入侵检测模型训练效果差的问题,提出了一种基于联邦深度学习算法的工业物联网入侵检测模型——Fedformer。首先,引入并改进Transformer网络模型的编码器结构并嵌合卷积神经网络和门控循环单元,利用注意力机制为工业物联网构建了入侵检测模型;其次,将检测模型融合联邦学习框架,允许多个工业物联网共同构建一个全面的入侵检测模型。在保护本地数据隐私的前提下,提高对工业物联网网络攻击的检测准确率并降低误报率。实验结果表明:在工业网络环境下Fedformer的检测准确率达到98.09%,误报率降低到8.31%。
中图分类号:
- TP399
| 1 | Wang S, Jiang X, Wu Y, et al. Expectation propagation logistic regression(EXPLORER): distributed privacy-preserving online model learning[J]. Biomed Inform, 2013, 46(3):480-496. |
| 2 | Gao D S, Liu Y, Huang A B, et al. Privacy-preserving heterogeneous federated transfer learning[C]∥IEEE International Conference on Big Data, Los Angeles, USA, 2019: 2552-2559. |
| 3 | IEEE Std 3652 1—2020. IEEE Guide for Architectural Framework and Application of Federated Machine Learning [S]. |
| 4 | Mnih V, Heess N, Graves A, et al. Recurrent models of visual attention[J]. Advances in Neural Information Processing Systems, 2014, 3: 1-12. |
| 5 | Bahdanau D, Cho K, Bengio Y. Neural machine translation by jointly learning to align and translate[J]. CoRR, 2014, 1: arXiv.1409.0473. |
| 6 | Vaswani A, Shazeer N, Parmar N, et al. Attention is all you need[J]. NIPS, 2017, 1: arXiv.1706.03762. |
| 7 | Liu Y, Pi D. A novel kernel SVM algorithm with game theory for network intrusion detection[J]. TIIS, 2017, 11(8): 4043-4060. |
| 8 | 燕昺昊, 韩国栋.基于深度循环神经网络和改进SMOTE算法的组合式入侵检测模型[J]. 网络与信息安全学报, 2018, 4(7): 48-59. |
| Yan Bing-hao, Han Guo-dong. Combined intrusion detection model based on deep recurrent neural network and improved SMOTE algorithm[J]. Journal of Network and Information Security, 2018, 4(7): 48-59. | |
| 9 | Wu K H, Chen Z G, Li W. A novel intrusion detection model for a massive network using convolutional neural networks[J]. IEEE Access, 2018(6): 50850-50859. |
| 10 | 李贝贝, 宋佳芮, 杜卿芸, 等. DRL-IDS:基于深度强化学习的工业物联网入侵检测系统[J]. 计算机科学, 2021, 48(7): 47-54. |
| Li Bei-bei, Song Jia-rui, Du Qing-yun, et al. DRL-IDS: intrusion detection system for industrial internet of things based on deep reinforcement learning[J]. Computer Science, 2021, 48(7): 47-54. | |
| 11 | 石乐义, 侯会文, 徐兴华, 等. 基于特征选择和时间卷积网络的工业控制系统入侵检测研究[J]. 工程科学与技术, 2022, 54(6): 238-247. |
| Shi Le-yi, Hou Hui-wen, Xu Xing-hua, et al. Intrusion detection of industrial control systems based on feature selection and temporal convolution network[J]. Engineering Science and Technology, 2022, 54(6): 238-247. | |
| 12 | Nguyen T D, Marchal S, Miettinen M, et al. DïoT: a federated self-learning anomaly detection system for IoT[C]∥IEEE 39th International Conference on Distributed Computing Systems, Dallas, USA, 2019: 756-767. |
| 13 | Liu Y, Kumar N, Xiong Z H, et al. Communication-efficient federated learning for anomaly detection in industrial internet of things[C]∥Proceedings of 2020 IEEE Global Communication Conference, Piscataway, 2020: 1-6. |
| 14 | Wang X D, Garg S, Lin H, et al. Towards accurate anomaly detection in industrial internet-of-things using hierarchical federated learning[J]. IEEE Internet of Things Journal, 2022, 9(10): 7110-7119. |
| 15 | Moustafa N, Slay J. UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set)[C]∥Military Communications and Information Systems Conference, Canberra, Australia, 2015: 1-6. |
| 16 | Morris T, Gao W. Industrial control system traffic data sets for intrusion detection research[C]∥International Conference on Critical Infrastructure Protection, Arlington, USA, 2014: 65-78. |
| 17 | Yang Q, Liu Y, Chen T, et al. Federated machine learning: concept and applications[J]. ACM Transactions on Intelligent Systems and Technology, 2019, 10(2): 1-19. |
| 18 | 张行健, 王怀彬. 基于CNN-GRU的入侵检测算法研究[J]. 天津理工大学学报, 2022, 38(1): 37-42. |
| Zhang Xing-jian, Wang Huai-bin. Research on intrusion detection algorithm based on CNN-GRU[J]. Journal of Tianjin University of Technology, 2022, 38(1): 37-42. | |
| 19 | 郑伟发. 基于CNN-LSTM混合模型的入侵检测算法研究[J]. 网络安全技术与应用, 2020(5): 61-64. |
| Zheng Wei-fa. Research on intrusion detection algorithm based on CNN-LSTM hybrid model[J]. Network Security Technology and Application, 2020(5): 61-64. | |
| 20 | Liu Y, Garg S, Nie J T, et al. Deep anomaly detection for timeseries data in industrial IoT: a communication efficient on device federated learning approach[J]. IEEE Internet of Things Journal, 2021, 8(8): 6348-6358. |
| 21 | Li B, Wu Y, Song J, et al. DeepFed: federated deep learning for intrusion detection in industrial cyber-physical systems[J]. IEEE Transactions on Industrial Informatics, 2021, 17(8): 5615-5624. |
| [1] | 霍光,林大为,刘元宁,朱晓冬,袁梦,盖迪. 基于多尺度特征和注意力机制的轻量级虹膜分割模型[J]. 吉林大学学报(工学版), 2023, 53(9): 2591-2600. |
| [2] | 何颖,王卓然,周旭,刘衍珩. 融合社交地理信息加权矩阵分解的兴趣点推荐算法[J]. 吉林大学学报(工学版), 2023, 53(9): 2632-2639. |
| [3] | 张云佐,董旭,蔡昭权. 拟合下肢几何特征的多视角步态周期检测[J]. 吉林大学学报(工学版), 2023, 53(9): 2611-2619. |
| [4] | 肖明尧,李雄飞,朱芮. 基于NSST域像素相关分析的医学图像融合[J]. 吉林大学学报(工学版), 2023, 53(9): 2640-2648. |
| [5] | 赵亚慧,李飞雨,崔荣一,金国哲,张振国,李德,金小峰. 基于跨语言预训练模型的朝汉翻译质量评估[J]. 吉林大学学报(工学版), 2023, 53(8): 2371-2379. |
| [6] | 车翔玖,徐欢,潘明阳,刘全乐. 生物医学命名实体识别的两阶段学习算法[J]. 吉林大学学报(工学版), 2023, 53(8): 2380-2387. |
| [7] | 王连明,吴鑫. 基于姿态估计的物体3D运动参数测量方法[J]. 吉林大学学报(工学版), 2023, 53(7): 2099-2108. |
| [8] | 张则强,梁巍,谢梦柯,郑红斌. 混流双边拆卸线平衡问题的精英差分进化算法[J]. 吉林大学学报(工学版), 2023, 53(5): 1297-1304. |
| [9] | 张振海,季坤,党建武. 基于桥梁裂缝识别模型的桥梁裂缝病害识别方法[J]. 吉林大学学报(工学版), 2023, 53(5): 1418-1426. |
| [10] | 刘培勇,董洁,谢罗峰,朱杨洋,殷国富. 基于多支路卷积神经网络的磁瓦表面缺陷检测算法[J]. 吉林大学学报(工学版), 2023, 53(5): 1449-1457. |
| [11] | 姜宇,潘家铮,陈何淮,符凌智,齐红. 基于分割方法的繁体中文报纸文本检测[J]. 吉林大学学报(工学版), 2023, 53(4): 1146-1154. |
| [12] | 吕卫,韩镓泽,褚晶辉,井佩光. 基于多模态自注意力网络的视频记忆度预测[J]. 吉林大学学报(工学版), 2023, 53(4): 1211-1219. |
| [13] | 于鹏,朴燕. 基于多尺度特征的行人重识别属性提取新方法[J]. 吉林大学学报(工学版), 2023, 53(4): 1155-1162. |
| [14] | 潘弘洋,刘昭,杨波,孙庚,刘衍珩. 基于新一代通信技术的无人机系统群体智能方法综述[J]. 吉林大学学报(工学版), 2023, 53(3): 629-642. |
| [15] | 何颖,樊俊松,王巍,孙庚,刘衍珩. 无人机空地安全通信与航迹规划的多目标联合优化方法[J]. 吉林大学学报(工学版), 2023, 53(3): 913-922. |
|